As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

HTC is heading in a strange direction lately. Instead of releasing just one flagship in the spring season, they released two top-tier phones, with one having last year's specs and both having last year's design. They were also supposed to manufacture both the Pixel 2 and 2 XL, but Google was unimpressed by the HTC-made Pixel 2 XL and looked to LG for the bigger device. Now it seems, HTC isn't finished yet.
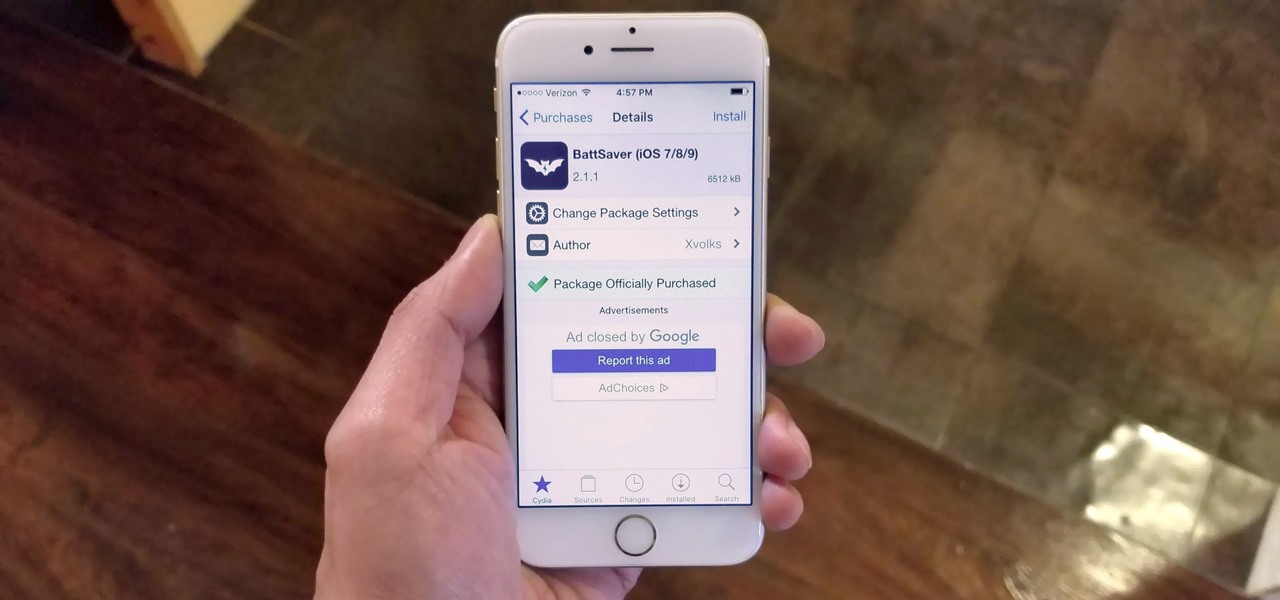
While widely known for its massive collection of free apps and tweaks that let you fully personalize your jailbroken iPhone, Cydia also comes laden with packages that can be purchased to take customization to a whole 'nother level. Similar in function to the iOS App Store, buying an app in Cydia is simple and relatively safe.

Augmented and virtual reality continues to be a hot commodity among tech investors, with more than $800 million invested in AR/VR companies in the second quarter alone and global tech leaders like Samsung focusing their investment strategies on the emerging field.

There are a lot of exciting improvements in store for Siri in iOS 11. Apple showed off some of the highlights at WWDC, but there are five changes in particular that you don't want to miss.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

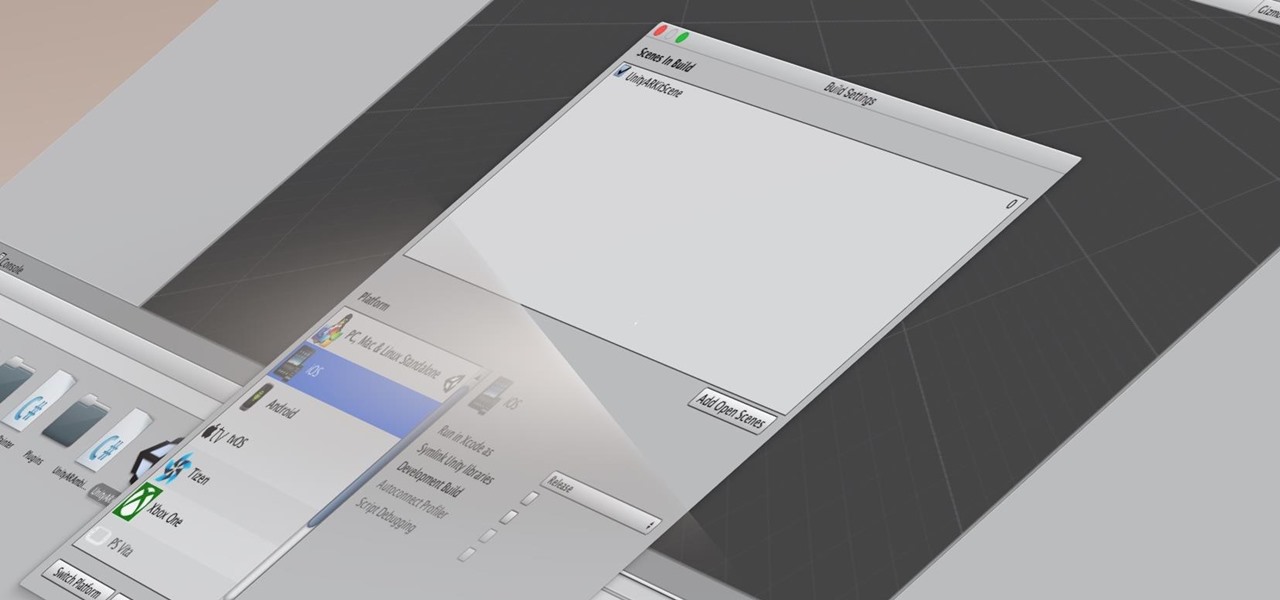
Many developers, myself included, use Unity for 3D application development as well as making games. There are many that mistakenly believe Unity to be a game engine. And that, of course, is how it started. But we now live in a world where our applications have a new level of depth.

