Around this time in 2016, the predictions for the next year had reached something of a consensus: 2017 would be the year of augmented reality. But a funny thing happened on the way to the future — nothing much, really. At least not for the first half of the year.

The augmented reality industry made great strides in 2017, but its apex is not even in sight. In terms of software, augmented reality is approaching meaningful mainstream awareness, thanks mostly to Apple and ARKit. Meanwhile, on the hardware side, AR is very much in its infancy, with headsets mostly limited to enterprise customers or developer kits and the majority of smartphones lacking the sensors necessary to achieve much more than parlor tricks.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

With their first attempt at the mobile market, Razer introduced a device that looks at the smartphone differently. Instead of focusing on minimal bezels or an amazing camera, Razer decided to make a phone for gamers. So how could Razer target the growing mobile gaming market, which is projected to generate $40.6 billion in global revenue in 2017? It starts with the IGZO LCD Display.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

If you're in the market for a new smartphone, you'll likely scan spec sheets and read reviews of the top phones, compare display size and technology, RAM amount, and processors. But one factor that is often overlooked is cell reception — and for T-Mobile subscribers, there's only one device that has flagship specs and an exclusive antenna that will actually improve your signal.

With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as gaming goes. Because of this, a lot of games once reserved for consoles and PCs have made their way to our smartphones.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

Apple demonstrated their continued interest and investment into the awesome world of augmented reality during their Sept. 12 event, highlighting a few new AR games that will appear on iPhones thanks to ARKit. But that's not all you can expect — as long as you have an iPhone with an A9 chip or later, there will be a ton of cool new AR tools, games, and other apps to play around from the App Store.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

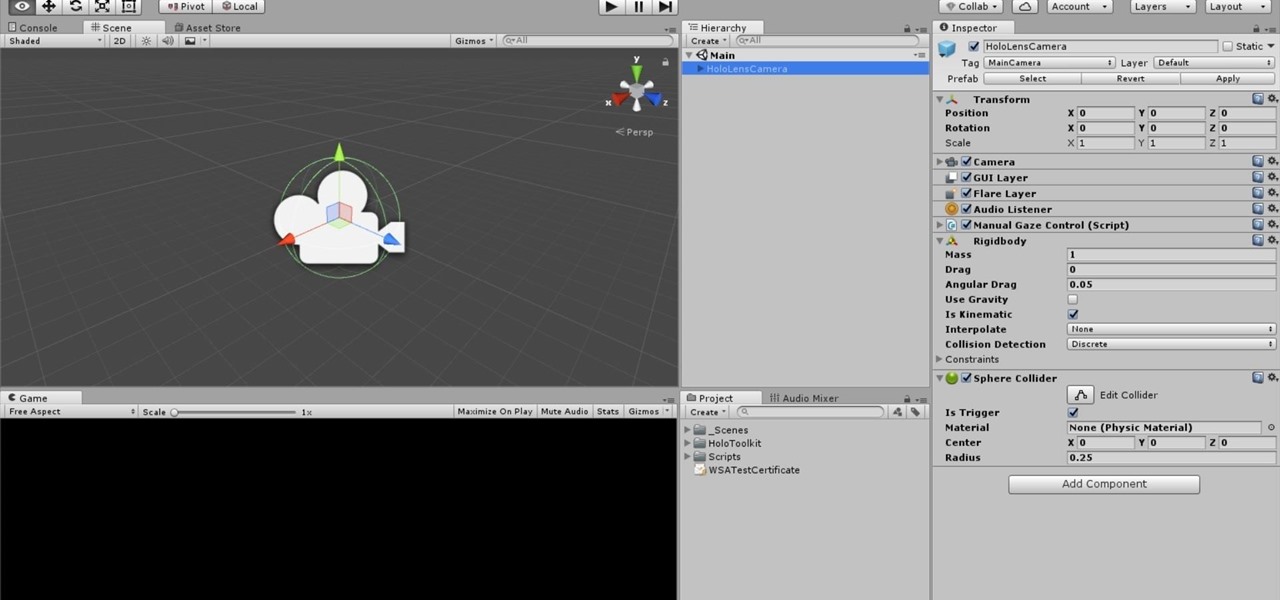
One of the truly beautiful things about the HoloLens is its completely untethered, the-world-is-your-oyster freedom. This, paired with the ability to view your real surroundings while wearing the device, allows for some incredibly interesting uses. One particular use is triggering events when a user enters a specific location in a physical space. Think of it as a futuristic automatic door.

