Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

While you may look ridiculous doing the potty dance and crossing your legs back and forth, holding it in can be worth the discomfort when you've got an important decision to make.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

Released last year for iOS devices, Frontback is a simple photo-taking and sharing app that not only snaps a picture of what's directly in front of the camera, but also behind it, which is to say, a selfie.
We've all heard our fair share of roommate horror stories, or have some of our own, because we never truly know who someone is until we've lived with them. Cohabitation issues generally revolve around things like bills, chores, cleaning, and groceries. Approaching a roommate, especially an adult one, to remind them to do their chores can be an anxiety-ridden and daunting task. After all, we're roommates, not parents!
Not particularly good looking, TouchWiz's lock screen adequately supplements the clunky and almost cartoonish-look of the infamous user interface on the Samsung Galaxy Note 2. While there are hundreds of lock screen options in the Google Play Store, I've never quite discovered one that I've thoroughly enjoyed, due to the obfuscation from so many options.

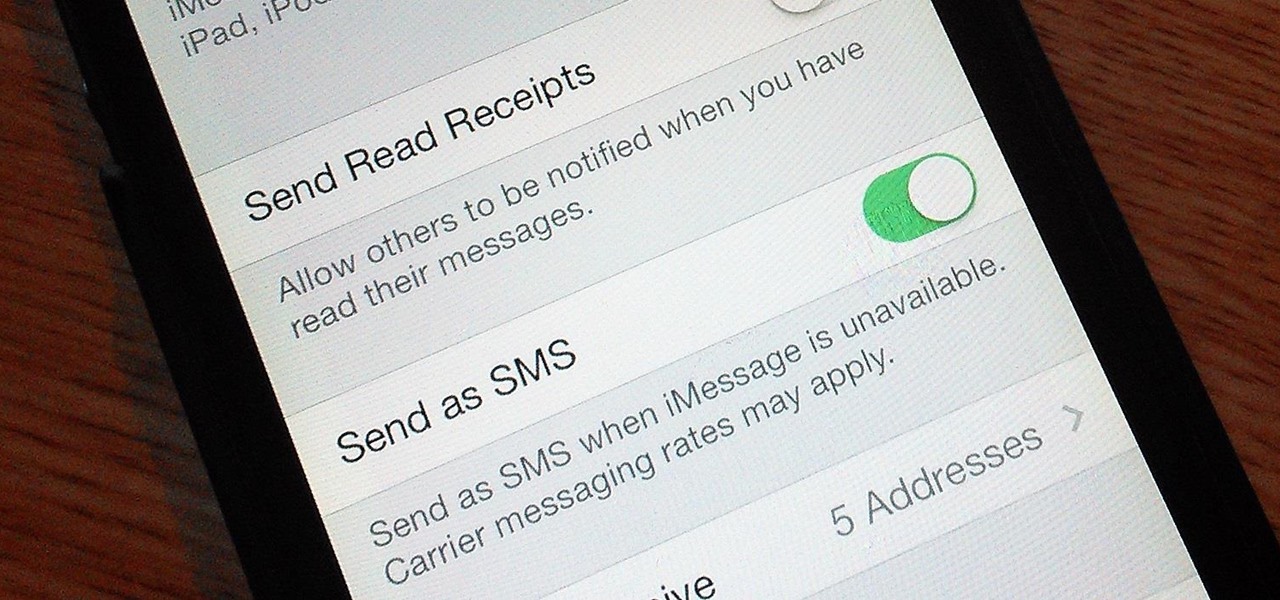
If you're an iPhone user, iMessage is great for cutting down on SMS costs from your carrier, but it doesn't always work right away.

According to WitsView, 8-inch displays will rule the tablet scene this year at 11.9% market share, compared to yesteryear's 2.6% market share. By year's end, it'll be almost 18%.

We frequently associate plastics with the modern era, starting at around the 1950s with the prevalence of bakelite. However, for all of you "you can't use plastic in Steampunk" purists out there, I have bad news for you:

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

There are only few steps to find the area of the triangle in a simple method. First you consider a triangle, and to find the area in a simple manner just add the triangle of same properties and side lengths as same as the first one and attach to it. Then we know the formula to calculate the area of the square. Then find area of the square by side*side. Then you will get the area of the square, now divide the area by two, as we add another triangle. Then the area of the triangle will be obtain...

