Tesla's Autopilot self-drive interface in its new Model 3 signals the carmaker is already prepping its cars for Level 4 driving years ahead of the competition.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Self-driving car models and fleets get most of the media attention, but it is the suppliers that design and make the technologies underpinning the driverless revolution, says Guillaume Devauchelle, the vice president of innovation and scientific development for leading tier-one supplier Valeo.
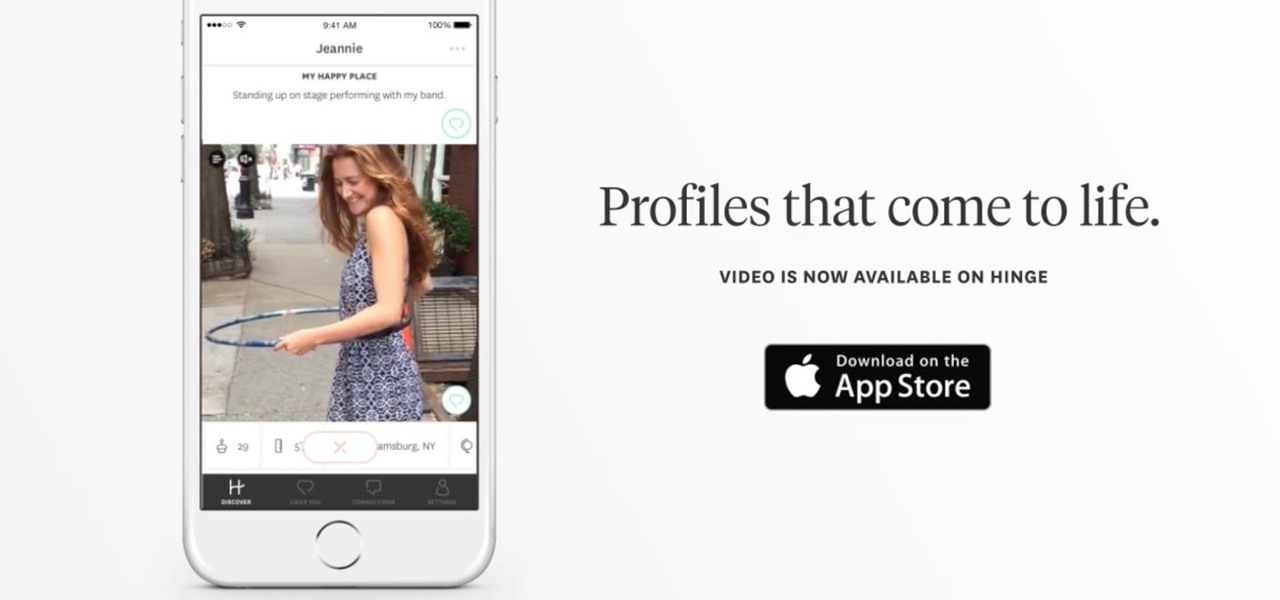
It seems we've come full circle in alternative dating routes. Just like a long time ago when people were able to go to matchmakers and watch videos of potential matches, the dating app 'Hinge' is now allowing you to add videos to your profile.

Meta Company filed suit today against a former employee and his startup DreamWorld USA, Inc. for the misappropriation of trade secrets and confidential information.

Keystroke injection attacks are popular because they exploit the trust computers have in human interface devices (HIDs). One of the most popular and easily accessible keystroke injection tools is the USB Rubber Ducky from Hack5, which has a huge range of uses beyond simple HID attacks. The USB Rubber Ducky can be used to attack any unlocked computer in seconds or to automate processes and save time.

The future of forests looks dreary in the face of a warming climate, but scientists are exploring the relationship between soil microbes and the ability of trees to move to higher altitudes, a key component of their survival.

How can bacteria that lives in the throat of 10%–35% of people—without causing an infection—cause life-threatening meningitis and sepsis in others?

