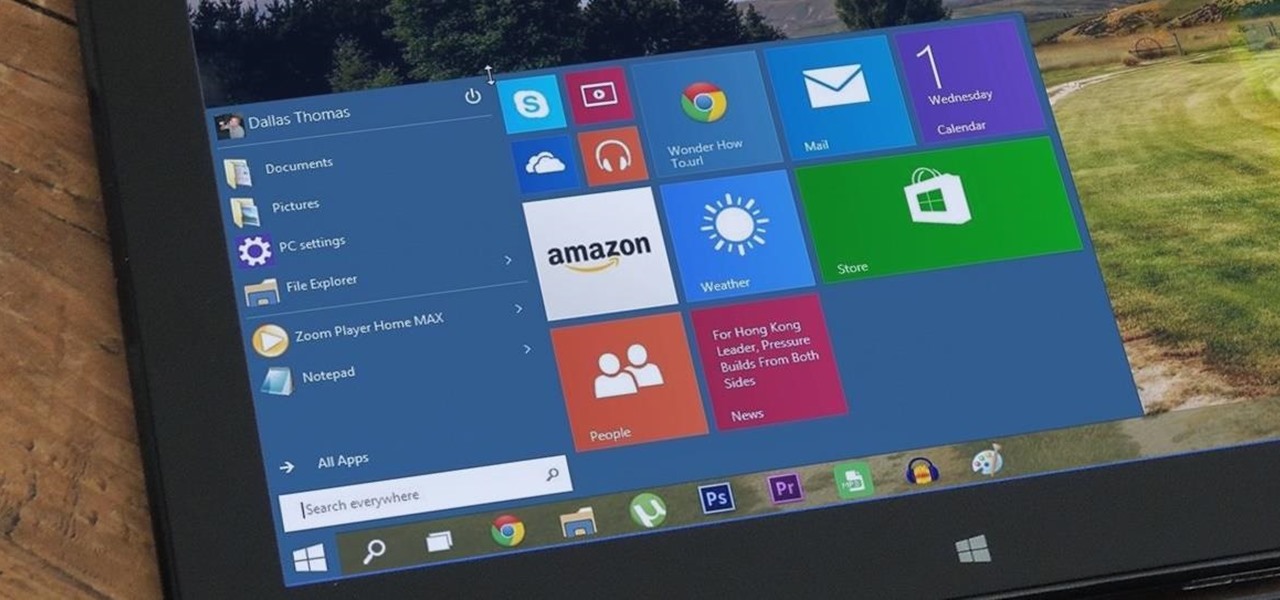
At a closed-door presentation on September 30th, 2014, Microsoft unveiled the latest iteration of its industry-leading operating system. Dubbed Windows 10 (seems as if Redmond isn't too fond of the "9" moniker), this new version brings along with it many UI optimizations and under-the-hood tweaks. With a particular focus on optimizing the interface for traditional mouse and keyboard computers, one of the most noticeable changes is the return of the Start Menu. While touch-optimized devices wi...

