
News: Consumer Smartglasses Powered by Intel Could Arrive This Year, Report Says
Intel Corp.'s augmented reality division could ship consumer-focused smartglasses before the end of the year, according to reports.


Intel Corp.'s augmented reality division could ship consumer-focused smartglasses before the end of the year, according to reports.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.
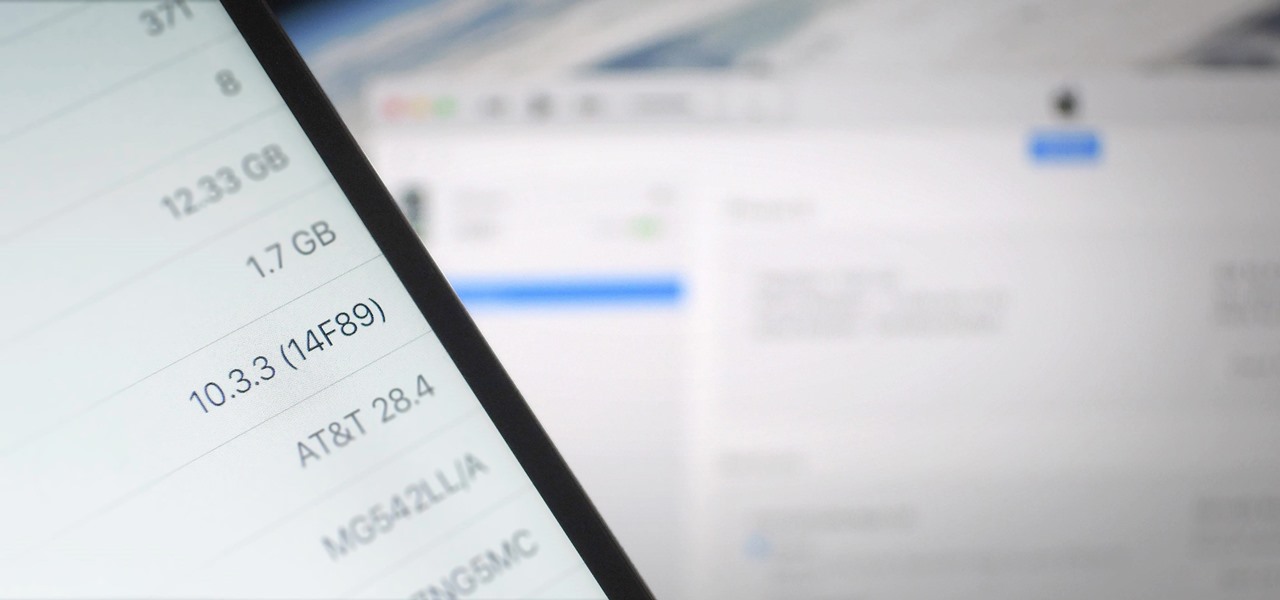
There's lots of new stuff in iOS 11, but just because things have changed doesn't mean they're better. So if you've updated to Apple's latest OS and decided it wasn't for you, you'll be happy to know that you can still go back to iOS 10.3.3.

When it comes to social media, Google has had it a bit rough. But its next big app in this category is apparently steps away from completion, with a platform that allows small groups of users to edit and organize photos in unison.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

The latest beta of the popular open-source media player VLC just hit the Windows Store, which means it not only runs on Windows 10 and Xbox One, but the HoloLens as well.

