As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.
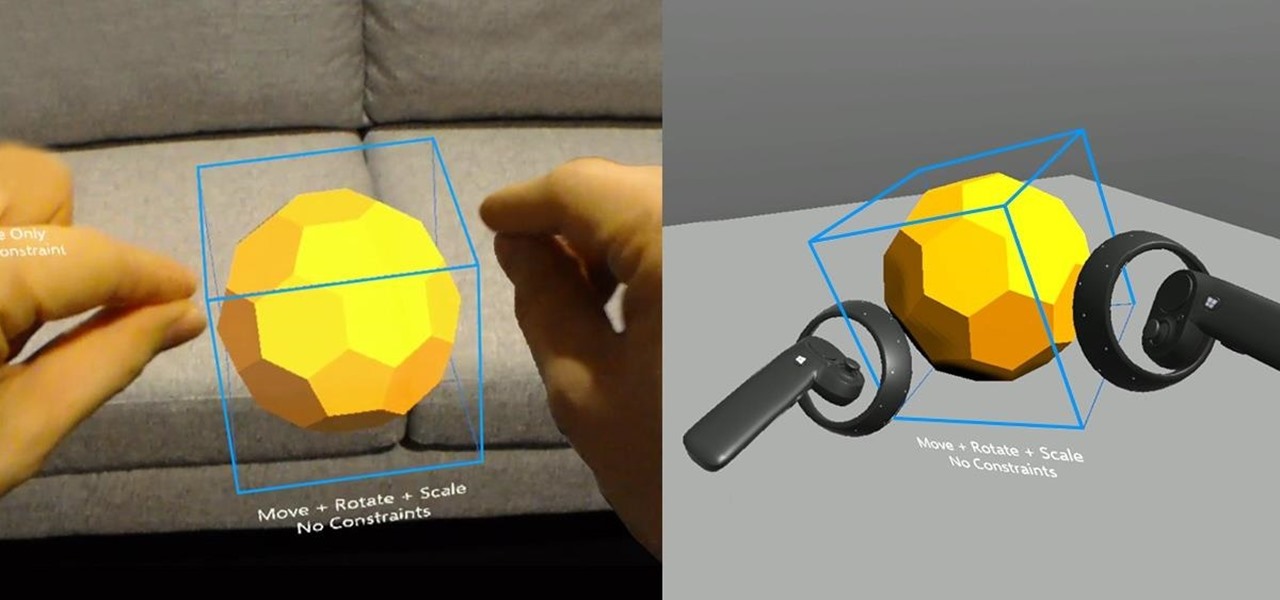
It is finally happening. After not having a major update since August of 2016, HoloLens owners everywhere will soon get a number of new features added to their devices. At least if they are members of the Windows Insider program.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

It has been an interesting few days in developer news. The Microsoft blog has been busy with information relative to the augmented reality space. Meta 2 has also announced an interesting development this week. Here is a collection of various tidbits that have been collecting up.

Nauto, which develops driver-monitor cameras and algorithms for autonomous vehicles, is among a growing list of driverless startups able to attract tens of millions of dollars in funding after raising $159 million in its latest round of financing.

A new feature in Android O is making it incredibly easy to multitask while you're watching a video. It's called Picture-in-Picture mode, and if you've ever used a TV with this option, you should already have a pretty good idea of how it works.

