The sun-drenched people of Phoenix can now sign up to ride in an automated car, for free, courtesy of Waymo. The Alphabet affiliate announced its "early ride program," which will (hopefully) demonstrate how self-driving cars will fit into people's everyday lives. Highlighting a challenge Nissan CEO Carlos Ghosn has spoken about that faces the driverless industry.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

When we talk about driverless technology, the go-to companies are usually Waymo, Uber, or Tesla. However, traditional automakers like Ford and GM are also staking claims to the driverless and advanced driver assistance spaces.

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...

When the time comes to replace your car, you most likely have a checklist of criteria that you would like on the new one. Your car is possibly the most expensive possession you have—or the second-most expensive, after your home—so you want to make sure that you are not only getting what you want, but that you are getting the best deal possible.

Alphabet's moonshot factory, X (formerly "Google X"), is a secretive place, but it seems that when they are close to graduating a project, then they need to staff it up quickly. Watching for these job ads is one easy way to know they're close to budding off a baby.

One of the best things about cold weather is soup, and there's nothing more comforting than a great chicken noodle soup. But I've often grabbed a can from the grocery store and found the chicken dried out and over-processed... and the noodles soggy and tasteless. What's worse: there's never enough of the stuff you like (such as the vegetables) and too much of what you don't (the nasty stuff I mentioned above).

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

When the power goes out, having the ability to contact others becomes extremely important, and your cell phone can be one of the most important tools to have. But if the power is out for an extended period of time, battery life becomes a constant problem.

Before starting a boxing training session it is important to wrap hands properly. A boxer's hands are useless if not properly cared for. Learn how to wrap hands in this boxing video tutorial.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

For years, Apple's Notes app has been a reliable way to jot down important ideas, tasks, plans, and more. While there are apps on the market that advertise themselves as being more feature-filled than the stock iOS option, Apple is now giving them a run for their money. Here are 14 new features and changes you'll see with Notes in iOS 13.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

In this video series, our expert will teach you how to write and pronounce the Chinese symbols for words related to house rental. Learn about the derivation of words like landlord, rent out and apartments. Get tips on writing and pronouncing the Chinese word for expensive, utilities, and transportation with expert tips in this free language lesson video series.

A sensory poem is a poem that uses all five senses to describe something. These are common poems for grade school children. They are not difficult to do and only need to choose something to describe and follow the rules.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

The COVID-19 pandemic has created a frenzy for news and information that is nearly unprecedented in the smartphone era, with a major side effect of misinformation. Now, major tech companies are making it easier to ask for advice about novel coronavirus from their respective digital assistants. Results may vary, but Apple and Google are the most useful at the moment.

As a native of Alabama, Apple CEO Tim Cook has a special place in his heart for the state. He also empathizes with the struggles that African-Americans have historically faced in the state, particularly during the 1950s and '60s civil rights era.

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

After debuting its virtual Pocket Gallery last year with the works of Johannes Vermeer, Google Arts & Culture has released a sequel that brings even more artists into your home via augmented reality.

