Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Snapchat is mostly credited as the first AR social network, and, like most social media companies, its revenue model is nested largely within advertising. As such, the company now has a new avenue for branded content.

Wherever there are people, the party is sure to follow. Well, a party of microbes, at least. That is what scientists at NASA's Jet Propulsion Laboratory have found after a 30-day microbial observation of the inflatable lunar/Mars analog habitat (IMAH).

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

People who have heart disease get shingles more often than others, and the reason has eluded scientists since they first discovered the link. A new study has found a connection, and it lies in a defective white cell with a sweet tooth.

I currently am and have always been what one might call a PC/Android guy. Many that know me well would likely even go so far as to say I am anti-Apple. About an hour after seeing the ARKit demo during the day-one keynote at WWDC, I became the owner of a brand new Mac.

We know that healthcare-related facilities can be fertile ground for antibiotic-resistant bacteria, but recent research suggests your produce aisle might be too.

Mosquitoes are a big problem, and citronella candles are not the solution. There are a lot of mosquito species. The American Mosquito Control Association reports there are more than 3000 mosquito species in the world, and about 200 of those occur in the US. The most common are the Aedes, Anopheles, and Culex species. These are also the three mosquito species most likely to transmit serious illness, and all of them live in the US.

In the worst measles outbreak in the state since 1990, the Minneapolis Department of Heath races to contain the spread of an infection believed to have originated from an infected traveler. Mistaken attitudes and unvaccinated travelers are creating a world of hurt and disease for Americans. A recent study found that more than half of eligible travelers from the US are electing to skip their pre-trip measles vaccine.

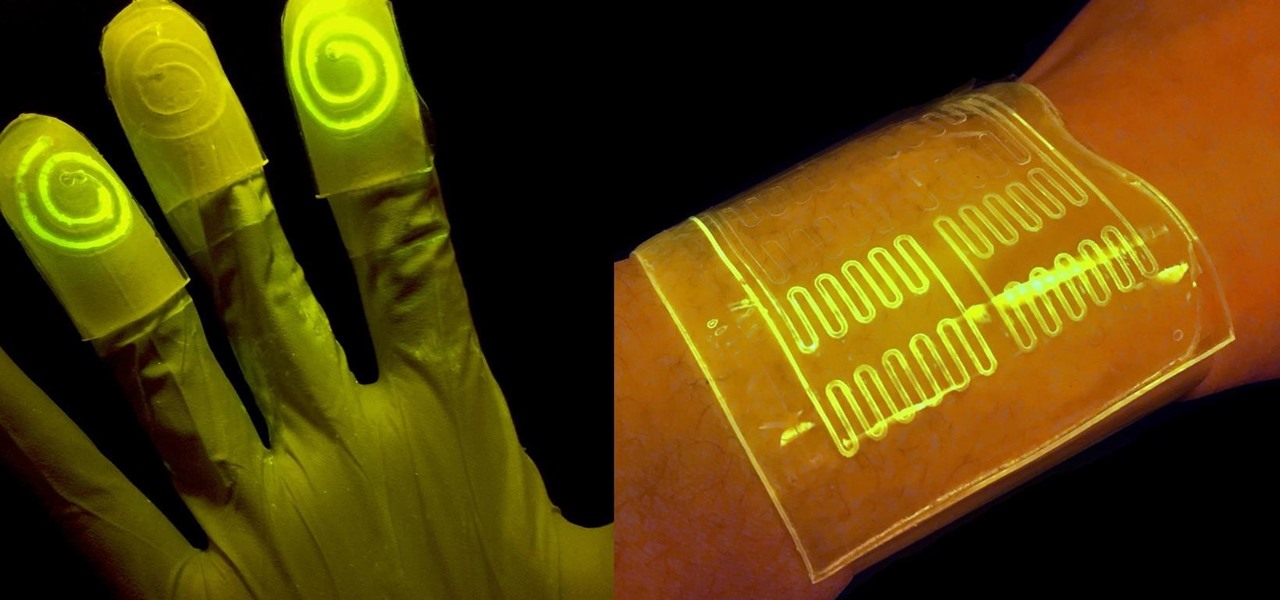
While at work, you notice your gloves changing color, and you know immediately that you've come in contact with dangerous chemicals. Bandages on a patient signal the presence of unseen, drug-resistant microbes. These are ideas that might have once seemed futuristic but are becoming a reality as researchers move forward with technology to use living bacteria in cloth to detect pathogens, pollutants, and particulates that endanger our lives.

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

Antibiotics used to prevent diseases in livestock are creating a world of hurt for humans and the soil we depend on for food. Bacterial resistance to antibiotics is a global health issue. The overuse, underuse, and poor use of these life-saving drugs is rapidly removing them as a treatment option for serious infections in humans—plus bacteria are naturally adaptive.

A robust appetite for imported foods is leading to increased disease outbreak in the US. Despite the locovore and slow food movements, America's demand for foreign foods is picking up. According to a study published in the journal of Emerging Infectious Diseases, demand for imported fresh fruits, vegetables, and seafoods has jumped in recent years.

Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

Paranoid Android has always been one of the most popular custom ROMs because of the inventive features its developers add to Android. Two of the biggest draws in particular have to be the "Halo" notification bubble, and the "Pie" navigation buttons, which can both fundamentally change the way you interact with your device.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...

The reality of tomorrow will not be static. We're here to bring you a daily look into the cutting edge innovations poised to merge the impossible worlds of our imagination with real life. We're NextReality.

Back in July, Oreo released their newest, limited-edition flavor, Choco Chip. These one-of-a-kind cookies are made up of golden, vanilla chocolate chip wafers with a chocolate chip creme filling.

There's a common saying that separates cooks from bakers: baking is a science, while cooking is an art. When baking, one little misstep can alter the texture, taste, and consistency of any recipe.

Why, for the love of God, do people keep inventing ridiculous devices that make the simplest things more complicated in the name of convenience? This may be a rhetorical question that will forever go unanswered—because these crazy gadgets just keep rolling out, one after the other.

Greetings, fellow NBers! Welcome to my sixth iteration of my sorting series. Today, we'll be discussing a personal favorite: Quicksort, or Quick Sort.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

Android Marshmallow was recently released, and as we've grown to expect, a root method was quickly made available to devices running the brand new operating system. Legendary root developer Chainfire has stated that he's working his way towards retiring from the scene, but he still had enough left in the tank to quickly publish an update to his popular SuperSU root method.

Cheap Chinese knockoffs have been around for ages, but recently, skyrocketing demand has led to a massive influx of counterfeit smartphones. Sellers on Craigslist seem to have no trouble getting ahold of these fake devices, then passing them off as the real deal and turning a solid profit before vanishing into thin air. This type of scam tends to happen even more frequently after Apple launches a new iPhone or Samsung debuts a new Galaxy.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Often, despite your favorite makeup mecca's rows and rows of endless colors, applicators, and brands, it's hard to find the perfect shade of lipstick—especially one at the price you want. Rather than resorting to what's available in stores, turn to your stovetop and a box of crayons.

A friend of mine is a classically trained chef, and she often invites me over to her house to eat whatever goodies she has concocted. A few years ago I asked her the cliché question that every chef is sick of answering: "What's your favorite food?"

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Most mobile games have moved to an online-only format, meaning you need to be connected to the Internet in order to get any kind of multiplayer action going. This is great when you're at home on Wi-Fi, but when you're out and about, slow and inconsistent data speeds can cause serious lag. Or worse yet, you may be nearing your monthly data cap!

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Before I start this tutorial, no, this is not that "Effective. Power." text that is going around. With that being said, let's talk about this attack.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.