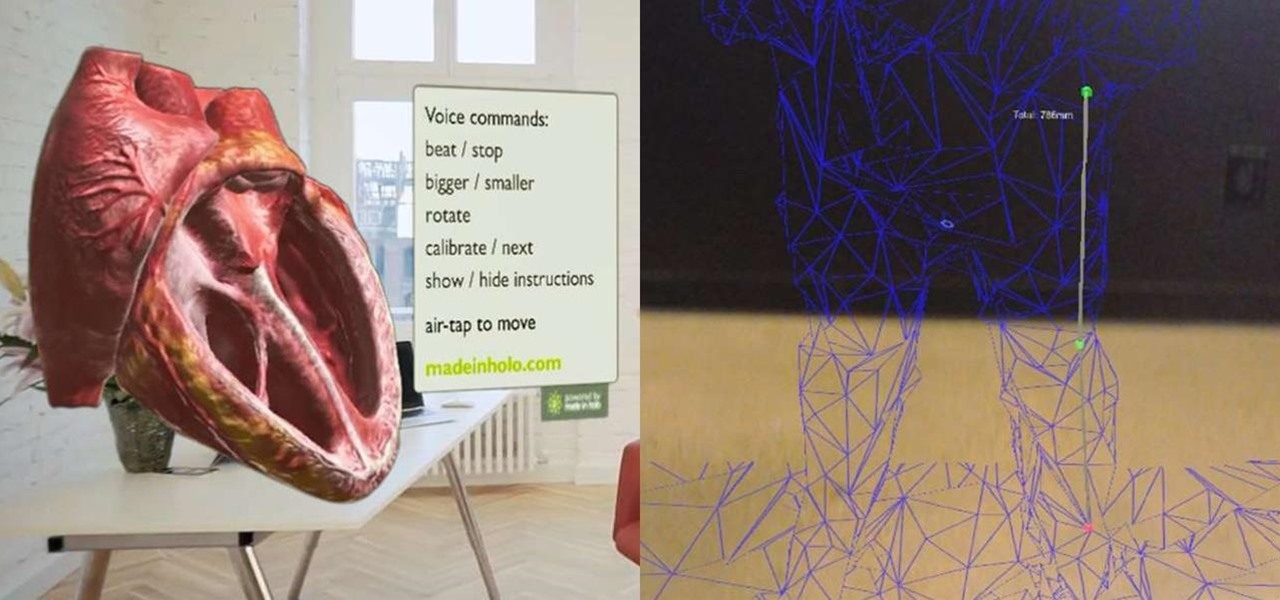
While all of my previous Have You Seen This? posts have all focused on individual HoloLens apps in the Windows Store, this time I'll be sharing a couple at once. These holographic applications are really simple in scope, so there is not a lot to say about them, yet they are interesting enough for me to want to share them with you.

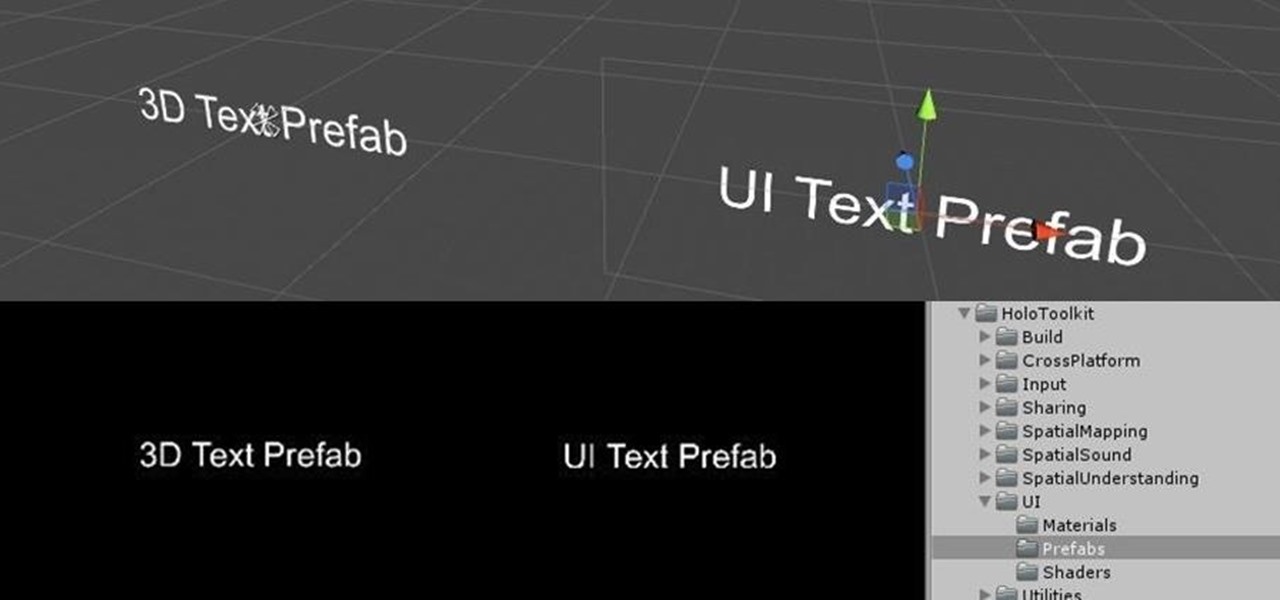
You may remember my post from a couple weeks ago here on NextReality about the magical scaling ratios for typography from Dong Yoon Park, a Principal UX Designer at Microsoft, as well as developer of the Typography Insight app for Hololens. Well, his ideas have been incorporated into the latest version of HoloToolkit, and I'm going to show you how they work.

