A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.
When you're driving, the last thing you need to be doing is messing around with your phone. But these days, people expect you to be available at all times, so the text messages continue to flow in while you're on the road. It's a terrible distraction, and one that is responsible for 25% of all car wrecks in the United States.

Drones are popular little toys, but they're not the easiest things to control. While hand gestures may not change that too much, donning a HoloLens and flying a physical object with a wave of your hand at least makes the process feel a lot more like a telekinesis.

I fry foods a lot. A LOT. We're talking wings by the dozen here. As a result, I go through a ton of frying oil. Now, frying oil isn't the most expensive ingredient out there, but it adds up when you fry regularly. Of course, I always reuse my oil, but straining it can be a huge mess and it gets to a certain point where enough is enough. It's time to start fresh.

Move over rainbow food trends, there's a new, darker kid in town: jet black ice cream. And no, it doesn't have squid ink in it.

Bacon on burgers and sandwiches is truly a wonderful thing, though not when it slides out and lands on your plate. Or, even worse—the floor.

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Smartphones have been a hot button issue around school campuses for several years now—some schools allow them, others confiscate them on sight. But the fact of the matter is, when used correctly, a smartphone can be just as much of a learning tool as a textbook or school-issued laptop.

In the tech world, it's all too common to slap a fake label and packaging on a lower quality product, especially SD cards. If you've ever bought an SD card on the cheap from a slightly-less-than-reputable source (or even a reputable source, in some cases), how do you know if it's the real deal?

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

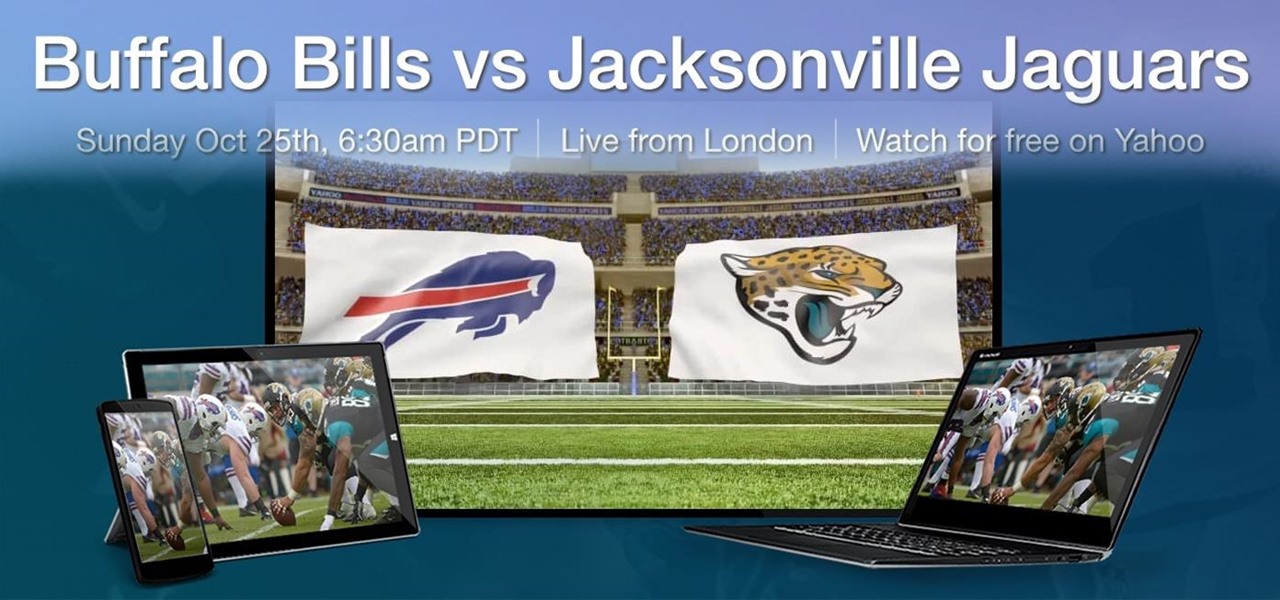
For a lot of would-be cord cutters, the lack of streaming local sports is the only hurdle that needs to be cleared before they can sever all ties with big cable. This is why it was a huge victory for us anti-cable folks when Yahoo announced that they would be hosting the first ever live-streaming NFL game this Sunday at 9:30 AM Eastern.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

Windows 10 has proved to be immensely popular (free upgrades certainly don't hurt), and with back to school time, there's a good chance you have a new computer running Microsoft's latest OS. You maybe you decided to go with a clean installation rather than an upgrade, or just haven't used your computer for much more than surfing the web and watching Netflix.

Downloading YouTube videos for offline use to watch later has always been a problematic endeavor. Dedicated third-party apps don't last long in the App Store, web-based converters aren't very functional on mobile, and rogue apps outside the App Store are tricky to sideload and open up the possibility of vulnerabilities. But that doesn't mean you still don't have a few good options.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

When I finally saved up some cash and got my first good chef's knife, I vowed to do everything by the book: clean it properly, hone it regularly, sharpen it faithfully, stand by it in sickness and in health, blah blah blabbity blah.

