How To: Manage pop up windows in Vista
Learn how to block those pesky pop up windows in your browser. This will keep you safe and sane as you block pop ups automatically, never to bother you again.


Learn how to block those pesky pop up windows in your browser. This will keep you safe and sane as you block pop ups automatically, never to bother you again.

A video tutorial that will show you how to Remove programs and applications from your computer in Windows XP.

A quick visual tutorial on how to change the boot screen dialogue on any Windows XP machine. Great for messing wtih friends.

A brief overview of the removal of Windows, and the downloading and Installation of Fedora. The end is a montage of screen shots taken during the install.

Add appeal to your new home with a new window box you make yourself. This video shows you how.

Tekzilla shows you a more efficient way to switch between all those open Finder windows cluttering your workspace.

Design your own characters or edit existing fonts with a hidden Windows program revealed by Tekzilla.

Duplicate the OS X's CoverFlow effect inside Windows and say goodbye to ugly thumbnail views! This tip from Tekzilla only works for image files.
Microsoft Visual Studio 2008 is an integrated development environment that lets you develop websites, web applications, and web services. It requires a bit of computer coding to run (C#, Visual Basic, ASP, C++) and will work on any web server that supports Microsoft.

Windows Vista's boot screen is pretty boring, and for those of you that like to really customize your desktop, you may be wondering why it isn't as easy in Vista as it was in previous versions? While it isn't as easy as it used to be, if you follow along while watching this tutorial you will see that changing the boot screen to your own custom image still fairly simple.
When you try running Apache, Joomla, PHP and MySQL at the same time, you should expect a few hiccups. But there are ways to get them running smoothly and effortlessly together, and this video will outline the process of getting your Joomla Content Management system up and running correctly on Windows.

A tutorial on how to change the remote desktop port number in Windows.
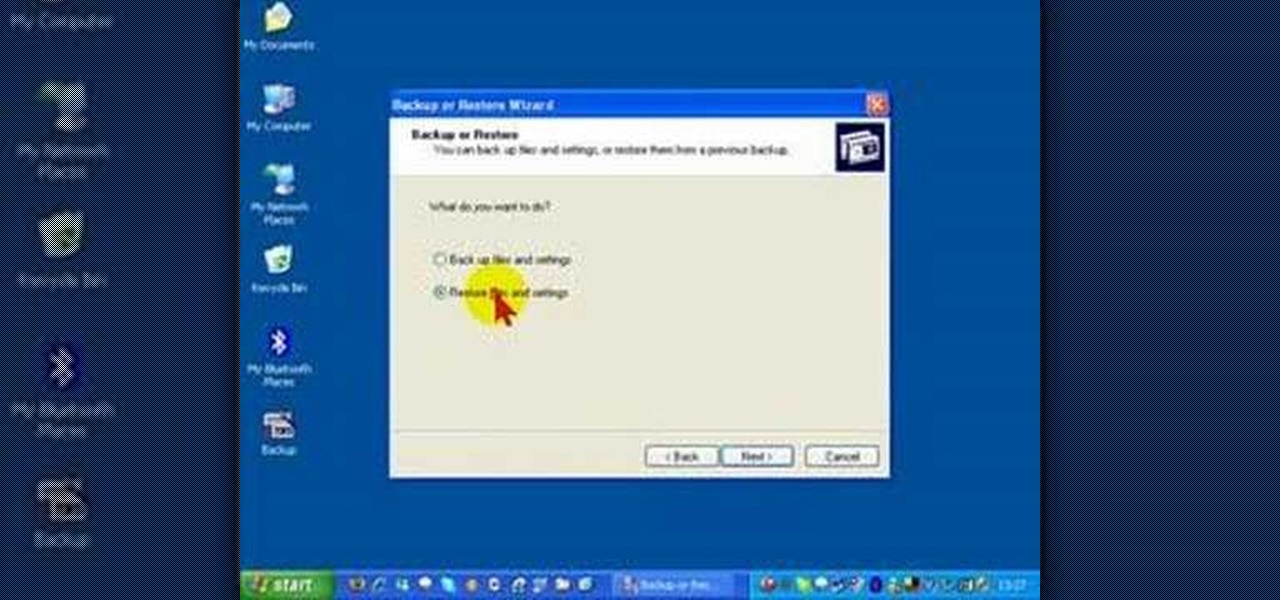
In this screencast, we show you how to restore your files and folders to their original location on your PC, from a backup file, using the Windows XP Backup and Restore Wizard.

