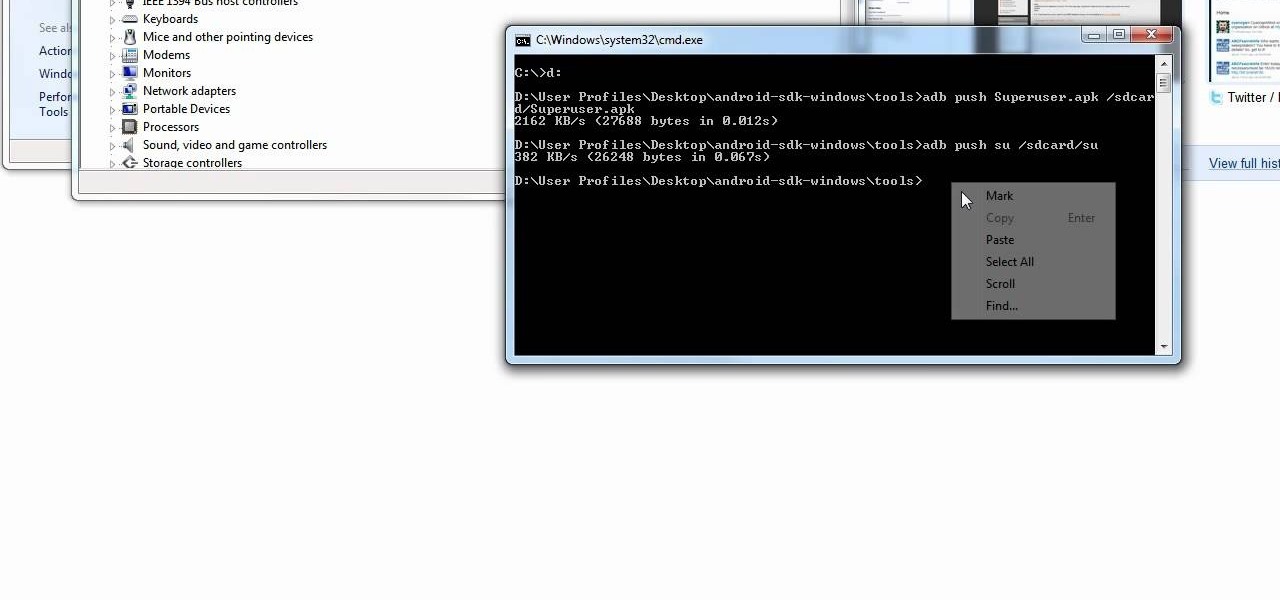
Turn the classic 70's wireless toy into a modern high-tech spy device with the instructions in this how-to video. I never picked up any chicks with it anyway. This is another fantastic video tutorial by KipKay.
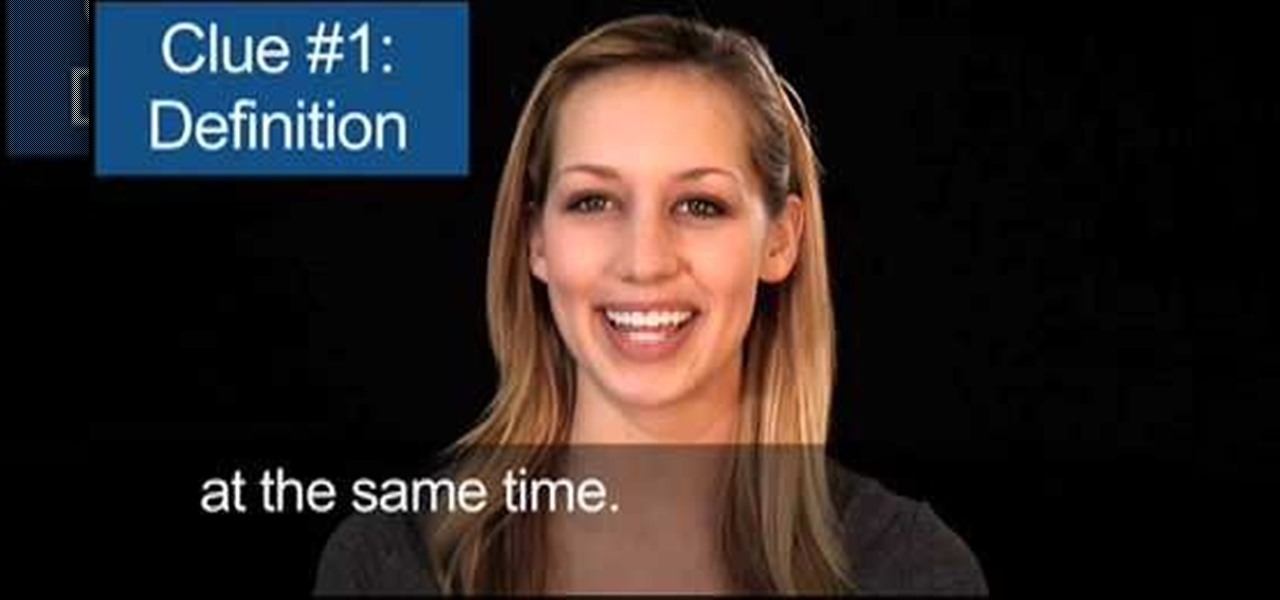
Today's word is "ubiquitous". This is an adjective which means being or appearing to be everywhere at the same time.

