
News: Cisco & Accenture Lead $17.2 Million Investment Round in Upskill's Enterprise AR Suite
Enterprise augmented reality software provider Upskill has raised $17.2 million in its latest round of funding, led by new investors Cisco and Accenture.


Enterprise augmented reality software provider Upskill has raised $17.2 million in its latest round of funding, led by new investors Cisco and Accenture.

Snap Inc.'s dedication to augmented reality has expanded the world lenses in Snapchat to our own Bitmojis. While it's great to see our characters interacting with real environments, we haven't seen them connect to other Bitmoji in AR space. That all changes with "3D Friendmojis," a lens from Snapchat that lets you stage scenes between your Bitmoji and a friend's.

Thanks to Samsung Experience 9.0 on the Galaxy S8 (AKA TouchWiz Oreo), we know the upcoming Galaxy S9 is going to enjoy some of the new keyboard changes coming to Samsung's iteration of Android 8.0. Those who preorder the device on March 2 or pick it up on March 16 can expect these changes out of the box, as the S9 will be running Samsung Experience 9.0 on day one.

We already know that the connection between virtual and augmented reality is pretty tight, with tools like Unity making porting some apps between the two platforms fairly frictionless. But there are some things currently going in VR that just don't need to come to the world of AR.

A recent update to Facebook's News Feed could significantly broaden its reach when it comes to delivering augmented reality content.
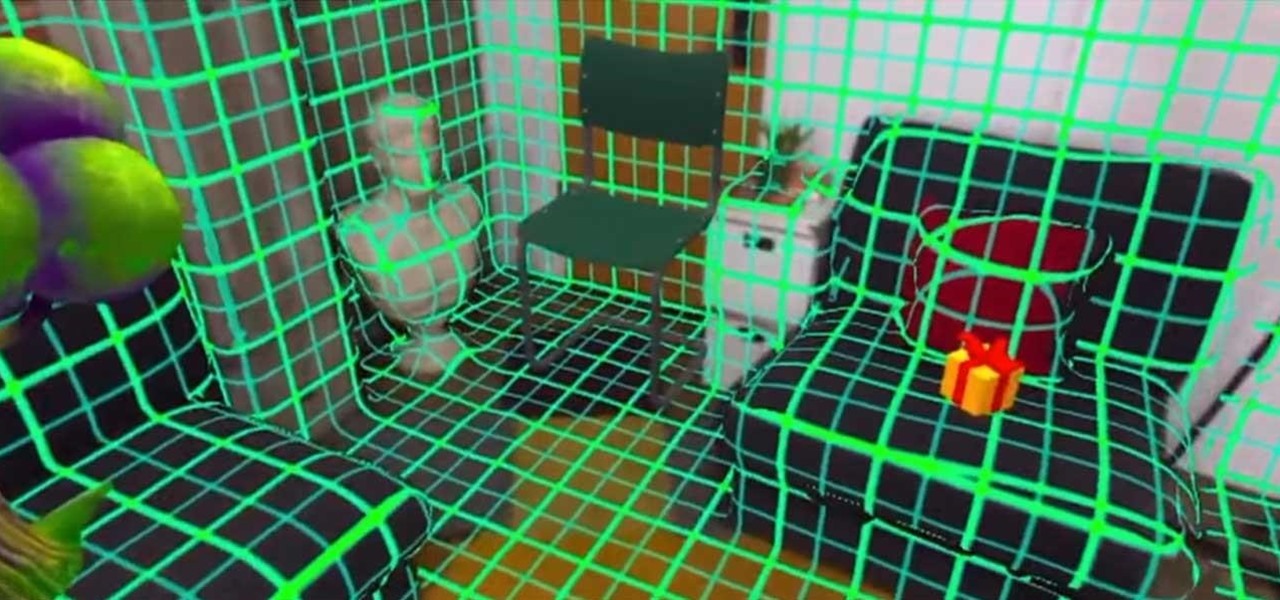
San Francisco-based 6D.ai is preparing to launch a beta of its AR cloud platform that's capable of constructing a real-time dense mesh from crowdsourced data for use in 3D mapping and multi-user AR experiences.