In this screencast, we show you how to use the Disc Defragmenter in Windows XP, to clean up your hard discs, and group fragmented files to make access to them much quicker.
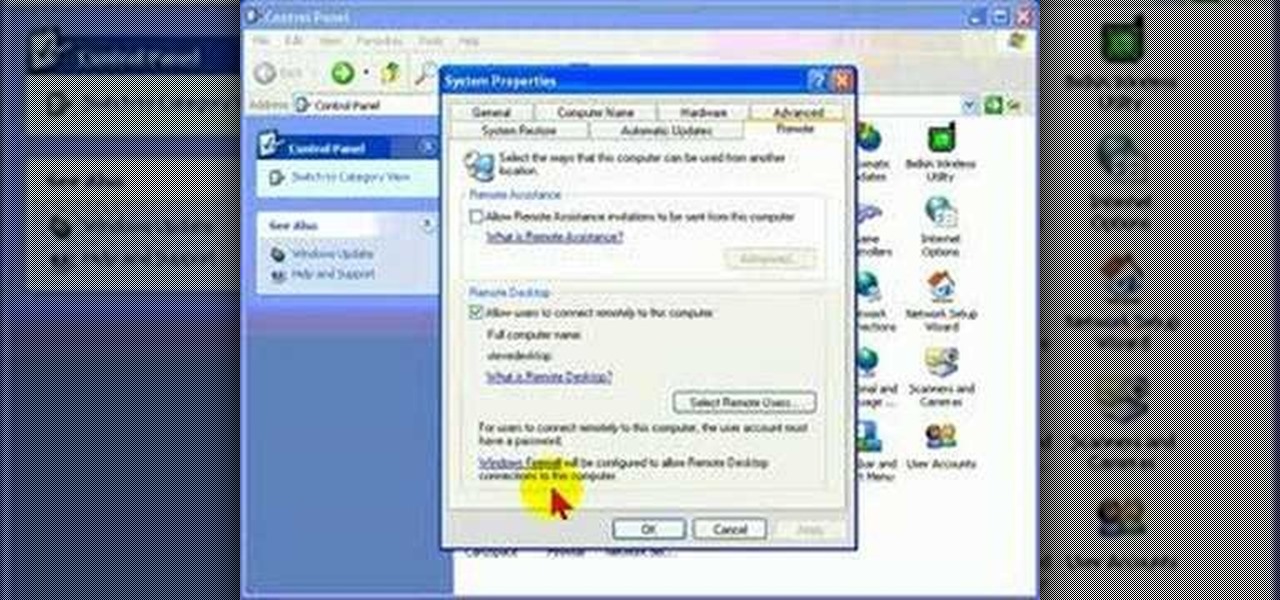
Remote Desktop is a feature of Microsoft Windows, that allows you to access your PC from anywhere in the world, and use it as if you were sat right in front of it.

The back window is the hardest to tint because of the curvature of the glass, but this video takes you through it step by step so pay attention and you should get it right.

Short tutorial on how to run a wide selection of Windows native programs on Ubuntu Linux using Wine.

Here is a simple trick you can play on your friends by pressing only 3 keys. Set Windows to High Contrast mode and ugly up someone's desktop.

How to fix the VLC media player glitch that keeps it from displaying video in Windows Vista.

