Make the most out of your cosmetic brushes by cleaning them regularly. Wet your cosmetic brush. Take a small amount of a natural shampoo in the palm of your hand and make circular motions with the brush . Rinse the brush under running water, continuing to make circular motions in the palm of your hand until the water runs clear with no bubbles. Don't allow water to extend past the bristles. Gently squeeze the bristles to remove excess water. You can also use conditioner to condition the brush...

This short video tutorial Bob Schmidt will show you how to make clean cuts in wood. The blade rotation of any pretty much dictates the best way to run your material through. To get the cleanest cut possible remember these tips: Whenever you run wood through a Table saw, always make sure that your finished side is up. Do the exact opposite when you are using your Power saw. The finished side of your wood must be at the bottom. When you use a Mitre saw, make sure the finished side of the wood i...
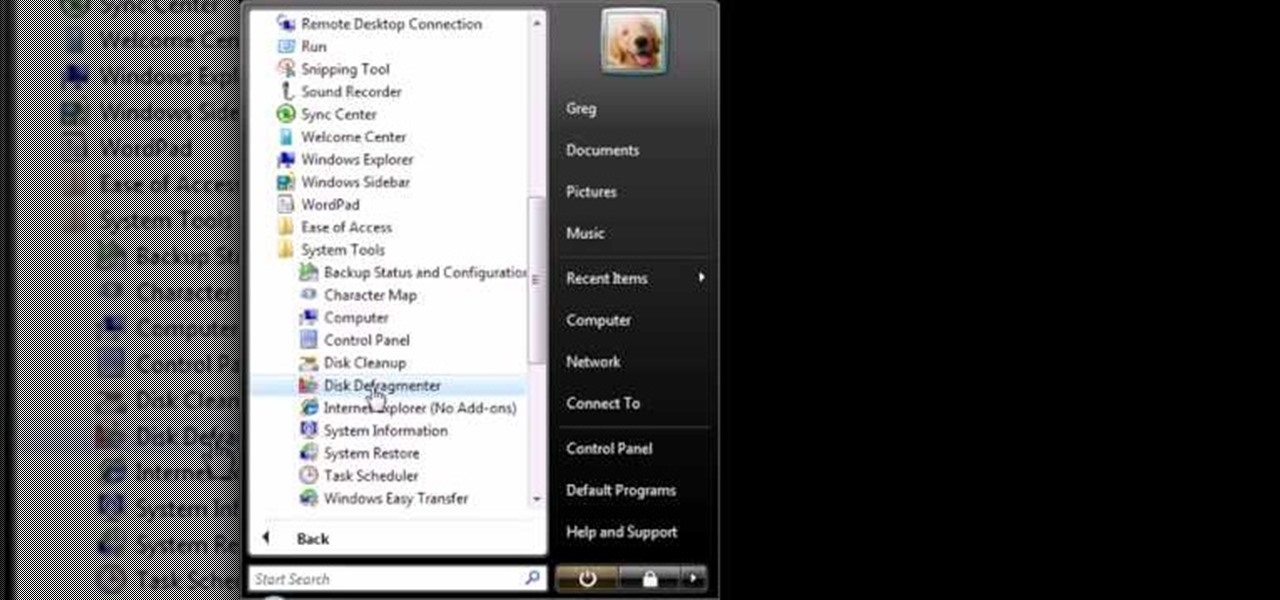
The thenewboston shows you some short tips on how you can speed up your computer. He is using the Windows Vista Operating System for the demonstrating. He says he believes it should also work with Windows XP. The first thing that he says to do is go to your start panel and then go to "All Programs" then to "Accessories" then click on Disk Cleanup. After watching this video and performing the steps, your computer should run faster then what it is running at now.
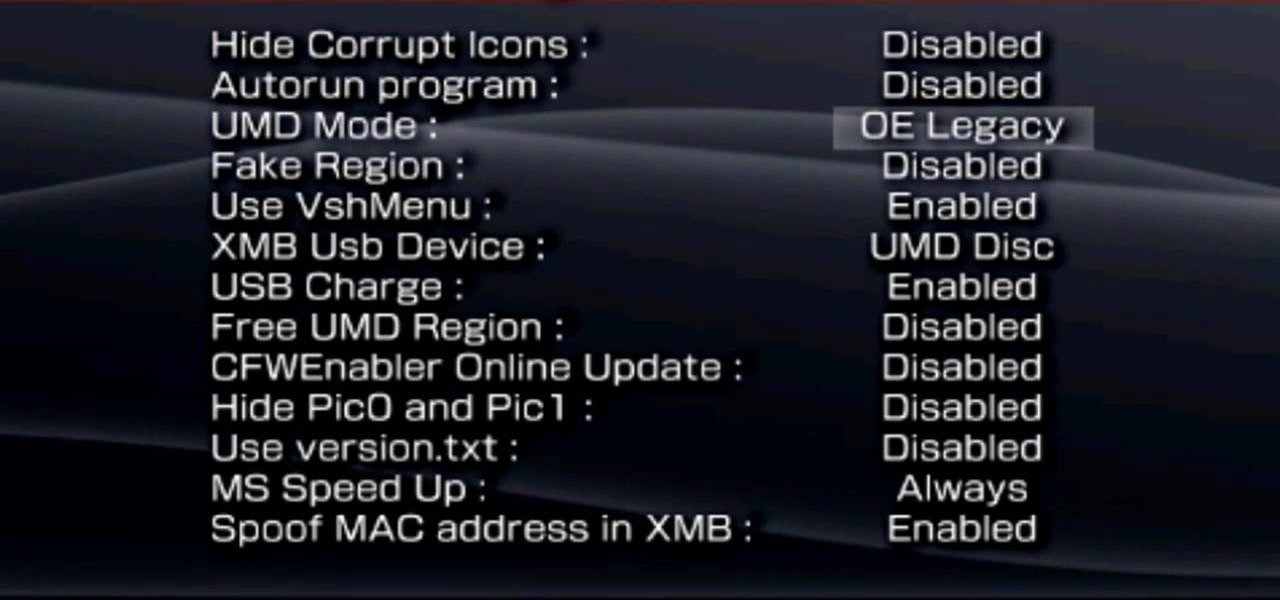
Did you know that you could make an ISO or CSO image of your PSP UMD and then run it off your memory stick. This solves space issues and the games even run faster! What you need to do is first go to the root of your memory stick and make a folder called 'ISO". Put the ISO that you've made from your UMD into this folder and then startup your PSP. In the PSP menu go to 'GAME' and then launch the custom firmware enabler. Inside go into the settings menu and into configuration and change the UMD ...