I've been an iPhone user in the iOS ecosystem for years now after a brief stint in the Android realm. But, I'm also enthusiastic about varying forms of technology in general; I realize that iOS is far from perfect and that healthy market competition is beneficial for all. So, naturally being curious about other platforms, I decided to take Windows Phone for an extended trial run.

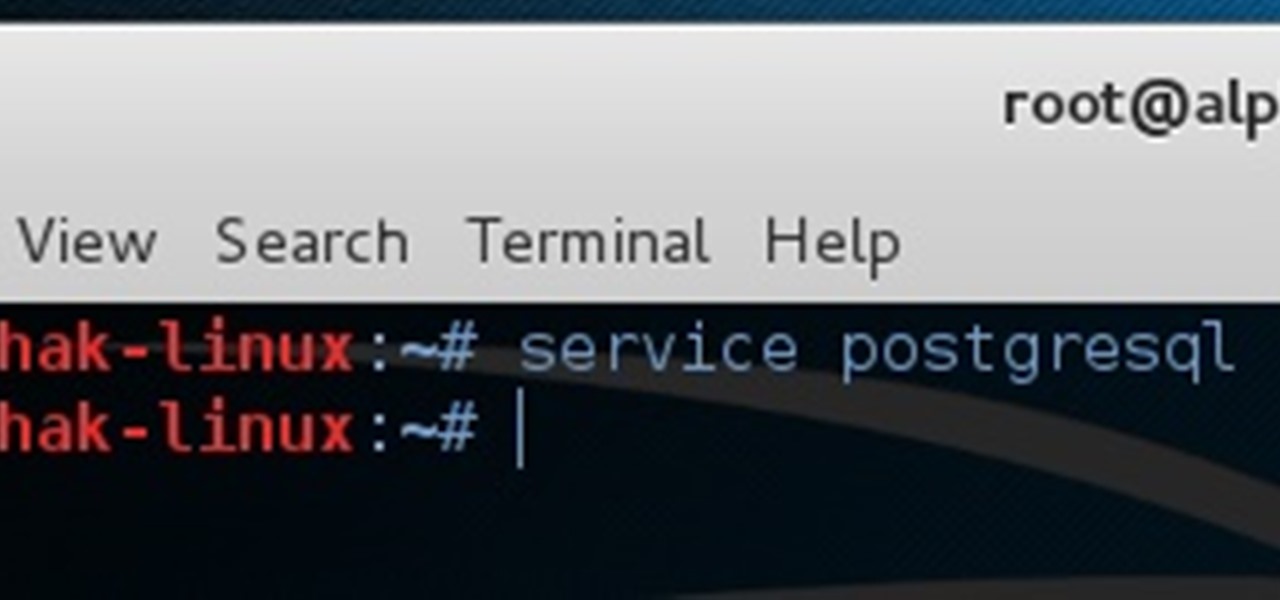
As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.

Nothing about living in a snowy climate is easy, but life with a snowy, frozen car doesn't have to be the worst part of your day. With a few clever hacks and some anti-weather tactics, you can fight off frozen windshields, icy locks, and even stubborn car doors, while keeping your car running smooth all winter. 1. Deice Your Car Locks in Seconds

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.