Whether you simply can't stand it or consider it a separate food group (or not food at all), there's no denying that Spam is everywhere. America's favorite canned mystery meat got its humble beginning in Minnesota, but is now used in dishes and found in homes around the globe.
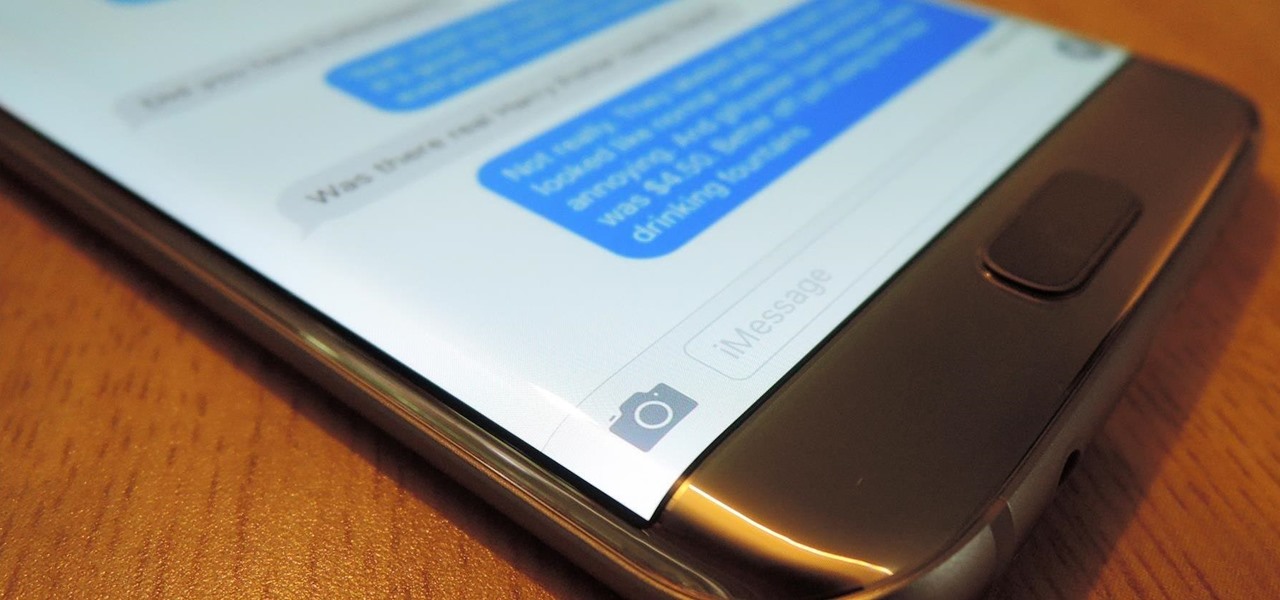
Android phones may soon be able to send and receive iMessages thanks to a new open-source app called PieMessage.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.
If your company has already released some popular and addictive game and you're thinking about creation a sequel, this article is just what you need. We gathered the main tips and advices that will be useful for the building a strategy and a sequel itself. Check out the following instructions and recommendations that can lend you a hand in making a sequel for your game.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Fall is the time for comfort foods—and what is more comforting than crusty bread slathered in melted cheese? Owning a fondue pot is both convenient and wonderful, but not all of us have the luxury of space for nonessential kitchen appliances. However, there are plenty of ways to make an absolutely delicious, lump-free fondue without the traditional equipment.

Protein powder is a fad in the same way that Justin Bieber's music is: you either love it, or you hate it. Everyone I know has a strong opinion about protein powder, ranging from "daily necessity" to "utterly useless."

CyanogenMod has been building upon open-source AOSP apps for many years now. They've made improvements to apps like the stock SMS client, the stock Audio Mixer, and a whole slew of others.

These days, using the power button to lock your Android seems a little old-fashioned. Thanks to third-party apps and mods, you could seamlessly lock your device using a double-tap, a swipe, and even gravity, or you could just throw it in your pocket, all of which help prevent additional wear and tear on your power button. Now, we've got another method for you—just shake.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.
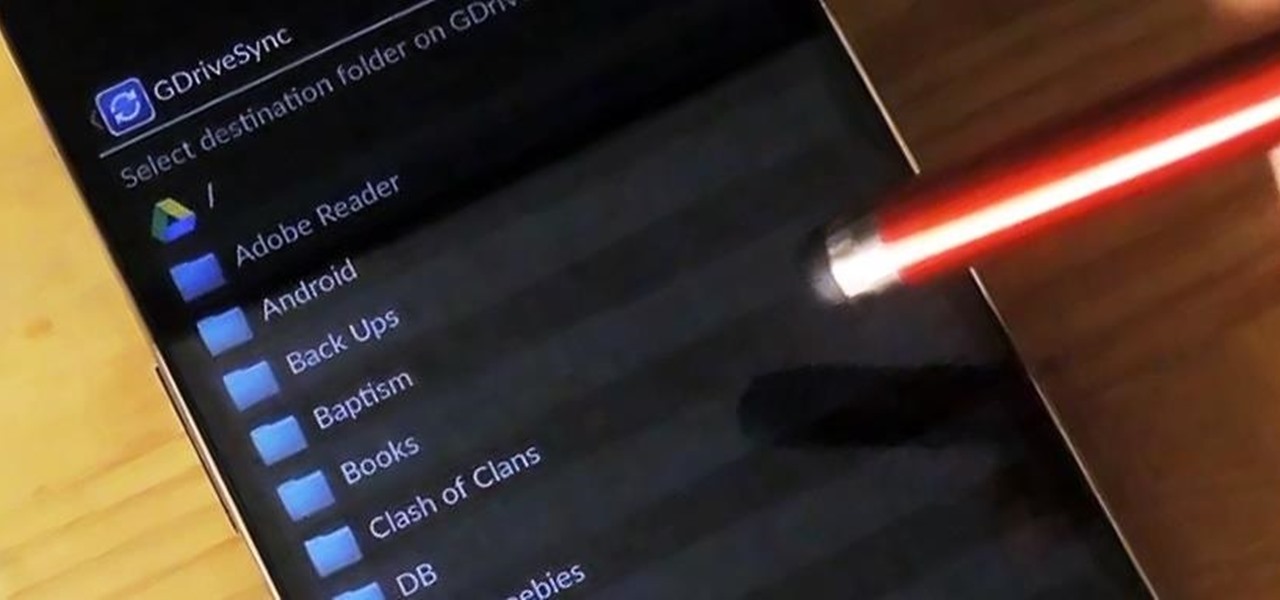
Google makes backing up your contacts, messages, and Wi-Fi passwords extremely easy, but leaves you out in the cold when it comes the data on your internal storage. With most Android devices now lacking SD card support, when you unlock your bootloader or do a factory reset, you're stuck having to back up everything to your computer beforehand.