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Biting into a perfectly ripened piece of fruit is enough to convince you to give up baked goods and plant your own garden. The combination of flavor, juice, and sweetness in a ripe mango, apple, plum, or berry is the stuff of life itself.
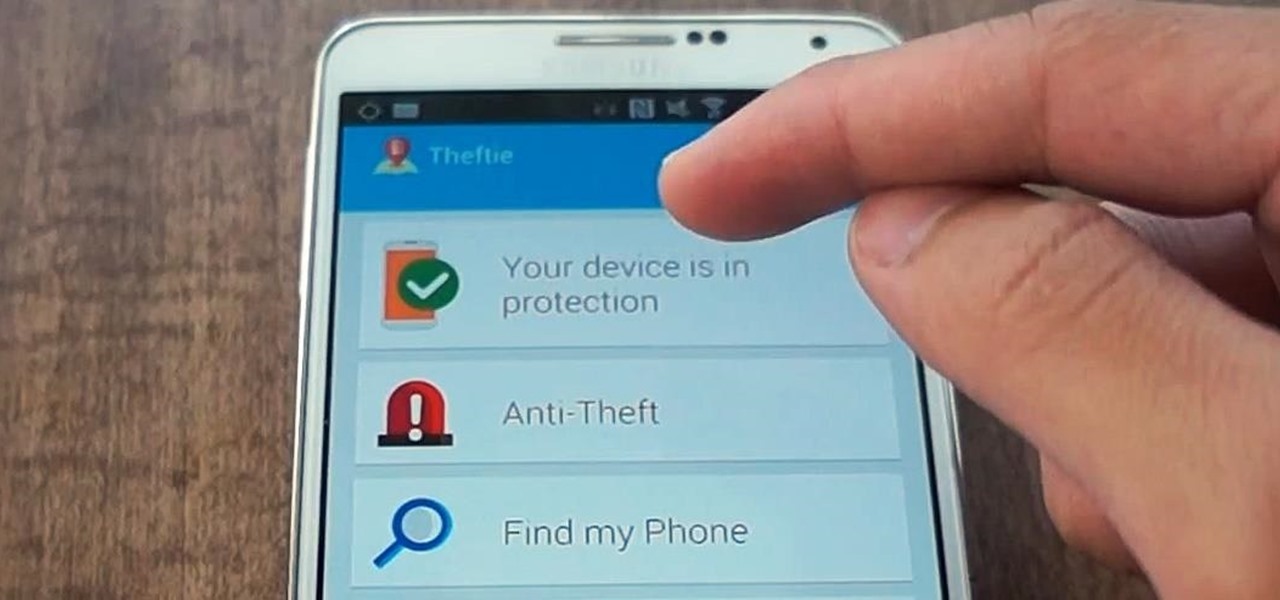
When you misplace your Android device, finding it with the Android Device Manager, or even better, Whistle Me, can help you find it no problem. But what about when your phone is not just hiding under the couch cushions? Your worst nightmare just came true. It's officially gone.

"The best season for food is the worst season for cooking." These words, spoken by food blogger Dave Klopfenstein of Dave's Kitchen, couldn't be more true.

People tend to skip toasting nuts in recipes or before adding them to salads because it seems time-consuming and the margin for error is high. However, skipping this step is a big mistake. Why? Because when you skip toasting your nuts (go ahead, you can laugh, we're all doing it), you sacrifice flavor and texture. And not just a little flavor, but a lot. Alton Brown recommends wok-frying peanuts before making your own nut butter for this very reason.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Multitasking has always been one of Android's strengths relative to other mobile operating systems. As the first cell phone OS with "true" multitasking, Android's been ahead of the game in this department for quite some time.

The long rumored and recently leaked Amazon phone has finally been unveiled, and in the interest of branding, continues down the Fire line—the Amazon Fire Phone. You can check out the full reveal here (warning: it's long), but I'll take you through all the features that sets this device apart from the rest. Before we get into that though, let's check out the specs:

Old habits die hard. It may be a cliché, but it's undeniably true, especially when it comes to the bad ones. Nail-biting, fidgeting, and overspending can label you as someone who is obsessive-compulsive, overly nervous, and routinely stressed out, but you can make the break less painful with a few simple tweaks to your routine and by understanding how your habits work.

It may seem impossible to win an argument against an irrational person, but it turns out the tried-and-true techniques that hostage negotiators use against hostage-takers work surprisingly well in everyday situations. You may not ever deal with a real hostage situation personally, but life is full of negotiations with unreasonable people, and those conversations don't always have to end in rage or disappointment. The mental techniques that professional hostage negotiators use can help both pa...

Apple's grand reveal of iOS 8 at WWDC in San Francisco is still a few days away, but that doesn't mean there isn't any speculation as to what features and enhancements might come packed in the new mobile operating system.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

As with most OEMs, HTC would like you to think that you can do virtually anything with your new HTC One M8, but as a softModder, you know that isn't true. To actually unleash the full potential of that device, you need access to the whole system, not just the parts that HTC deems okay for you to mess with.

