Chromecasts can make for some fun nights. Whether you're setting up a collaborative YouTube watch list, letting everyone add to a giant party playlist, or playing games like Cardcast and Big Web Quiz, Google's streaming media stick is a hit by all accounts.

Can you tell when your friends are serving up a bunch of BS, or are you constantly oblivious, unsure if they're spinning a valid story? With so many ways to lie and fake information floating around, it can be impossible to tell what's the truth from what's complete BS. Here's how to sort through what you hear and find the real truth.
Hello everyone. The red ring of death of Xbox 360 has been a huge problem since the beginning of Xbox 360. Many gamers like me have faced this problem and the red ring of death (RROD) is one of the biggest reason behind all the rant on Xbox 360 gaming console.
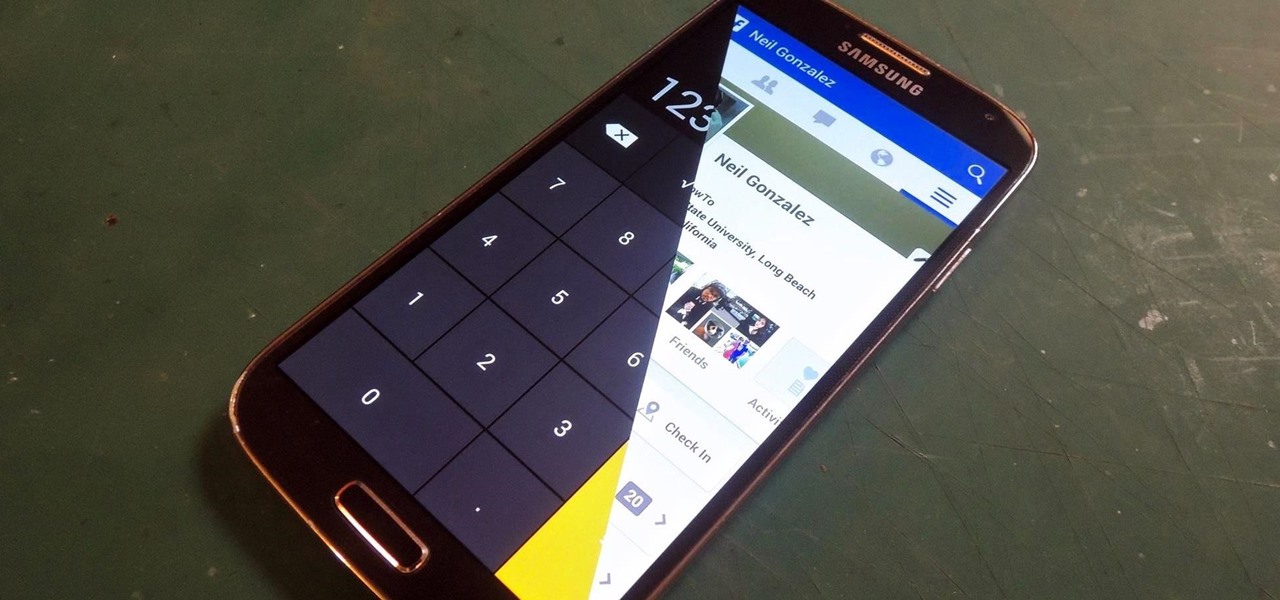
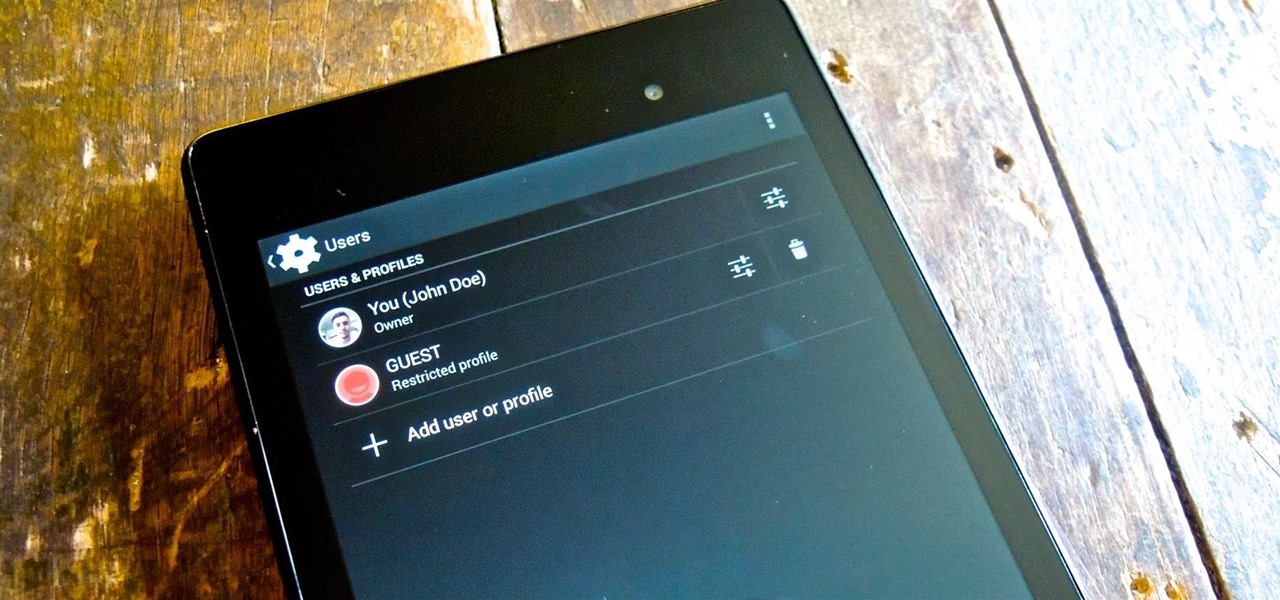
Trust can be a touchy subject in general, and is often required when sharing personal information—especially so when handing our phones over to others. You may not have a ton of secret or nefarious information on your device, but that doesn't mean you want your mom or snoopy coworker having easy access to your messages or Facebook app.
While LG G3 users have been patiently waiting, developer the cubed and his Codefire team have been diligently working on a successful unlock method for the heavily locked-down bootloader. Now it's finally here, and the unlocking method is extremely easy to do—and it works for all G3 variants.

