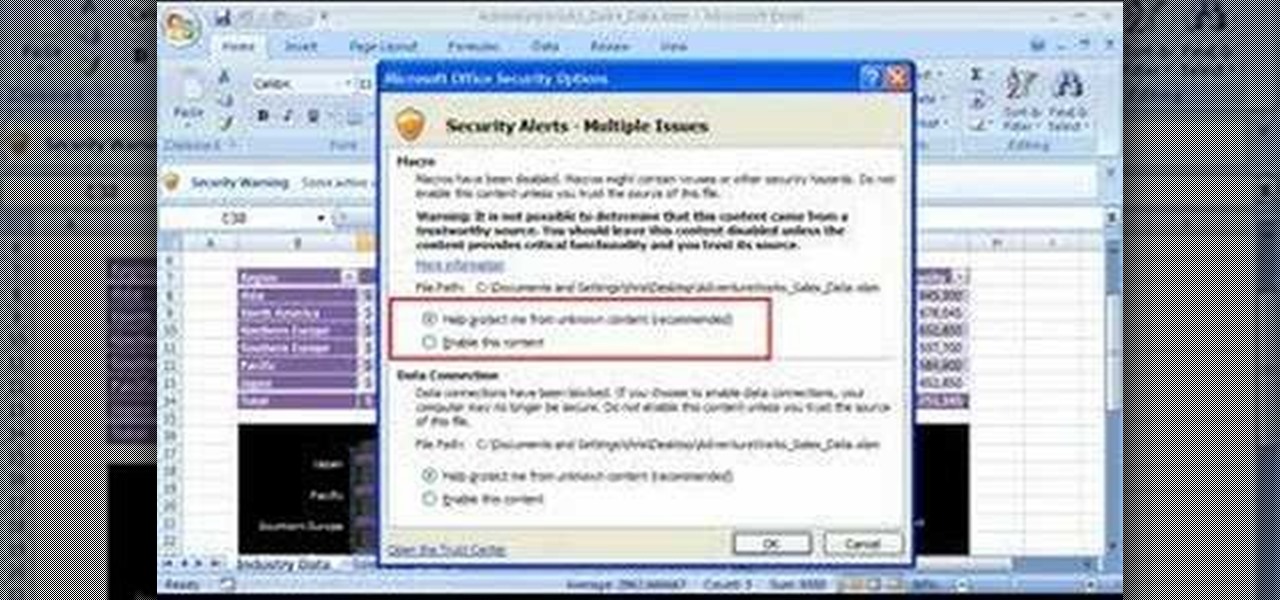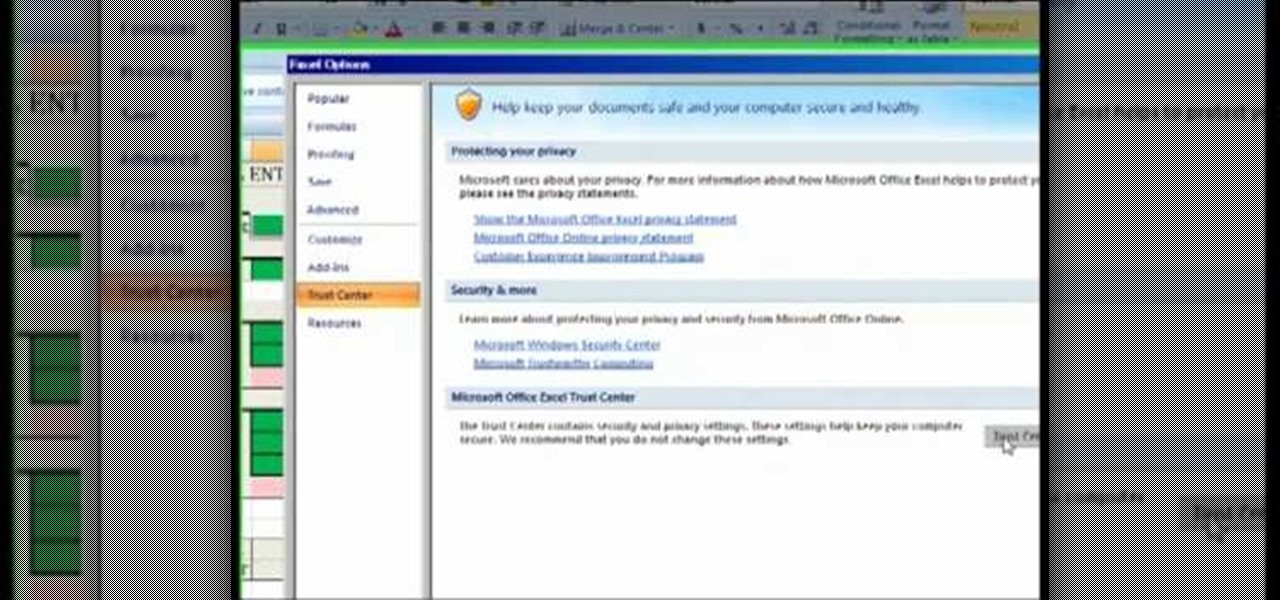
The Costsheet demonstrates how to enable macros in Excel 2007 to run correct spreadsheets. First, open up the spreadsheet. Make sure that the macros are enabled. If they have not, enable the macros by placing them in a trusted source by saving them in a particular folder. You can also choose to recognize the publisher as a trusted source. Click the office button and scroll down to Excel options. Click on the trust center option and go to trust center settings. Then, view the trusted locations...

