The iPhone X has a new unlocking mechanism called Face ID, which replaces the old Touch ID system since the phone no longer has a fingerprint sensor. The way it works is simple — you just look at the phone, it recognizes your face, then the system unlocks — so Apple deserves the praise they're getting for it. But did you know you can get almost this exact same feature on any Android device right now?

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

If you're not one to trust you digital SLR camera's automatic focus options, then the only thing you have to do is go to manual mode. With the Canon EOS 7D, select the Manual AF Point Selection and take control. It allows you to pick the area you want to focus on.

Learn how to bake a scrumptious apple crisp with this cooking video. This apple crisp recipe is brought to you by Sarah Bacon on How2Heroes. Search How2Heroes on WonderHowTo for more cooking videos.

You don't need a florist to make beautiful flower arrangements. Learn how to arrange a dozen roses with this free video series about arranging roses in a vase.

Ever tried to sign up for auto-insurance, or some other thing that required your VIN number, and ran around trying to find it in frustration? Well frustrate no more good people! This video will show you all of the various places that you can locate your VIN number! Trust me, there's a lot....

Hanging out with the folks can be fun. Really, trust us. This video gives tips on how to obtain a better relationship with your parents.

Learn how to kickbox from the trusted folks at Expert Village. Strap on your gloves and get in shape with some simple tips and workouts. This video is a culmination of moves that you can learn individually as well.

Steer clear from empty flattery and malicious social engineering with these tips on how to avoid a player.

Keep your possessions safe from thieves with these tips. You Will Need

Discovering your partner's affair can be devastating, but it doesn't have to mean the end of the relationship.

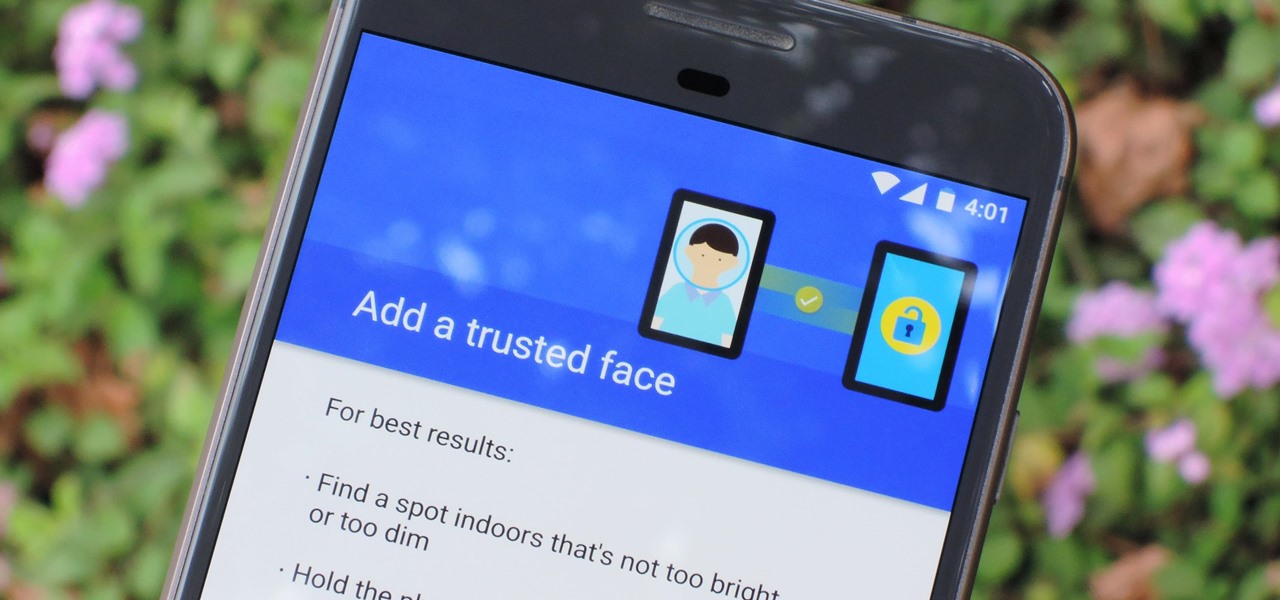
The OnePlus 5T was just released, and it's packing several new useful features. While many OnePlus 5 buyers are feeling frustrated with the quick release cycle, lots of fans are still clamoring to buy the new device. Aside from the larger screen, most of the buzz around the 5T has centered around the new face unlock method. Thanks to a clever hack, you can now get this feature on almost any phone!

