If you're a ladies man like me then this next tip could save you from sorely embarrassing yourself. Here's the problem: You think you are texting Kelly M from New Year's when you're actually texting Kelly F from that one bar. Needless to say this could cause a problem with your relationships.

This is about how to make a rabbit become less wary of you and more trustful with you also. I myself have a Dutch that was released by its previous owner, then I rescued it. She never wants to be took out of her cage, but now she doesn't mind as long as I'm gentle and nice.

Communication is the key to any healthy relationship, and when I say any, I mean human and non-human. Previously, one of the biggest culprits for not understanding what you meant was Siri, but now it looks like it has some competition with the new Kinect system, which can control practically everything on your Xbox One—if it can understand you.

I've never been much of a runner. I've tried running alone, with a partner, on busy sidewalks, and back country roads, but I just never got it. There are a few other forms of exercise I genuinely enjoy, but have yet to experience that "natural high" that avid runners are always talking about.
In any project management career, there is no such thing as a person who knows everything for each project. Many times, those who got too much confident with their jobs fail because they were not able to make things clear before and during the project implementation.

Merrill never fails to amaze. In this video, he instructs you to "come as you are— but bring a pencil." And you don't have to be a diehard Nirvana fan to understand what this tutorial's about— Kurt Cobain. Watch and learn how to draw Kurt Cobain in a portrait, step by step, using pencils and a few art tricks.

Heartbroken? If your girlfriend threw in the towel before you were ready, there are a few ways you can try to win her back. Follow along with this tutorial and try to mend your broken heart.

Before you get started exploring a big new city or even just getting reacquainted with the one you live in now, make sure you aren’t putting yourself in any unnecessary danger. Memorize good traveler habits that will keep thieves and scam artist off your back.

Motivational speaker and leadership coach Tim Warneka teaches how to write a successful college essay in nine simple steps. Read and understand the directions and expectations the professor has for the assignment. Sit down and write whatever comes to mind on the topic. Edit your paper, making sure to use academic English. Allow yourself time to "sleep on it" and come back to re-read your essay with a fresh mind. When you come back to it, read the paper out loud to find any mistakes. Allow one...

No matter what your shape is, follow this advice to make sure you strut your stuff with style. You Will Need:

Watch this tutorial to learn how to draw a screaming angry mouth. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

Not in the mood to do jumping jacks in your hideous gym uniform? There are ways to sit it out. You Will Need

Is there something missing from your dance relationship? This four part how to video teaches you how to communicate with your dance partner. Use these secret tips from Naomi Uyama and Andy Reid, and become a better dance partner.

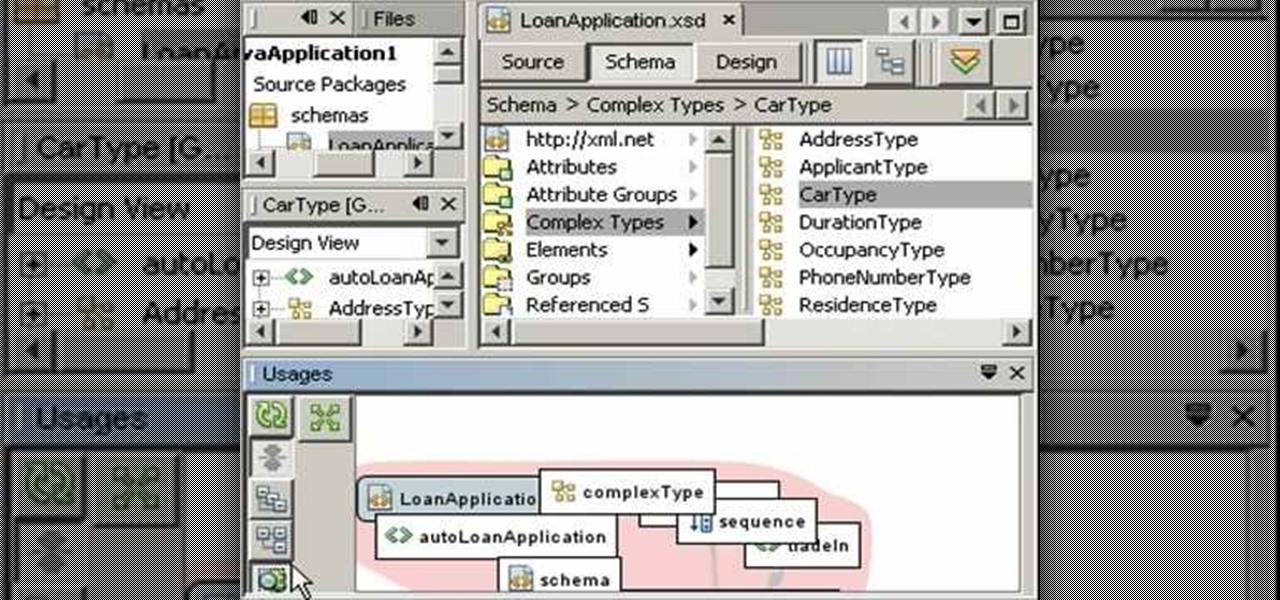
Watch this video tutorial to learn how to use the XML schema tools, which enable you to create, visualize, and edit XML schema in NetBeans 6.0. With these tools, you can visualize relationships between schema elements and use queries to find usages. You will also learn how you can easily create XML schemas by example. You will see how to navigate large schemas in the Design View, and you will learn how to visualize and edit multiple file schemas.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