If you want a challenge, try this at home or anywhere. Learn to spin a book on your finger. This will make you enjoy more of your vacant time. It also helps your balancing skill developed. 1. Get a book. 2. Get your finger to the center of the gravity of the book. 3. Spin the book on your finger. 4. As the book spins, your finger gets outside of the center. 5. Try to get your finger back to the center and you can do that by moving your hand in a linear circular manner. 6. Keep practicing by s...

This video demonstrates how to fold a fitted bed sheet neatly. For this, first spread the bed sheet on a flat surface like a bed. The outside of the bed sheet should be facing down and the inside should be facing up. Make sure all the corners are visible. First take the right corner over your hand like a puppet with the inside facing out. Then take the left corner over your hand in the same manner with the inside facing down. Repeat the same with the other two corners of the bed sheet. Once y...

With careful wording you can avoid lying and still avoid going to something that you just don’t want to attend. Even without a good excuse you can politely decline without hurting anyone’s feelings or ending up in an embarrassing situation.

You've uncorked a bottle of fine wine. Now what are you supposed to do with that cork? Don't just throw it away! Breathe new life into your old corks by recycling them into all-natural coasters.

In this video you will see how to apply butter cream frosting to a large circular cake for a wedding or for any occasion that calls for a fantastic cake. You will need a lot of frosting and an adequately sized smoothing tool. It is very helpful to have a platter that turns to get smooth, uniformed edges to your cake. Dipping your tool in a glass of warm water will allow for a more refined smoothing ability. You will use dowel rods placed through the cake to support the following layers. Frost...

To create a simple game in flash select the first frame and open the action bar where you will write "stop[];". Next you will make a start or begin button. Convert this button to a button. Then you can open the action bar and write "on(release) {gotoAndPlay(2)}". Afterward use F7 to insert a blank key frame and turn on onion skin. Next draw a path starting from the (onion skin) Begin button, make sure to draw the outer lines too, then color the area outside your path. Convert the colored area...

It might not be on the top of your to-do list but activating your Windows XP is simple and only takes a moment. No need to put it off any longer. You just need your product key and your computer and your ready to go.

Gather your hoop and supplies. Wrap the suede evenly around the entire ring. Wrap it either eight or sixteen times, depending upon your preference. Glue the ends to the hoop. Secure them with a clothespin until the glue dries. Make the web. Tie the nylon string to the suede. Make eight knots evenly dispersed around the ring. Keep the thread taunt between knots. Make a second row. Place each knot "between" the knots of the previous row. Continue in this manner until a small hole remains in the...

Coders are accustomed to working remotely. The beauty of coding is that all you need is a laptop and a WiFi connection, which makes working anywhere a fairly simple transition. If you're looking for a career change, now might be the perfect time to give coding a try.

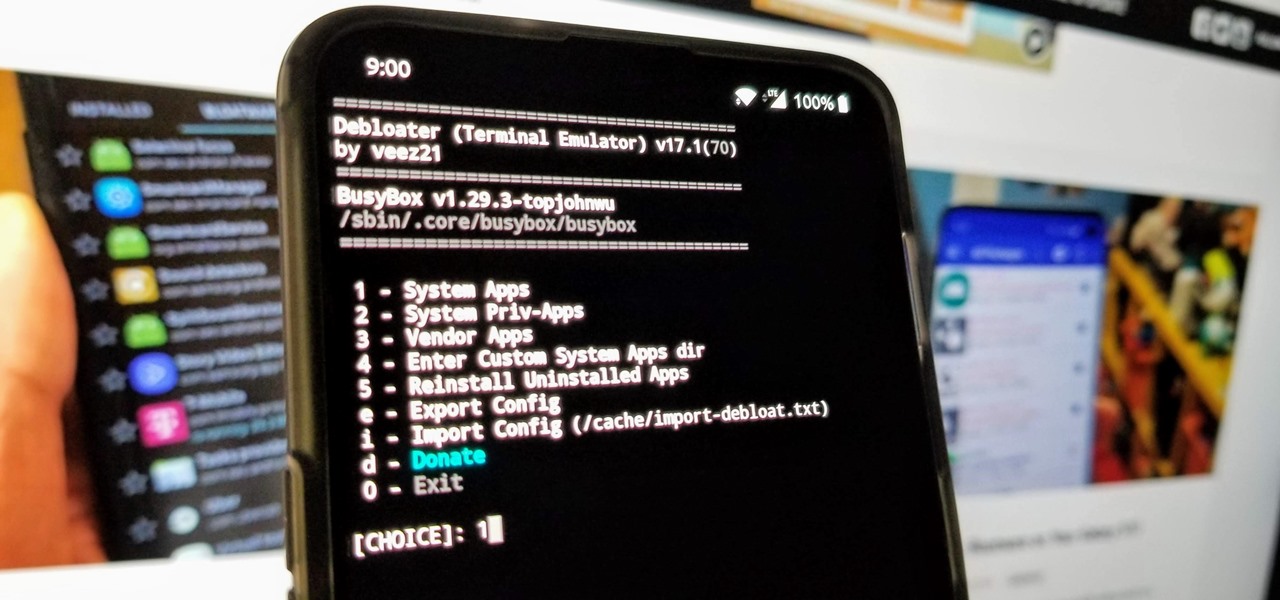
When you get a new phone, the last thing you want to deal with is a ton of preinstalled programs staring back at you. They not only clutter your home screen with apps you'll probably never use, but they're also wasting space on your internal storage and potentially draining battery. To truly uninstall them, you'll need root — but even then, it can be hard to pin down all the apps that should be removed.

