While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

With the recent launch of the LG V30 and the Pixel 2 XL, LG has reintroduced the world to POLED. This display tech was showcased at CES 2015 and billed as a rival to Samsung's AMOLED displays, then promptly disappeared from the market for two years. But now that two of the biggest flagship phones this year are using the technology, many folks will be wondering what makes POLED different.

The Pixel 2 is a solid upgrade when compared to the 2016 model, but we've reached a point where the latest generation of a smartphone is never leaps and bounds better than the last. It's hard to justify dropping nearly a grand on a phone when it doesn't improve your situation much — especially when a few software tweaks will give you most of the upgrade for free.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

The bacteria in our gut — a community called the gut microbiome — have been in the spotlight a lot lately. What we're learning about how our intestinal bacteria adapt and grow with our bodies could help athletes perform better, according to researchers starting a company focused on creating probiotics that mimic athletes' microbiomes.

So cute, so furry, and so chock full of parasites. While raccoons are fun to watch, they are neither friendly nor clean — and they can make you sick in more ways than one.

Chromecast comes to mind when "casting" video from a smartphone to a big screen television, but it's not the only way to "cast" streaming content. This is especially true for Netflix, where you can cast movies and TV shows to not only a Chromecast-enabled TV, but to smart TVs, video game consoles, and other streaming media players so that you have complete control right from your smartphone.

Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.

Tell the truth. The bat picture creeps you out. You are not alone. But in reality, bats truly are some of our best friends. They gobble thousands of disease-spreading bugs a night. But they also carry viruses that can be deadly to humans. So, bats — friend or foe?

There's no debating that the Galaxy S8 and S8+ are top contenders for the most beautifully designed handsets of 2017, but the same can't be said for their TouchWiz interface, which has been met with lukewarm reception at best.

The OnePlus 5 just made its official debut, so we now have all of the juicy details. From the announcement, this device definitely sounds like it's going to be another flagship killer, following in the footsteps of its predecessors.

Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at 8:01 a.m. (PDT) on March 24, 2017, so we'll go over some tips to help you secure a red iPhone before it's sold out.

The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fictional creatures found in Pokémon GO. However, there were some video game consoles that kept kids indoors, such as the Game Boy, SNES, and more importantly—the first ever PlayStation.

For some, drinking raw milk is a way to get back to nature, improve family nutrition, and hedge against asthma and allergies. However, according to public health authorities, drinking raw or unpasteurized milk is a big mistake—even fatal. So what's the story?

If the rumors are right, Microsoft has decided to cancel the second version of the HoloLens, and they will instead move onto version three of their mixed reality headset. In the latest report, Thurrott's Brad Sams states that the expected release date of this new Windows Holographic device wouldn't be until 2019, a long two years away for those of us putting full effort into HoloLens app development.

Long before Apple and Android became household names, Nokia dominated the mobile industry. The Finnish company was one of the first to develop smartphones, and their classic N95 with 2G "high-speed" internet connectivity was declared the "best smartphone ever" by some in 2007. Outside of the US, before the iPhone became all the rage, owning a Nokia phone was a status symbol akin to wearing a Rolex or Omega watch.

It's that time of year again. The world's largest electronics companies are sending representatives to the annual Mobile World Congress event in Barcelona, and for gadget lovers like us, that means we'll get our first look at some of this year's biggest upcoming flagship smartphones.

While music may not technically be a "universe language," it is the one language listened to by all. There are over 1,500 music genres today—rap, classical, rock, jazz, trap, hip-hop, house, new wave, vaperwave, charred death, nintendocore... and the list goes on. And if you're like most people, you now probably listen to the majority of your music on your phone.

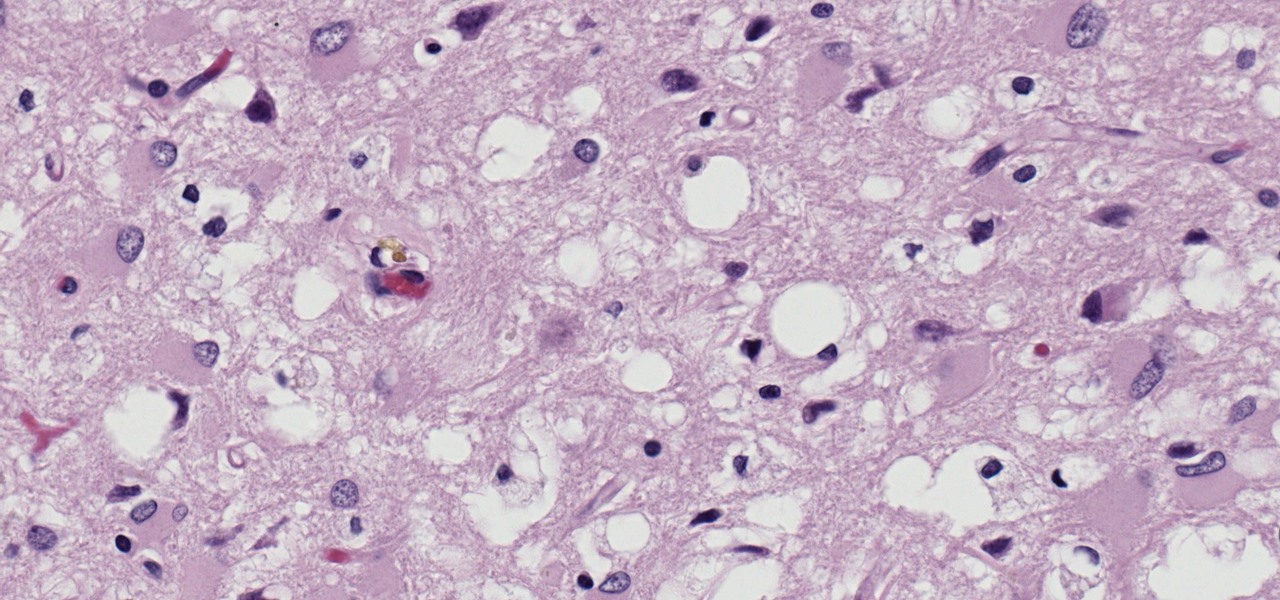
Prion diseases are a group of infectious brain diseases that causes extensive tissue damage, resulting in sponge-like spaces in brain tissue. Prions include Creutzfeldt-Jakob disease in humans, bovine spongiform encephalopathy (often called mad cow disease), and chronic wasting disease in hoofed ruminant mammals.