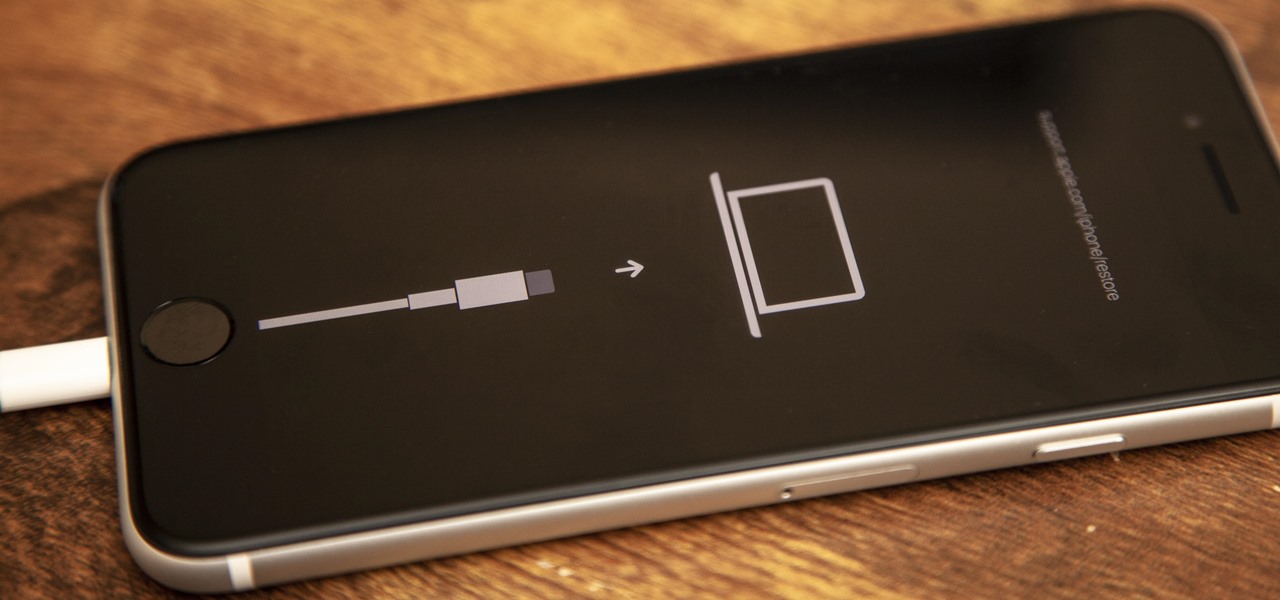
If your new 2020 iPhone SE is frozen, unresponsive, or won't load the system, and a standard power down and up procedure didn't work, there are few more things you can try. Force-restarting the device may do the trick, recovery mode is a last-ditch option, and DFU mode is your fail-safe.

Confession time: I hardly ever leave the first page of my iPhone's home screen. No, my iPhone isn't super organized and, no, I don't limit the number of apps I download as well (trust me, this phone is a mess). The truth is that you don't need to rely on your iPhone's home screen pages to find and open an app. In most cases, there's simply a much faster way.

Apple's update for iOS 13 is not without bugs and other issues, and if those problems become annoying or impede your ability to use your iPhone like usual, you may want to downgrade. Hundreds of new features may not matter if you can't use your iPhone like it's meant to be.

