Many Samsung fans were excited when the Galaxy S9 kept the 3.5 mm headphone jack. While this is a rare delight in 2018, you also have the option for high quality audio playback over Bluetooth. When used with compatible headphones, the S9's new Bluetooth audio codecs can greatly improve audio quality.
WhatsApp comes with a ton of great features that make it the go-to messaging app for millions of people around the world. Among these is the ingeniously simple Read Receipts that let you know your message has been viewed. If you want to read a message without alerting the sender, however, there are simple tricks you can perform to give yourself plausible deniability.

When it comes to media players, few are more capable than VLC. With its extensive codec support, VLC is able to play almost any video file. Partly due to its open-source nature, features are constantly added. This trend has continued with a new update that added native Chromecast support.
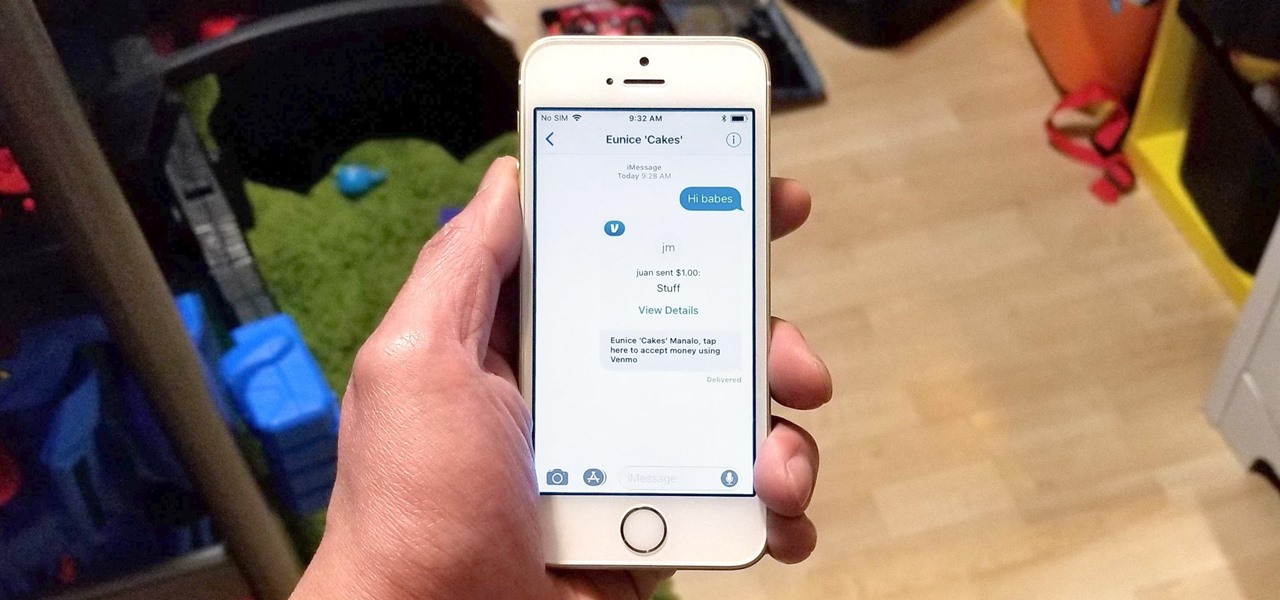
Venmo makes it incredibly convenient to send money to friends and family, and it all happens instantly from the comfort of your smartphone. Even better, if you have an iPhone, Venmo lets you conduct transactions straight from the default Messages app, giving you more flexibility and convenience over Android users.