Although The New York Times may have won the race in terms of presenting coverage of the 2018 Winter Olympics through augmented reality first, The Washington Post is nevertheless working to compete in AR in a different way—via gaming.

If you're an Android user, you're very likely jealous of your iPhone friends who have access to the wide, wonderful world of augmented reality thanks to ARKit.

Augmented reality software maker 8th Wall has closed a Series A funding round of $8 million in capital to feed the growth of its development platform.

Soon, Pokémon GO allies attacking a raid boss at a gym will be able to do so together in augmented reality.

Medical training technology company CAE Healthcare has given birth to the latest example of how augmented reality can help to build practical operating room skills for doctors and nurses. The company's newest product is called LucinaAR, which harnesses the power of the Microsoft HoloLens.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

If you ever thought the Snorlax in Pokémon Go should be taller, and you have an iPhone compatible with ARKit, get ready to look up.

Last week, Magic Leap CEO Rony Abovitz teased his Twitter followers with some "fun and cool stuff" to share in the coming days. On Monday, he made good on that promise, sort of.

Just as the modern travel experience has improved thanks to the internet, Airbnb wants to make your stay in a stranger's home easier by way of augmented and virtual reality.

The first teaser for Jurassic World: Fallen Kingdom just hit computer screens on Sunday, but now plans for an augmented reality book for the film have also emerged.

It appears that the new AR app from LEGO is inching closer to release.
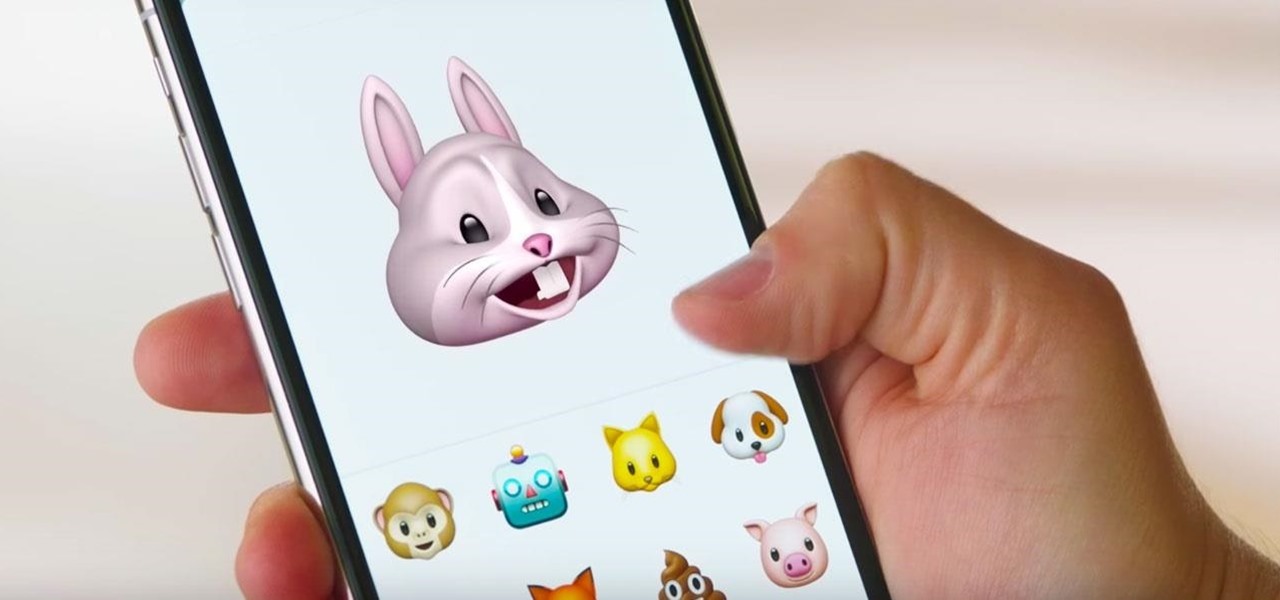
Apple CEO Tim Cook told us that augmented reality would change everything, and now we have a better idea of exactly what he meant.