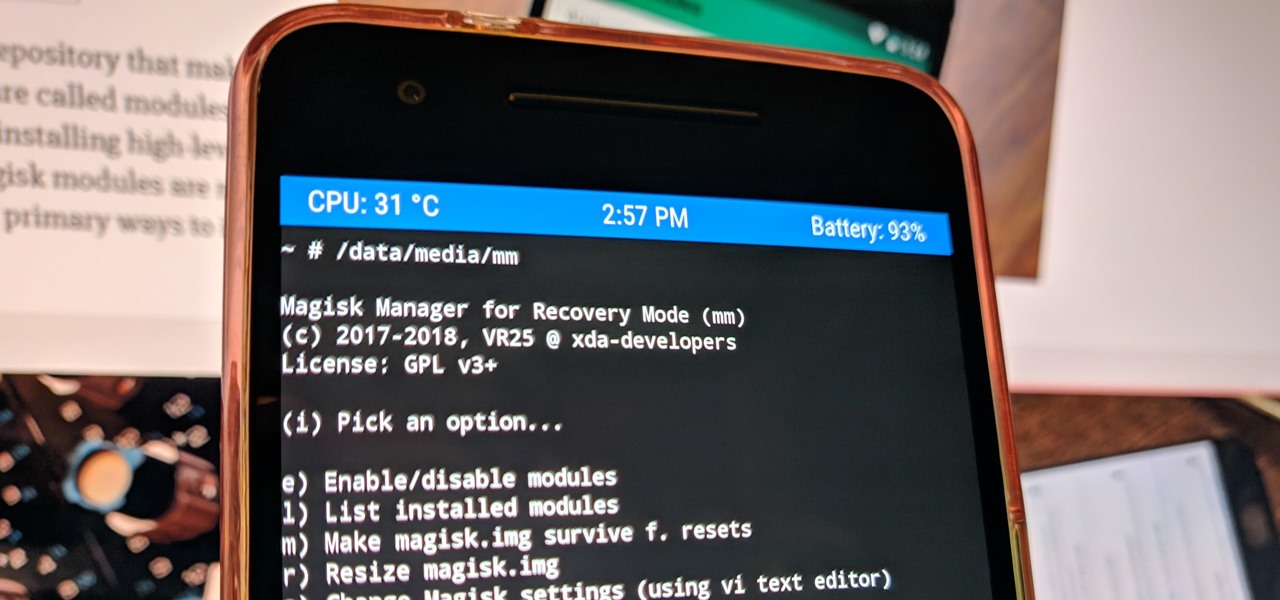
When it comes to customizing Android, there's nothing quite like Magisk. You can potentially combine dozens of modules to create a one of a kind user experience tailored to you, but not all modules will work well together. You might run into a bootloop by accident once in a while, which could cause some issues on its own.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

With this year's iPhones, Apple built upon the success of the iPhone X in a somewhat iterative manner. All three phones borrow from the 2017 flagship's design, which many praised as being the best in years. They also tried to help those of us who don't have more than a grand to spend on phones, creating a new product with a few compromises.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Action Launcher has some exclusive features that add real value to your overall experience. One such feature is Shutters, and like with most aspects of Android, there's a workaround that will let you enjoy this functionality on other launchers.