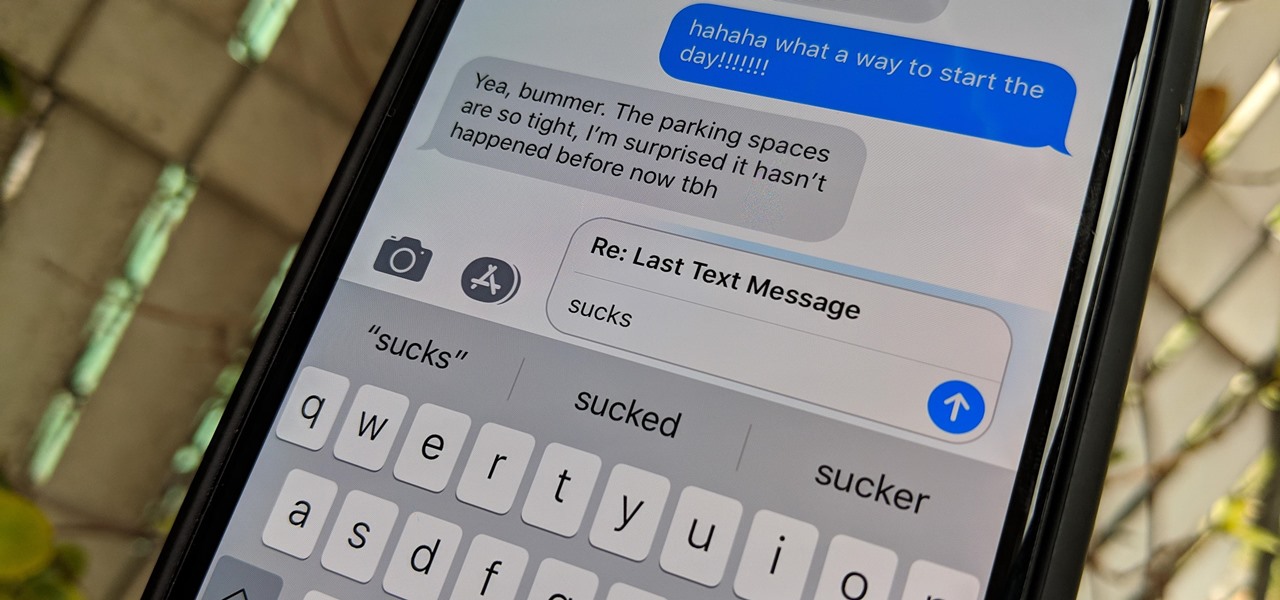
The subject line is a crucial part of an email, but you don't see it very often in texts. That's mostly because many people don't even know it can be done, and even if they do, why would they use it? Just like with emails, subject lines can make iMessages and SMS texts seem more important and more professional. Plus, they can help with organization and searching past messages, as well as make text bold.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

Location-based gaming company Niantic knows its business model is inextricably tied to the outdoors, so it is in its best interest to help preserve that environment to give players a place to play.

In a move sure to stir up even more speculation about the future of Snap Inc., the company's vice president of content, Nick Bell, is leaving the company after five years.

Samsung makes more than just the Galaxy S and Note series. With a large portion of the world not able to afford phones with flagship specs, Samsung makes several different series that focus on price. The latest is the Galaxy A6, a budget option with a flagship feature.

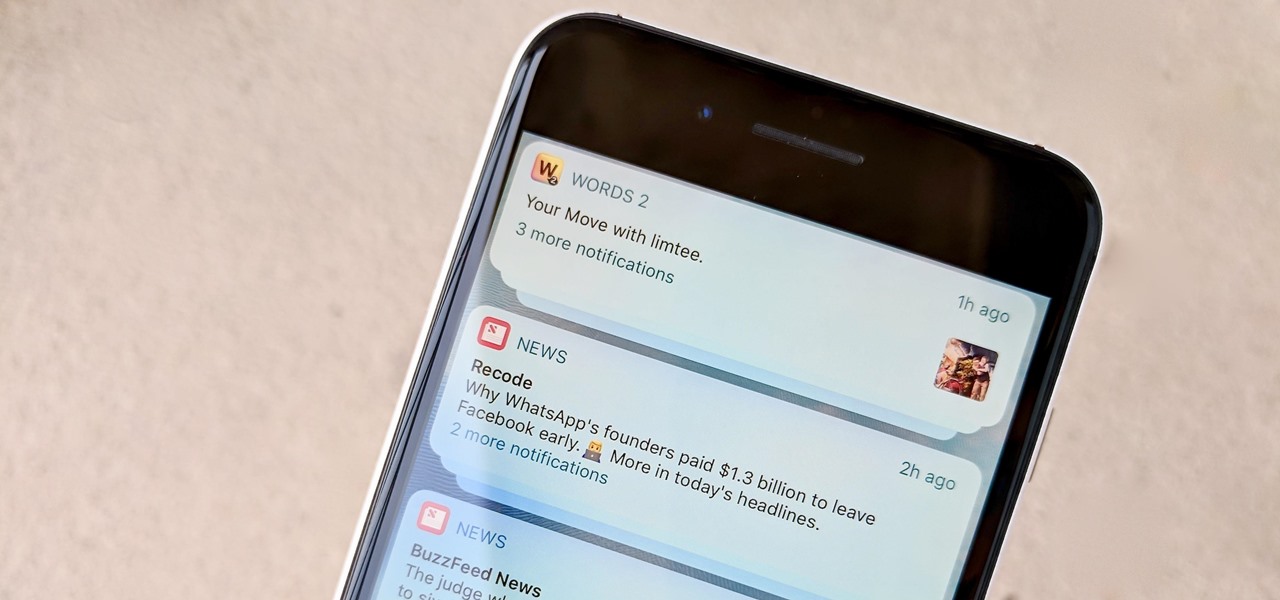
While iOS 11 was famous for its instability, performance issues weren't the only factor holding it back. The OS overhauled the notification system on iPhone, but not necessarily for the better. iOS 12, however, improves upon these changes, bringing critical features that make viewing and interacting with notifications on your iPhone on par with Android.