This video segment will show you how to install window film in your home or business. You can achieve professional results with a great cost savings by doing it yourself.
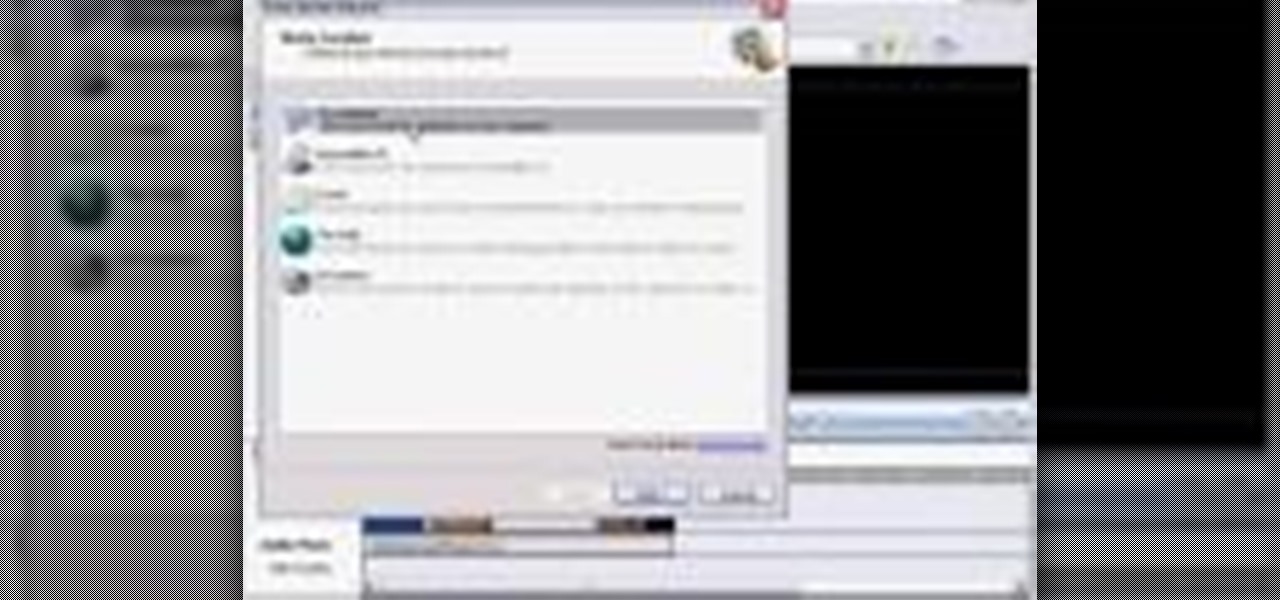
This video shows you how to export your movie after you have finished editing in Windows Movie Maker.
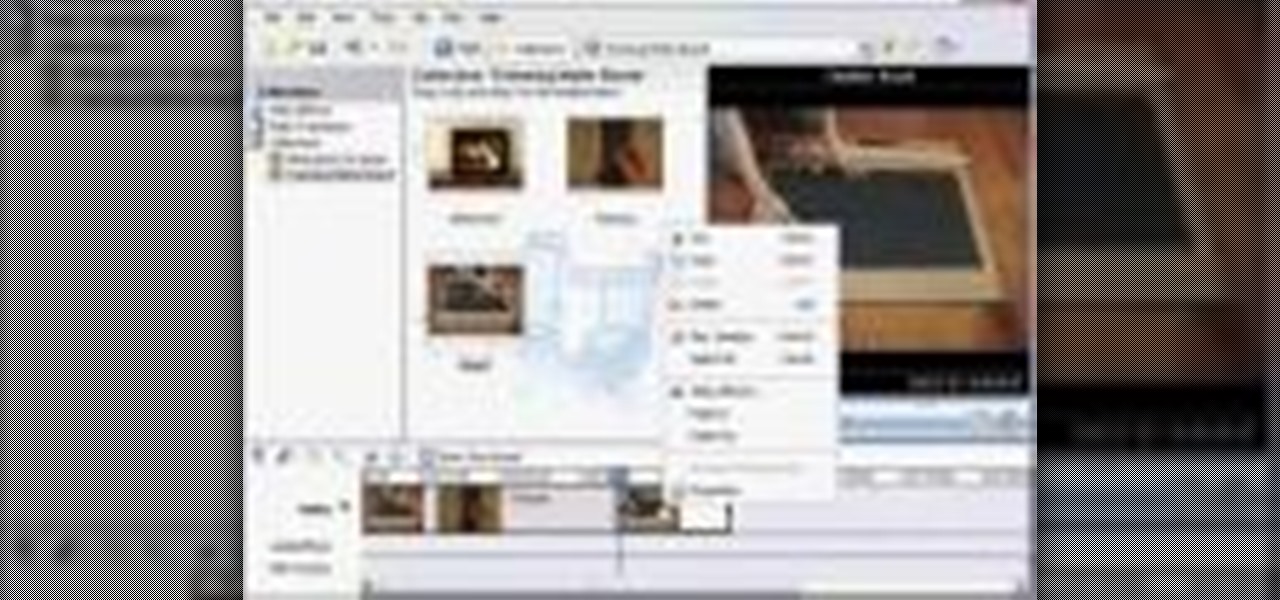
This video gives a short tutorial on using the timeline in Windows Movie Maker.