Using a wireless video camera and an RC Car or Truck, you can make a working spy car that transmits live video to a nearby TV or computer.

This video demonstrates how to connect a PSP to a home wireless network. To do this, just turn on your PSP, create a new network connection, and start the web browser on the PSP.

Kitchen utensils and computers, that's right! This video will show you how to increase your computer's wireless connection using a strainer!

It's no secret that iPhones are expensive. Whether or not you believe the price tag is justified, $1,000 is a lot to spend on an iPhone 11 Pro. But if you're in need of a new iPhone, you picked a great time. Black Friday is rapidly approaching, and for Walmart, many of those deals are already available.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

It's looking more and more likely that rumors stating that the iPhone 7 will not include a 3.5 mm headphone jack are true. Chinese websites Wei Feng and Anzhuo.cn reported that anonymous sources on the supply chain confirmed that the controversial design choice is a reality.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Yes, the Droid X from Motorola can be rooted, and yes, you can do it at home. Just make sure you follow the directions precisely. If you succeed, you'll have a completely rooted smartphone. eFuse doesn't matter. If you want to expand your options on Verizon Wireless's Droid X, then you just have to take a chance… use this video in conjunction with the links and description below.

The future is now, which means you can do crazy things like connect to the world wide web through your Xbox 360 and PS3. Cool, right? Definitely. But before you start surfing the Internet you'll need to adjust the settings on both your computer and gaming console. This instructional video tutorial demonstrates the process and offers helpful user tips in setting up an Internet connection on your video game system using Microsoft Windows XP.

The augmented reality cloud will probably be one of the most important pieces of digital real estate in the next few years, and China has no intention of being left out of the virtual land grab.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Earlier this year, rumors began to swirl regarding Apple's upcoming iPhone SE 2. They predicted an A10 processor and a glass back for wireless charging, all at a price point at least $150 cheaper than the iPhone 7. While it wasn't poised to turn heads like the iPhone X, it would have been a reasonable upgrade for many users looking for a more budget-oriented Apple device.

The fifth developer beta for iOS 11.1 was released on Oct. 24, and the official iOS 11.1 update was pushed out to iPhones everywhere on Oct. 31. However, that isn't stopping Apple from seeding developers with the iOS 11.2 beta already.

Android lovers out there might be sad to hear that a high-end version of the Samsung Galaxy S8+ with 6 GB of RAM and 128 GB of internal storage won't be released in the US, but rather, in China.

Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The result is RCS Universal Profile, or simply Chat, and it's finally catching on.

If you already have speakers that you love, you don't need to ditch them for an expensive wireless set for convenience's sake. With products like Chromecast Audio, you can turn any set of wired headphones or speakers into wireless versions for much less, and stream music or audio to them from pretty much any device connected to the same Wi-Fi network.

