Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.

If you installed Android 9.0 Pie, you might have enjoyed trying out some of the new features in the latest version of Google's OS. However, change isn't always a good thing, so you might be wishing you could downgrade back to Oreo right about now. Good news — you can.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

All day I dream of eggs: scrambled, poached, over easy, hard-boiled, fried, baked, raw... Okay, the last one is a joke (unless you're Gaston, which means that you eat five dozen of them and you're roughly the size of a barge). But eggs are freaking good in just about any cooking prep, and more often than not are the foundation of your favorite baked goods.

Samsung's Note series is directly responsible for some of the biggest innovations in smartphones. As the first "phablet," it sparked the current craze for bigger screens, and the S Pen stylus has been mimicked numerous times. Even the curved display made famous by the Galaxy S6 edge made its debut on the Note 4, so this is the one smartphone line you want to keep track of if you like to stay on the bleeding edge.

Chrome apps and extensions are powerful tools for students: they can help optimize your web browsing experience by helping you take notes, check your grammar as you compose documents and emails, and even help you squeeze a little more juice out of your laptop's battery by freezing unused tabs and optimizing YouTube streams.

This year, Google released two Nexus phones to glowing reviews, and as we've grown to expect, the Android community wasted no time in coming up with a root method for both. In fact, legendary root developer Chainfire even devised an entirely new "systemless" method for rooting that should make updating a bit less complicated, along with a few other benefits.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.
Welcome back Hackers\Newbies!

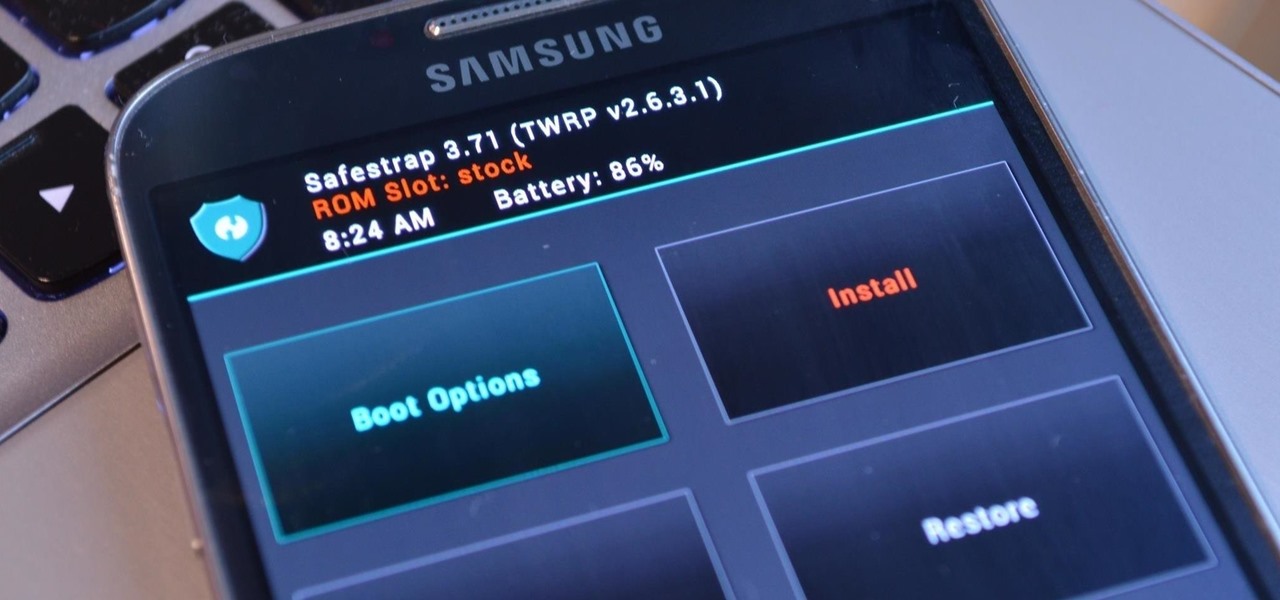
Returning your device to stock, whether it is because you need to sell it or just want to receive OTAs again, is not always a simple process. Since HTC has released countless variations of both the M7 and M8 HTC One, it can be a pain in the ass finding the right files and tools to get your phone back to stock settings.

My bathroom is like my own private arcade room. Whenever I'm seated comfortably on the toilet, no one is going to disturb me, so I can play anything I want on my smartphone. You probably do it, too — and your parents, kids, friends, colleagues, and boss — so don't be afraid to admit it.

Stop! Do not pour that leftover wine, coffee, or bacon grease down the drain. And those herbs that have been in your fridge so long they've literally turned on you? And what about when that recipe only calls for two tablespoons of heavy cream, a quarter cup of tomato purée, or three cloves of garlic? Unless you plan on using the leftovers again in the next week or so, don't bother refrigerating them because they won't last.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

Food labeling is a tricky beast. For instance, when I read the words "cage-free" on an egg carton, I think it means that happy chickens frolic in a sunlit meadow all the livelong day until they're gently herded into a clean, sweet-smelling coop to lay a few dozen eggs—which I can purchase for a reasonable price, of course.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

When it comes to give away or sell your iPhone, you can't just power it down, take out the SIM card, and hope everything will be okay. There's valuable data on your iPhone, and you need to get rid of it. Plus, if you don't perform all the necessary steps, chances are whoever ends up with the device won't even be able to use it. If you're selling it, that could ding your seller reputation.

