This is working about working with sources: Quotation, Summarizing and Paraphrasing. Quotation: When directly quoting an outside source, the author's words should be taken verbatim. Quotation can lend the essay credibility. Too much quotation makes it sounds like you, the writer don't have anything to say. Quotes should be used only when the writer needs to be precise, clear, and powerful. You should use the quotes when the person you are calling said in a unique way that really can't be put ...

In Boca Al Lupo: The end is almost here. This is the last mission you will need to complete. Talk to Mario and he'll send you on your final mission, to assassinate Rodrigo Boriga in the Vatican in Rome. The mission is more linear than any other you've done up to this point, and it requires much stealthiness. But at first, it requires you break into the Vatican. Climb the wall to the west and use the beams sticking out from the wall to jump to a hanging platform to the south.

Learn how to do hold a squat while doing a power single cable wide pull down. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do dumbbell squat thrust with speed alternate neutral presses. Presented by Real Jock Gay Fitness Health & Life.

If it's all you can do to drag yourself through the day, why not increase your stamina with these time-honored techniques. Watch this video to learn how to boost energy naturally.

Research shows that color can have a powerful effect on our emotions. Start harnessing that power today. Watch this video to learn how to improve your life with chromotherapy.

Othello, also known as Reversi, is played with two players, each representing a color on the board. The rules are simple, but strategy is what will help you win. Watch this video to learn how to play Othello or Reversi.

Watch this how to video and discover why induction cooktops are the hottest trend in the kitchen. These Home & Garden tips will help you decide on an induction stove that is right for you kitchen.