This past year, Facebook spent $19 billion purchasing the popular messaging app WhatsApp, and for good reason. Mark Zuckerberg isn't going to spend that type of money on just any application. WhatsApp is widely popular and frequently used by more than 500 million users worldwide, which is almost twenty percent of the Earth's population.
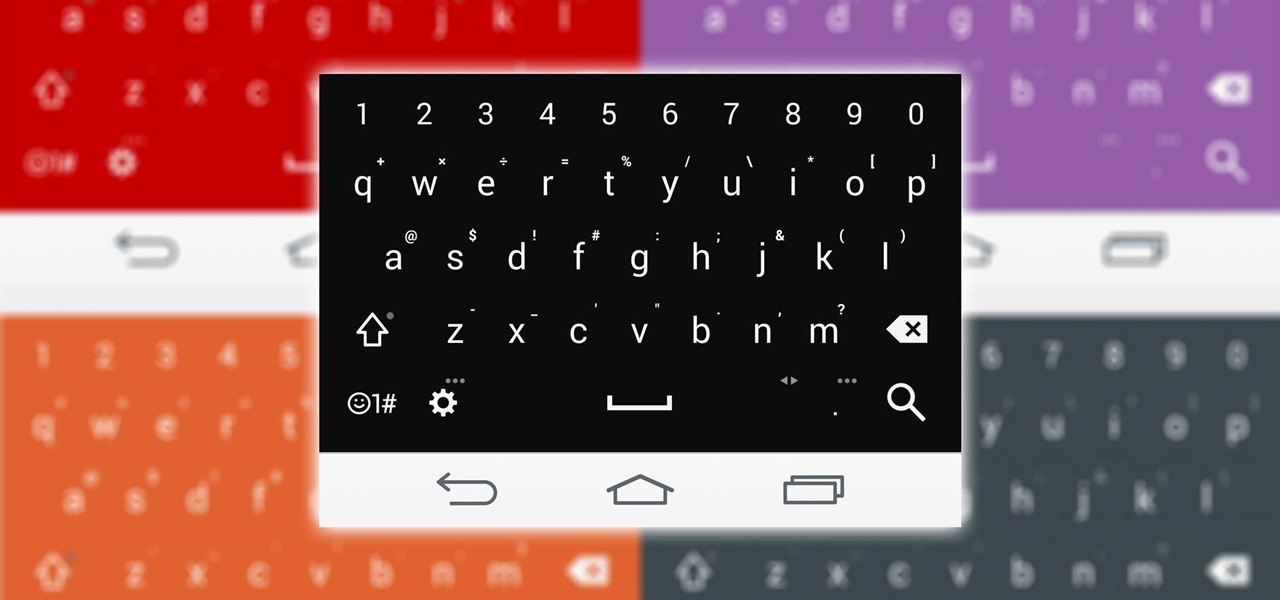
Personality is something we're constantly attempting to inject into our lives, whether it be the car we drive or clothing we wear—and our mobile devices are no exception.

