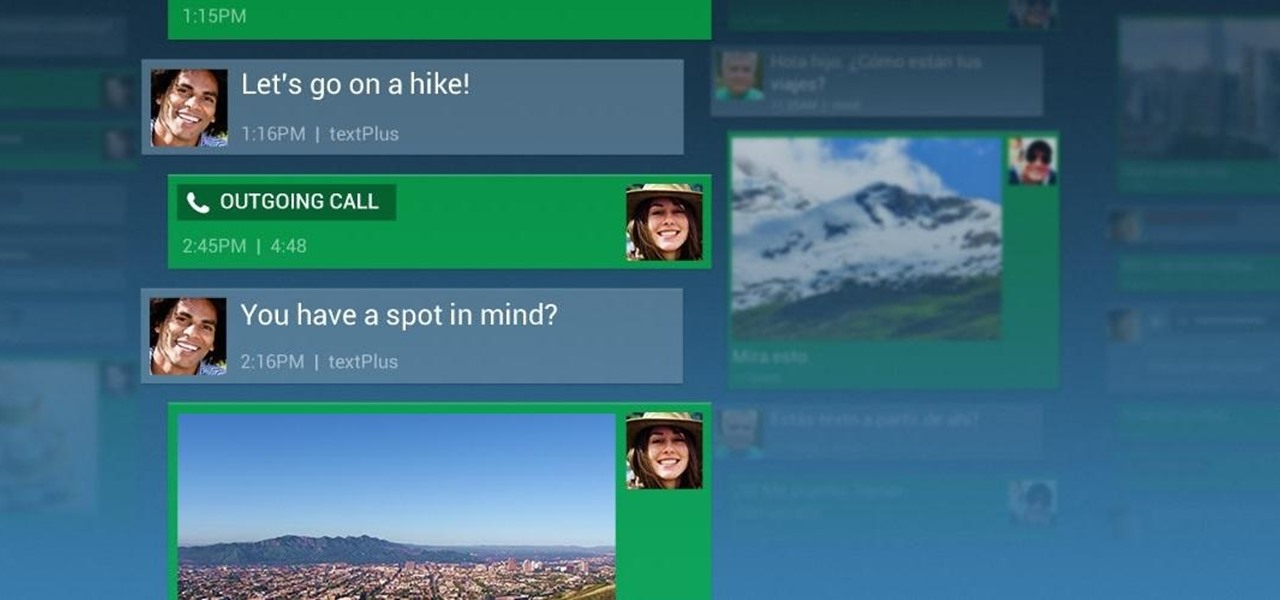
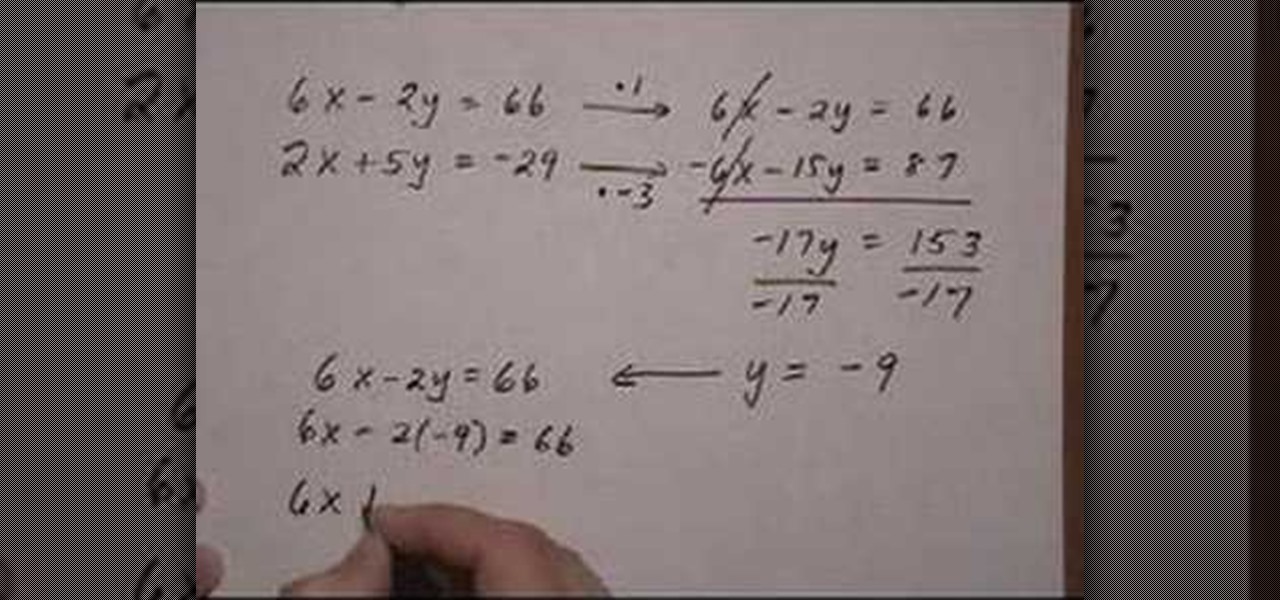The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

When the Steam Link app was first introduced in 2018, I was impressed. As long as you were on the same network as your PC, you could play your Steam games on your phone. But now, it's even more impressive. By enabling a few extra settings, you can play your Steam library on mobile data anywhere in the world.