A how-to on how to share files and folders from Ubuntu to Windows XP and XP to Ubuntu.
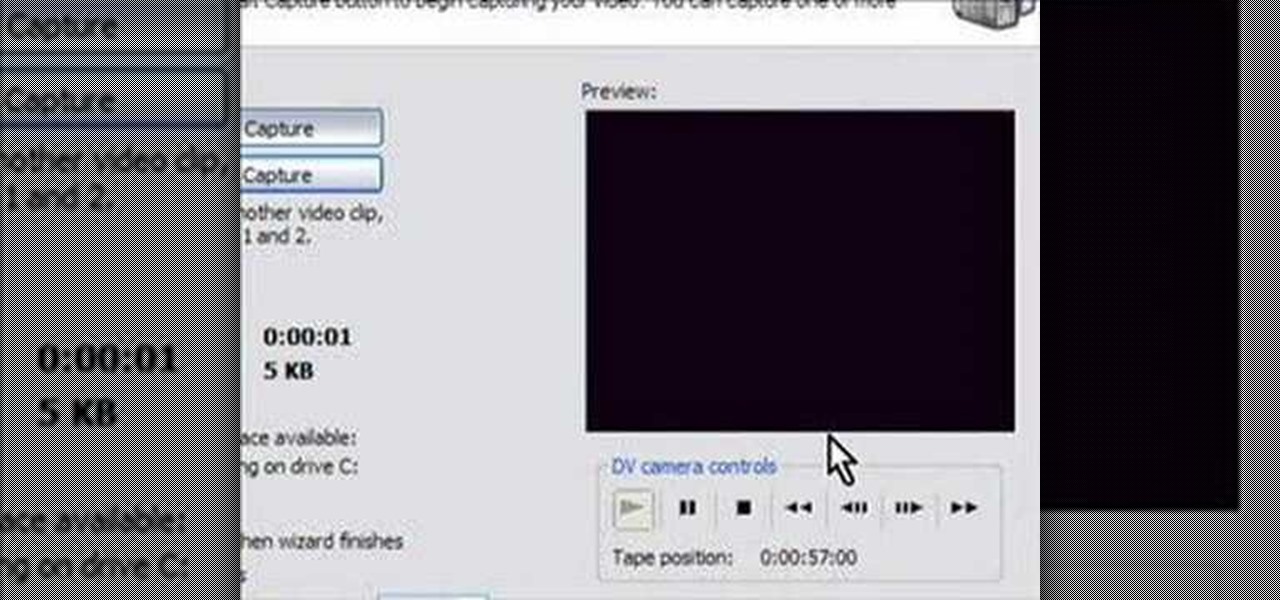
How to capture video from a camcorder, save file and then upload to YouTube using Windows Movie Maker.

