Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

Fewer and fewer Android phones are being released with SD card slots, so it's always a struggle to make sure you have enough free storage space for your photos, videos, and music. Things like app data and cache slowly build up as you use your device, which means your available storage number gradually decreases over time.
If you read the reviews on Google's Pixel C, you'll notice one big complaint about the tablet/laptop—most reviewers feel that Android simply isn't ready to be used as a desktop OS. The developers at Jide felt the same way, so they set out to make a custom version of Android with proper multitasking support and a UI optimized for the mouse and keyboard.

Even those of us most comfortable in the kitchen can be daunted by the idea of cooking for a whole houseful of people. Whether you have a large, well-equipped kitchen or a small one with just the essentials, it can prove to be quite a task to prepare food for a dozen or so people. It takes a certain type of recipe that allows for mass production, in respects to both technique and ingredients. And what I've provided below includes several recipes that you might normally make for just a family ...

If you're running iOS 10 or lower, there is no built-in way to make a screen recording on an iPad, iPhone, or iPod touch directly from the device, but that doesn't mean there isn't a way to record your screen at all.

The end of a weekend can be depressing knowing just how bad Monday morning will be when you get back to work, but that feeling is tenfold when coming back from a lengthy vacation with zero work responsibilities.

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

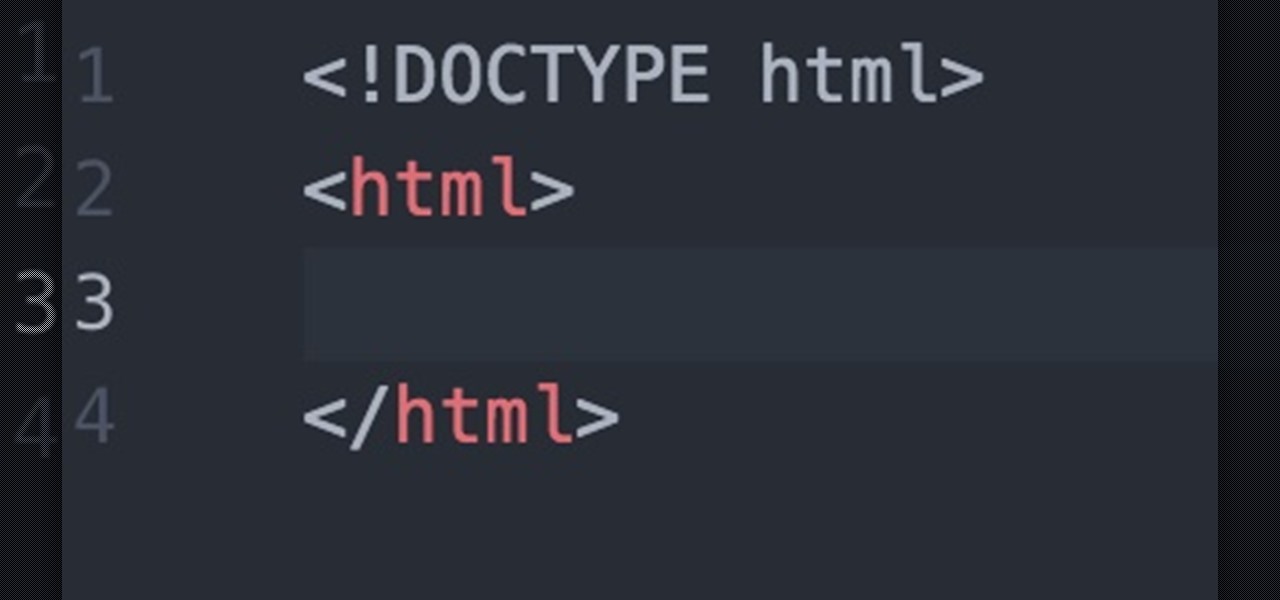
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Hanukkah, also known as The Festival of Lights, commemorates the rededication of the temple in Jerusalem in 168 BCE. (Jews and secular publications, such as academic or scientific papers, use BCE—"before common era"—rather than the Jesus-centric BC, or "before Christ.")

I always have several sheets of puff pastry in my freezer. It's unlike any other pastry dough: the layers of butter let out steam when the dough bakes (hence, the "puff" in puff pastry). The dough's flakiness perfectly compliments sweet and savory dishes, which makes it a totally versatile—and completely necessary—fixture in your kitchen!

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

I held the orange packet in my hands and presented it to my friend, Seth, as though it were a plastic-wrapped jewel—rather than three ounces of dehydrated noodles.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

If you haven't come up with a funny, innovative costume yet for Halloween, you're running out of time. While all your friends are busy perfecting their month-long DIY costume project, you're still being lazy about it and have just now started to search online for ideas.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Not too long ago, Sony was looking to create a method for theming the interface of their Xperia smartphones and came up with a framework called Runtime Resource Overlay (RRO). They then contributed this framework to Android's main code base, and Google has since taken over the development of RRO as a way for manufacturers to implement themes in their skinned versions of Android.

One of my favorite things about cocktails is that they're so diverse. They can be sweet or savory, filling or refreshing. And they can take advantage of nearly any ingredient imaginable, including egg whites, smoked ice, flavor cubes, and even beer.

Preparing and serving seafood can be a daunting task. Fish is so delicate that one extra minute of heat can turn a juicy, flaky filet into a dried-out disaster. But that same fragility also allows us to use unconventional methods to chemically transform the fish into its cooked consistency.

Often, despite your favorite makeup mecca's rows and rows of endless colors, applicators, and brands, it's hard to find the perfect shade of lipstick—especially one at the price you want. Rather than resorting to what's available in stores, turn to your stovetop and a box of crayons.