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

Last week, I showed you why your refrigerator is one of the best tools in the kitchen when it comes to saving money and preserving food at its tastiest. But did you know your freezer is another underutilized ally in the cooking game?

To steal a quote from Mean Girls, Halloween is the one night when a girl can dress like a total slut and no one can say anything about it—but why do girls get to have all the fun?

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

You probably know Lenovo from their low-cost Windows PCs here in the states, but something you may not be aware of is that they also make smartphones. Right now, their biggest market is in China, but a rumored merger with BlackBerry could make Lenovo a contender in North America, not to mention one of the biggest smartphone manufacturers in the world.

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

Glow sticks, a popular favor at parties and outdoor events, and a must-have on Halloween, can be traced back to the United States Navy in the mid-1960s. The military desired improved visibility during night operations, and glow sticks, with their small-size portability and lack of batteries, were a perfect tactical solution.

Facebook just released its new "home on Android" last Friday, appropriately called Facebook Home. Taking a cue from Amazon's Kindle, Home serves as an "operating system" that runs over Android.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

Video: . Optimize your Marketing with a Mobile Website

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.

There was recently a case that came to national attention where a gentleman was arrested at an airport for having a watch that looked like a bomb, among other things. As it came out, the watch was, in fact, not a bomb, and the man was just an artist who was probably trying to make a statement of some sort. Well, that message was lost amongst the hail of people shouting that either he had been stupid for bringing that watch on the plane and so deserved to be arrested, or that it's a free count...

There's something special about Laika Inc.'s Paranorman... Hey! Did you love Coraline? Are you interested at all in stop-motion animation? Well, watch this feature on Laika Inc.’s new film, Paranorman.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

If you've run out of time for all of our more time-consuming Halloween costume ideas, here are some places on the web for free, downloadable paper masks. There must be at least 100 options among these links to satisfy your last-minute costume needs! Just download, print, and cut 'em out to the appropriate size, then either glue a stick/handle on or tie some elastic string on.

There are a surprising number of hidden features in your iPhone's Phone app, from secret dialer codes that provide info or perform actions to special characters that dial extensions automatically. However, there's one little-known trick every iPhone owner should know when using the Phone app for calls — and it's the simplest and most useful of them all.

There aren't many iPhone apps that let you change their color theme beyond light and dark appearances. They really don't need to either because iOS has a few hidden tricks up its sleeves to help you customize any app's colors either during a specific session or every time you use the app.

The new iPhone 14, 14 Plus, 14 Pro, and 14 Pro Max all come with great, never-before-seen-on-iPhone features, including the A16 Bionic chip, Bluetooth 5.3, precision dual-frequency GPS, and dual ambient light sensors. But that's only a few new features exclusive to the 2022 lineup.

The practice of using sound to trigger augmented reality interactions hasn't been widely used, but a new experience is so impressive that it could kick off more use of the dynamic.

Cosmetics brands have a long love affair with augmented reality, embracing virtual try-on effects as a means to help sell eyeliner, hair color, lipstick, and the like.

Pretend you're a phone thief for a moment. You might be a pickpocket or a stickup kid, but you're in possession of other people's phones on a regular basis. Now ask yourself this: what's the first thing you do after you steal a phone?

QR codes are so handy. Nowadays, all you have to do to scan one is open your phone's camera app and tap a button. But creating one is a different story — online QR code generators aren't always trustworthy, and most phones don't have a built-in feature for it. Thankfully, Google Chrome now does.

After piloting the Nreal Light in South Korea and Japan via carrier partnerships and securing another round of funding, Nreal is now ready to begin selling the consumer edition of the smartglasses to the western world as well as introduce a version for enterprise customers.

I must admit, upon learning that the NFL was broadcasting the contest between the New Orleans Saints and Chicago Bears on CBS, Amazon Prime Video, and Nickelodeon, the latter was the only option I wanted, purely for the novelty of the experience.

Whether you want to give a gift that your loved one has wanted all year or one that they never even knew existed, there's something awesome for everyone in these gifts. Just as exciting as their innovative features is their price.