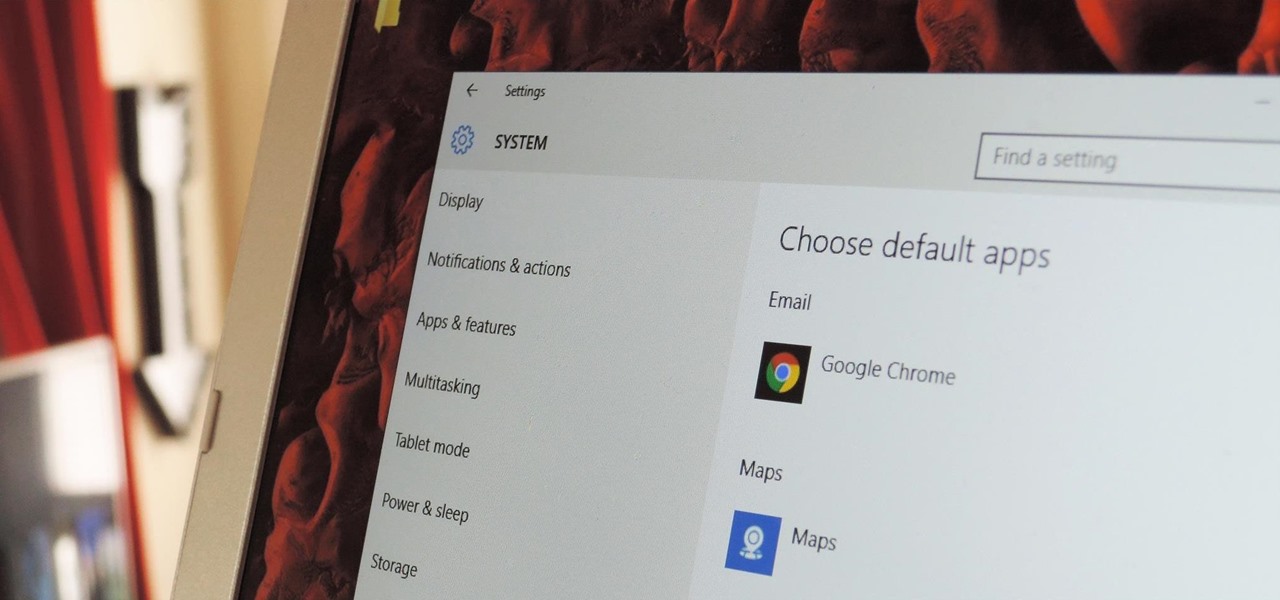
The first time you launch any type of file, Windows 10 will usually prompt you to select an app to open it with. Occasionally, though, this "Open with..." screen doesn't show up, and instead Windows will use a pre-installed system app to launch the file without ever giving you a choice in the matter.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nmap.org/

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"

Windows 10 has proved to be immensely popular (free upgrades certainly don't hurt), and with back to school time, there's a good chance you have a new computer running Microsoft's latest OS. You maybe you decided to go with a clean installation rather than an upgrade, or just haven't used your computer for much more than surfing the web and watching Netflix.

When I first moved to Los Angeles, I rented a bed in a tiny studio. I was too broke to afford my own place, so all I had was a mattress in someone else's apartment. Unfortunately, this person had no interest in cooking, and therefore no kitchen equipment whatsoever. To make matters worse, there wasn't even room for my kitchen equipment. Needless to say, I ate a lot of tubs of Trader Joe's hummus, and frequented a lot of taco trucks.

As familiar as it may look at first glance, there are still tons of subtle changes in Windows 10. Many options that existed in past versions have been moved, and virtually every system menu received at least a small visual makeover.

Ah, the fabled dark mode. In the past, many users were delighted to find the existence of something called Royale Noir, a dark theme option that was available for Windows XP. Yet for reasons unknown, Microsoft had kept knowledge of Royale Noir a secret until some bright minds discovered its existence, and the rest is history.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

While you can do a lot of things on your smartphone that were once only done on a computer, having a laptop is still necessary and critical for many tasks. Often times, the two devices work very well together.

How to make a Macrame Bracelet with Diamonds and Beads.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

With AirPlay for iOS, Chromecast Screen Mirroring, and even third-party PC-pairing apps to play around with, getting your devices to interconnect could not be any easier than it is today.