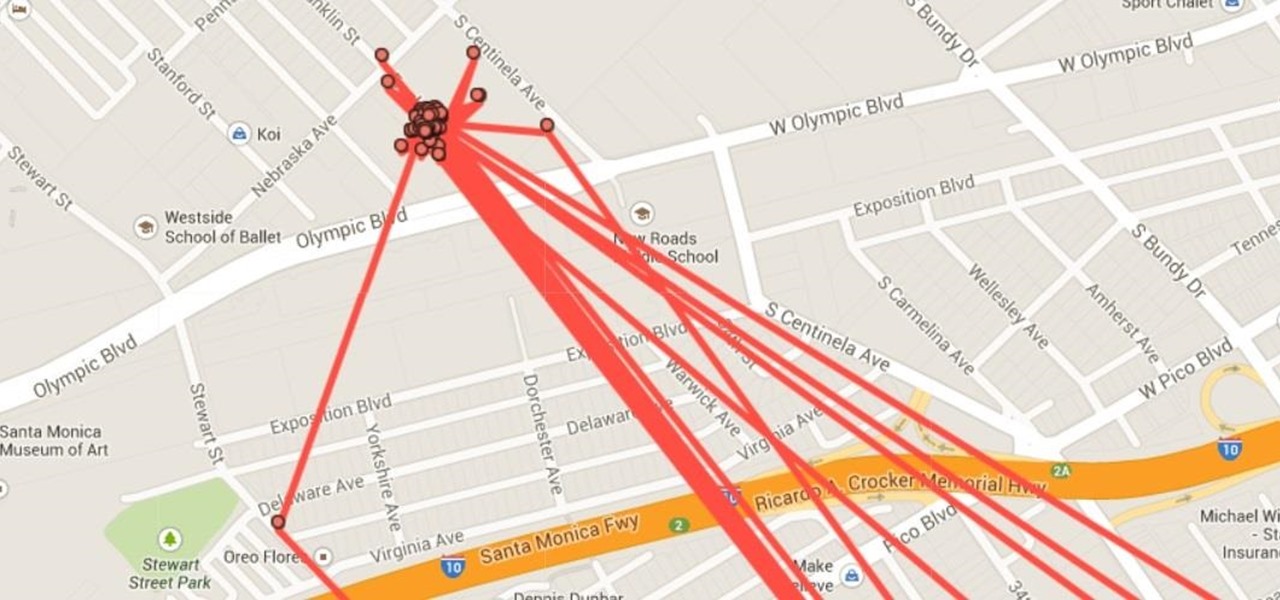
There has been an outbreak of syphilis in Oklahoma County with 75 confirmed cases connected by a social network driven by drug use and sex.

As many as 700 species of bacteria live on our teeth and in our mouth, and just like the microbiomes inhabiting other parts of our bodies, they change in response to diseases and other health conditions.

To shine light on the future of the relationship between humans and viruses, a team of researchers from the University of Oxford looked into the dim and distant past.

Kodi, formerly known as XBMC, is one of the most versatile media players available. With it, you can play virtually any internet and media file in a large variety of formats, and it can be used on practically every single operating system out there, including iOS 10. Kodi, an open-source software, was originally designed to connect to your TV so you could control your media from up to ten feet away, and the core functionality still shines today. All of this is what makes Kodi so popular today...

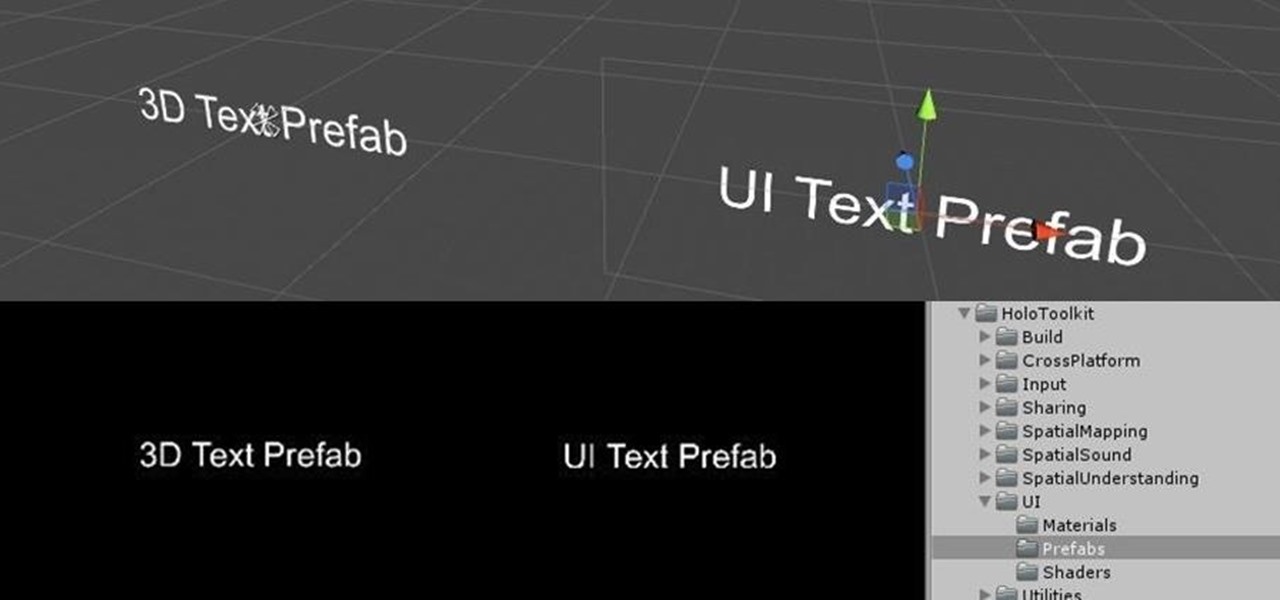
You may remember my post from a couple weeks ago here on NextReality about the magical scaling ratios for typography from Dong Yoon Park, a Principal UX Designer at Microsoft, as well as developer of the Typography Insight app for Hololens. Well, his ideas have been incorporated into the latest version of HoloToolkit, and I'm going to show you how they work.