DNS spoofing - how to use the hosts file in Windows XP to block unwanted spyware/popups/etc, block programs from reporting to a site, filter/block/redirect websites, and locally create forward lookups (IP to name resolution in network)
Once your video is on the Web you can share it with friends and family in an instant. Learn how to export with Windows Movie Maker so the best possible version of your video is shared.
Take control of your raw footage- learn how to capture video in Windows Movie Maker, and take the first step to editing the video into a completed project.
The right music can add interest and flow to any video. Learn how to add this essential production element to your videos with Windows Movie Maker.
Even when you delete a program, remnants of it can remains on your system and take up valuable memory. The Lab Rats, Andy Walker and Sean Carruthers, teach you how to completely remove programs from you Windows XP and Vista PC.
Learn to disable services and startup items you don't need and enhance system performance in Windows XP.
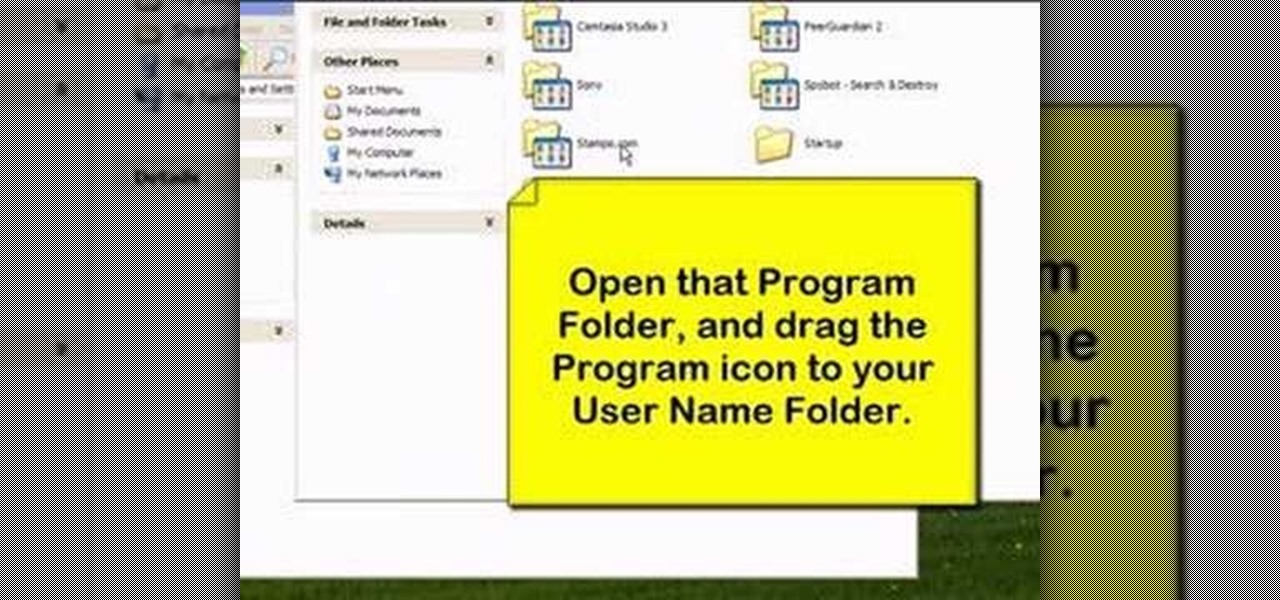
Learn how to organize and declutter an overloaded start menu in Windows. But be careful if you have multiple users with different preferences because this will make the same start menu for each user.

The difference between an effective and a boring video is tight editing. Learn the basic steps to get started editing your raw footage with Windows Movie Maker.
Learn how to import elements like video footage, pictures, audio, and music into Windows Movie Maker and use outside elements to make your videos more unique.

Add titles, credits, and other text content to your Windows Movie Maker projects with these easy steps.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

Apple's codec for photos and videos in iOS 11, HEVC (High-Efficiency Video Coding), as well as the container, HEIF (High-Efficiency Image File Format), result in a reduction in size for pictures and movies without sacrificing quality. Seems like a win-win situation, but Windows-users can't open the .heic extension that these files use. In order to open HEIC files on a Microsoft Windows PC, you'll have to turn to third-party apps and tools. One of these tools, CopyTrans HEIC for Windows, essen...

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.