Unlike the normal cars, the racing cars are more powerful, more maneuverable and less error forgiving. That's why you always have to move them from one track to another with a tow, and not on their own. In this tutorial, I will show you how to lift a racing car on a tow.

Parlez-vous français? While we all wish we were fluent in multiple languages like Jason Bourne, most of us are probably one-trick ponies. When traveling abroad, or even when taking language courses, having a translator handy is extremely important.

Midway through 2013, a popular custom ROM called Paranoid Android introduced their multitasking feature "Halo." Bubble-style notifications inspired by Facebook chat heads pop up near the top of the screen, and you simply tap on them to bring up the app in a floating window.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Today, I'm taking a short break from my usual secret tips to share some exciting news with all of you. As some of you may already know, my first published book "I Think I Am in Friend-Love with You" will be released in bookstores next month.

With the bombardment of technical issues that have plagued GTA Online since its inauguration, it hasn't been easy to enjoy stealing cars and killing hookers with all your friends.

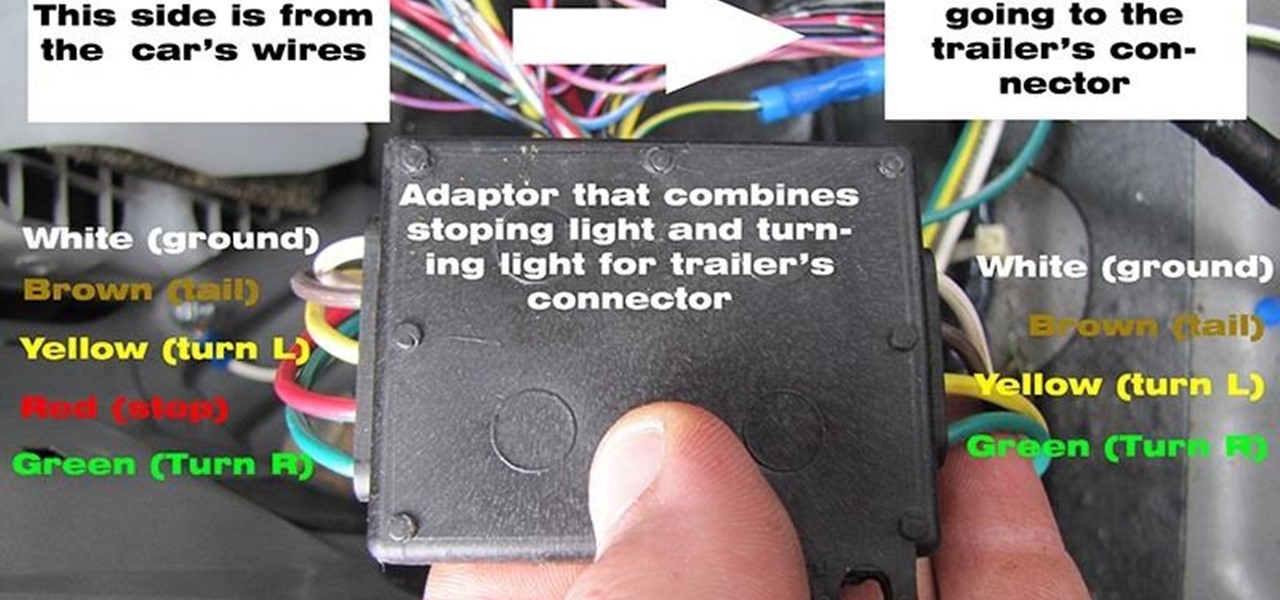
Hi there, first I'm canadian and my SUV so. I'm a hobbyist doing his best, not a mechanic, I don't take charge of other people's installation issues. Anyway, I decided to buy a SUV some months ago, and it comes without the wiring harness for the trailer and the hitch. I made it myself. In this part, only the wiring will be presented. This is for 4 pins harness connector. In any doubt, you can do as I have done for some wires; use a multimeter. Everything on that car works on a 12VDC. Ground y...