Every dollar that comes your way is a blessing, especially when it comes to trading in the volatile world of bitcoins. Thankfully, Coinbase rewards you for sending much valued customers their way, giving you more money to feed your cryptocurrency trading needs.
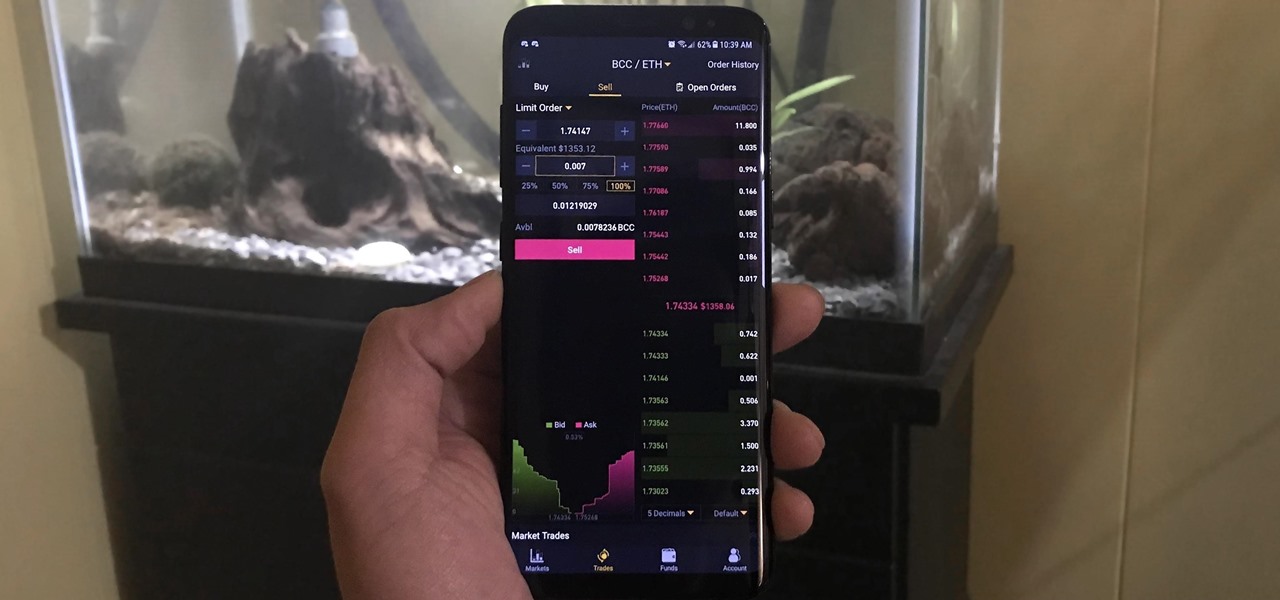
Using Bitcoin (BTC) or Ethereum (ETH) to buy alt-coins like TRON (TRX), Stellar (XLM), or Ripple (XRP) can seem intimidating if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

With Google's release of Poly API on Thursday, the search giant has found a way to simplify the workflow for AR creators by enabling the ability to integrate its 3D object search engine Poly directly into an application.

A few months ago, we gave you a small peek at a new entrant in the race to deliver augmented reality smartglasses to the masses, and now the device is finally ready for the public. ThirdEye Gen is now accepting preorders for its X1 Smart Glasses, which will also provide users with an AR-centric app store.

Meta Company has filed its response to allegations that the user interface for their augmented reality headsets infringe on six patents owned by a mostly-unknown company.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

The staff at Next Reality News is legitimately excited about the prospects that Google's ARCore could bring not only to smartphones and tablets running Android, but also to Android-based hardware such as smartglasses.

Gonorrhea infections reached a peak in 1975, then decreased until 2009, when infection rate started rising and has increased each year since. With the rise of antibiotic resistance, those numbers are only going to get worse — unless we find new treatments against the bacteria.

Cytochrome P450 (P450s) are proteins found in nearly all living organisms, which play roles that range from producing essential compounds and hormones to metabolizing drugs and toxins. We use some of the compounds synthesized by P450 in plants as medical treatments, but the slow growth and limited supply of these plants have put the drugs' availability in jeopardy and jacked up prices.

Zently — the mobile app for renters — is taking on Venmo with its newest feature. Traditionally used to automate rent payments, deliver rent checks for free, and communicate with your landlord, it now allows you to connect to your bank account and split bills with housemates. Following the addition of Zelle to several major banks apps — to allow users to transfer money to their contacts — the battle of the mobile payment apps is getting increasingly fierce. With this new update, Zently is als...