This could happen when you trust a guy to hang out wet clothes. Ladies, beware, guys simplify housework simply because they don't care of it's a chore they just don't want. Watch and learn to be creative about the ways you spice your every day chores up. Most of all, laugh your head off.

If you were born with skinny, thin lips, then lip plumpers are probably your best friend. We get it: Plump, pillowy soft lips are gorgeous, but at the same time we don't know if we trust all those gnarly ingredients that most lip plumpers contain.

Rapper Lil' Wayne has admitted he can't read, instead citing that his musical prowress comes naturally to him. While this may work for the musician, most piano players, singers, and sax players can benefit from a lesson in music theory or two.

We all love primping products, but what girl doesn't want to save a few bucks when she can? While lots of beauty companies will advertise that they have the best curling iron for you to achieve those Kate Hudson beachy waves, the truth is that you really don't need a curling iron at all. In fact, to get your hair bouncy and curly, all you really need is a flat iron.

Drawing a perfect cylinder is hard. Heck, drawing a damn circle is hard for most of us. Which is why you shouldn't be ashamed of using some extra tools when formulating one on paper.

If you've ever owned a leather purse, you know that ink or pen stains are a pain in the ass. If you've ever owned a designer leather purse, then you've probably even cried over an accidental stain (oh no! My $3,000 purse is ruined!). Removing ink stains from leather is thought to be extremely difficult, but there is a way to do it quickly and easily.

Purchasing an HDTV, plugging all the gizmos in, and turning it on to watch without any tweaking is like buying a table from Ikea and assembling as is: it works, and it looks good too, but honestly, it can look better with a few tweaks.

Do you die over chocolate and can't think of any better way to vacation than simply turning on an episode of "Friends" and gorging on bag after bag of Godiva chocolates? We hear you.

This how-to video explains the importance of choosing a quality car mechanic and shop. This video is by AAA. They say that by investigating a shop before you trust them making repairs on your car, you can save a lot of money later if they make a mistake. John Neilson of AAA explains to look at the cleanliness of a shop because if it is clean then they probably take customer service very serious. If you follow these easy instruction you will be assured that you can select a quality car mechani...

This video explains how to keep a dog calm and to be less reactive to objects that it is not used to including baby strollers, hats, canes, and a few other items. Starting with a few tips on how to get a dog used to the item in question such as keeping a leash on the dog and far enough away from a person the dog trusts and loves so that the dog will associate the object with a person. There are many aspects when training a dog in this way and each method can be tried if one does not work. Aft...

If you're a LARP maniac, or just a fan of LSD-themed (Latter-day Saint) games and activities, then this tutorial is just the ticket. Check this video out to learn how to make a foam-padded sword that is easy and inexpensive. This level two boffer sword will take care of your LARPing opponents like Chuck Norris. If you're a fan of live action role-playing, then this boffer sword is just the beginning, trust me. There's a level three boffer sword, too.

In this online video series learn from expert freelance florist Amelia Tallman as she teaches how to design floral arrangements, how to use floral foam, and what tools to use when creating an arrangement.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

So it's 2017 and there are no flying cars and teleportation devices around, but there might be holographic smartphones sometime soon. As cool as that sounds, should we trust a holographic smartphone from a company that has never made smartphones before?

Things aren't looking good for Uber after its driverless experiment in Pittsburgh soured relations with local authorities. Surprised? Me neither.