With recent security breaches in the news, there is no better time than the present to make sure you know exactly what's happening on your device.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

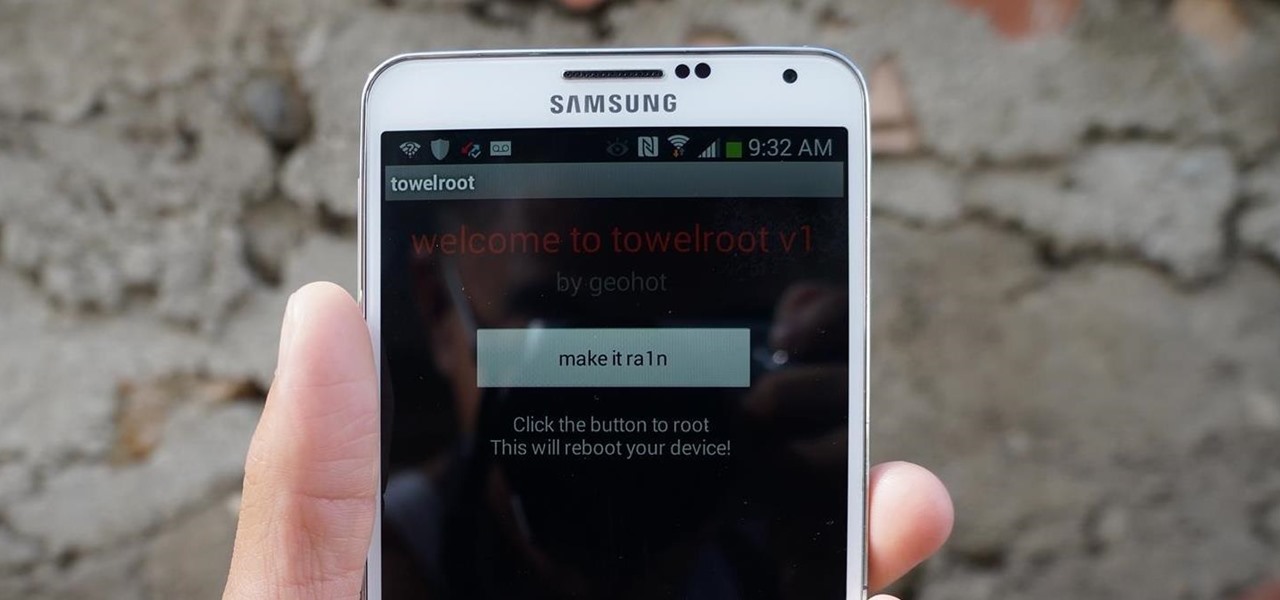
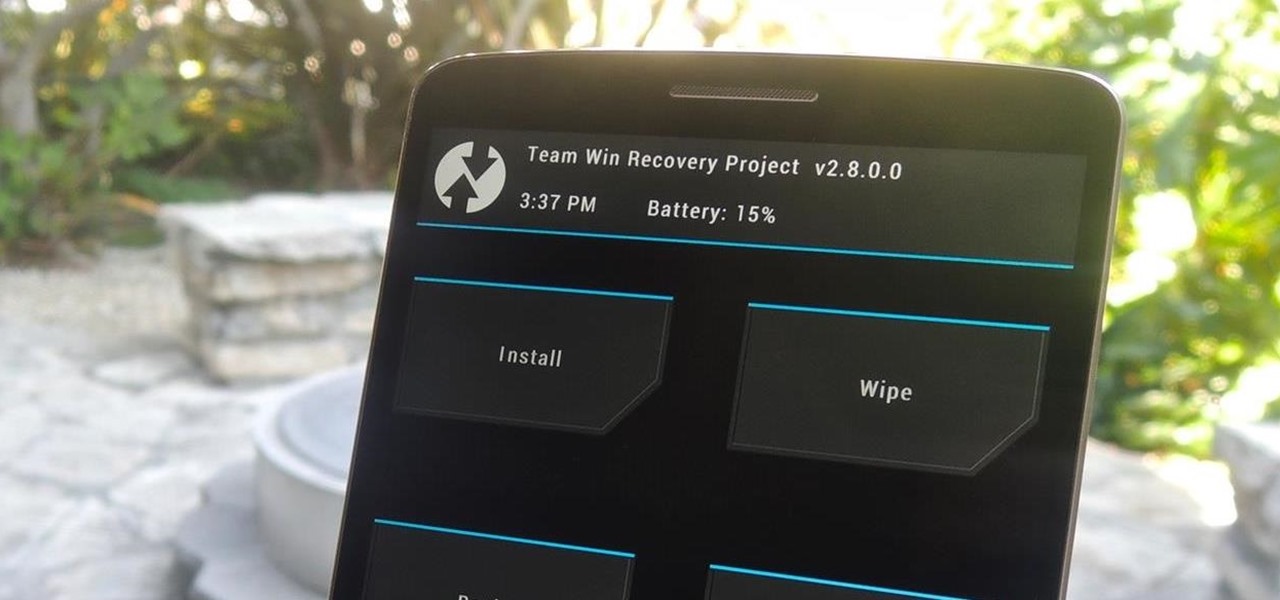
AT&T and Verizon customers, it's finally happened. After many long months of waiting, and a fairly significant bounty up for grabs, your Galaxy Note 3s can finally be rooted! Best of all, it may be the simplest method for achieving root we've ever encountered.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