It's that time of the year, y'all—when the air becomes crisp, the nights grow long, and people crave hearty, warm soups and stews. And of all the season's offerings, my hands-down favorite has to be chili: It's versatile, meaty, and above all else, it's damn easy to make. (Thank you, Lord, for the slow cooker. Amen.)

YouTube's massive user base comprises almost one third of all people on the internet, and collectively, users spend well over 100 million hours on the site watching billions of videos each day. Add it all up, and this means that YouTube is viewed by more people than any U.S. cable network—making it by far the favorite "TV station" of the internet generation.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

Don't believe what you read on the internet, especially today, when web giants like Amazon, Google, and the like showcase their otherworldly products and services. If they seem too good to be true, they probably are—but that doesn't make them any less fun.

Ironing is a serious chore: hot, unpleasant, and frustrating all in one, but necessary if you don't want to look like you crawled out of bed just before work. While you might only turn to your flatiron when faced with wrinkled clothing, this little appliance packs the power to tackle even greater challenges—and here are our 10 favorites.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

Although your friends might roll their eyes every time you talk about playing Clash of Clans, Call of Duty, or Candy Crush Saga, your excessive gaming habits might actually be making you healthier than everyone else.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

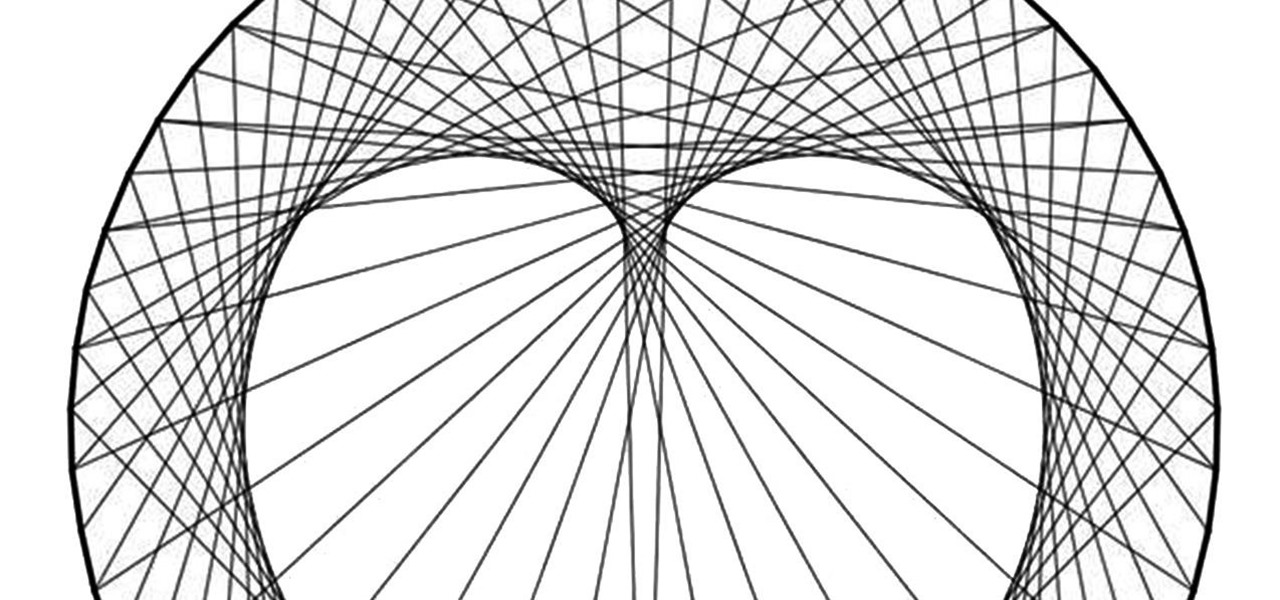
Using only a circle and straight lines, it's possible to create various aesthetic curves that combine both art and mathematics. The geometry behind the concentric circle, ellipse, and cardioid dates back centuries and is easily found in the world around us. From an archery target to an apple, can you name these geometric shapes?