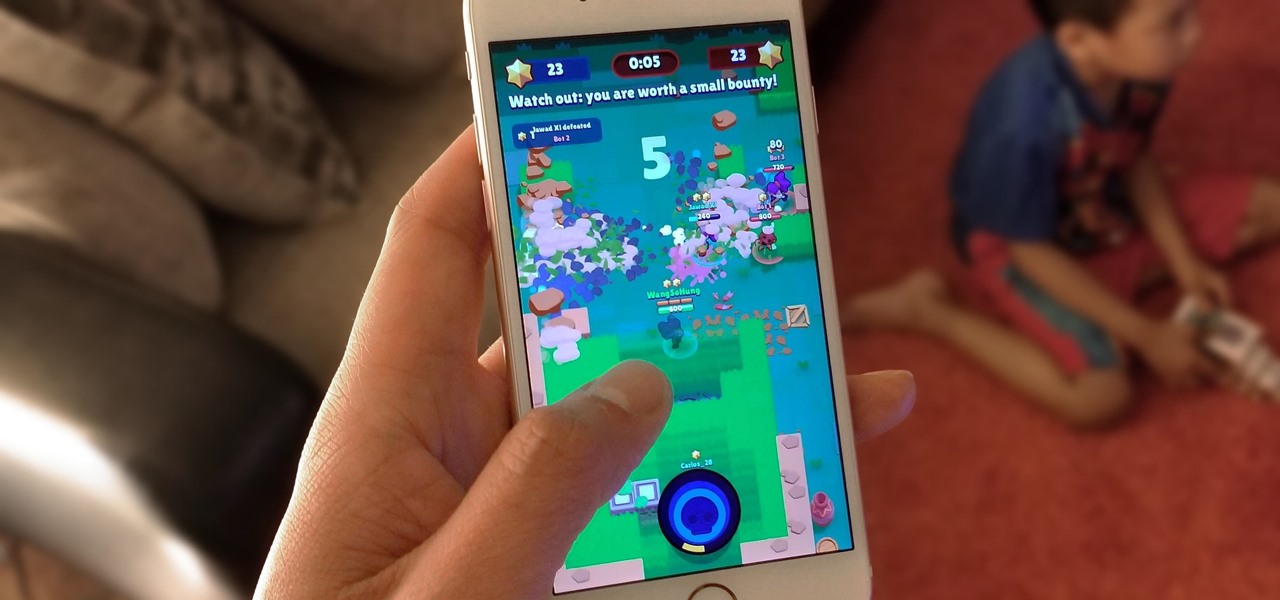
Supercell's highly anticipated Brawl Stars has soft launched in Canada, with gamers worldwide salivating at the prospect of a full debut around the corner. Unbeknownst to many, this game can be played on your iPhone right now, regardless of where you live.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

Every now and then, it's refreshing to play a game that doesn't involve much thinking. Sega is set to bring us just that, as a new game called WWE Tap Mania has soft launched for iOS and Android in the Philippines.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

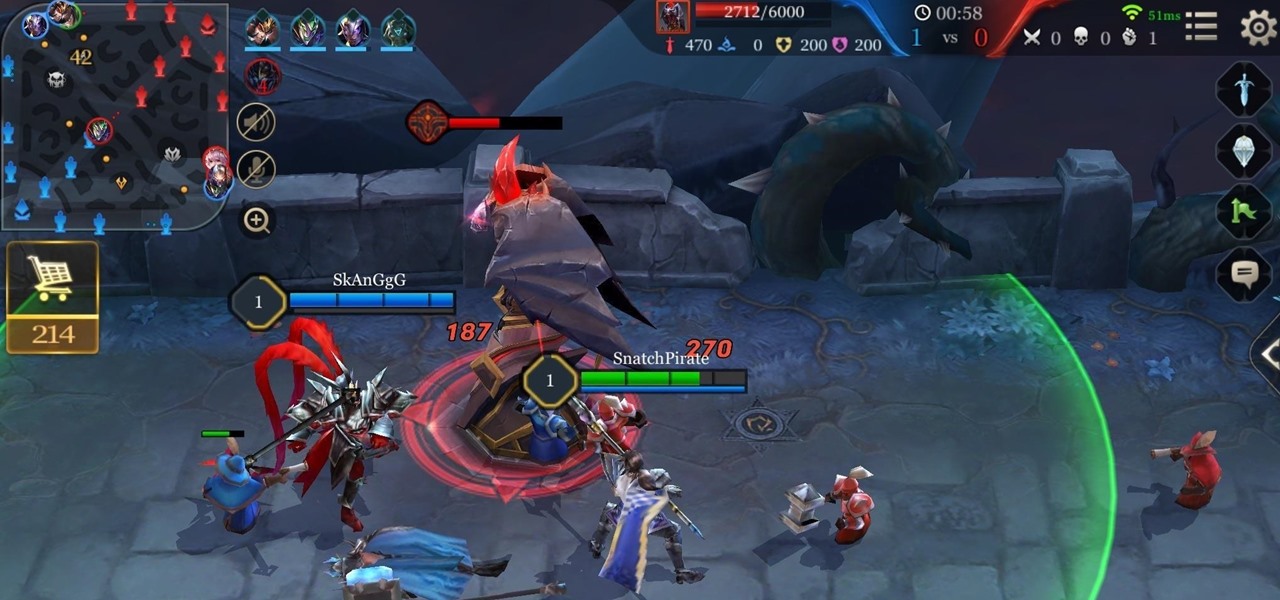
You may have heard of Honor of Kings, the multiplayer online battle arena game so popular that it has the potential to do for mobile what League of Legends has done for the PC in the world of competitive online gaming, but you'll soon hear about its western iteration, Strike of Kings. Tencent, the China-based online gaming giant now looks to expand to the lucrative western market and has released the game to many parts of Europe as a soft launch for iOS devices. Gameplay in Strike of Kings is...

