Architects are natural candidates to be early adopters of mixed reality. Their trade consists of not only designing buildings and spaces, but also presenting those designs to clients, who then decide that their vision is worth spending thousands (if not millions or billions) of dollars to build in reality.

As summer mosquito season approaches, researchers are warning people with previous exposure to West Nile virus to take extra precautions against Zika. A new study found that animals with antibodies to West Nile in their blood have more dangerous infections with Zika than they would normally.

It has become hard to decipher where your digital imprint ends and your true self begins in today's tech-dominated world. Scrolling through news feeds and endless updates is not conducive to a good night's sleep, nor does it help you lead a well-balanced life.

If you have a HoloLens, you can now control the lighting throughout your home or office via holographic controls using the free Hue Lights app in the Windows Store. The app, made by California-based AfterNow, works with the Philips Hue colored lighting system and is much more polished than the prototype we saw in January.

One thing you'll find a lot of in the Windows Store for HoloLens is demos and mockups, but very few projects are as fully realized and fully-functioning as Muralize. Created by Magnopus, an all-female development team, Muralize first appeared in the Windows Store in late-November of 2016, and makes it easy and fun to create real-life murals using a HoloLens.

To some people, Thanksgiving is merely quality time with family and friends that they can't get throughout the rest of the year. To others, it's that one time when it's okay to be a greedy hog and get hammered all weekend long.

Before the iPhone 7 was launched and all the unrealized reports about the phone's features were tucked back into their annual rumor mill, there was some speculation about wireless charging. Specifically, whether or not the iPhone 7 and 7 Plus would support it. We now know they don't, and here's why.

What happens when a entrepeneur/theme park creator and special effects artist/magician team up? You get a team crazy enough to create the first true virtual reality theme park (sorry, Six Flags). They only have a single experience so far, but it's already taken a giant leap beyond the wonders we've seen in today's consumer virtual reality headsets.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...

The future of augmented and mixed reality offers many possibilities, mostly because we're still figuring out everything it can do. While Meta is open to exploration, they've spent a lot of time thinking about what the future of this technology will be.

The reality of tomorrow will not be static. We're here to bring you a daily look into the cutting edge innovations poised to merge the impossible worlds of our imagination with real life. We're NextReality.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Welcome back! Sorry for the dry spell, but I've been rather busy setting up some side projects! If you remember back to a few training sessions ago, we covered basic file I/O. This is a very important step in making our scripts applicable in a real life scenario, and today we're going to further these concepts.

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

Please read the following in Rod Serling's voice. Picture, if you will, a mother. She comes home after a long day at the office, relieved that she took some chicken breasts out to thaw and will be able to make a quick and easy dinner for her family. She opens her refrigerator to get the chicken, but to her horror she does not see it… she forgot to take the chicken out of the freezer after all. What will she make for dinner now? How will she feed her family? She has entered…the Panic Zone.

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Well, first things firsts, it's been awhile! I'm sorry the series has been dead for a little bit, but I recently hit some personal relationship issues and needed to take some time to think. But, now that it's all said and done, the dust can settle and we can start training again!

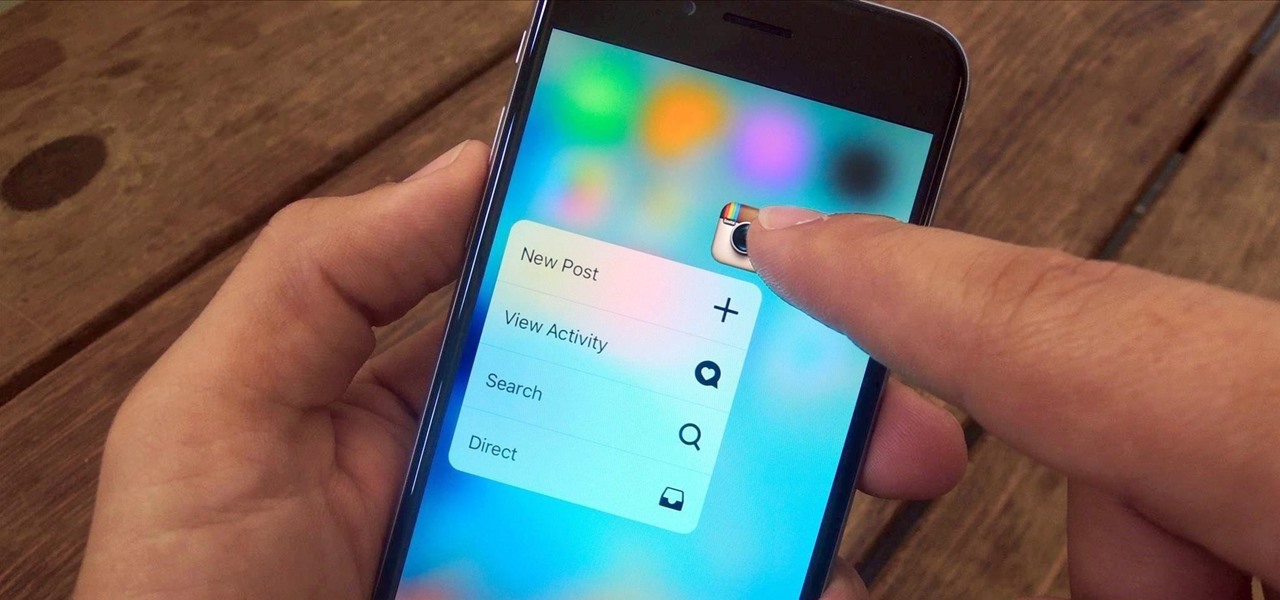
3D Touch is a new feature on the iPhone 6S and 6S Plus that's reinventing the way we interact with our smartphones. With just a little bit of added pressure when tapping on the display, you can perform Quick Actions from an app's home screen icon, "Peek" at emails, stories, and photos in-app, as well as perform other app-specific gestures. Since 3D Touch is such a new concept, here are some of the apps that currently support it, along with the shortcuts you can use.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

When I get struck by a craving for something SCJ (savory, crunchy, juicy), nothing fits the bill better than a BLT. But why settle for the sandwich form when there are so many other possibilities? Some of my favorite alternative ways to serve up a BLT are 1) as a salad, 2) in tomato cups, 3) in mini bread bowls, 4) as lettuce wraps, 5) as a dip, and 6) in bacon cups.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Now that the Super Bowl is over, you might find that you have an econo-sized bag or two of opened potato chips slowly going stale in your pantry. After all, there are only so many bowls of Buffalo Chicken Pizza Beer Dip you can eat with 'em—and you definitely don't want them to get so old that you have to throw them out.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

When a Houston mom got tired of her kids seemingly refusing to return her calls, she decided that she'd take action. Sharon Standifird's vision was to create an app that would somehow force children to get into contact with their parents. Having no experience with app development, Standifird quickly taught herself the ropes and hired an experienced developer to help with coding.

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.