Many of the beauty products you buy at drug and department stores are loaded with potentially toxic ingredients like parabens, while their active ingredients are made of things like glycolic, lactic, malic, and alpha hydroxy acids and retinoids, which are all derived from foods.

Screen timeouts serve mostly as security measures and energy savers, but they can also interrupt you when you're reading a book or editing a document. There is no built-in way to manage screen timeouts on a per-app basis, but if you've got root access, you can do just that using Never Sleep from Android dev Hamzah Malik.

Welcome back, my newbie hackers! Recently, I "upgraded" to Kali as my hacking platform, despite my preference for BackTrack. I did this reluctantly, primarily because new readers here could no longer download BackTrack from their site. I want to point out here that we all must keep in mind that with any software—or for that matter, any product—that is newer is not necessarily better.

There are many mods and tweaks you can do on your Samsung Galaxy S4 to make it feel more fresh, like using a more customizable keyboard and a better PIN unlock, but if you want to make your Galaxy S4 feel even fresher, add a little Galaxy S5 touch to it.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.
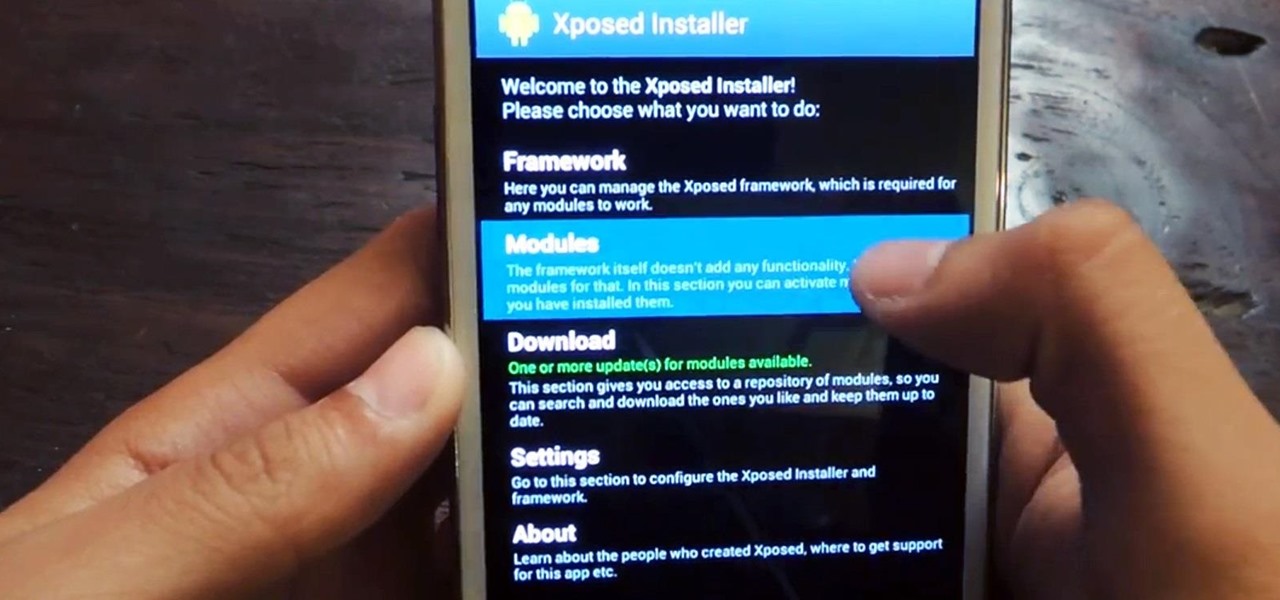
Android's deeply customizable platform has long been the attraction for those of us looking to make our smartphones more unique, but that doesn't mean that it's always easy. Flashing mods and installing custom ROMs can be difficult at times, as well as dangerous.
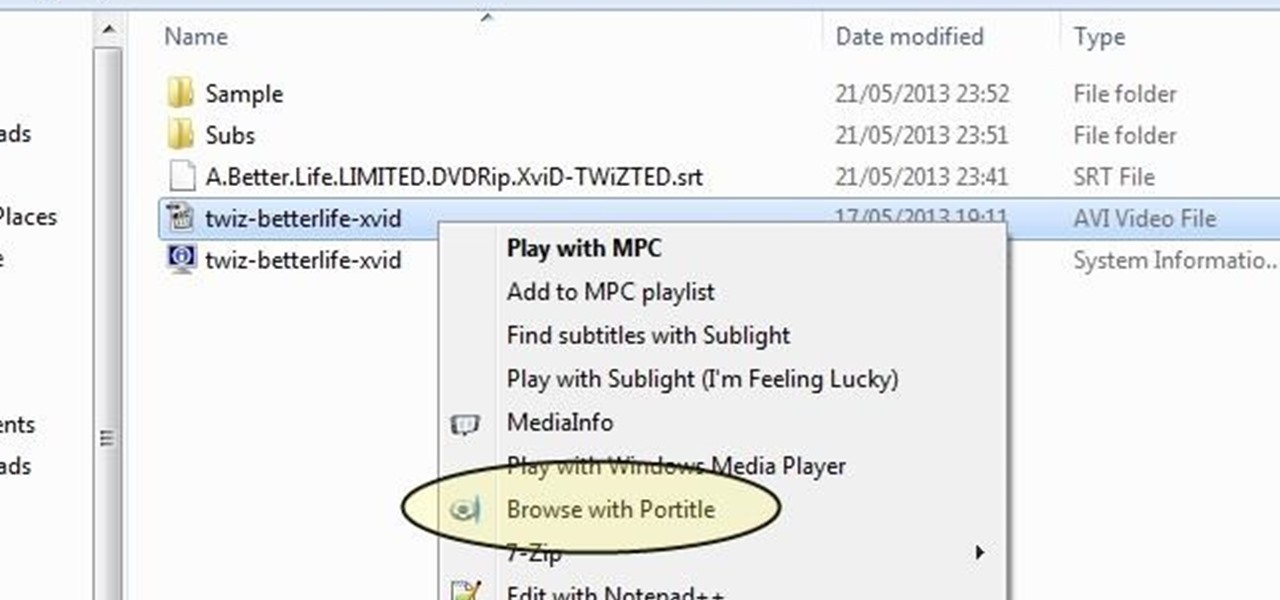
Understand the Problem of Couch Potatoes I have a lot of movies stored on my PC and when I have to finally have the time to watch something, I do not always remember which movie is which. So now I have to google for each movie with the keyboard or search in IMDB.