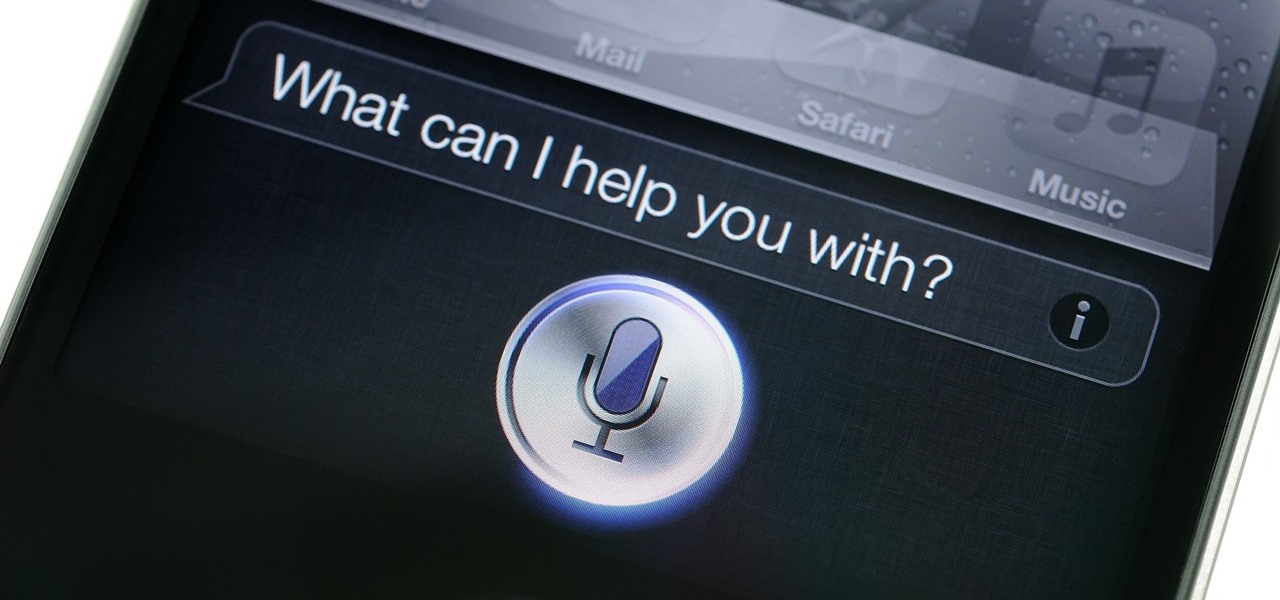
If you follow tech, you're probably familiar with Siri, Apple's personal voice assistant, which has been integrated heavily into iOS ever since iOS 5. But you might not have known that Siri is capable of performing some tasks when the iPhone is in a locked state. The default state of iOS is to allow access to Siri from the lock screen, most likely for the convenience of hands-free access to the phone.

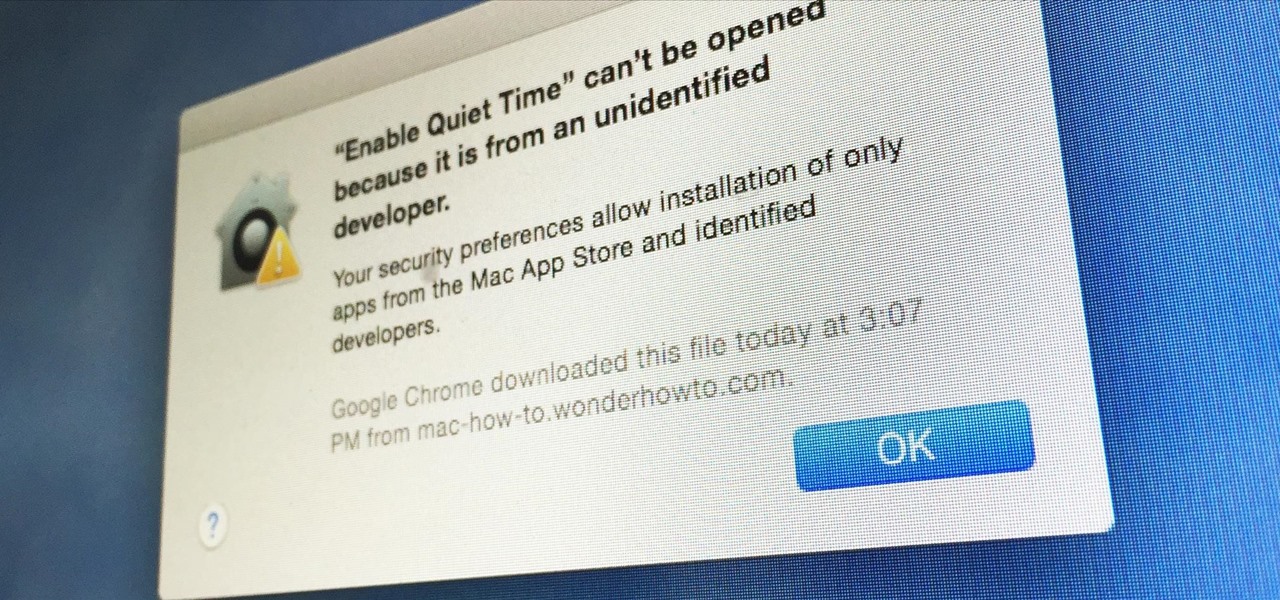
Apple has a built-in way to protect you from opening up potentially malicious apps on your computer in Mac OS X Lion, Mountain Lion, Mavericks, Yosemite, El Capitan, and macOS Sierra. This setting, named Gatekeeper, will never stop you from installing apps from the Mac App Store, but it could from anywhere else. If it's an app you're sure you want to install on your system, here's how to do it.

Leaving your Wi-Fi radio "on" allows your smartphone to auto-connect to trusted wireless networks in lieu of using cellular data, but it also consumes battery power while it's constantly network hunting.