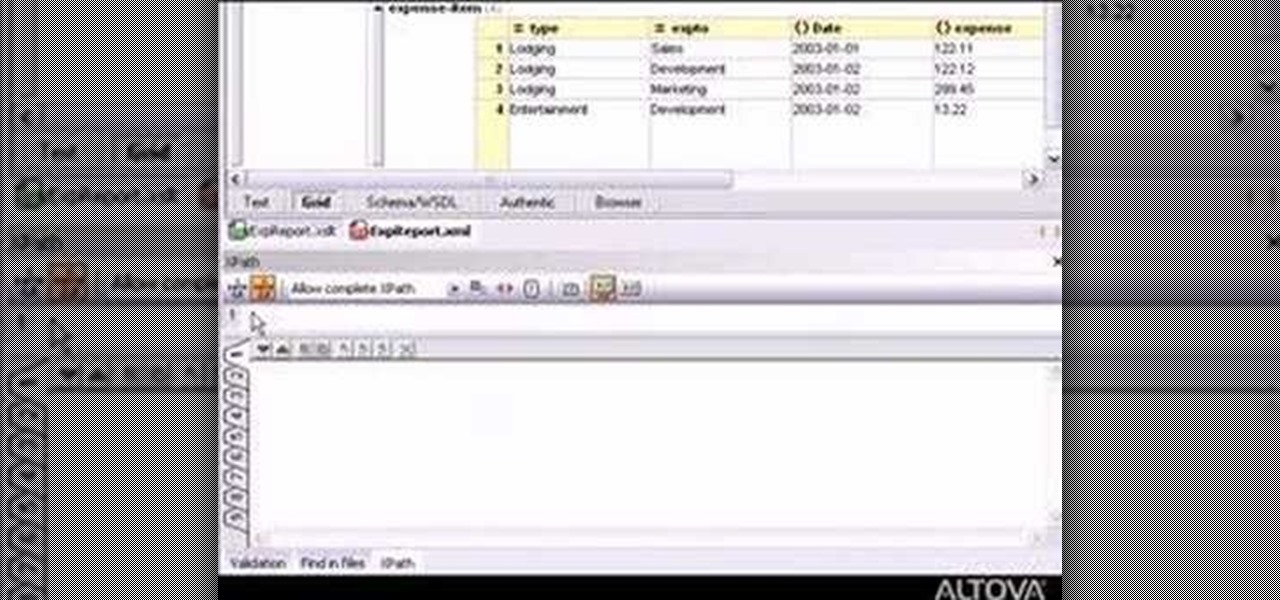
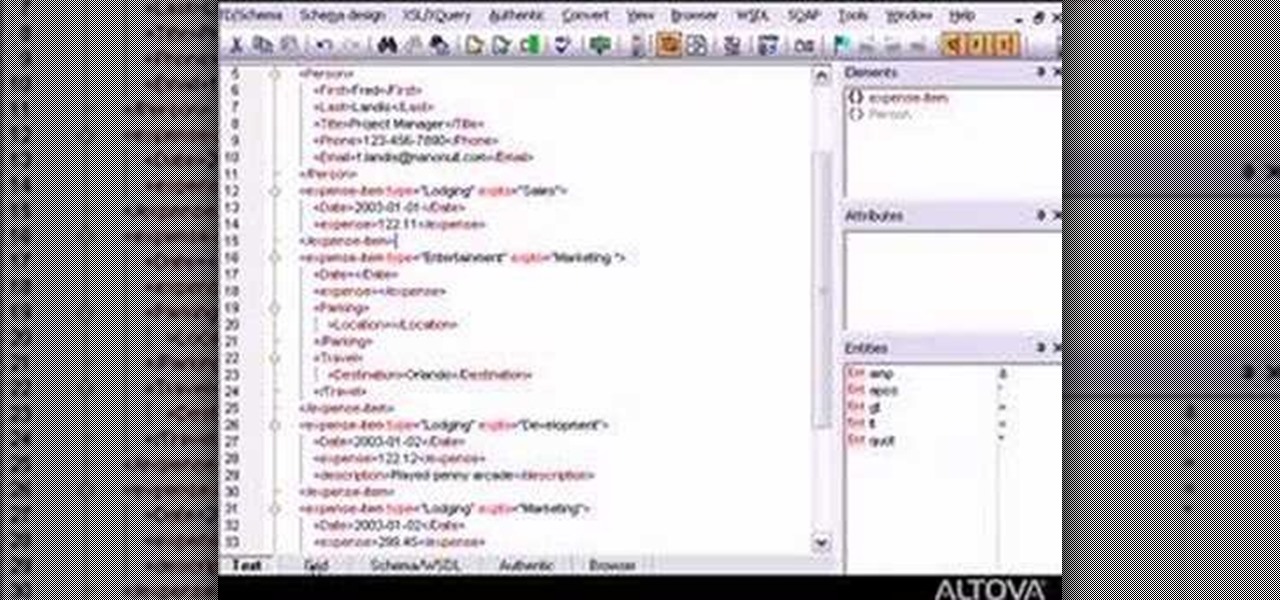
Desire to be an XML editor/programmer? This video will help you. You'll learn how to edit, analyze, and debug XPath expressions with XMLSpy.

Altova XMLSpy 2007 includes powerful viewing and editing tools that simplify the creation and editing of XML documents for your markup languages. This video will show you the general rules on how to use XMLSpy for XML programming.