The era of AT&T and Magic Leap has quietly entered a new phase that ramps up the mainstreaming of the cutting edge augmented reality device.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.
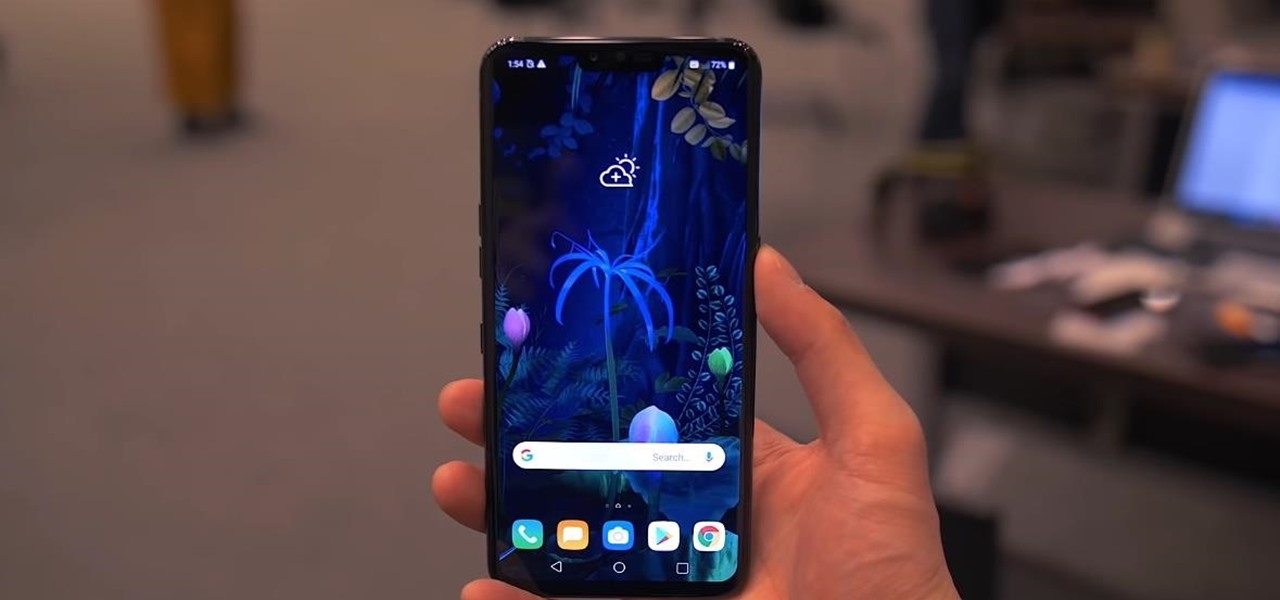
Similar to last year, LG is mixing up its releases. Instead of the G series in the first half of the year and the V series in the second half, LG is releasing both heavy hitters together. However, unlike last year, this is a true upgrade from its predecessor, the LG V50 ThinQ 5G.

Let's face it, iPhones are expensive. With the latest iPhone XS Max reaching as high as $1,449, our wallets could all use a little support. That's where Black Friday comes in, supplying us with deals and discounts on iPhones of all kinds. If you're looking for a new iPhone this holiday season without having to break the bank, you've come to the right place.

It's that time of year again. No, not Thanksgiving. Black Friday. There are a lot deals available this holiday weekend, many of which include flagship Android devices. Whether you are thinking of buying a phone for yourself or looking for a gift for someone else, you can find a little savings to shop smart during the holidays.

Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPhones, making it a worthy choice to upgrade to if you're in the market for a new mobile device.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

While everyone was marveling at the latest drama over at Magic Leap involving employees last week, a major rumor listed in one of the reports, related to the company's flagship device, was mostly overlooked.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

With the official release of iOS 11, the availability of an app that uses the much-hyped ARKit platform to place virtual furniture in one's home was expected.

Every year, football fans get excited about the next crop of blue chip prospects joining their teams, from five-star high school recruits graduating to college to first-round rookies drafted into the NFL.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

Esports — and, subsequently streaming it — are possibly some of the more surprising products of the 21st century so far. Who would have thought that people would be watching professional gamers play, the same way we've watched pro sports players on TV for more than half a decade?

The leaks and rumors surrounding the highly anticipated Galaxy Note 8 just keep coming. But none have suggested that the new Samsung phone might be powered by a different chipset than the Snapdragon 835, until now.

We fight cancer in a variety of ways, but no matter whether drugs, biologics, or our immune cells are part of the battle, they can do a better job fighting back cancer if we can help them find the tumors.