In a world where mobile devices are the new norm for interacting and staying in contact with one another, it's important to make the experience as smooth as possible, and typing is the biggest problem for me.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Whenever I hand my tablet over to someone, my heart always races for a second at the thought that they may stumble across my private pictures, texts, and videos. I trust them, and they may not be the snooping type, but it can be easy enough to come across private stuff by accidentally opening a gallery or messaging app.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

There's one reason why most of us have a Samsung Galaxy S3—because we don't want an iPhone. Yes, there are some pretty cool things about the iPhone aesthetically, but looks aren't everything. Anyway, with the nearly unlimited customizations options we have available for Android, cloning the iPhone-look is no problem—even the lock screen.

We have shown you how to get CyanogenMod on your HTC One and Samsung Galaxy S3 in only a matter of minutes. But when modding your phone by installing custom ROMs, you'll often lose your access to Google Apps. Since Google's Apps are very useful (Gmail, Chrome, and Maps to name a few) most people will prefer to have these apps on their custom ROMs. While you can scour the internet searching for individual .APKs, it's hard to find the correct versions to work with your particular system (and do...

If you're not acquainted with 500px, you should be. One of the more preeminent photography communities out there, 500px takes you through a journey of incredible shots—anything from nature and urban explorations to cities and architecture to the abstract. Whatever your preference is, you can be sure to find it on 500px.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

If you've tried watching a video that requires Adobe Flash Player installed on your Samsung Galaxy Note 2, then you're probably well acquainted with the "Flash Player is not installed" message. If you try tapping the deceiving Install Flash Player button it takes you directly to the Adobe website, where you're greeted with a message saying:

We've all had that moment when we enter into a classroom, meeting, or theater and completely forget to put our cell phones on silent.

"Dude-man-bro, are you going to Coachella this year?" If I got a dollar for every time I was asked that question, I might just have enough money to actually buy the dang ticket. Concerts have been, for a very long time now, a great way to spend a night or a weekend having fun with friends and listening to some great tunes.

Samsung just concluded their live unveiling of the Samsung Galaxy S4! A more in-depth look can be found here.