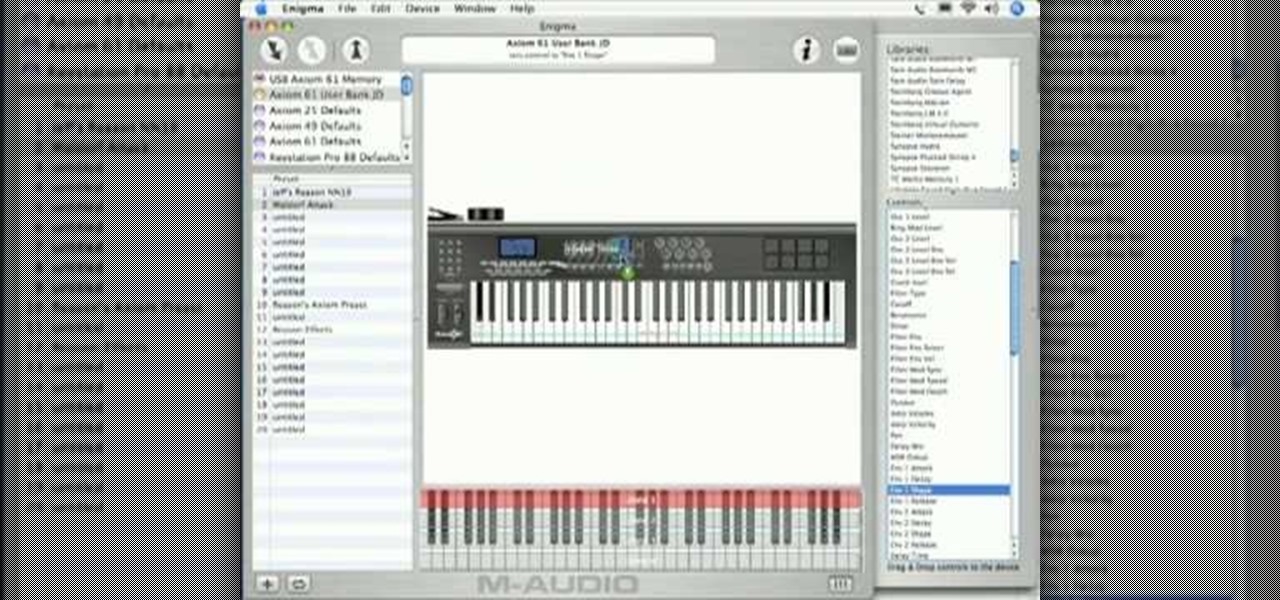
In this tutorial, Jeff Dykhouse demonstrates how to use the powerful Enigma Editing Software to assign MIDI message to all the different controllers that the Axiom 61 keyboard has at its disposal. Jeff covers: Downloading Presets, Creating User Banks and Loading and Creating Presets. You can use the Axiom 61 with Reason, Ableton Live, Pro Tools and even GarageBand.

A Mole wrench is a useful tool it has a powerful grip and is able to be latch-on to objects holding and gripping them hands free. This is a good tool for diy, do it yourself.

Is your computer's power supply on the fritz? Learn how to install a power supply in a desktop PC with these easy steps.Before we begin, you should know that many brand name PCs use specially designed power supplies. So, make sure you contact them directly before installing a new power supply. Also, an unplugged power supply still can give you a powerful electric shock by put something inside an open vent.

You don't need to work in the accounting department of a Fortune 500 company to use and appreciate Microsoft Excel. Although primarily associated with a wide variety of functions pertaining to accounting and finance, Excel is actually an incredibly powerful and multifaceted platform that can be found at the heart of many large-scale analytics environments.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

This week's Magic Leap Lumin OS update contained a number of goodies, including iris authentication, and a way to stream to Twitch from the device.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as gaming goes. Because of this, a lot of games once reserved for consoles and PCs have made their way to our smartphones.

Thanks to ever more powerful smartphones — the iPhone X with its advanced A11 processor and the Galaxy Note 8 powered by Snapdragon's 835 come to mind — the mobile industry is fast closing in on consoles and PCs with regards to gaming. Game developers have been aware of this fact, and have ported many games once dedicated to computers onto our handheld devices.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

Cartwheels are so much fun! Who doesn't love to twirl around? If you don't know how to do one of these fun moves, check out this video! Step by step, this tutorial will teach you how to relive your childhood or release your inner gymnast.

All of these four videos are excellent. You will notice that while all the videos and articles have slightly different design dimensions, they are fundamentally very similar. I urge you to view and read everything I am serving up. Then, my final words of advice are simply....choose between a barbeque switch and a taser gun. (Hint: there is a right choice, and there is a wrong choice.)