Telling others that you have crabs isn't always a bad thing. Especially if those crabs of yours are baked into crab cakes! A delicious staple on the east coast, and a favorite in the Hamptons, crab cakes are the ultimate summer dish.

Here at WonderHowTo, we're used to seeing zillions of hairstyling tutorials that focus on "beachy, summer hair" or "bohemian braids a la Lauren Conrad." Summertime is a great time to experiment with your hair, but it seems that many of us lean on our braids and waves like LBDs.

One of the most challenging, arduous parts of gardening is weeding vegetables that are close to the ground. Cabbage, for instance, leafs out near the earth and can be fiendishly tricky to weed. In this Growing Wisdom gardening tutorial, you'll learn about some of the tools that can help you weed those hard-to-reach spots without breaking your back in the process.

Do you actually trust your friends to not mess around with your files when you let them check their email or get on Facebook on your computer or laptop? You should think long and hard about that. If you insist on letting anyone get access to your computer, you should check out this tip from Tekzilla. Learn how to prevent people from messing with your files. Keep your files from being deleted or renamed, and keep them secure.

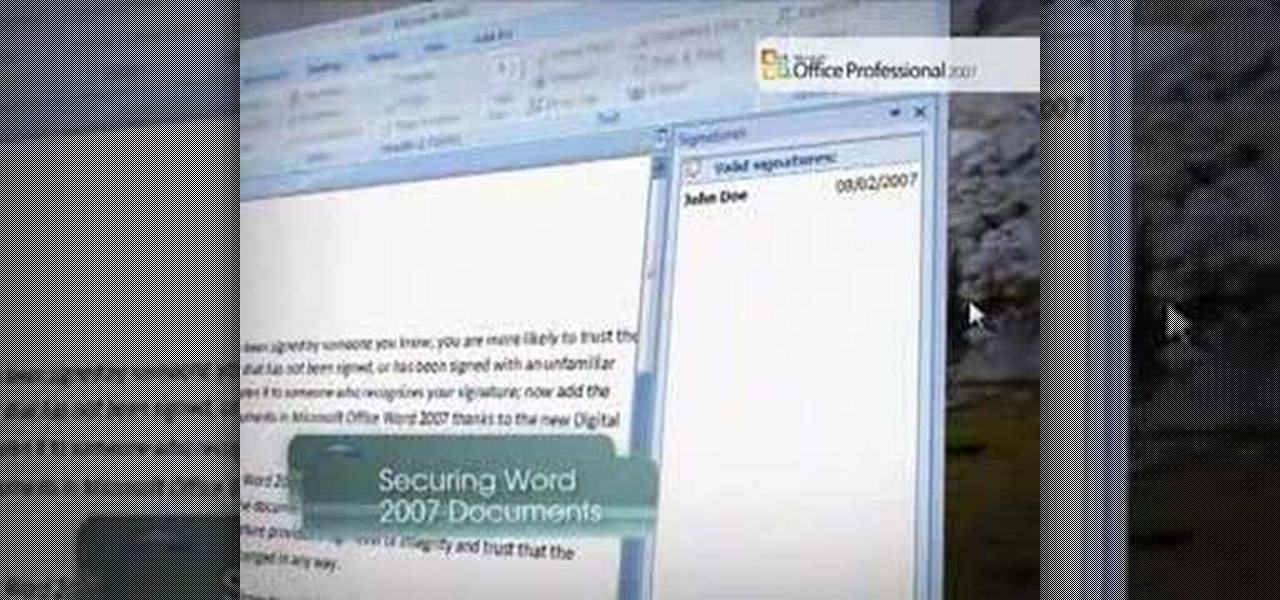
Securing Microsoft Office Word 2007 documents with Digital Signatures - When you receive a document that has been signed by someone you know, you are more likely to trust the contents than those of a document that has not been signed, or has been signed with an unfamiliar signature. Signing a document validates it to someone who recognizes your signature, now add the same degree of integrity to your documents in Microsoft Office Word 2007 thanks to the new Digital Signatures feature. For more...

Add a little South American flavor to your wrist by learning to make your own Peruvian bracelet. You'll need some heavy string and some macramé skills to craft your own Peru-style bracelet, but trust us—it's not hard. Just follow along with the video and see how easy it is.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

Everyone benefits from positive coping strategies when dealing with divorce – learn how. Step 1: Stay in touch with both parents

If you're trying to learn a new skill, you wouldn't want to waste your time learning from someone with sub-par experience. No, you'd want to learn from the very best of the best to ensure you're getting a quality education.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.