The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.
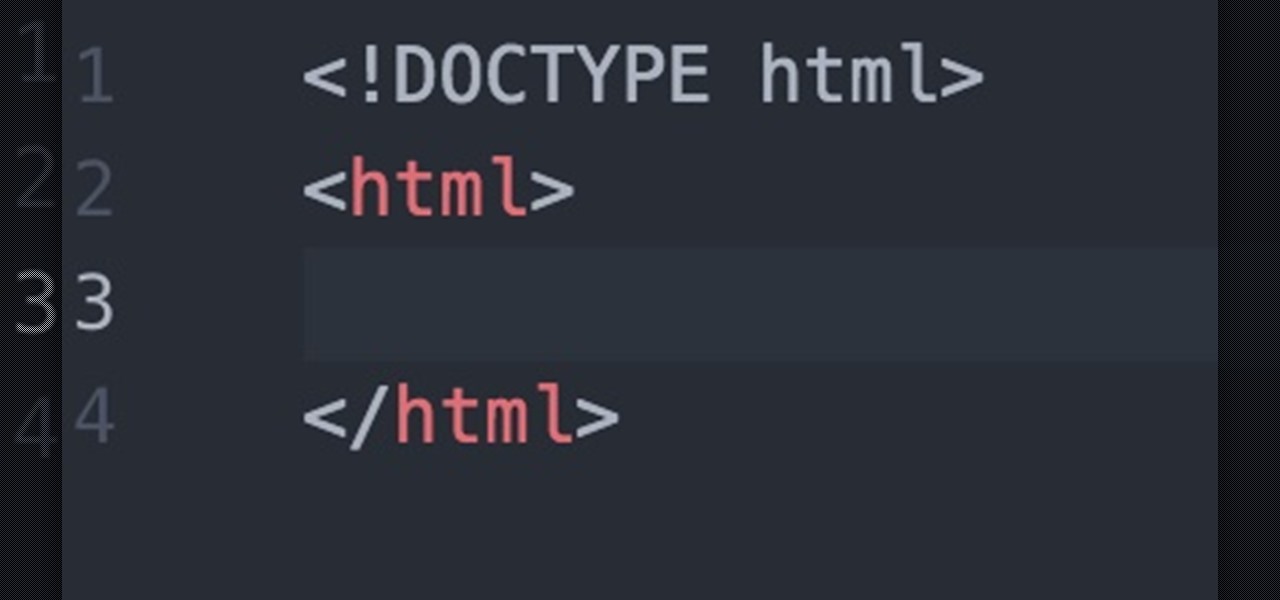
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.

If you're anything like me, you probably think it's borderline sacrilege to even think about a sandwich or a burger that doesn't have a layer of smooth mayonnaise. But I don't just keep a jar of it in my fridge for lunch—it's also there for practical purposes.

While Kobe beef cows get massaged, American dairy cows are taking a real beating. Many people are cutting back on dairy while a growing number of people are discovering that they're lactose intolerant. As the public's disdain of cow's milk grows, milk sales themselves are at a forty-year low.

Cooking with animal blood is as old as civilization itself. I promise that your ancient ancestors, no matter where you're from, didn't have the luxury of throwing away any part of the animal, including the very lifeblood that used to run through it. Animal blood, along with everything but the skin, would invariably end up in the stew.

Soup can be one of the most finicky dishes to make. While seemingly innocuous at first, the texture of this meal can change in an instant. For example, adding too many vegetables can result in soup that's too watery, such as tomatoes, which contain a lot of liquid.

Look, I'm no food snob. I once dedicated an entire day to eating only deep-fried things (butter, Twinkies, Oreos, pickles) at the Minnesota State Fair. But even I draw the line at instant mashed potatoes. I mean, why bother? It's not that hard to make perfectly delicious and fluffy mashers yourself.

Who doesn't enjoy sitting down to a nice dinner with a cocktail in hand? After a long day, a drink is a great way to unwind. Yet your favorite spirits can do more than just help you relax after work. By utilizing alcohol in the kitchen, you can enhance everything from how food tastes to your health.

Any pizza lover knows that a quality crust is crucial to the whole experience. Good pizza crust should be delicious on its own, for once you get to the edge, it will be without any toppings, sauce, or cheese to disguise a bad character. It should be redolent of fresh, good wheat and taste full-bodied, rather than flat, flabby, or metallic, the way so many big chain and frozen pizza crusts do. The exterior should be crisp, while the interior contains an airy crumb as well as having a tender, s...

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

One of the most frustrating things on the Internet are sites that make you register just to view content. I'm not talking about paywalls—I mean the sites that make you give them personal information to look at free articles or forum threads. Most people are uncomfortable with this because a lot of these sites either spam you themselves, or sell your information to someone else who will.

As people continue to upgrade their PCs to Microsoft Windows 8, more and more developers are adding content to the Windows Store. While the offerings are not as vast as Google Play or the iTunes App Store, it does have some solid apps for both productive users and those looking to just while away the time.

Store-bought fake blood isn't too expensive, but the consistency and color are always the same. Real blood varies, from bright red when oxygenated (arterial blood) to deep, dark red when deoxygenated (venous blood), and it can be either thick or thin. So to achieve the best special effect, you're better off making a batch of DIY fake blood yourself to get the look and texture you're going for. And it's very simple to do.

Make sure your next apartment rental goes smoothly by properly checking the property before signing a contract. This way you will avoid unexpected disappointments or problems that you were not aware off. Moving is hard enough, give yourself all the advantage you can by going in prepared.