The recent pitfalls and media fallout hitting Facebook hasn't stopped the social media giant from looking to the future.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

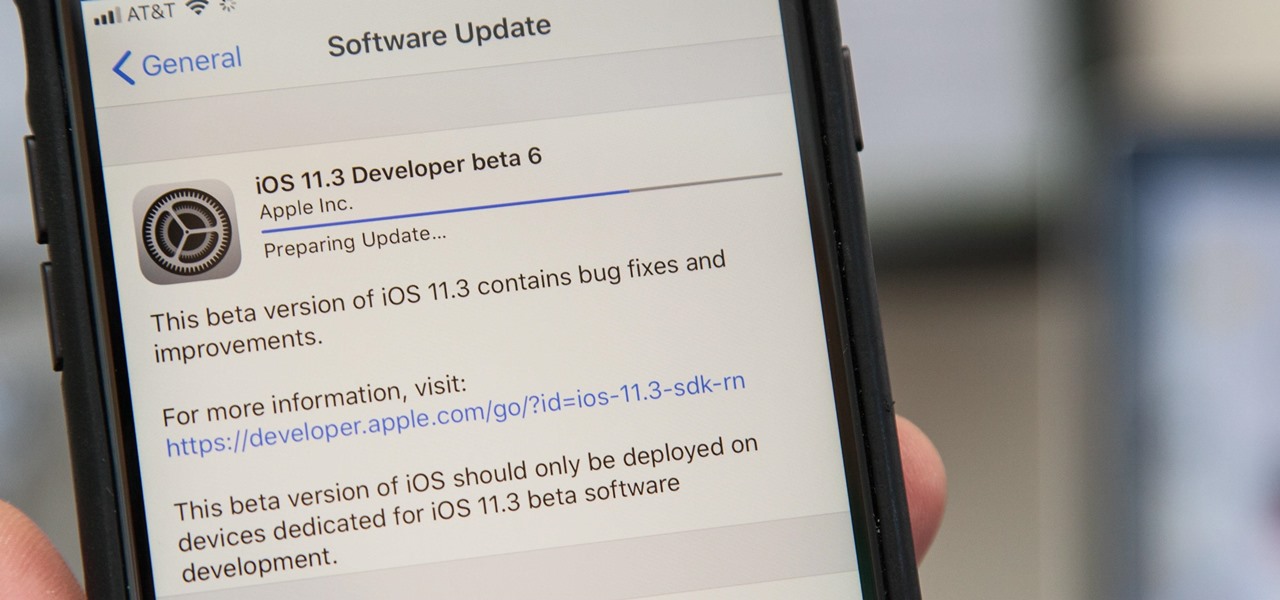
Apple released the sixth beta for iOS 11.3 on Friday, March 16. It comes as a surprise, considering the company released the fifth beta only four days ago — an unexpectedly short time between updates. This new beta, much like beta 5, appears to bring minor patches and bug fixes.

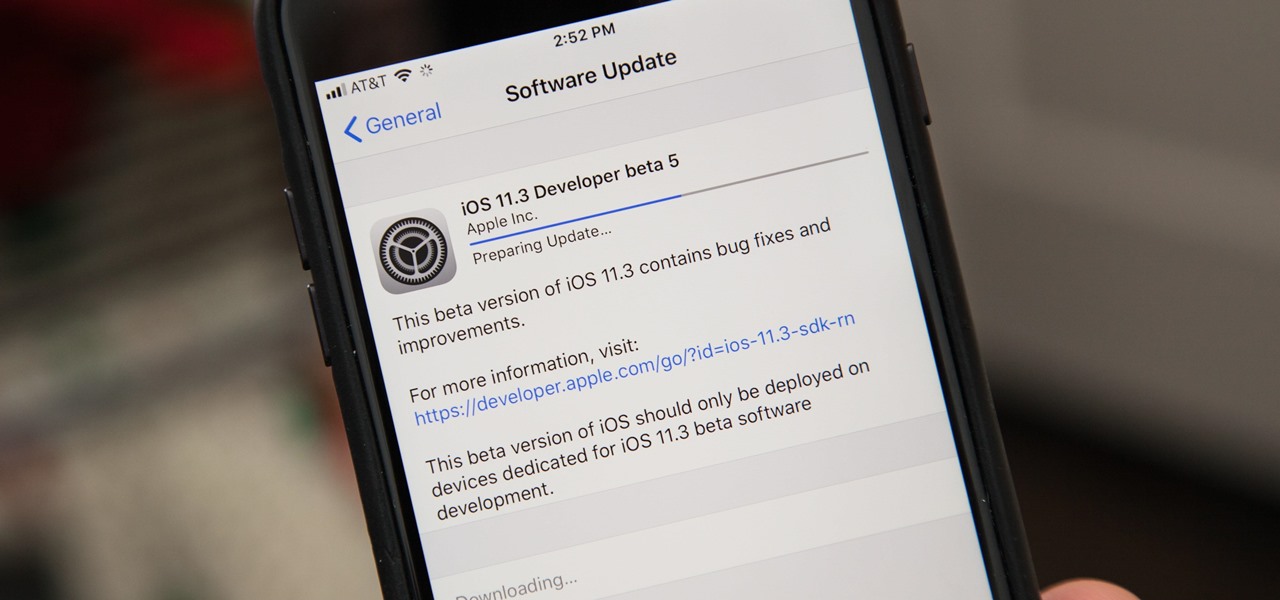
Apple released the fifth build of the iOS 11.3 developer and public beta on Monday, March 12. The update comes exactly one week after the March 5 release of beta 4, which mostly introduced bug and stability patches. At this time, this new beta appears to do much of the same.