The paper towel is a wondrous invention. It allows cooks to wipe up really gross stuff without having to constantly do laundry and drain fried foods so they're crunchy and crispy instead of oily and heavy. But did you know that your humble paper towel has several other uses besides the obvious ones? Read on to find out these essential hacks.

Update, November 12, 2014: Android 5.0 Lollipop is officially out now. If you haven't gotten the OTA yet, check out our new guide on installing the official Lollipop builds on any Nexus for download links and instructions, for Mac or Windows.

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

Third-party ROMs like CyanogenMod are the ultimate form of customization for softModders. Hard-working developers offer us alternate Android experiences to replace our often bloatware-riddled stock ROMs.

Alright, I'll admit it, iOS can be quite nice. Android loyalist that I may be, I'm not so stubborn that I can't recognize a good thing when I see it. Apple's iOS has a lot of strengths, and our Nexus 4s, god bless 'em, are growing a little long in the tooth.

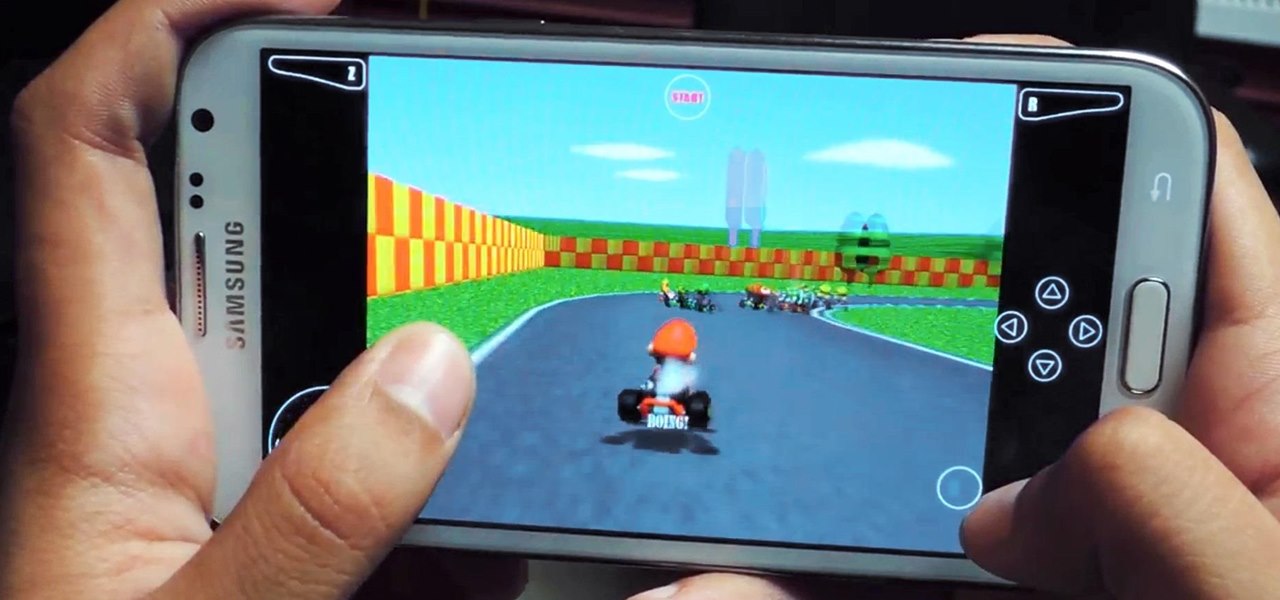
Nothing can beat a portable system designed specifically for gaming. There are tons of emulators available on Google Play, but most have awkward controls, large game files, resolution issues, and hardware compatibility problems. The list could go on...

This is a simple pattern, designed to produce a well-fitting mitten. Both the right and left mittens worked the same up to the shaping for the top of the mitten. A slight adjustment for making one right and one left, then they are worked the same. The gusset for the thumb constructed with the increases made in the center of the gusset, rather than on each side. This makes it easy with a minimal amount of counting stitches as you go. I have been crocheting for 56 years. In doing research for w...

I know, "Steamdown" conjures images of a hoedown, but "Steampunk prop breakdown" is a bit of a mouthful, I thought.

Still on the fence about Apple's native Notes app? The latest Notes update for iPhone, iPad, and Mac is about to change your mind. With some fantastic new features and plenty of valuable tools from previous software versions, Notes is becoming a clear winner when it comes to saving important information from your personal and professional life.

The new iPhone 16, 16 Plus, 16 Pro, and 16 Pro Max are worth upgrading to, but if you want more advanced features, especially for the camera, you may want to take a closer look at the iPhone 16 Pro and iPhone 16 Pro Max.

If you're in the market for a new smartphone and want nothing but the best of the best, now's the time to act. Some of the greatest phones money can buy are being released as we speak, while others are still in their prime and will continue to be for most of 2024. Whether you want an iPhone or Android, we've rounded up the best picks you have to choose from for top-of-the-line specs and advanced features.