Our canine best friends could spread our bacterial worst nightmare, according to a recent study. The problem with drug-resistant bacteria is well known. Overused, poorly used, and naturally adaptive bacteria clearly have us outnumbered. As science drives hard to find alternative drugs, therapies, and options to treat increasingly resistant infections, humans are treading water, hoping our drugs of last resort work until we figure out better strategies.

This week's Brief Reality is led by a pair of stories with an eye to the future of the augmented reality industry, first in terms of standards for the industry, then with regards to its future applications in the automotive realm. Finally, one company looks to boost its future sales with an executive hire.

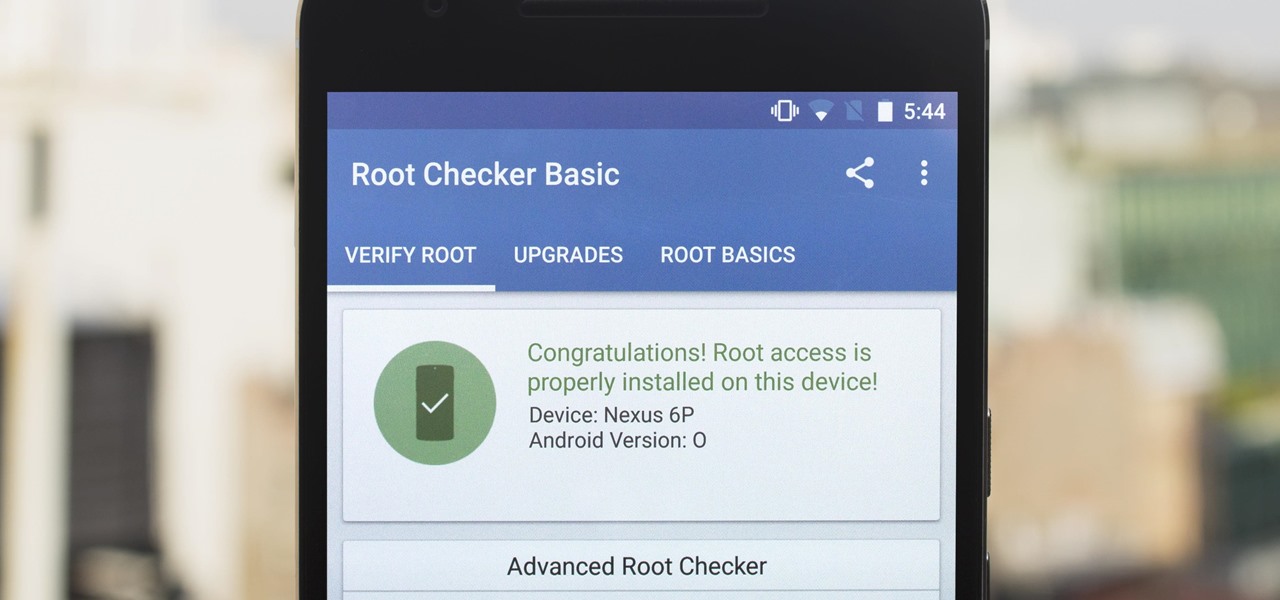
The first developer preview of Android Oreo 8.0 was only out for a couple of days before Chainfire created a new root method for it. For the time being, only the Nexus 5X and Nexus 6P are supported by this first SuperSU ZIP, as the Pixel's dual-partition layout has created some hurdles, though Chainfire is surely working on overcoming those at some point soon.

The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fictional creatures found in Pokémon GO. However, there were some video game consoles that kept kids indoors, such as the Game Boy, SNES, and more importantly—the first ever PlayStation.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Antibiotic-resistant infections that usually occur only in hospital settings are spreading in communities, increasing hospital stays—and danger—for young children.

It won't come as a surprise to hear that your cell phone, tablet, and laptop are loaded with bacteria and other organic material. While most of these bacteria are harmless, there are good reasons to reduce the capability of your mobile devices to infect you—or other people.

In the perpetual search for a renewable and convenient energy source, our bacterial friends have once again stolen the limelight.