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

In a double-stuffed episode of Scam School, you'll learn how to fake ESP powers — a diabolical method to fake telepathy between you and a friend — and see a mind control trick from outer space with Scam School's first intergalactic student!

Using different sounds on your iPhone for different notifications can help you determine — just by listening — alerts you may want to look at immediately versus untimely alerts or even ones you typically ignore. But Apple has never given us complete control over notification sound customization on iOS, though the latest iOS update is a step in the right direction.

Now that Vision Pro, Apple's mixed reality headset, has been announced, Apple can free up some R&D resources to commit to its upcoming foldable iPhone, which has been rumored for just as long as Vision Pro has. Will it be a flip-style or a larger foldable? Let's see what all the industry experts and Apple leakers have to say.

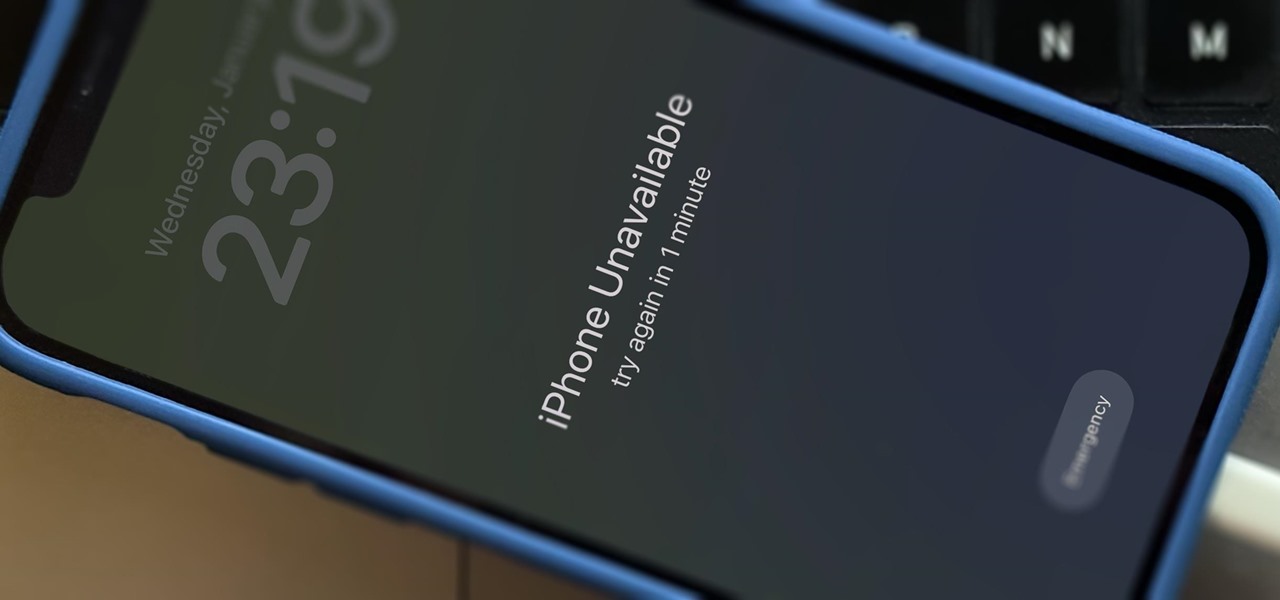
There's only one thing keeping hackers, thieves, law enforcement agencies, and maybe even the people you thought you could trust from breaking into your iPhone should they ever get possession of the device. Their odds of bypassing that thing are pretty good, but there's an easy way to make it an almost impossible feat.

You can wake up to ringtones, music from streaming services, or downloaded audio files when setting alarms in Google's Clock app for Android, but that's not all. The latest feature lets you turn your own voice into an alarm sound, saying whatever it is you need to say to wake you up.

When it comes to the ever-shifting sands of the augmented reality space, you never know which week will end up being truly historic. Well, this one was one for the history books.

Ever since Facebook announced its partnership with Luxxotica brand Ray-Ban to produce smartglasses, the augmented reality space has been on high alert awaiting more details.