I haven't bought into Apple Pay just yet, but I do love the idea of having quick access to passes like loyalty programs, boarding passes, and my Starbucks card. However, for some users, it's impossible to open these passes stored in Apple Wallet on the iPhone's lock screen. While it's not totally obvious, or even ideal, there is a way to get those Wallet passes back on your lock screen in iOS 9 or iOS 10.

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

Ever since the Google Play Store removed its "Designed for tablets" section, it's been a lot harder to find good, tablet-optimized Android apps. Not that it was all that great to begin with considering that they used to list apps like Facebook and Twitter, which only have oversized phone UIs on tablets, not actual customized UIs.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

Chestnuts are roasting on an open fire, which can only mean one thing: Christmas is nearly here. It's the time of year we're supposed to spend with family and friends, but usually we spend it stressing out over what to buy everyone on our list without going over budget, or shopping for decorations or holiday-friendly food items.

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

Having a store-bought cold pack on the ready is the perfect solution for minor bumps, bruises, sprains, and strains, but why spend money on bright blue ice packs when you can make your own right at home?

I was bored when I found this piece of literature: ==Phrack Inc.==

If you ever need to make calls and/or send texts to the U.S. or Canada from abroad, or even just receive them from those locations, there's an easy way to do so without breaking the bank. In fact, it's free, and all you need is a smartphone, computer, and some free tools.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device.

Whether it's the start, middle, or end of summer, it's prime-time grilling season. If you find yourself without a grill, however, it may seem as if half your summer plans of swimming by the pool while stuffing hot dogs in your face could be ruined.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

Super Bowl Sunday is just around the corner. With 111.5 million viewers tuning in last year (112.6 if you count streaming), which broke another record that it previously set for the most-watched television event in U.S. history, it's safe to say that most of us will be watching Super Bowl XLIX on February 1st, 2015, whether via TV, web, or mobile.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

Many of the beauty products you buy at drug and department stores are loaded with potentially toxic ingredients like parabens, while their active ingredients are made of things like glycolic, lactic, malic, and alpha hydroxy acids and retinoids, which are all derived from foods.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

With its growing popularity, it's clear that the Chromecast isn't going away anytime soon, with options for casting games, cloud files, music, and much more. But not all content providers are in a hurry to add support for the device, and SoundCloud is one of them. While My Cloud Player is by no means an official SoundCloud app, it comes pretty darn close.

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

During a contest in 2010 regarding which country Justin Bieber should visit next on his tour, North Korea won by a landslide. Unfortunately, he never went, and that's partly because nobody in the internet-less dictatorship probably voted. Instead, the contest was rigged by 4chan members and a few playful bots that voted for NK hundreds of thousands of times. What this shows is that not only is Justin Bieber an asshole, but that bots can be used as a very powerful tool—not only to cause mischi...

Why is transferring contacts from an old smartphone to a new one still insanely difficult? I can check my bank account, upload a picture to Instagram, email someone across the globe, and check the weather forecast on my phone—all in under five minutes.

There are two options when it comes to a dent in your car — live with it, cringing each time it enters your view, or get rid of it. While the latter is obviously the best option, most of us will probably just live with dents and dings since spare money is better spent on the actual functionality of the vehicle. However, there is a way to knock out automobile dents yourself with relatively little cash in the bank.

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities. But don't wait—start submitting your own projects to the most appropriate World now!

It can be a real challenge to plant your seeds in evenly-spaced lines. In this episode of Growing Wisdom, Dave Epstein will show you how to use a four-row pinpoint seeder to plenty your seeds. Using devices like this, planting seeds in even lines will be a whole lot easier.

Play "Scream" from High School Musical 3, an acoustic guitar tutorial. Follow along with this demonstration, tabs & lyrics here:

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

While it's rare, there could be a day when your iPhone 12, 12 mini, 12 Pro, or 12 Pro Max isn't responding, where taps and swipes on the screen do nothing, and the Side button won't let you force a restart. The culprit could be any number of problems, from corrupted files to beta software or even manufacturing issues. But one thing is certain: recovery mode could help you get back up and running.

With the whirlwind of noise surrounding the COVID-19 virus sweeping the nation, it's not hard to default to panic mode. One of the best ways to avoid panicking, however, is to follow trusted sources of information and avoid all of the opinions and trolls that don't reflect reality.

Alongside Sesame Street, the Dr. Seuss universe has been a constant presence in the formative years of several generations of children in the US.