In my opinion (and I suspect in the opinion of the masses), there is no greater snack food than potato chips. They're crunchy, they're salty, they're fried, and they're bite size; what's not to love? But I believe that, like almost all foods, potato chips can get even better. Especially if they're the most basic garden variety type of chip: sea salt.

Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!

A lot of people like to trash stand mixers for being overpriced and rarely used kitchen appliances. As an avid bread baker I certainly don't agree with that assessment, but I understand where people are coming from. A good Kitchen Aid stand mixer costs a few hundred dollars, and if you only occasionally bake, you probably don't use it much, and therefore aren't getting your money's worth. But what most people don't know is that stand mixers are one of the most versatile appliances in the kitc...

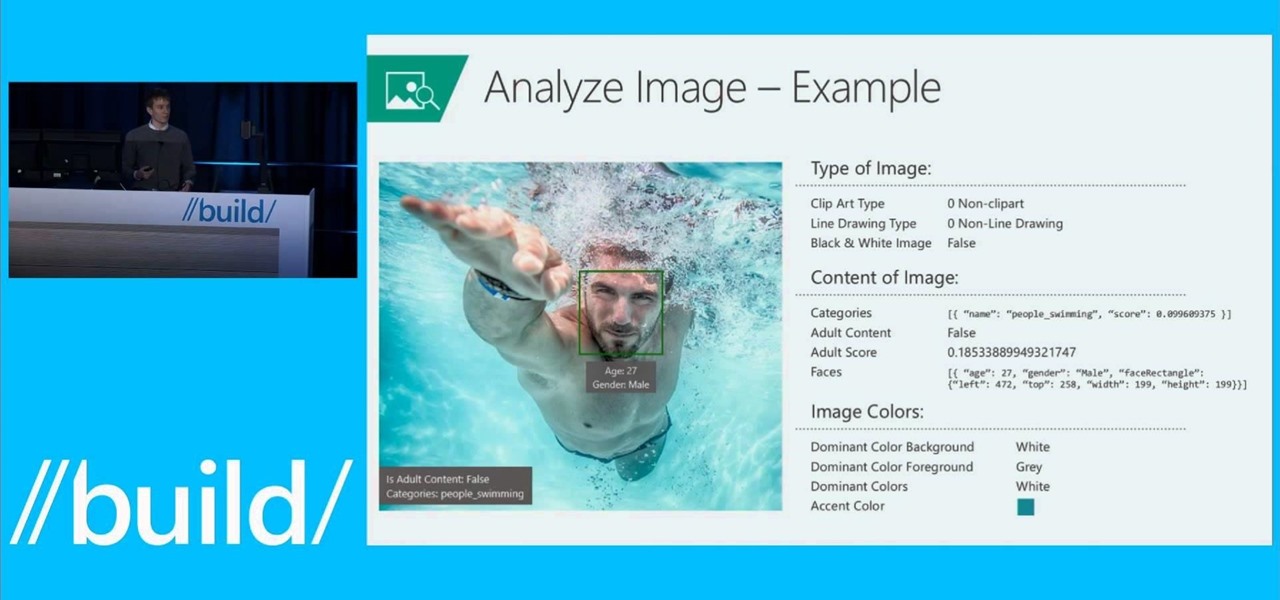
Microsoft is developing a new API project called poject "Oxford," and it includes face, speech, and more "smart" API technology. Despite being Microsoft, I actually found this to be very useful. ;)

Brought to you by Purdy Paints The art of painting requires excellent tools. And with so many options on the market, it can be hard to find a brand that works for you and your DIY project. That's where Purdy comes in.

Fiddlehead ferns look like something from Alice in Wonderland, or something that you might see when you close your eyes while listening to Pink Floyd and enjoying some herbal refreshment. What they don't look like is a tasty vegetable that's perfect for any spring or summer dish. Yet that is exactly what these bizarre spirals are. What Are They?

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Ad blocking on Android usually requires root access, but a pair of new browsers based on the open source Chromium and Firefox builds are looking to change this.

After you have registered to this site,sign in then to start missions. Basic Missions

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

It happens to even the most avid cereal eaters: sooner or later you open a box, unfurl the crinkled plastic bag, and find that the cereal inside is stale. Maybe you forgot about it, maybe you ate it too slowly, or maybe you just found a new, better cereal and left it behind like Andy left Woody. Either way, the crunchy goodness is now stale, and you grab the box and walk to the trash can. Stop!

Summer is right around the corner, which means it's time to switch from perfect hot coffee to perfect cold coffee. A nice icy glass of cold coffee is wildly refreshing and just plain delicious. In my opinion, it's the key to enjoying any sunny day (warning: if you don't already drink cold coffee, you may find yourself drinking four or five glasses a day very quickly).

Your Apple Watch is a fantastic tool that can help you perform daily tasks on your iPhone. Notifications get filtered through it, you can respond to messages on it, and you can even use Apple Pay to purchase goods and services. Your Apple Watch is also a valuable asset when it comes to finding your lost iPhone, too.

Meringues are a French and Swiss dessert made of whipped egg whites and sugar, and they are light, sweet, and crispy confections. To make traditional meringues, you beat egg whites into soft foamy peaks, and then keep whipping as you gradually add sugar until the peaks become stiff. Once you've reached the right consistency, you bake them at a low temperature in the oven for a long time. They take both technique and time.