Want to learn what it really means to put your faith in someone else? Try a trust fall, where one person falls backward, depending upon another to catch them.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to backup Wii games to SD to play in HD.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to obscure your OS fingerprint.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to boot Windows from a USB flash key.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to map networks with Spiceworks.

There's more to earning someone's trust than simply shaking their hand, especially if you're not particularly trustworthy. Your body language doesn't reveal your thoughts, it reveals your intentions, and sometimes intentions are better left unrevealed. Psychopaths, take note...

Trying to trust again after your loved one fell into an emotional affair? It can be incredibly difficult, so here is some advice from two "love experts" who say if you can't get over it, to cut that person loose. Watch this YourTango advice video to see why it might be the best alternative.

Not sure what to do when you get a security warning about a macro? What are macro security settings, the Trust Center, and Trusted Locations anyway? Watch this instructional video to learn how to enable macros and make informed security decisions that can help you keep your computer safer while you work in Microsoft Office Excel, Outlook, Word, Publisher, PowerPoint, and Visio 2007.

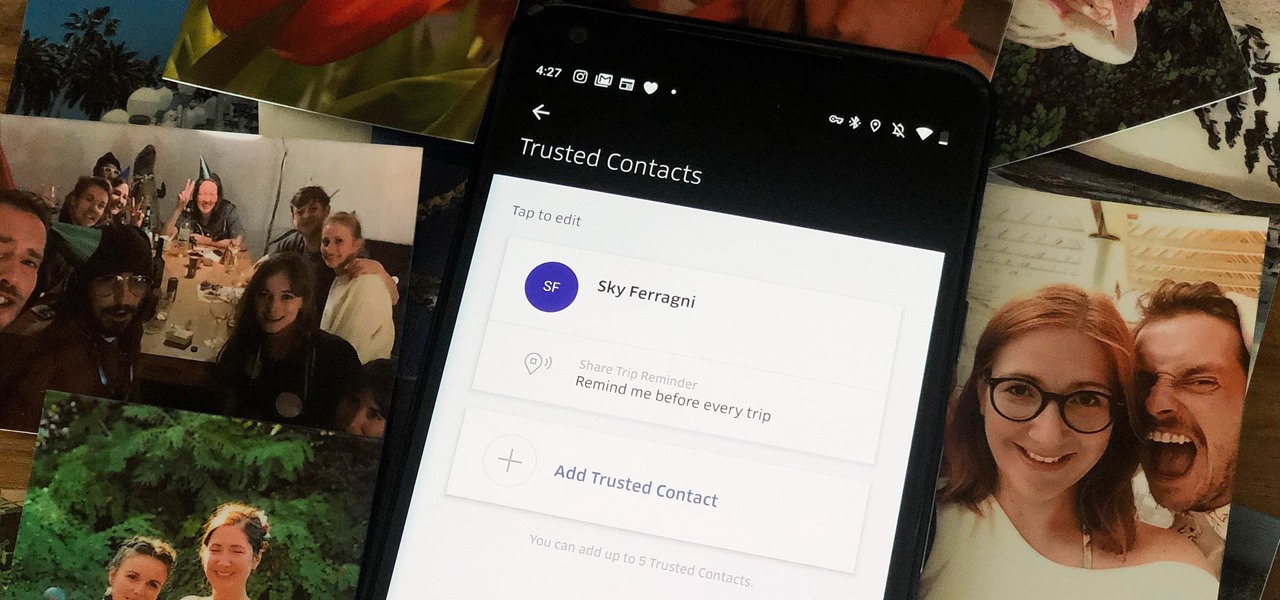
When you're riding in an Uber, on your way to meet family or friends, they may want to know where you are exactly to see how long until your arrival. On the other side of the coin, there may be times when you want to tell family or friends where you and your Uber car are without them asking, like when you're in a dangerous situation. Uber makes this easy, as long as you set it up first.