Unscheduled pit stops go hand in hand with road trips, no matter how well-planned they are. In the past, making a stop due to low fuel or an emergency bathroom break may have snowballed into massive delays when you went off course on your own, but thanks to a feature in Apple Maps, you can do this in the most efficient manner possible.

When you run an augmented reality company worth billions of dollars, backed by some of the biggest names in tech, and you haven't even released a product yet, even late night tweetstorms rank as worthy of dissection. Such is the case with Rony Abovitz, CEO of Magic Leap, who decided to spend a little time on Twitter on Wednesday to outline his vision of the future of immersive computing.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Cholera may be rare in the US, but cases of the disease have increased worldwide since 2005, particularly in Africa, southeast Asia, and Haiti. An estimated 3 to 5 million people are infected, and more than 100,000 die from the disease globally each year, mostly from dehydration.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

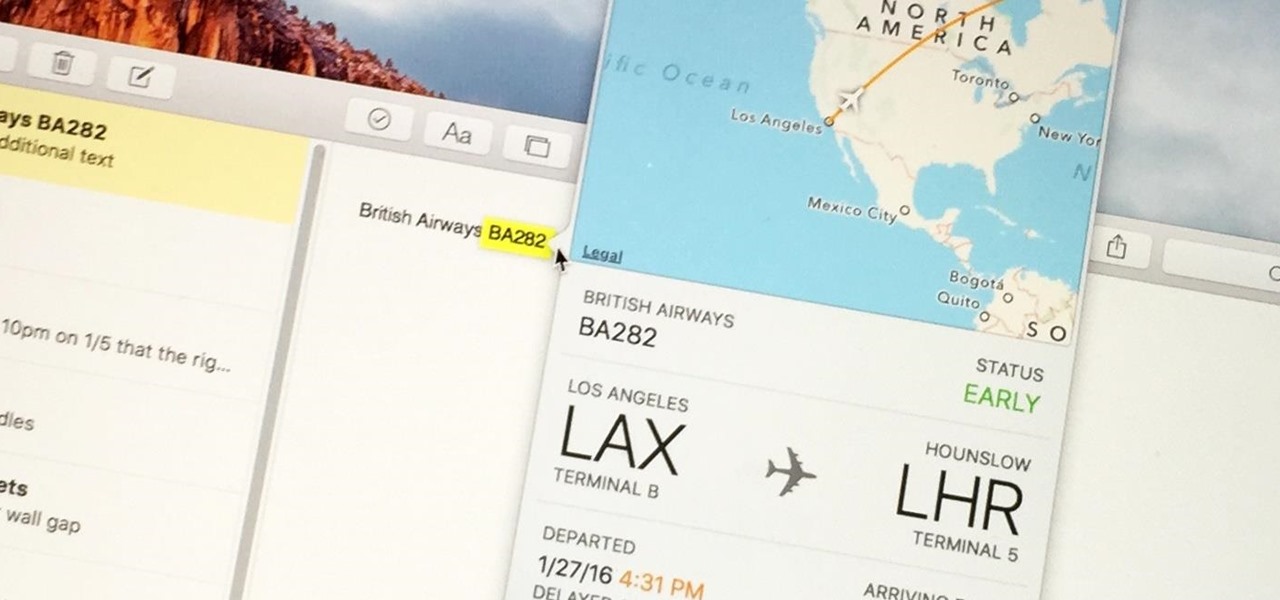
Turns out, you no longer need third-party flight tracking apps to get information on yours or others' flights—your iPhone and Mac can now give you flight details right from your Mail, Notes, and Messages apps.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

By now, a mobile phone that isn't "smart" is about as hard to come by as a TV that isn't high definition. As a result, members of older generations who were previously reluctant to purchase a newfangled smartphone have no other choice but to cave into the more recent trends when their old device finally breaks down.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Out of all the questions that we receive from our readers and viewers here at Gadget Hacks, the most frequently asked one is "What wallpaper is that?" On occasion, our wallpapers may be personal or images from the web, but for the most part, they come from dedicated wallpaper apps.

Whites are the hardest color to keep looking bright and new after just a few months' time. Your sweat and oils quickly become stains, and colors from other clothes will eventually bleed into the fabric, discoloring your bright whites into something merely whitish. But before you reach for the bleach, the ultimate chemical cleaner, try some a few of these safer, less-toxic DIY solutions out instead.