
How To: Stop laughing in inappropriate situations
Have you ever found something funny in an awkward situation? When you feel a laugh coming, it can sometimes be hard to avoid. Check out these steps to stop your laugh before it gets you in trouble.


Have you ever found something funny in an awkward situation? When you feel a laugh coming, it can sometimes be hard to avoid. Check out these steps to stop your laugh before it gets you in trouble.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a motorcycle camera mount for under five bucks.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to homebrew and hack the PSP.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to analyze packet captures and network taps.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to extract Windows executables from packet captures.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to backup and load Wii games for the Dolphin Emulator.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a free XMPP/Jabber server in ten minutes.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to track a USB device.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to edit Super Mario World levels with Lunar Magic.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a mini multi-touch table and photo stitch.

Learn how to play "Heal Over" by KT Tunstall on guitar, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

This is the basic prayer that should be meant from your heart and soul, and not just saying the words from your physical tongue. A true redeeming confession to the lord Jesus Christ, asking Him to come into your heart as your personal lord and savior, asking Him to forgive you of all of your sins, rejecting all evil from continuing to be involved in your life, and rejecting this world's ways, and listening and following God's rules and directions.

Southwest Yard and Garden featuring John White, Dona Ana County Extension Agent, hosts a 6 minute clip with co-host Master Gardener Valois Pearce both of Dona Ana County, New Mexico host a short web show featuring plants that can easily survive on smaller amounts of water over typical plants. They begin by discussing the full sun Ice Plant, which comes in many species and colors as well as their hardiness, but unfortunately are easy targets for wildlife. They then move onto the Gopher Plant, ...

John White, a Doña Ana County Extension Agent, highlights a new section on the show - a monthly checklist for the garden. This time, he talks about what to do in your garden in the month of February. The checklist includes planting dormant plants, pruning with a purpose and applying herbicides and pesticides. He shows us various types of dormant plants that can be purchased from nurseries in February for planting such as potted, bare-root or root-balled plants wrapped in burlap. As for prunin...

Doña Ana County Extension Agent John White and Master Gardener Benny Knudsen look at stone fruit trees on their tour of the "Garden of Weeden". The Mariposa Plum, the dwarf Stella Sweet Cherry, Elberta Peach, Tilton Apricot and the almond tree (which also belongs to the stone fruit family) are featured in this segment of Southwest Yard and Garden series. The suitability of these trees for a small garden is mentioned. Besides this, also discussed is the problem of late frost and its effect on ...

Master Gardener Rosamarie Maddox asks John White, Doña Ana County Extension Agent, about problems facing her pecans, grapevines, and native shrubs. An unidentified insect found on her pecan tree is identified by John White as a Twice Stabbed Ladybug. This ladybug is a useful insect that often over-winters on the tree and helps takes care of the aphid problems faced by pecans. Pink fuzzy coating on pecan nuts is also brought up. The coating is normal for pecan and contains bitter tannin. Too m...

There are two parts to the StormShield product: The server components (including the relational database and server) and the various agents that run on each endpoint. Among other things, the agent contains a host-based firewall and policy engine that can be customized to control applications and particular endpoint device features such as USB peripherals and registry entries. So watch this tutorial and learn how to protect your PC computer with SkyRecon's StormShield.
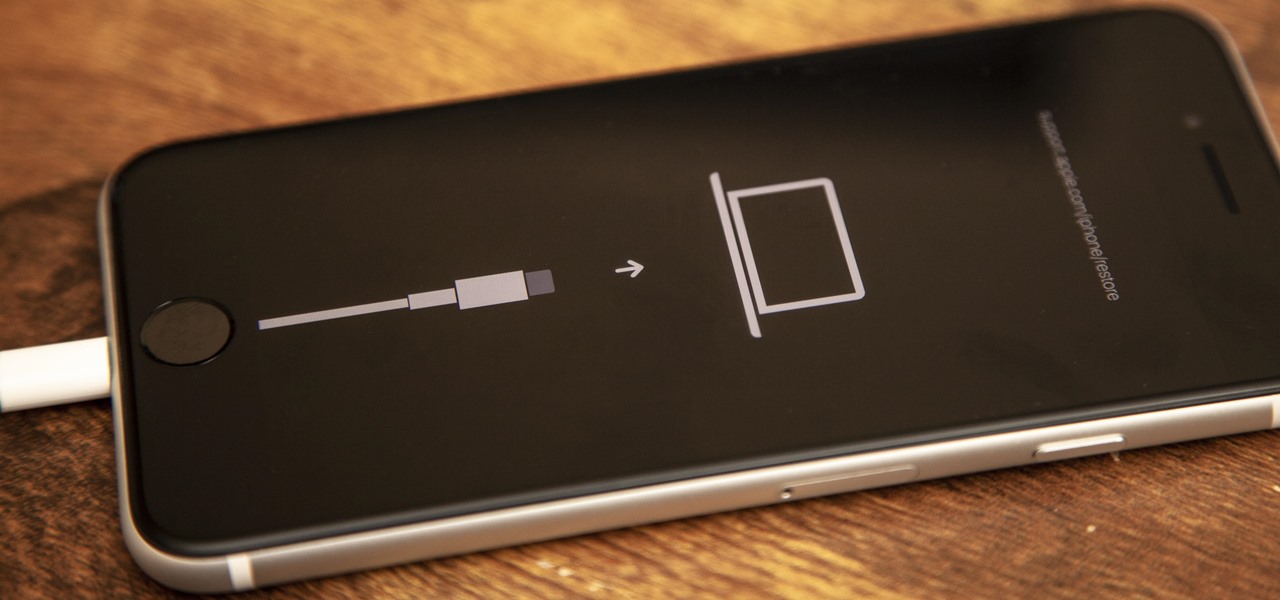
If your new 2020 iPhone SE is frozen, unresponsive, or won't load the system, and a standard power down and up procedure didn't work, there are few more things you can try. Force-restarting the device may do the trick, recovery mode is a last-ditch option, and DFU mode is your fail-safe.