And so it begins... CES 2017 is upon us! This is a very exciting time for those who are looking out for the newest innovations and releases from the world of technology. I said this was going to be a fun week, and here we start it with a bang from smartglasses developer Osterhout Design Group (ODG).

You just sat down, coffee in hand, and the day is ready to start. Now that you have taken a few sips, let me pose a question: What is living in that coffeemaker of yours? The answer might make you dump that coffee down the drain pronto.

Each generation of smartphones ushers in a new set of top-of-the-line specs, with processing power, battery size, and display resolution growing by the year. These headlining features get the most press, but there's one unsung hero that has the potential to make the biggest difference when it comes to real-world performance: RAM, or random-access memory.

If you've been following NextReality, you've surely seen me around, or at least have seen my articles. My name is Jason Odom, aka Subere23, and it's about time for a formal introduction.

When it comes to busted smartphones, liquid damage ranks right up there with shattered screens as one of the most common issues owners have to deal with—as well as the most embarrassing. Thankfully, though, with the rise of waterproof phones such as the Samsung Galaxy S7 and even the iPhone 7, this is becoming less and less of a worry. But not everyone has a waterproof device.

Fight me all you want, but it ain't a party without alcohol—whether it's a Halloween party, Christmas party, dinner party, or even a damn wedding. (If you think that people will stick around after dinner for a dry wedding, then you're sorely mistaken.)

Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The result is RCS Universal Profile, or simply Chat, and it's finally catching on.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Are we about to witness the future of Android OS? Of Google? Of the entire smartphone ecosystem?! Google has just turned 18 today (right?), Android just had its 8th birthday, and the rumor mill is firing on all cylinders in the lead-up to the October 4 launch event where they'll announce their latest hardware and software products.

For me, the smoky brilliance of a good barbecue can't be beat. The way the smoke flavor seems to permeate every part of the meat is, in my opinion, the closest thing we have to food magic. Throw a piece of meat in a smoker with some select wood choices, wait a few hours, and suddenly you have something rich, complex, and bursting with smoky flavors.

No matter how far technology advances, battery life continues to be an issue. Powerful new hardware is introduced each year, but smartphone batteries only get a few extra milliamp-hours to compensate.

A carefully constructed frittata is one of the culinary world's perfect wonders. It's inexpensive to create, can be made with all sorts of leftovers, and is outstanding to eat for breakfast, lunch, or dinner. However, frittatas can go downhill fast and come out spongy, tasteless, dry, and over-done.

If I were to write a snickerdoodle FAQ list, the top question would undoubtedly be "Do I really need to use cream of tartar in my snickerdoodle cookies?"

The sweet aroma of cooked fruit filling your kitchen is one of the trademark scents of summer. Yet attaining the perfect consistency for homemade jam can be difficult to master. Often it ends up a watery mess or over-solidifies into thick mystery goo that is destined for the trash, not topping your toast.

With the weather warming up and the days getting longer, fruit salads are starting to appear at backyard BBQs, beach picnics, and pretty much everywhere else. Often these sweet side dishes are unremarkable, with each colorful bowl blending into the next. Luckily, there are easy ways to spice up your fruit salads so that everyone will still be talking about them next summer.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

Fresh, homemade pasta definitely beats the dried stuff from the store. However, most of us aren't usually in the mood to knead dough for 10 minutes... or to clean up a sticky, doughy, floury mess afterward.

Cocktail rims are an easy way to add extra fun and pizzazz to your favorite drink; Most cocktail rims only take a few minutes to put together, and are a great way to add a burst of flavor to compliment what you're drinking.

It was definitely a shocker when Microsoft proposed cross-network play between the Xbox One and PlayStation 4 last month. After all, Microsoft and Sony have been competing for the same user base for more than a decade now, and this new feature might actually decrease console sales as a whole.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.