Imagine you have mastered the perfect cherry pie for your annual work picnic but, upon taking it out of its airtight pie carrier, your heart sinks as you realize the crust has turned to mush thanks to the moisture from the filling. Sound familiar?

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

When we were kids, snacks on-the-go or in our lunch box were often Kellogg's Nutri-Grain cereal bars. There were flavors like strawberry, blueberry, and our beloved apple-cinnamon.

As a child, you probably spent some time trailing an adult at the grocery store. You lovingly eyed the aisle with brightly colored fruit snacks, reaching for the tempting boxes, placing them discreetly in the cart only to be told, "No! That's JUNK FOOD. You can't have it."

When it comes to sharing files between a smartphone and a computer, there are several solutions available for a Windows and Android pairing. But for those of us with Apple devices, the selection of apps in this category isn't quite as great. You can use AirDrop to quickly share files, but searching for files is not so easy.

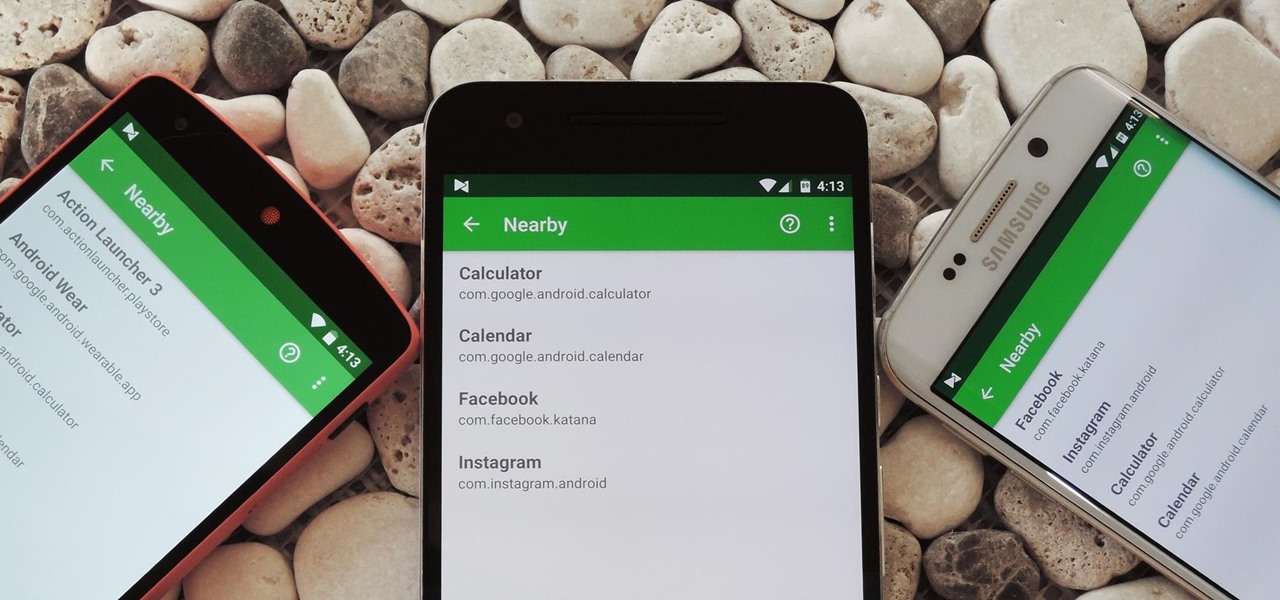
Google has an intriguing feature called Nearby that lets users share content without being on the same Wi-Fi network, or without even exchanging contact info first. Instead, the function uses an array of standard smartphone features, as well as subsonic sound, to identify other devices that are in the room, then makes a secure connection to transfer any data.

Soda bottle jello went viral when the popular YouTube channel AwesomeDisneyToys posted video directions for this revolutionary gelatin confection. I just had to try it out to see what the hype is all about.

Dried spices and herbs seem to be immortal; a peek in your parents or grandparents' cupboards will likely unveil cinnamon, basil, and oregano older than you.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

A couple days back we told you about the 30-day free trial for people interested in YouTube Red, and now Google is running a concurrent promotion that really sweetens the deal, especially if you're a first-time subscriber and own or plan to buy a Chromecast.

There's a feature in Google's Photos app for Android, iOS, and the web that lets you create shared albums with your friends and family. It's really a useful feature that makes it fun and easy to collaborate on an album with a person or persons of your choosing.

Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget you ever used Windows Vista... almost.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.