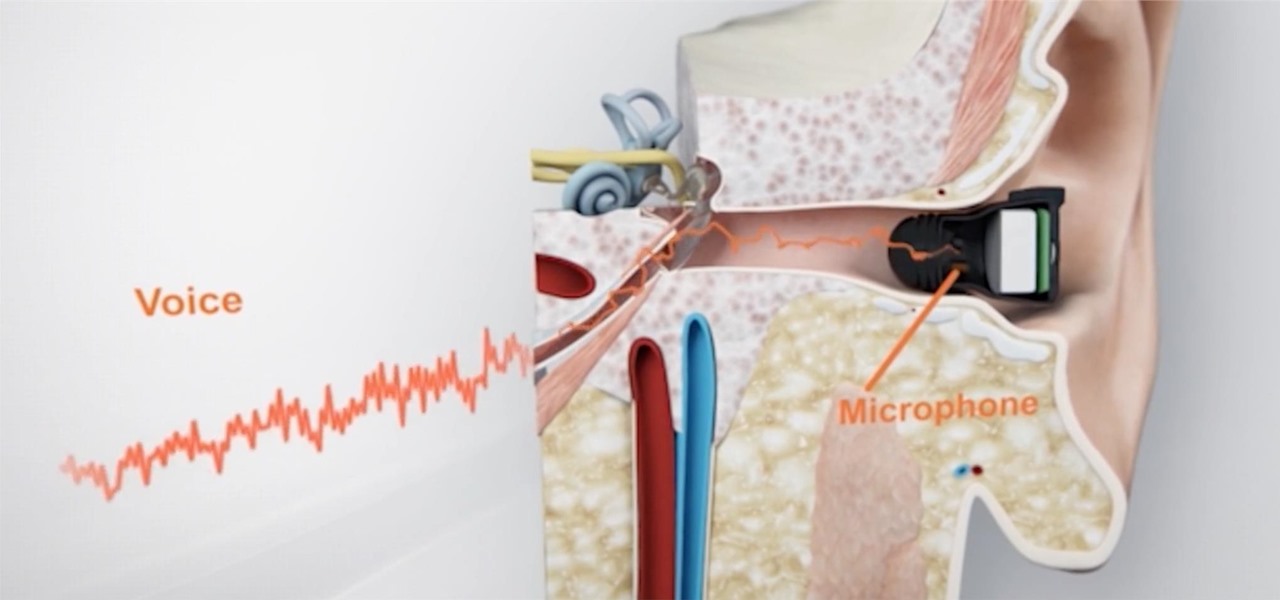
What's better than wireless in-ear headphones with noise-canceling technology? Giving them a microphone to hear you talk from inside your head. And that's exactly what you get with RippleBuds; its inside-facing mic helps keep your voice crystal clear over phone calls, and makes sure Siri, Cortana, and Google Now will always get the right command.

Update: August 1, 2014 Earlier today, President Obama signed into law the Unlocking Consumer Choice and Wireless Competition Act, making the act of unlocking your unsubsidized cell phone 100% legal.

Whether you have AT&T, Verizon, Sprint, T-Mobile, or any other mobile carrier, chances are your smartphone is sold locked to only work on that specific carrier's network. Sure, you could unlock your carrier-subsidized device, but that would mean breaching the Library of Congress' latest Interpretation of the Digital Millennium Copyright Act—making the whole process illegal. As softModders, boundaries and regulations are things that we don't take lightly, although many times we have to begrudg...

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

Most newer computers come with a webcam, but if you're using an older system, you may not have one. If you only need to use a webcam occasionally, it may not be worth putting the money into, so why not just use your smartphone? There are a few apps out there that can help you turn your phone into a super-convenient wireless webcam and save some cash.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

Suddenly, Magic Leap's lawsuit against Nreal, as well as its barrier to entry in the Chinese market, appears to be as insurmountable as The Great Wall itself.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that your iPhone has even less battery power, you're affected. But there is a fix you can implement right now.

OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.

The bootloaders on the AT&T and Verizon Wireless variants of the Samsung Galaxy Note 3 still cannot be unlocked, despite the $1,400+ bounty that arose late last year. Nine months later and still nothing. But just because we can't "unlock" the bootloader doesn't mean we can't get around it.