According to a new study from the Reuters Institute and the University of Oxford, people are getting their news from ... unexpected sources. Put away your CNN app and stop checking the New York Times because a familiar app is now keeping you up to date on current events: WhatsApp.

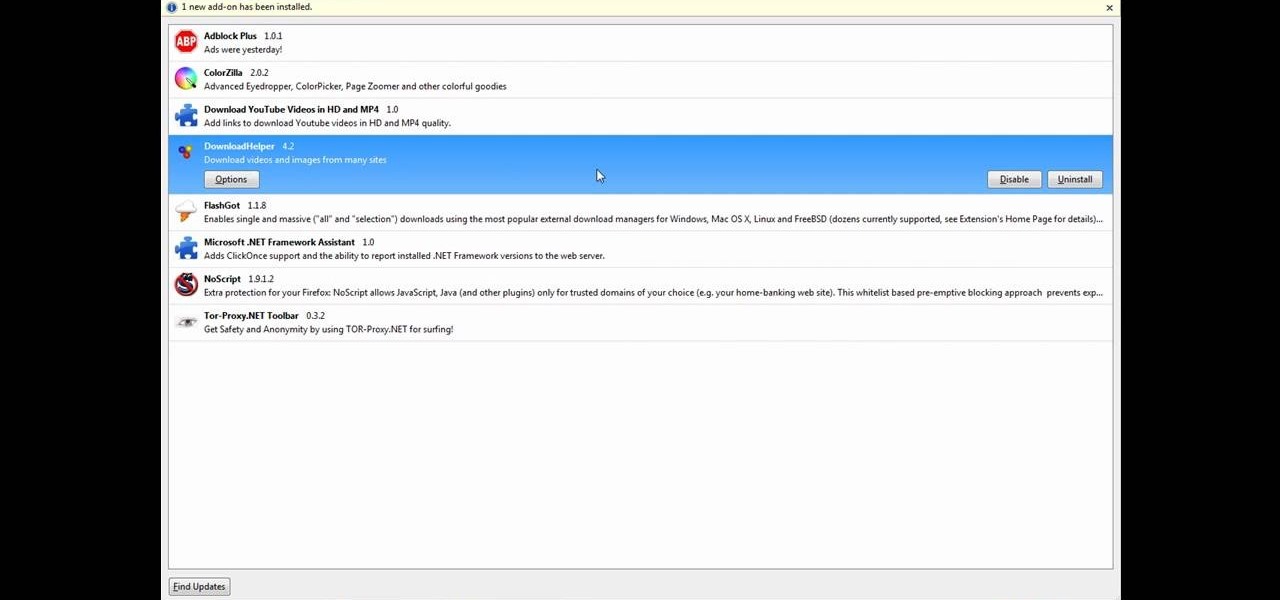
This tutorial will make you think step by step how to add a plug-in (Firefox Add-on) to your Mozilla Firefox browser that will allow you to download videos and music from YouTube and similar sites. The add-on that is used is called Video Downloadhelper. This is a trusted author and a trusted download. To begin this tutorial you will first need Mozilla Firefox and flash. This will enable you to go through the video and help ensure that YouTube will play the video you are trying to download.