If you bought your first mobile phone in the early-to-mid-2000s, there's a good chance that it was a Nokia and it had the game Snake preinstalled.

Google just unveiled it's biggest search product in recent memory, except this time the search giant is looking to take over the world of virtual objects.

It's finally that time. Stranger Things 2 dropped today, just days before Halloween. And to get you in the mood, Snapchat has quietly launched a spooky new filter that lets you immerse yourself in the world depicted in the hit Netflix series.

With a pair of new APIs and low-latency media servers, Twilio's Programmable Video platform could soon help ARKit and ARCore app developers build shared AR experiences between multiple users.

Microsoft's latest move to further secure its hold on the emerging mixed reality space comes in the form of two new Mixed Reality Capture Studios in San Francisco (the flagship studio) and London.
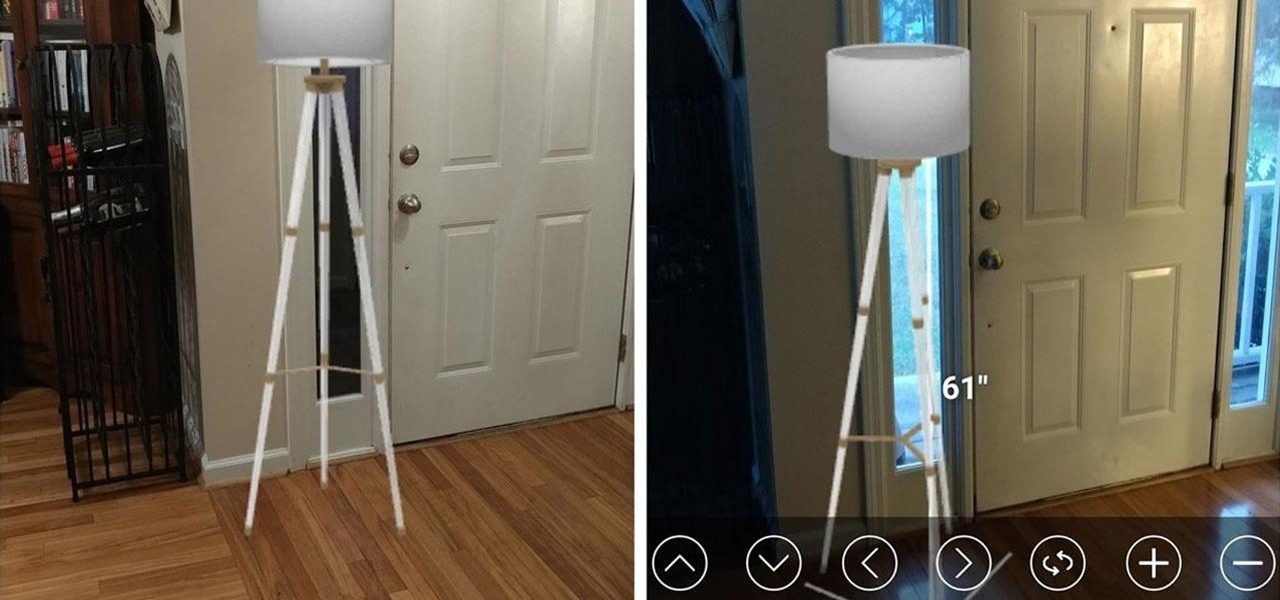
While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.
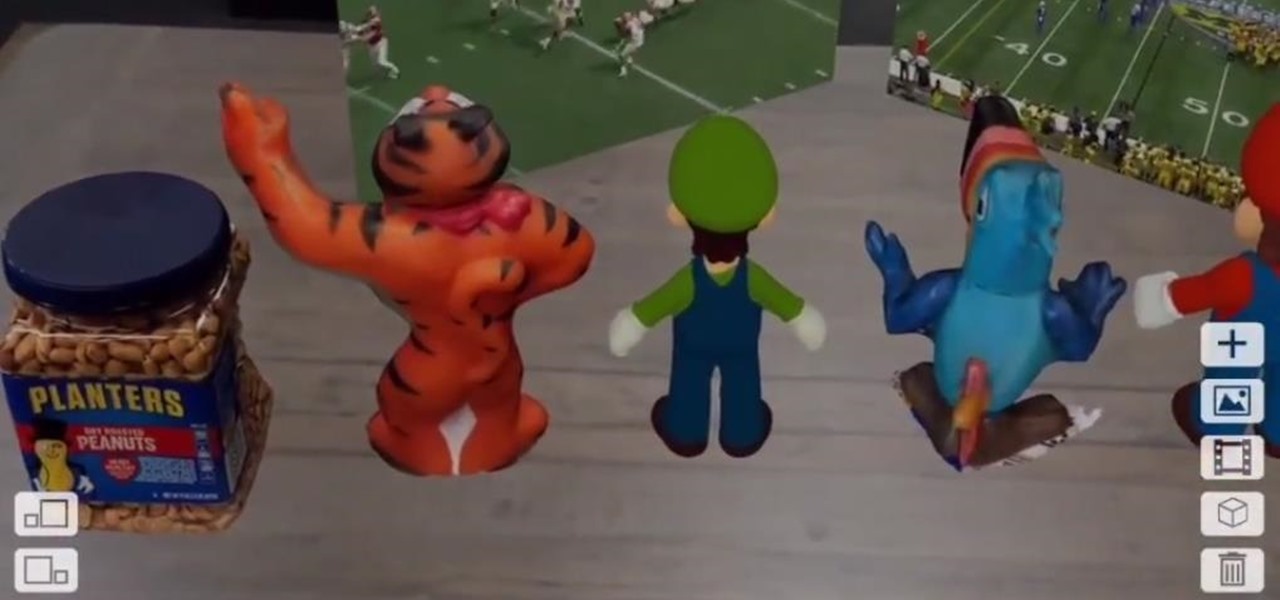
One of the byproducts of the success of Pokémon Go was the viral images that made the rounds on social media of people putting Pikachus, Charmanders, and their brethren in compromising positions. Snapchat has a similar claim to fame, most recently with the inexplicable popularity of the dancing hotdog.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