Google Drive has been a gamechanger in the business world. First launched in 2006, Google Sheets has become much more than an alternative to Microsoft Excel. The powerful spreadsheet program is a boon for efficiency that's accessible wherever you have an internet connection—or when you have time edit offline.

Django is a powerful Python-based framework that makes creating complex, database-driven websites easy to build and maintain. The free, open-source platform emphasizes reusability, the "pluggability" of components through APIs, rapid development, and less coding.

Data analytics is crucial to the operations of every modern business. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics. Experienced professionals that can project manage data initiatives are in high demand.

Linux has been one of the most popular desktop operating systems for nearly three decades, ranking fourth in the world behind Windows, macOS, and Google's Chrome OS. The open-source operating system is loved for its quick, powerful, text-based interface and efficient communication tools.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

Since its release back in 1988, Microsoft Office has been the top client and server software suite for businesses around the world. Office's domination is thanks to both Microsoft's extraordinary foresight and their continual updates and innovations to ensure that companies always get what they need.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

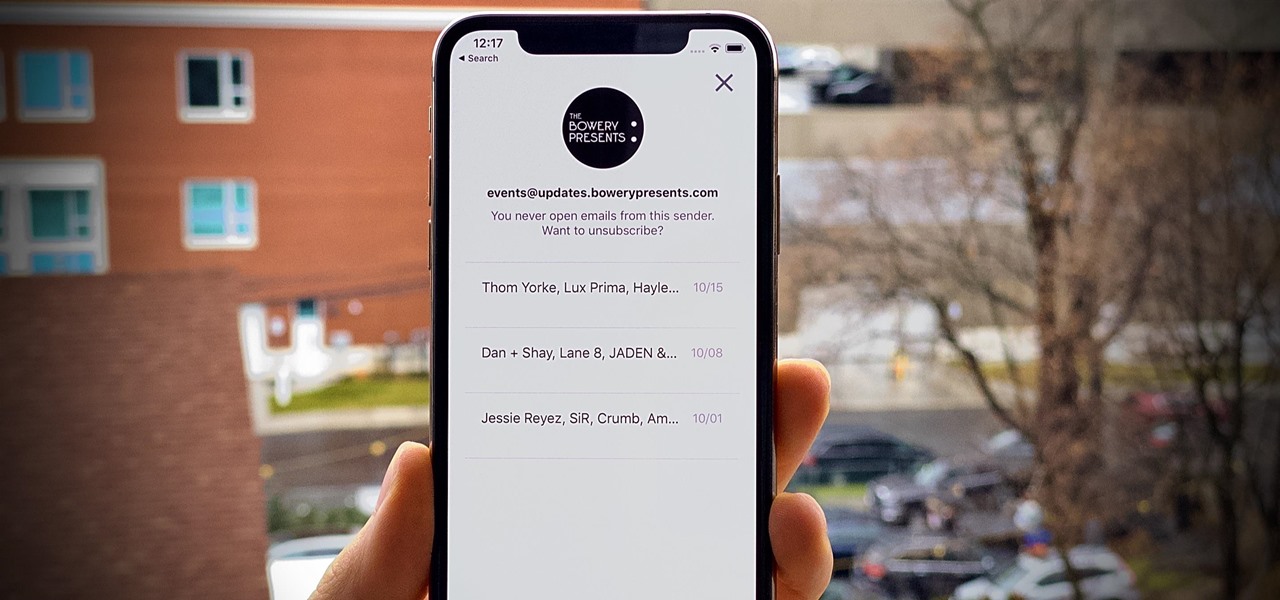
Edison Mail's big 1.17.0 (iOS) and 1.12.0 (Android) updates introduce a new, powerful Assistant to the mix. Aside from the fresh calendar integration and extensive customizability, you'll probably be most interested in the Assistant's unsubscribe feature. It helps to locate and cut down on your inbox's ever-growing jungle of spam. Here's how it works.