Remember the feeling you had the moment you removed your shiny new Nexus device from its packaging and booted it up for the first time? You swiped through the app drawer at lightning speed and thought to yourself, "This is the last Android phone I will ever need, they just aren't going to get any better than this."

International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot.

The Citrix Receiver is an app that allows you to securely access your desktop and business applications directly from your Droid Bionic smartphone. You will first need to make an account at the Citrix site, and from there you can decide what you want to have access to on your phone. On the Android app launcher, be sure to pick the Citrix Receiver app so that you can login with your Citrix account.

This how to demonstrates how to use your Apple iphone as a spy camera to spy on others. If you're suspicious, paranoid or just downright creepy, this video can show you how to convert your Apple smart phone into a device for surveillance on others.

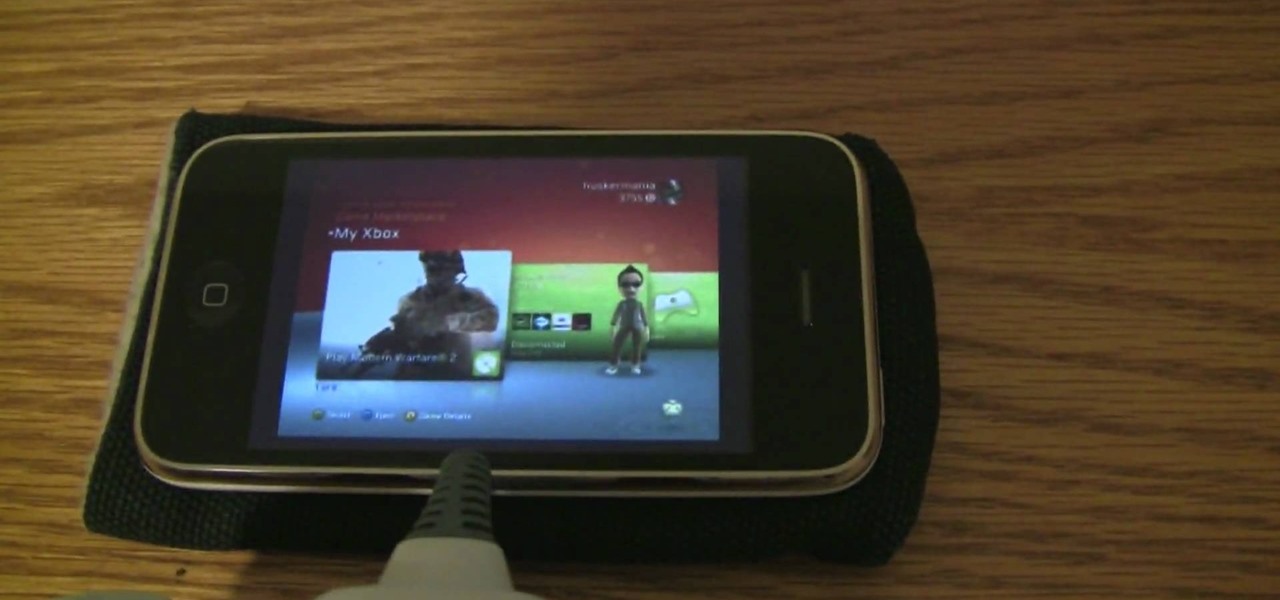
This video will show you how to play on your Xbox 360 using your iPhone 3GS. In order to do that just follow these steps: You will need to get a Slingbox Solo, a composite cable and the Slingbox Player installed on your device. Now you will need to plug in the composite cable into the Slingbox Solo and into the Xbox 360. Connect the Slingbox with the wireless router and with the internet modem. Now configure the network and connect with the iPhone. The last thing to do is to start the Xbox 36...

In this clip, you'll learn how to find and connect to WiFi networks on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

Not only can your T-Mobile G1 phone get Internet access by itself, you can also use it as a router or modem for your home wifi network. All you need is to download a single app from the market, install it, and you're ready to set up your home wifi network!

In order to make a retro wireless handset, you will need the following: vintage handset, a momentary switch, a resister, a Blue tooth headset, wires, a drill, and a blue LED and mount.