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

Apple's update for iOS 13 is not without bugs and other issues, and if those problems become annoying or impede your ability to use your iPhone like usual, you may want to downgrade. Hundreds of new features may not matter if you can't use your iPhone like it's meant to be.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

This is about how to make a rabbit become less wary of you and more trustful with you also. I myself have a Dutch that was released by its previous owner, then I rescued it. She never wants to be took out of her cage, but now she doesn't mind as long as I'm gentle and nice.

Purify water 3 different waysThere are three water purification methods demonstrated: Chlor floc tablets, 2% tincture of iodine and a MSR hand filter.Gather water into your plastic bottle. Add one chlor floc tablet to one liter of water. Close the top and shake the bottle for one minute. Wait seven to ten minutes. The floculation agent in the tablet takes the dirt out of the water so that it can be separated. Strain the water using a bandana over the cup to trap all loose sediment. The water ...

This is a steamy part of Heavy Rain for PS3. Steamy and sexy. But this is edited for nudity, so don't worry about seeing anything you shouldn't. See how to beat Chapter 5 - On the Loose.

in this episode of Heavy Rain, you confront the Shark. Just try not to get yourself killed when he pulls out that shotgun. Then, are you going to kill him, or are you not? See how to beat Chapter 4 - The Shark.

Now that the identity of the Origami Killer has been revealed, it should be easy to find him. In this walkthrough of Heavy Rain (PS3), you'll be in the killer's apartment. See how to beat Chapter 5 - Killer's Place.

Is the real killer captured now, or is a different man? Will you leave the case or will you continue the hunt on your own? The Origami Killer may still be out there, and it's up to you to find him. See how to beat Chapter 5 - Solving the Puzzle.

The city is full of reptiles, and in Heavy Rain, the lizard is the most treacherous of all. See if the lizard can get you one step closer to solving the murder mystery of the Origami Killer. Porcelain isn't what it used to be. See how to beat Chapter 3 - The Lizard.

Butterflies are usually sweet and innocent, but not in the downpour that is Heavy Rain. In this PS3 walkthrough, see what's up with the Butterfly and if you're ever going to catch the Origami Killer. See how to beat Chapter 3 - The Butterfly.

Can't sleep? Of course you can't, not with a stage called "Sleepless NIght" in the video game Heavy Rain for the PS3. Watch a walkthrough of this level and see if you can get some zzz's, or see if you should be sleeping. See how to beat Chapter 2 - Sleepless Night.

This level of Heavy Rain has you in the Lexington Station, where hopefully you can make it through the crowd without embarrassing yourself. Watch the full video walkthrough to see what happens, and how to continue on. See how to beat Chapter 2 - Lexington Station.

Nothing can beat a father and son. Check out this Heavy Rain video walkthrough for the PS3 on "Father and Son". Do you think you're getting closer to catching the murderous Origami Killer in this level? See how to beat Chapter 1 - Father and Son.

Clean out the empty bottle that you are going to use. You can use a white dish-washing soap bottle or a cleaning agent bottle. Just make sure it is empty and clean. Use the pen to draw a wide rectangle that measures 3 inches long by 1/4 inch wide onto the bottle. The teeth you are making are going to stretch from either side of your canine teeth above and over your two front teeth. This will help them be more secure. Draw this onto a part of the bottle where it is curved. Draw two vampire tee...