This particular video series covers what is called the natural facelift. It is essentially an intense facial that is more involved and has agents that target those trouble areas where wrinkles tend to occur more often such as around the eyes and mouth. This is a fantastic alternative to the pain and cost of surgery. Instead of weeks of recovery you have no recovery time and see effects almost immediately. It also removes the risks of a surgical procedure and is very relaxing as well. Check ou...

Election Day is today, and Apple News is making it easy for you to stay informed with real-time results for the 2024 presidential election through a new Live Activity feature on your iPhone, iPad, or Apple Watch.

The battle for augmented reality and social media supremacy starts with the people working behind the scenes, and this week Snap pulled off a telling win that could indicate a shift in the AR space.

After years of testing and modifications, the US Army is moving forward with its customized version of HoloLens 2 from Microsoft.

It looks as though the novel coronavirus and social distancing guidelines are here to stay for a while. So companies of all sizes and industries are scrambling to adapt to a new reality in which everything from morning meetings to large-scale presentations are done entirely online. It looks like this is going to be the new normal for the foreseeable future.

With so many competing outlets to reach people, accessing inboxes remains one of the most effective forms of communication. Yet newsletter creators run into a constant problem: bounced emails.

Even under normal circumstances, it's almost impossible to speak to a representative for a government agency or company in just one try. Many systems will put you on hold for long periods or ask to call you back when someone is available, but there are still some out there that just give you the busy signal over and over again. In those cases, there's a jailbreak tweak that can help.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out these seven free multiplayer games that only require one iPhone or Android device to play.

The landscape of podcasting has exploded in recent years, with everyone from dedicated longtime podcasters reaching the mainstream spotlight, to traditional media personalities moving from TV, radio, and newspapers to grab a slice of the listening pie. The good news is that the barrier to entry is relatively low, so even if you're not a celebrity or media luminary, you can still get your voice out there by starting a podcast.

We've been so worried about volumetric scans possibly robbing celebrities and performers of their agency and right to control their image that, somewhere along the way, we forgot that scans may not always be necessary to produce passable holographic performances.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

Google Images, TinEye, and other reverse image search engines can help you find where images appear on the internet. You can discover what TV show or movie an image comes from, who took a photo, and if the profile picture of someone you're talking to online is really them, among many other uses. And there's a shortcut for iOS that makes running a reverse image search easy.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

Spam calls are one of the most annoying things to happen in the world of smartphones for more than one reason. Not only are they bothersome, but they can also be dangerous to people who don't know any better. Google has come up with a crafty solution known as "Call Screen" to let the Google Assistant handle the call for you while you listen in on the caller like a stealth ninja.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.

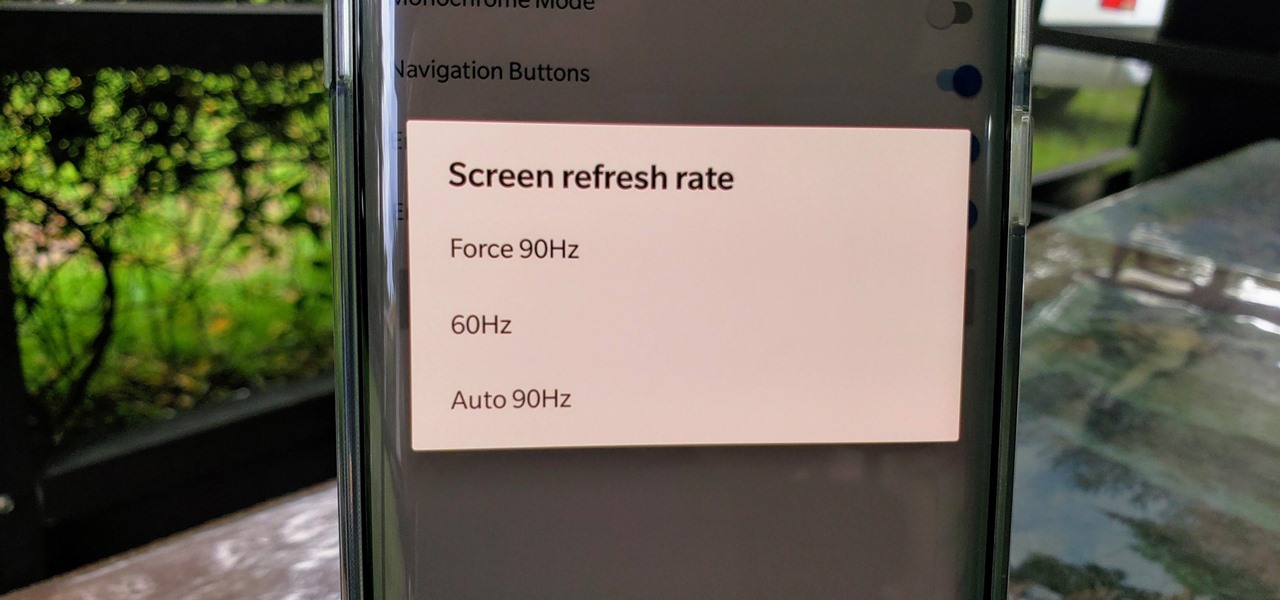
One of the standout features of the OnePlus 7 Pro is the 90 Hz display. A higher refresh rate means smoother gameplay for all your favorite games, which is precisely what you'd want out of your gaming experience. However, not all games play nicely with these higher refresh rates — but luckily, there's a pretty simple fix.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.