As Android's de facto virtual assistant, Google Now lets us speak directly to our phones in plain English to answer our questions and perform many basic tasks. With the app open, just say "Okay Google," then wait for the beep, and ask almost any question.

When you look at an Italian flag, what do you see? Green, white, and red? Well, I see a Caprese salad. And no, I do not need to have my vision checked. It simply means that I have the eyes of a chef.

When I first heard about the Thermomix, an all-in-one kitchen appliance from Australia, it sounded like an old SNL commercial parody: It slices! It dices! It heats! It kneads! Is there ANYTHING this machine CAN'T do?

Why did I write this when they're tons of scanning tools available.

The other day I was doing the math on roughly how many eggs I eat each year. I estimated about 500. That's a lot of eggs. And, subsequently, that's a lot of eggshells to throw in the trash.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Few things in life are as relaxing and enjoyable as baking. When I'm having a bad day, I make cookies. When I'm stressed out, I bake a cake. When I have a free Sunday with nothing to do but listen to music and drink coffee, I bake a tart or a batch of cupcakes.

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.

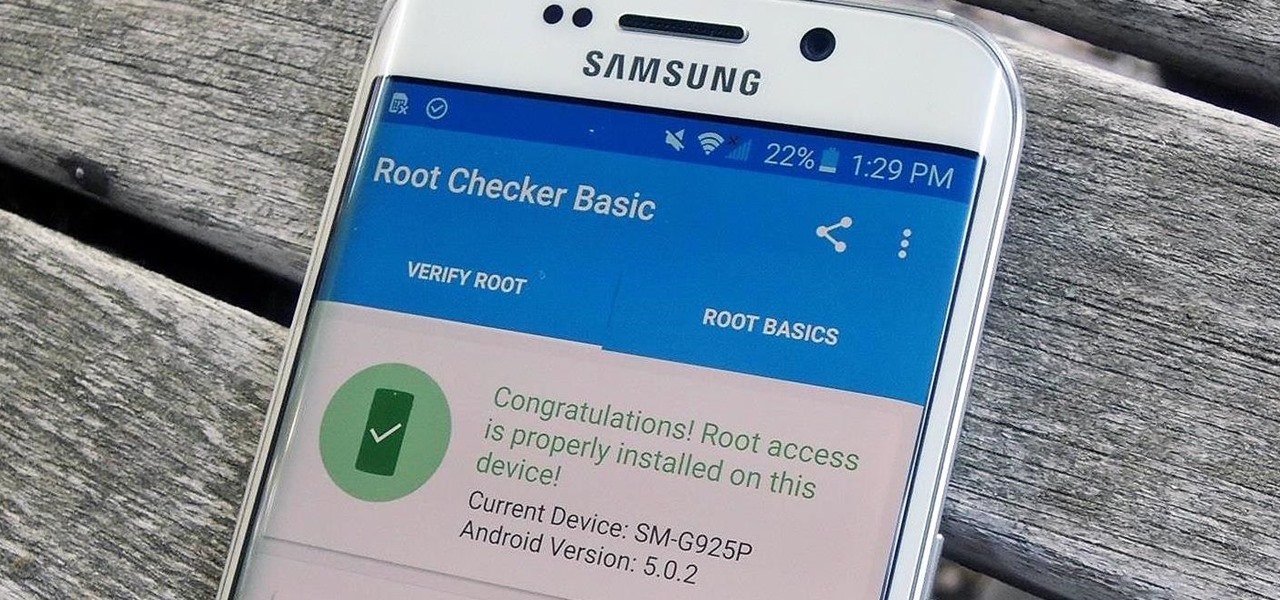
Thanks to leaks and hard working developers, rooting tools for brand new Android devices are usually available right around the time of the smartphone's release, if not earlier. The Samsung Galaxy S6 and S6 Edge are no exception.

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

One of the great joys of cooking is taking the most basic of foods and preparing them in new and exciting ways. About two years ago, my wife opened my eyes to a delicious staple of Indian and Moroccan cuisine that is made in a very elementary way, the preserved lemon.

The gag reflex: it can interfere while in the dentist's chair, upon seeing another person throw up, or even just getting a whiff of a disgusting, stomach-twisting scent. Every time this reflex kicks in, it stops us immediately, inducing a choking, gagging, coughing fit.

Any beer aficionado who's been to Ireland will always talk about how the Guinness there "just tastes different." But save your eye rolls, skeptics: it turns out your favorite lagerhead actually has a valid point.

If you're a child of the '70s, then you'll probably remember Pop Rocks, those fizzy little candies that created such a buzz. They went out of style in the States for a while, but now they're back with retro status. I was surprised to see them in my kids' Halloween bags a few years ago, and one taste brought me back to my childhood.

Your iPhone's home screen is a tricky thing. You can sort your collection of apps in any order you'd like, but where you place those apps is a totally different story. App and folder placement follows a strict grid on iOS from left to right, top to bottom. No exceptions, and that's how Apple wants it. So you might think without a jailbreak you're stuck with this layout — but you're wrong.

You've heard the old saying, "When life gives you lemons, make lemonade." Well, the same goes true for snow. When Mother Nature dumps loads of the white stuff onto your neighborhood, then make the most of it with treats like maple snow candy, snow ice cream, and snow cocktails.

If you're a sushi lover but not an expert sushi maker, you can still enjoy the flavors of sushi rolls at home with these deconstructed sushi dishes.

Dulce de leche is a beautiful, caramel-like spread that you can slather onto bread or use to flavor cakes, cookies, or flan. You can also use it as a drizzle for ice cream, chocolate candies, and pastries. It tastes like heavenly toffee, translates roughly to "milk candy," and is popular all over Latin and South America. A version of the confection is also popular in the Philippines, in Russia, and is known in France as "confiture de lait." The traditional way to make dulce de leche is to slo...