If you want to learn how to block websites in Windows, just follow these few simple steps. Watch this video for more information!

This video will instruct you step by step on how to style side hair spikes. Starting with a straightening iron you ensure all hair is as straight as possible. Once done you would apply hair spray where you want the spikes to be. Then you run your fingers up through your hair to get your hair to spike. Continue running your finger up through hair until the hairspray begins to dry and the spikes stay. Apply more hairspray as needed to make sure they stay. Very quick and easy to follow way to cr...

A frozen pipe doesn’t have to mean major trouble. You can keep your water flowing all winter long. You Will Need

To be the best at the Madden NFL video game, you have to be willing to get advice, but not just any old advice... professional advice. To beat everyone, you have to be ruthless and know all of the strategies and gameplay tricks. To master Madden 08, check out this quick, football game, video tip from Madden Nation (EA Sports and ESPN) with video game pro Charles James (or Chuck Hollywood).

Your car needs care and maintenance to run properly. Let Firestone Complete Auto Care teach you the basics about keeping you automobile running smoothly. Check out this video tutorial for some helpful hints on maintaining the windshield wipers on your vehicle.

Your car needs care and maintenance to run properly. Let Firestone Complete Auto Care teach you the basics about keeping you automobile running smoothly. Check out this video tutorial for some helpful hints on maintaining the belts and hoses in your vehicle.

If you have a new Mac and run OS X, you probably already use your Apple Remote for your photos, music and movies. But did you know you can use it for your Keynote presentations as well? While running Keynote, press play to begin the presentation, use the forward, or back, buttons to move between slides, and use the up and down buttons to raise or lower the volume. To put your computer to sleep, just hold down the play button. For a video demonstration for each of steps, watch this OS X tutorial.

In this tutorial, you'll learn how to use the emacs text editor, accessible through the terminal on any computer running Mac OS X, to play a simple version of Tetris. The steps are simple and as follows:

Take a look at this instructional video and learn how to load virtual console games onto your Nintendo Wii. You'll need the Twilight Hack and an SD card for this process. The Twilight hack allows you to run unofficial software through the SD (Secure Digital) card inserted into your Wii. Since the Twilight hack was found through the lastest Zelda game Twilight Princess, the game needs to be loaded every time before you can run any "homebrew" software.

Take a look at this instructional video and learn how to run a USB cable through existing phone cords. You'll need two phone jacks, a USB extender, and a phone cord. Although dual jacks are featured in this video tutorial, single jacks are preferred. The process is fairly simple, what you need to do is open up the jack and cut the USB extender in half. Strip to the multicolored wires and match up the the wires with the opened phone jack's, all except for the white wire which will go to the ye...

This is the first live action run of the Tesla CD Turbine II with simple hi-speed CD Disc Pack. This particular model of the CD Turbine has no magnets, as well as no shafts, no bearings, no seals and no blades.

This is a running demonstration of the water-pressure powered Tesla CD Turbine III and Magnetic Coupler, running smoothly and safely at up to 1000 rpm at the sink. The CD Turbine is made from recycled CD's and neodymium magnets.

For right-handers, work from right to left or top to bottom. For left-handers, work from left to right, or top to bottom. Bring the needle to the front of the fabric at A, and pull the thread through. Now, for the rest of your stitches, you can work them more quickly if you "run" them on the top of the fabric, without taking your hand to the back. Go down at B, and, using your fingers on your non-dominant hand (the one that's not holding the needle!) behind the fabric, encourage the needle to...