The mainstreaming of augmented reality won't happen overnight, but it's becoming increasingly clear that traditional media is leading the charge in the effort to introduce the public to immersive computing. A recent example came from none other than USA Today via its 321 Launch app.

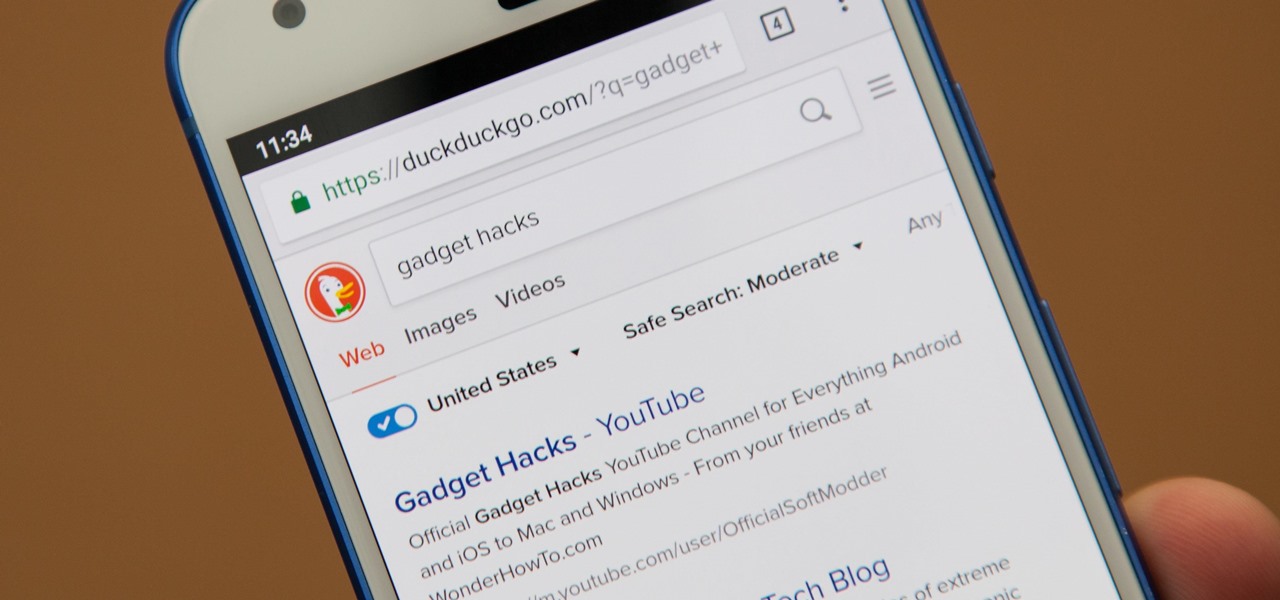
Even if your default mobile browser is Google Chrome, you may not want Google to also be your search engine. Maybe you're not impressed with Google's search results all the time, maybe you want a more private search experience, or maybe you just don't want Google's hands over everything in your life. Whatever the case, it's easy to switch from Google to another default search engine.

While it may seem to some like investors are just throwing their money at augmented reality companies simply because the tech is heavily hyped, these money managers do actually want to see a return on their investments.

On Wednesday, Scope AR, makers of Remote AR, the augmented reality video conference calling and remote assistance solution, announced that the app is finally available for HoloLens. Next Reality had a chance to talk with the founder and CEO/CTO of Scope AR, Scott Montgomerie, inside this new version of Remote AR.

During its third-quarter earnings call, Apple CEO Tim Cook said that "AR is going to change everything."

Meta Company has filed its response to allegations that the user interface for their augmented reality headsets infringe on six patents owned by a mostly-unknown company.