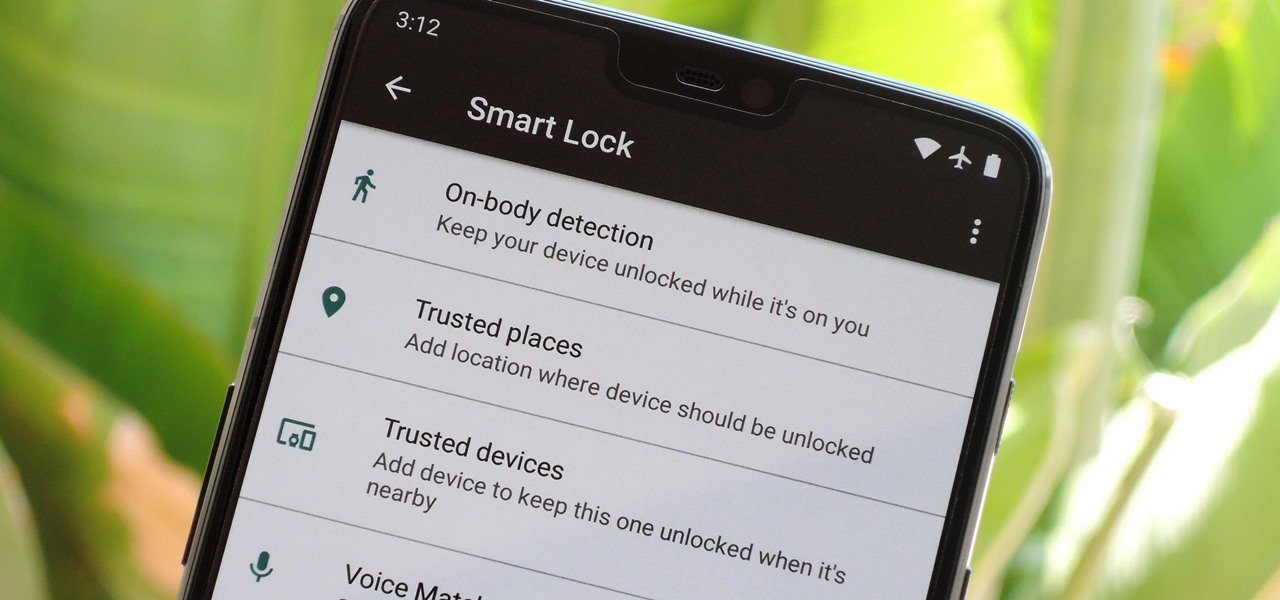
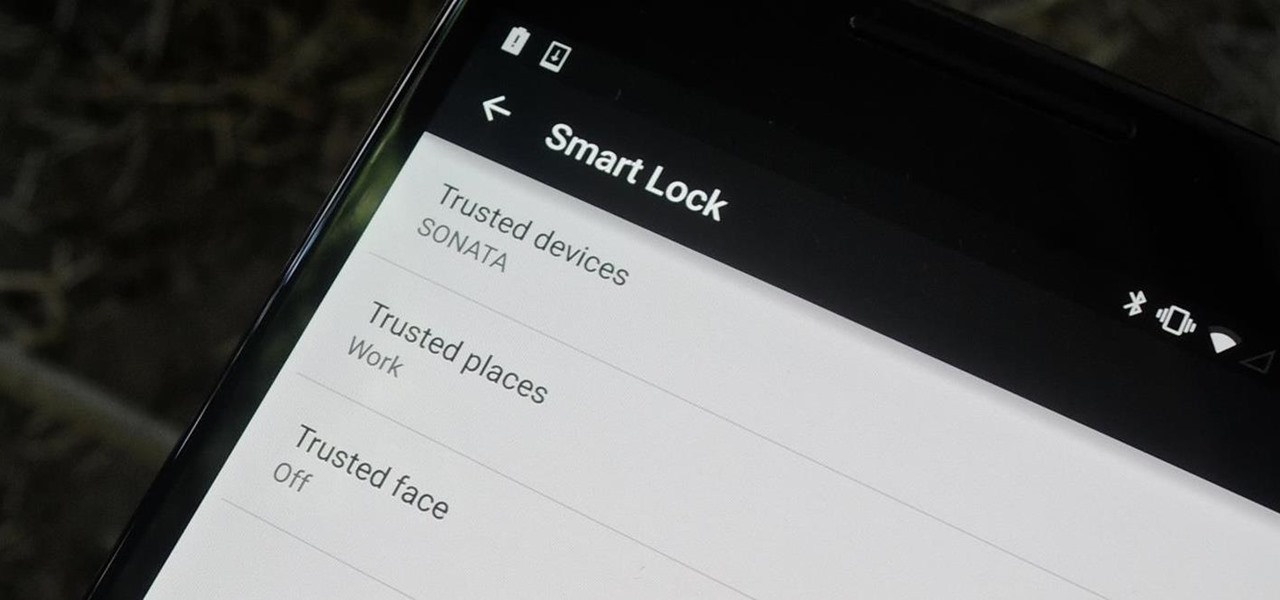
When it works, Android's Smart Lock feature is incredible. There's no need to enter your PIN when your phone "knows" it's in your hands — just unlock and go. But Smart Lock, particularly its Trusted Places feature, can be finicky sometimes.

Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).

Android 5.0 has a killer new feature that should make securing your device easier than ever. It's called Smart Lock, and it essentially lets you bypass your secure lock screen when you're in a "trusted environment." This means that if you're connected to a known Bluetooth device or near a pre-programmed NFC card, you don't have to bother entering your pattern, PIN, or password.