It's really easy to binge-watch episode after episode, and that's exactly what Netflix wants us to do. Before you can even think twice, the next video is playing and you're stuck wallowing in the abyss of unintentionally marathon-viewing your new favorite TV show, and there's nothing you can do. Except there is something you can do — and it's as simple as disabling one little feature.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

Rumor has it that Google Assistant will be coming to an iPhone near you. A "trusted source" broke the news of GA's arrival on iOS to Android Police ahead of Google's I/O conference this week.

Over the years, we've covered many different methods for enabling background playback for YouTube videos on Android, but none have ever been as easy as this: Simply watch the videos with Firefox for Android, and they'll continue playing when you leave the app.

If you've ever wanted to be right in the thick of an operating room, you're about to get your chance. On Thursday, April 14th, you'll be able to watch a VR live stream of a tumor removal surgery. With their 360-degree camera, you'll be able to see the entire operating table and its surroundings.

All across the web, countless users and critics have already decided that Periscope, the Twitter-owned live video-streaming app, has killed (or is on the verge of killing) Meerkat off for good.

Lending someone your phone to make a call is always an awkward situation, as you closely monitor them to make sure they stick to a phone call rather than wandering off into private applications like your photo or messaging apps. You don't necessarily want to eavesdrop on their conversation, but trusting people with your phone is difficult, especially if you have some risqué or embarrassing pictures stored on it.

If you live in a small town, weather apps can be unreliable. Before moving to Los Angeles, I always had to add or subtract five degrees or so from what my weather app said because I couldn't trust it. With the help of BloomSky, you will be able to get an accurate weather reading directly from your backyard.

If new leaked images are to be trusted, an iPhone with a display around 5 inches will be released later this year. From Italian site Macitynet, images show a device that's stated to be the new iPhone 6 side-by-side with the new Samsung Galaxy S5. A couple of weeks ago, I showed you leaked internal emails and memos that suggested Apple was concerned with not only Samsung's marketing strategy, but about the industry trend towards larger devices.

One of many cool features in iOS is the ability to listen to your Music app and have the player options, as well as album art, available on your lock screen. While that's super convenient, it's not all that easy on the eyes. The player is placed over a blurred version of whatever your lock screen wallpaper is.

Katie wanted to make a difference in the world, and thanks to the ACUVUE 1-DAY Contest, and Disney Channel star and singer, Bridgit Mendler, her dream became a reality. Watch ACUVUE's video below and check out our tips on how you too can begin the transformation and motivate others to make a difference.

I learned the hard way that boxed dyes just don't work well for me. A few months ago, I tried one that had a pretty name like "soft violet black." Sounds nice, right? What I ended up with was brown hair and hot pink roots. Trust me, it wasn't cute.

Ever wonder what your brain looks like while you're singing? No? Neither had I, but as this music video for the song "Better Man Than He" by SiVU (aka James Page) will show you, the answer is "pretty cool."

Convenience is a big deal these days. You can buy single-serving or single-use sizes of just about anything, from fruits and vegetables to sanitizing wipes, and, apparently, even bananas. Uhh, it already has a wrapper...

One of the roles our government has taken on is to provide us with information to be used in making decisions.

Have a super secret spy communication you'd like to send out, but don't have the funds to hire your own trusted operatives to deliver the message? Then stick to what you're used to—email it. SafeGmail is a browser extension that allows you to send encrypted emails right through your regular Gmail account. While this may seem a bit unnecessary for most messages, encrypting your email can definitely be useful.