An average user's smartphone tinkering doesn't go much further than taking their phones out of the box, signing into their account, and installing apps. But some of us want more functionality and customizability than the basic experience provided by Android and iOS.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

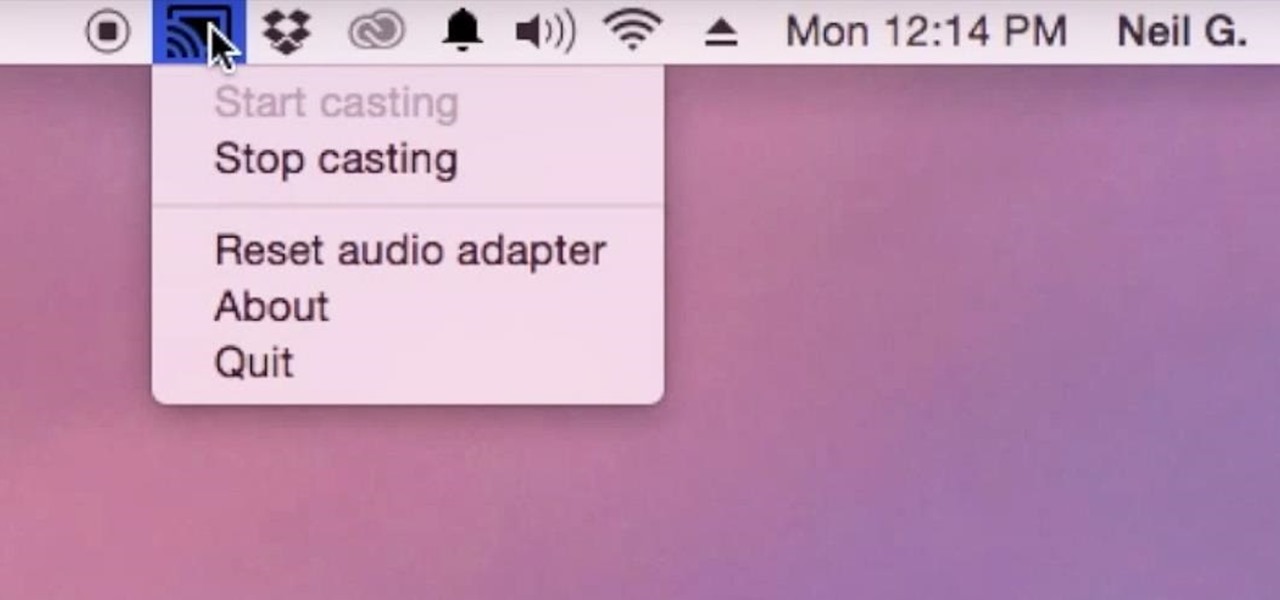
Although I know it will never happen due to Apple and Google's tempestuous relationship, I sometimes wish I could cast iTunes or Apple Music from my Mac to Google's Chromecast. When you don't have speakers to blast your music, the television is a great alternative to amplify your music.