During Google Developer Days, taking place now at the ICE Congress Center in Krakow, Poland, an introductory session on ARCore provides some insights on how the platform operates.

Augmented reality developer Blippar has created a new visual positioning service based on computer vision that is two times more accurate than GPS in urban locales.

On August 21, a total solar eclipse will be able to be seen across the country for the first time since June 8, 1918, and it's going to be incredible. Retired NASA astrophysicist Fred Espenak spoke to ABC News about what to expect and said:
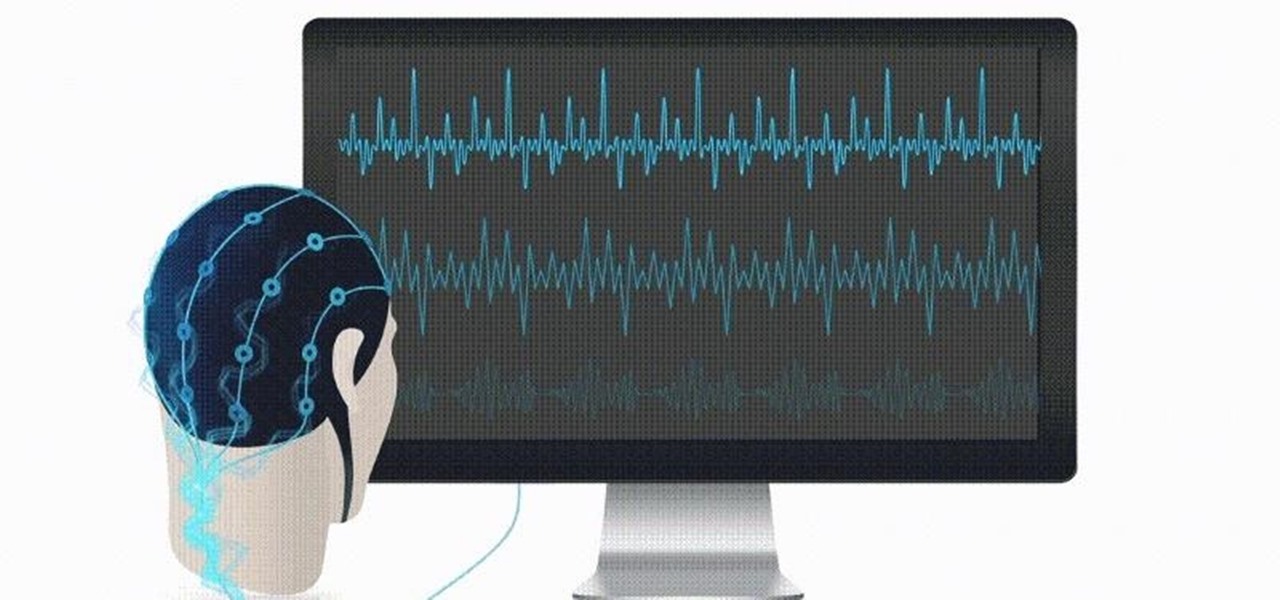
As promised earlier this year, Neurable has introduced limited beta of a Unity-compatible software developer's kit (SDK) for its brain control interface (BCI) for augmented and virtual reality.
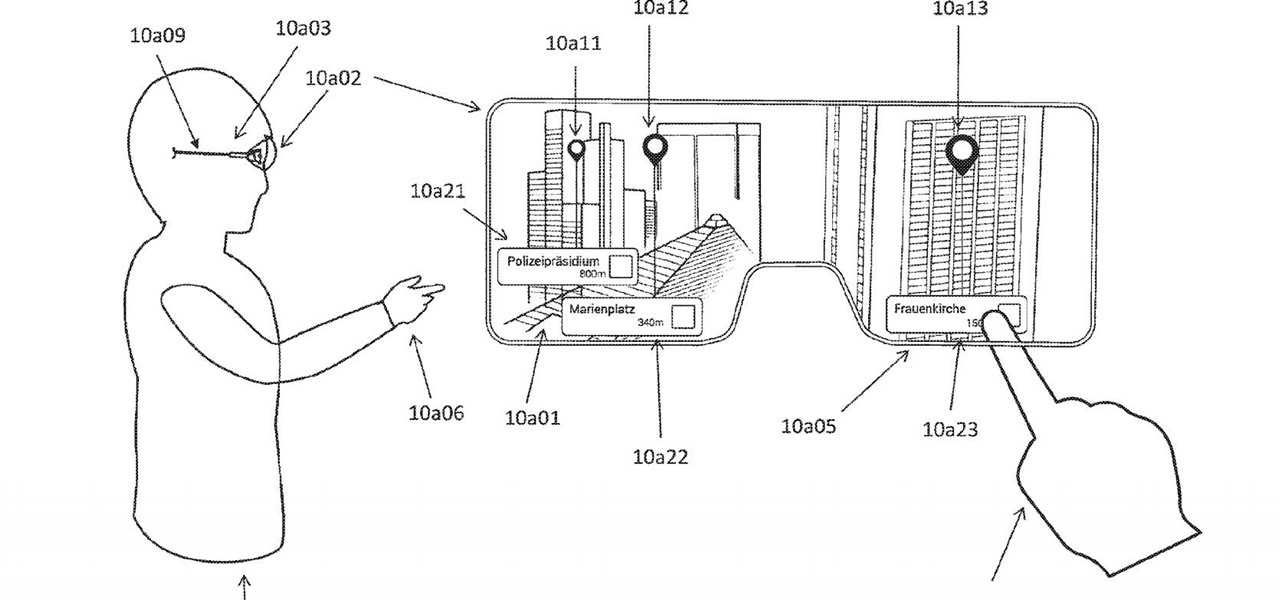
Apple has sprung a massive AR following since the announcement of their ARKit, with users waiting to see what exactly the tech giant will do next.