Why can't all electronic devices be waterproof like my watch? There are watches worth three times as much as my iPhone that I can wear into the hot tub without a worry in the world, but cleaning most of my electronics requires a lot of caution.

How to unblock a toilet EASILY & WITHOUT a PLUNGER! That's right, without a plunger! How to unclog a toilet has never been easier. A blocked toilet is without doubt a major inconvenience, but don't call the plumber just yet. Save yourself a truck load of cash and give this method a go.

These days, we increasingly have more and more devices in our everyday possession. While a notebook computer, a tablet, and a smartphone may seem like overkill, they do work to make our lives easier and even help reduce clutter in certain ways.

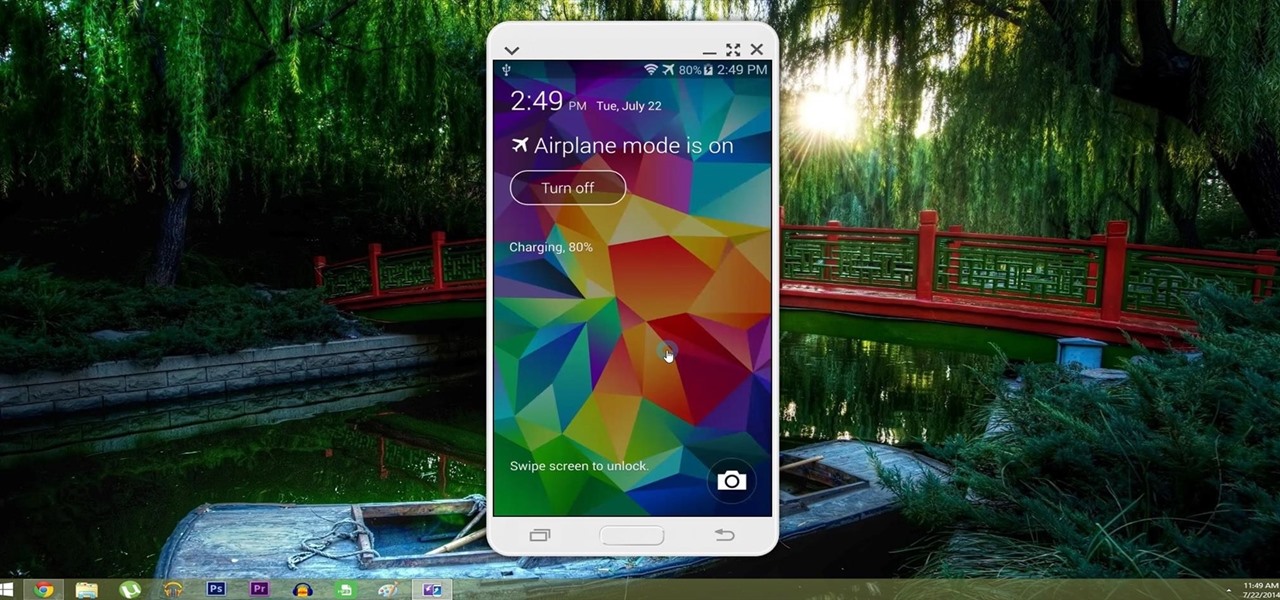
Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

As people continue to upgrade their PCs to Microsoft Windows 8, more and more developers are adding content to the Windows Store. While the offerings are not as vast as Google Play or the iTunes App Store, it does have some solid apps for both productive users and those looking to just while away the time.

Think your roommate's been using your computer while you're not around, but don't have any proof? Worried your little brother or significant other is snooping through your stuff? Here's how to check on both Windows and Mac OS X so you can catch and confront anyone who's logging onto your computer without your permission.

The Droid Bionic was rooted the same day it came out with the one click method used to root the Droid 3. This tutorial will walk you through the process of rooting Motorola's Android device so that you can unlock the full potential of Verizon Wireless's flagship device.

Spice up your computer's appearance with a cool looking screensaver like PolarClock. PolarClock works on OSX or Windows and replaces a dull screensaver with one that doubles as a clock. Now when you step away from your mouse and keyboard you can keep track of the time in style.