After several weeks of testing out the public beta, Apple has finally released iOS 8.3 to the general public. The latest iteration of iOS for iPad, iPhone, and iPod touch serves mostly as an update to fix many of the bugs that plagued earlier versions, but there are still a couple of awesome new features included in the new build.

Potatoes are one of cheapest, most nutritious whole foods that you can make and eat. Is it any wonder you can find budget-friendly, low-fat potatoes in every cuisine in the world?

Can you tell when someone is shooting you a fake smile? Even though fake smiles are easy enough to see through, we all still do it, attempting to show others just how happy we are when we're really feeling less than fantastic. Unfortunately, every smile we fake makes us a tiny bit more miserable.

There comes a time in relationships when two people decide to move in together, and when this happens, you learn two things:

While most are still fighting through a somewhat ridiculous invite system, OnePlus is starting to ship out a decent number of their One flagship devices to those who were able to obtain one.

True story: a friend of mine regularly started a fight with her boyfriend everyday at 4 p.m. Every day. This went on for years until he finally got the bright idea of shoving a granola bar at her the minute she came home from work. Shazam! The fights were a thing of the past.

We're only years away from a complete Robot Revolution and Google Inc. will surely be leading the charge.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

If you haven't walked into a department store or seen one of those millions of jewelry commercials airing over the last month, you might not know that February 14th is Valentine's Day.

As a former English major, I have a love/hate relationship with many books. And when I saw that this NFC-enabled charging dock project included a little book mutilation, I was suddenly more interested. Now, for those of you who have nothing against books, this is still a great project to add some style to your tech devices.

To work with out emotions in Rasa Sadhana, we must be aware of the relationship between our emotions and the food we eat. There is the direct effect of the taste, the second effect during digestion and the third after digestion. Taste addiction and food addiction can be solved through Rasa Sadhana, the Tantric practice of emotional fasting.

Here's a low-key way to take advantage of someone's trust. Gain access to a friend or frenemy's iPhone and add curse words as separate new contacts to their contacts page. Sit back and wait for your friend to text someone. Enjoy.

Crayola Washable Watercolors offer the best and brightest watercolor painting experience, without the mess! They come in a variety of vibrant colors that blend smoothly for more color-mixing possibilities. Washability you can trust™! This video has great ideas for projects to do with your kids!

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

If there's any silver lining to being stuck at home right now, it's the fact that many of us have way more time to take care of those things that have been sitting on our back burner for ages, like beefing up our resumes.

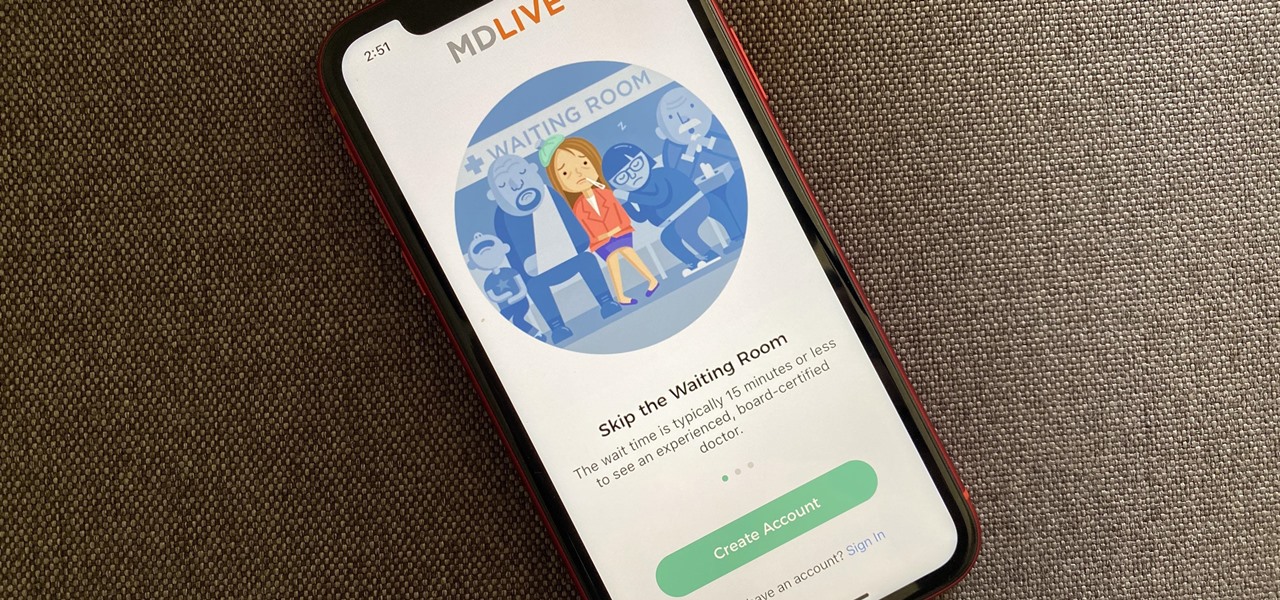
The World Health Organization has declared the new coronavirus a pandemic, and the Centers for Disease Control and Prevention recommends video visits with a healthcare professional to reduce the risk of being exposed to the coronavirus that causes COVID-19. If you are experiencing mild flu-like symptoms, virtual doctor visits may also prevent you from endangering others.