This is a quick and easy method for receiving the backend IP (1) of a server who is hidden behind a proxy (2) or a firewall (3).

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Leaving your computer unattended, whether at home, work, or a coffee shop, even for just a short while, is enough time for someone to steal it or look at your personal files. While there are ways to deter thieves, it's a little harder to keep snoops away.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Apple computers have long been maligned as the computer for Starbucks aficionados and graphic artists. "Dude, have you used Excel on a Mac? It's terrible," says everyone that owns a Dell. The whole PC versus Mac battle was encapsulated in what I think to be the greatest ad campaign of all time, "I'm a PC and I'm a Mac." And yes, I know that PC really stands for Personal Computer, which means that a Mac would be a PC, but for the sake of the article, it will mean all things non Mac.

Hey dolls some advice on the dos and don'ts of the gay scene. Slutty behavior, Bitchyness, backstabbing and safe sex are all issues that go on in the gay community. Coming out and or dating in the gay community for the first time can be scary. Stay true to yourself and don't do anything you don't want to do, stand out from the crowd and be yourself. Do t feel the need to fall into the stereotypical gay "Look". Follow these steps to make sure you come out of all the drama with a better chance ...

Sometimes, doing the right thing is way more difficult than it should be, like trying to return a lost smartphone. Despite having the best intentions, it's often hard to track down the rightful owner, especially if the device is armed with a passcode. On the other hand, there are plenty of people who see an unattended iPhone or Samsung Galaxy S3 as a chance for profit. In 2011 alone, the number of lost and stolen cell phones in America was worth over 30 billion dollars. That's right, billion....

Like most Android devices, the Nexus 7 suffers from its fair share of battery gripes. Nobody wants to see that dreaded "connect charger" warning pop up on their screen. NOBODY. Yet it probably happens to you every day nonetheless. What can you do about it besides charge, charge, and charge? Well, there's actually plenty that you can do. You can manage your notifications better, keep your screen brightness low, and kill apps running in the background. Or, you could just optimize your battery t...

Smartphones are great. They help you keep in touch with your loved ones and stay up to date on what's going on in the world. The problem is that like everything else that's useful, they cost money to use, and between calling, texting, and data plans, it can get really expensive.

This video is about using the elimination method to solve a linear system. The lady presenting this video says that elimination method means that one of the two variables has to be eliminated while adding up the two linear equations. She then explains the example equations 6x-2y=66 and 5y=-29-2x. She asks you to first line up x and y. So the second equation is rewritten as 2x+5y=-29. Then she says that, to eliminate a variable, we should have their variables equal in value but of opposite sig...

Bored of sitting on your PC? Need internet on your Nintendo DSI? First check out whether you have WAP/WPA2. You can find out whether you have WAP by going to internet and typing your IP address and going to your wireless settings. If you do have WAP/WPA2 then go to system settings, then to internet. If you have Wi-Fi connector, turn that on. If you have WPA2, then go to advanced settings. This will get your Nintendo DSI get connected to the internet.

If you're a gal and you don't know what a Brazilian is, then you've clearly been living under a rock for the past year. A recent development in hair straightening and, er, fluffing, the Brazilian blowout makes coarse, tumbleweed strands as smooth as silk while creating envious volume that lasts not for one day but a few months.

Nailing a picture or a work of art to a wall is pretty easy in and of itself, but when it comes to arranging these pictures stylishly people have more trouble. It's true that you can nail pictures to the wall, but what about to bookcases?

If you're a true makeup junkie then you probably have more palettes than you know what to do with. Since palettes are rather large compared to other makeup products you're probably just stacking them on top of one another wherever you have room.

The tradition of bringing a colorful boquet of dead flowers to your true love is old as balls, not to mention sort of morbid. Stop sending "let these deceased flowers signify the longevity of our relationship" messages by making paper flowers that'll last a long time if not forever (so long as you don't sit on them).

More augmented reality fun (Rock Paper Scissors Tee, Video Game Drone) and another peak into our sci-fi future.

The alluring beauty of Asian women is celebrated around the world. And they often look years younger than their true age. Ever wondered what the secret was to the gorgeous skin of Asian women? We’ve uncovered a few.

Learn how to solve the Hanayama Cast Quartet metal puzzle. Hanayama cast iron puzzles are the perfect solution to being bored. This video tutorial will show you exactly how to solve this mind boggling Cast Quartet puzzle, which is rated a 6 out of 6 in difficulty by Hanayama.

Do you dream of standing on stage in front of millions of fans with a guitar in your hand? You could make this dream come true, if only you could play the guitar! This guitar tutorial series from Robert Renman teaches you the basics of guitar playing along with a few beginner and intermediate techniques. You can learn how to play octaves on the guitar with this lesson. This octave technique is used in many songs. You can be jamming on the electric guitar to your favorite tunes, or even write ...

This video will show you how to use your makeup to apply a very colorful eyeshadow look. This look is great for going out at night, or when you just want to be festive with your makeup.