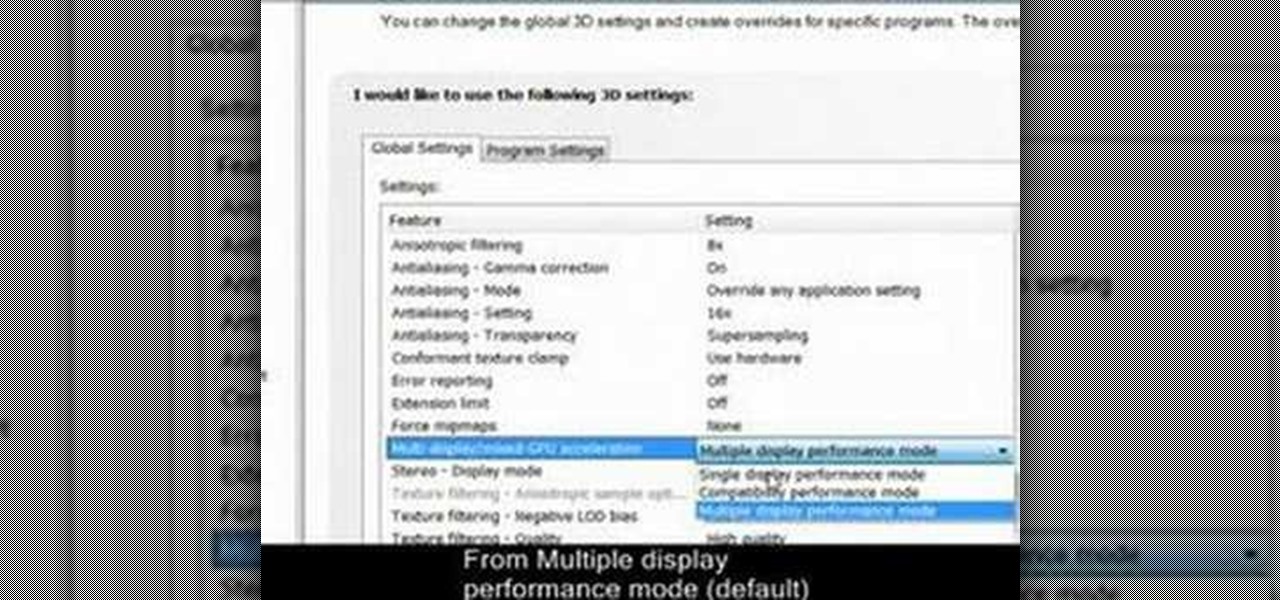
Single-display performance mode: If you have only one active display, this is the setting for you. You can also specify this setting if you have problems with the multi-display modes.

Installing Joomla on a Windows server can be tricky, on Windows running IIS even more so. Installing Joomla 1.5 in this scenario has caused many frustrations.In this video, we take the process step by step and jump over the hurdles that cause some people to wind up pulling their hair out. If you follow along closely, you will be up and running in no time, and if you haven't already tried to do this, you will wonder why people find it so difficult. There are some prerequisites to the steps in ...

This is an instructional video for and by a beginner ukulele player. It goes over the tuning, chords, and strumming pattern for one possible way to play "Keep the car running" by Arcade Fire.

A reasonably in depth Talk & Walk around and eventual start up and run of my DIY Jet Turbine Go Kart. Please excuse my mistake when I stupidly say that Jet engines don't 'Squeeze' the air - of course they 'squeeze' the air !! The compressor wheel within the turbocharger see's to that! - What was I thinking of ?? Oh, AND the fact I refer to the OIL pump as a FUEL pump as well - what a chump. Also, the tacho didn't seem to want to work correctly, It wouldn't read over 5000RPM for some reason - ...

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

Chi running focuses on core muscles, integrating body and mind, and long-term performance to enhance the joy of running. In this tutorial, you will learn how to harness your Chi and improve your running technique and overall fitness.

Getting regular cardiovascular exercise is extremely important to maintain good health but it can be difficult to find an exercise that isn't strenuous on the joints. Luckily aqua jogging is a great workout for any age.

Hacking RC is easy with Piaps Restaurant City Hack! Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to cheat Restaurant City with Piaip's Hack (11/08/09). See how to download, install and run Piap's Restaurant City Hack v.1.13 or 1.12.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

Apple released iOS 13.4.1 to the public on April 7 but also pushed out the update for the new second-generation iPhone SE model on April 23, one day before the device's official release. The update fixes a FaceTime bug and Bluetooth quick action failure that appeared in iOS 13.4.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Even three years after its initial release, Niantic's Pokémon GO is still going strong. If you're an Android user still on the hunt for your city's latest Pokémon haul, however, you'll want to listen up — Niantic is cutting support for aging Android devices, meaning soon your dream of catching 'em all may be coming to an end.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.