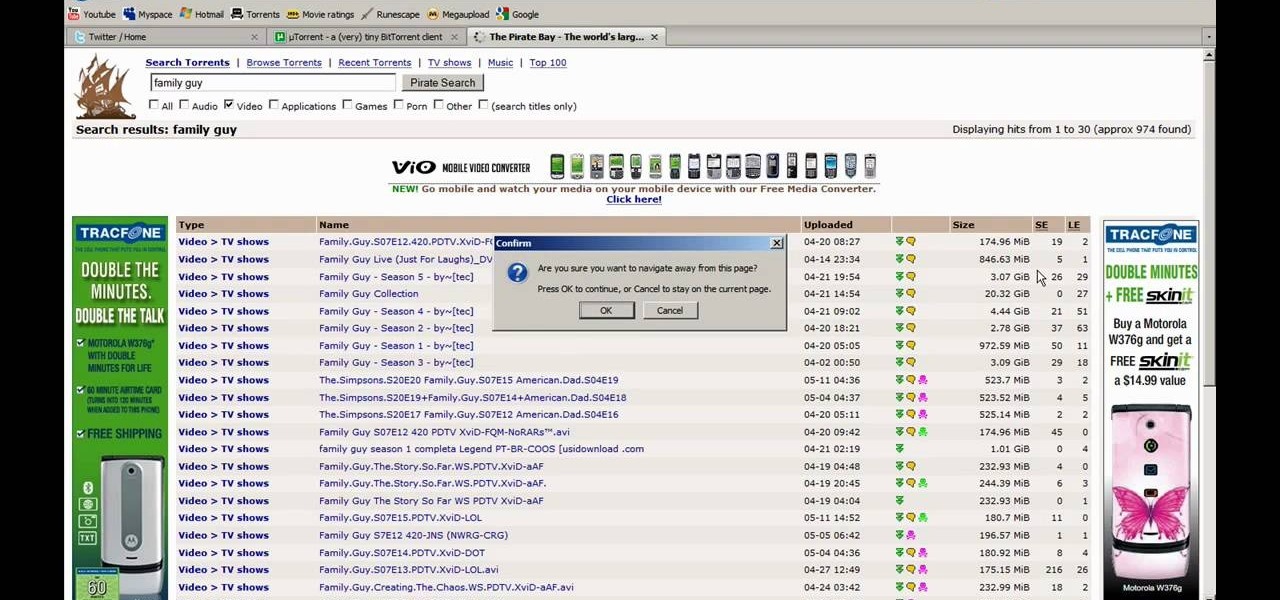
This video tutorial from JdudeTutorials presents how to download a torrent for the first time.To start, open your Internet browser. Browse to utorrent web page.Download and install uTorrent client version, suitable for your operating system (MacOS or Windows).Once you've installed application, browse to The Pirate Bay.This is the largest torrent source in the world.Check Video option under the search bar and type family guy (as an example).Click Enter. A list of torrents connected to family g...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to install a Wii homebrew hack using the Twilight Hack.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn a Fon+ wireless router into a network tap.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to get free WiFi by tunneling through DNS.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to program a USB development board for cheap.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a web-enable remote controlled tank.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to make a Twitter tamagotchi bot with PHP.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure remote desktop.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to defend your hacker space with a USB missile launcher.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to set up SSH tunneling to securely transmit HTTP traffic.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to session hijack with a pineapple.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to configure Cisco and iptables firewalls with a utility.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to packet sniff networks with the fundamentals.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to break down IP and TCP header with Wireshark.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn any Windows application into a service.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to organize your desktop with Microsoft Scalable Fabrics.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Don't even attempt this exercise if you're not trusting of gravity (and have amazing core balance). Combining one-armed push-ups with chest bounces from the stability ball, the exercise is dependent on your core strength and trust that the ball won't fly away as you come down.

Brazil has more untamed wilderness than almost anywhere else, so you can trust their survival experts to know what they're doing. In this video a Brazilian survival expert will detail all of the basic supplies that he packs for any trip into the bush and why you should do the same.

We know what you're thinking: You have two left hands and even cutting in a straight line is a monumental feat. But trust us, even butterfingers can cut their bangs professionally. In fact, if you tend to cut slightly slanted or jaggedy then your bangs will look even better!

The ways and means of finding your goddess and god and your inner bell: Finding goddess and god:One way of finding your goddess and god is through meditation. We have to align with any god whom we believe. Meditation can be done by sitting down or standing using candles, stones etc. We can do meditation at any place like hall, bedroom, or in open place. Our concentration should be on our god and godess. The very important thing about finding our own god and goddess is having belief in god.

On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hack a SharePoint site.