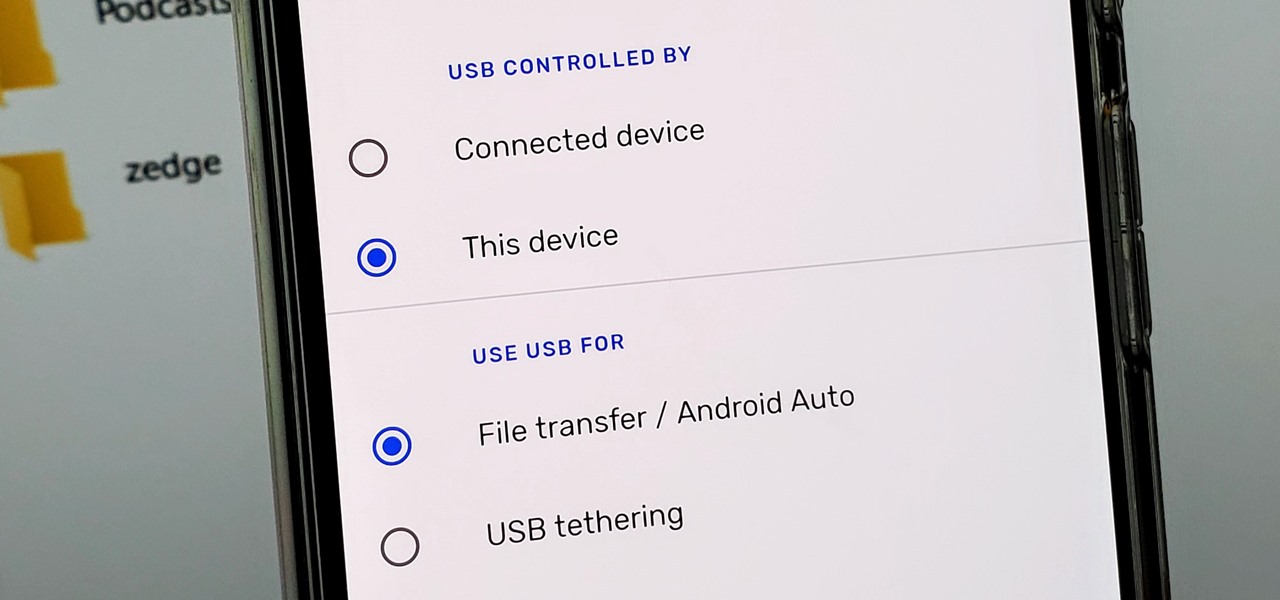
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions of Android changed that to help increase security.

One of Android's biggest strengths relative to iOS is how simple it is to sideload apps that aren't on the official app store. Rather than having to sign IPA files or tell your phone you trust a developer every two weeks, you can just enable a setting and be done with it.

Decades ago, Japan rocked the automobile industry with its revolutionary manufacturing and car quality, but today that title seems to be moving over to Elon Musk's electric car company Tesla. Nevertheless, Japan isn't done innovating mass-produced hardware.

There's definitely some malware-ridden apps on the Play Store. When it comes to the third-party apps you've connected to your Google Fit account, some have a crazy amount of permissions they have no business accessing. For example, you probably don't want a heart monitor app having access to your personal location data.