According to Nielsen, the average American spends about 34 hours per week watching television. That may sound like a lot, but when you factor in multi-screen viewing, it could be even higher—81 percent of Americans use their smartphones or another device while watching TV. It's the new picture-in-picture.

Having to read a bunch of articles and tweets everyday can be tiresome, but if you can have a sweet-ass personal assistant read them for you, you're pretty golden.

A faulty or broken thermostat can be one of the most annoying things to ever happen to your house. It's always too hot or too cold, and you can end up wasting money on your electricity bill.

Looking to transmit some super-secret audio communications to your other spy buddies? A laser is the perfect tool for getting your sounds heard from a small distance—without anyone intercepting them— even if it's just a cover of your favorite pop song. A laser audio transmitter uses light rather than radio waves to transmit sound. This is a much more secure way to send audio communications because the laser is a focused beam of light, whereas radio waves are not controlled, so they can be pic...

Because who wants to mess with all those wires, programming and power sources? You can make your own origami robot out of paper or cardboard! Though it probably won't do as much as a real robot would, it's nevertheless a fun project to do! All you need are a few sheets of paper (you can also used cardstock or a thin cardboard, depending on how sturdy you want your robot to be). Then just follow the steps in this tutorial!

GIMP is the free alternative to Photoshop, and many of the things that you can do in Photoshop, you can also do in this open source software. Want to see how you'd look with a lip piercing, or want to touch up a photo and add one where there isn't? This tutorial shows you how to add a fake lip piercing to nearly any photo. It's not that difficult - as long as you're familiar with the basics of GIMP, you'll be able to make this work for you!

In this video, we learn how to create professional looking business promotional video. To make your video more professional, you can first make your video shorter. The shorter the better, which will get your point across more quickly. Videos should be less than a minute and thirty seconds. If you're using a web cam, don't get too far away from it. If you're using a Flip camera, use a tripod and make sure the light source is coming from in front of you. Natural lighting is also nice. Make sure...

The first step in this video is to draw a rectangle on a piece of paper to gauge the length of the hair stokes. The artist then makes long pencil marks along the inside of the rectangle that are much less defined towards the middle. It is explained that you need to go in one direct with your pencil strokes as going back and forth gives an unrealistic final product. It is shown that you must begin at the beginning of the hair source and bring the strokes downwards for more realism. Four exampl...