First off, let me say this—using real steam power is dangerous, and heavy, and just generally not worth it when you have modern alternatives. Except, you know, if you're a Steampunk. Or this guy:

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

Say whatever you want, but Steampunk is primarily a maker culture. Consider that Steampunk has existed since the 1960s and yet more or less languished in obscurity until approximately 2005, which is when it made the leap to costuming. That costuming was what provided the leap to the tangible, despite the fact that Steampunk art had also existed for years.

There's nothing worse than losing your phone—except losing your phone when the ringer is silent. If you're alone, it can be excruciatingly hard to find your lost device even if the ringer is on, considering most of us don't have landlines anymore. So, the next time you find yourself hunting for your phone, don't tear your house apart until you've tried some of these quick tips.

Traps are great, but sometimes you don't want to kill anyone, you just want to know when they're around. When that's the case, check out this handy alarm system that uses the power of doors! Doors, you say? Yes, doors! Some of you may already be familiar with how obnoxious doors can be in Minecraft, but if not, check out this video of it in action:

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

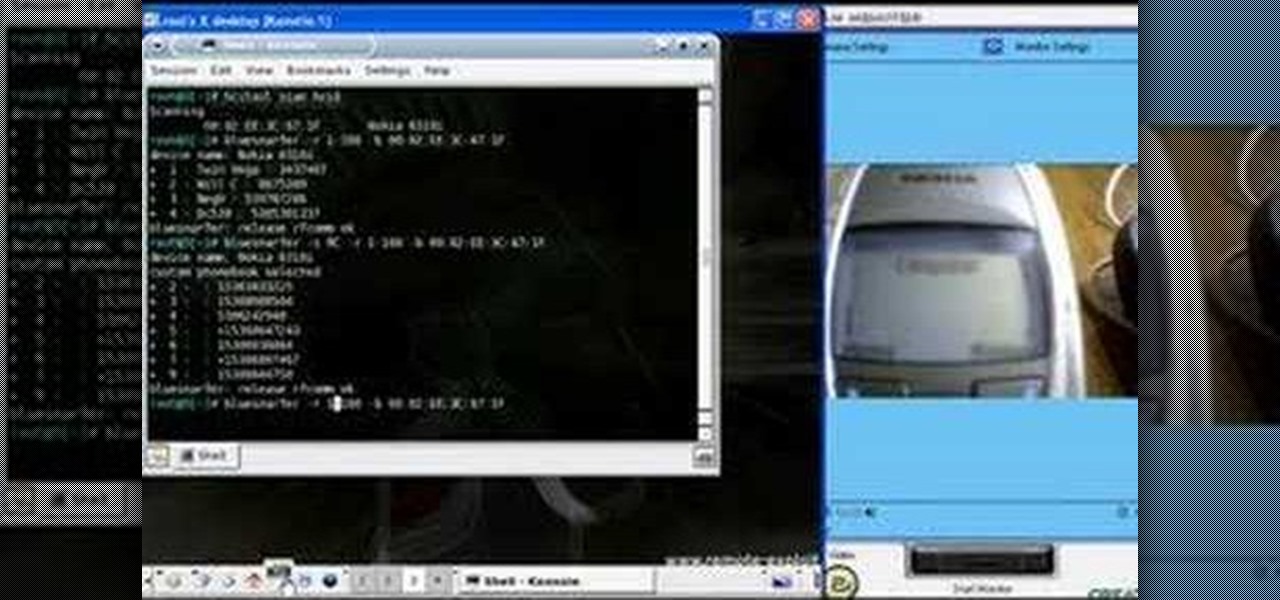
Check out this video tutorial to see how to bluesnarf a Nokia 6310i handset (cell phone). What is Bluesnarfing exactly?

A cold frame is a great way to extend the growing season in your garden. When you set up a cold frame, you can keep your plants healthy and growing, even when it's cold outside. In this video tutorial, you'll learn how to set up and use a cold frame.

Aerating your soil is an essential part of gardening, but it can be long and back-breaking work. In this episode of Growing Wisdom, Dave Epstein will teach you how to use a broadfork to aerate your soil. Using a broadfork, you can aerate the soil without damaging the soil's ecology.

The emergence of Facebook's collaboration with Ray-Ban to launch Stories smartglasses has finally put an exclamation point on a new category of smartglasses: the pre-augmented reality wearable segment.

On this platform, we talk a lot about the future of augmented reality, and we pay attention to what is being said elsewhere as well.

Your smartphone is likely full of COVID-19 news and coronavirus panic. These are scary days, and there doesn't seem to be any end in sight. If you're having trouble coping with the stress and anxiety the virus brings with it, know that your iPhone or Android device can actually help you, rather than just bring you further down.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?