The app SketchAR is an easy, innovative way to trace what you want to draw onto the canvas of your choice. It was first released on iOS and Android Tango phones, but now, finally, it has been released on Microsoft's HoloLens.

The auto industry continues to shift into high gear to lay the groundwork for driverless cars with an electric vehicle (EV) emphasis.

The BBC's Taster VR app released July 5 is providing new experiences visible on both iOS and Android, and one of the releases is a VR version of Planet Earth II. It is viewable on YouTube and works properly when viewed with a mobile VR headset.

Though the Microsoft HoloLens' release to the consumer market is still a distant thought at the moment, Ubisoft is preparing for the future with the unveiling of AR video game prototypes.

These past few days have brought more bad news for our national parks. Interior Secretary Ryan Zinke confirmed that there will definitely be big cuts to national park budgets. This comes after Donald Trump's budget request revealed a call for $300 million cuts to national parks.

All the Driverless news you need to know from the past 24 hours, bundled together in a tightly written package, about Uber, London delivery services, capital investments, and kangaroos.

The number of Legionnaires' cases in New York over the last couple weeks has led to concern and recommendations of caution for those at risk.
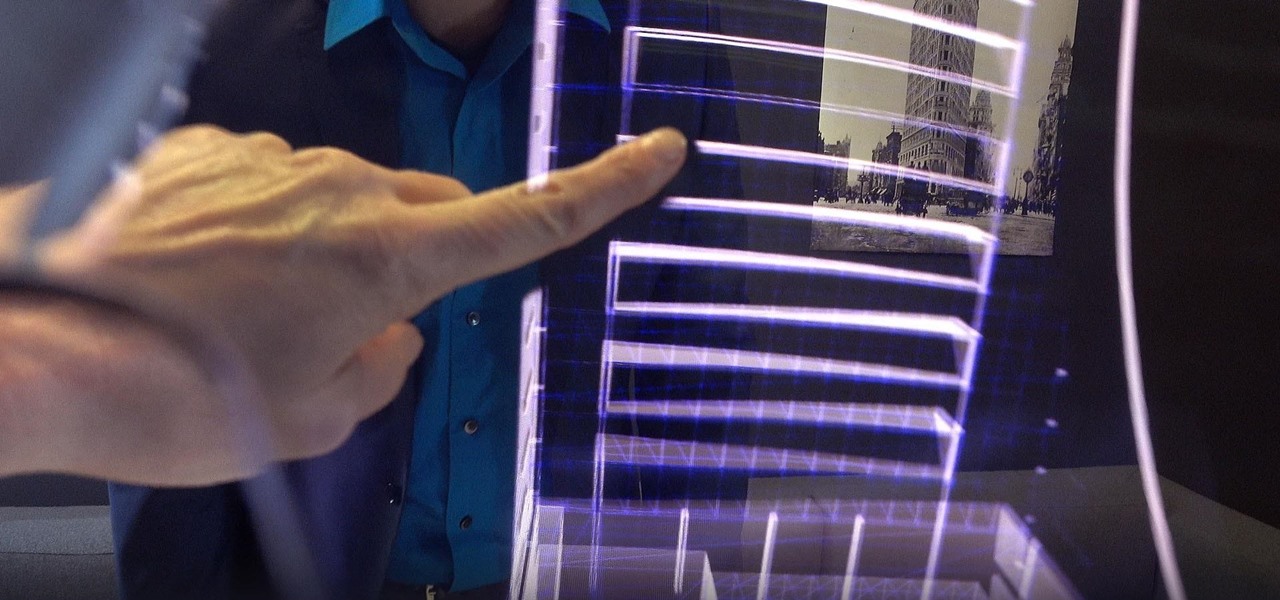
While two augmented reality companies were recently recognized for their innovative technologies, other companies have turned to augmented reality to innovate in their respective fields. Over the past week, use cases have ranged from selling snacks and video games to raising awareness for public health issues.

Uber CEO and co-founder Travis Kalanick is taking an indefinite leave of absence from the company, as Uber's recent upheaval has far overshadowed any developments in its driverless initiative during the past few days.