Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

Read palms for success in the hand. To focus mainly on business or workplace look to the mound of Jupiter, which should be prominent. Additionally, the first finger should be longer. A longer first finger is as long as the third finger. This shows someone who is ambitious, connected with work, and authority over others.

Treasure may be buried as close as your own backyard. If you have some time to kill, try the art of treasure hunting. You’ll be sure to discover lots of interesting thing after learning how to use a metal detector to look for treasure.

In this series of spine chilling costume videos, our Halloween authority tells you how to create a glow-in-the-dark skeleton costume that would have scared the Dickens out of Charles himself.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

Learning a new language as an adult isn't just hard because your brain works differently from when you were a kid. You also have to contend with having less time and energy to practice. However, if you're looking to add another language to your repertoire at a pace you decide, then the Babbel Language Learning: Lifetime Subscription for All Languages: 2-Pack will be a useful tool for you.

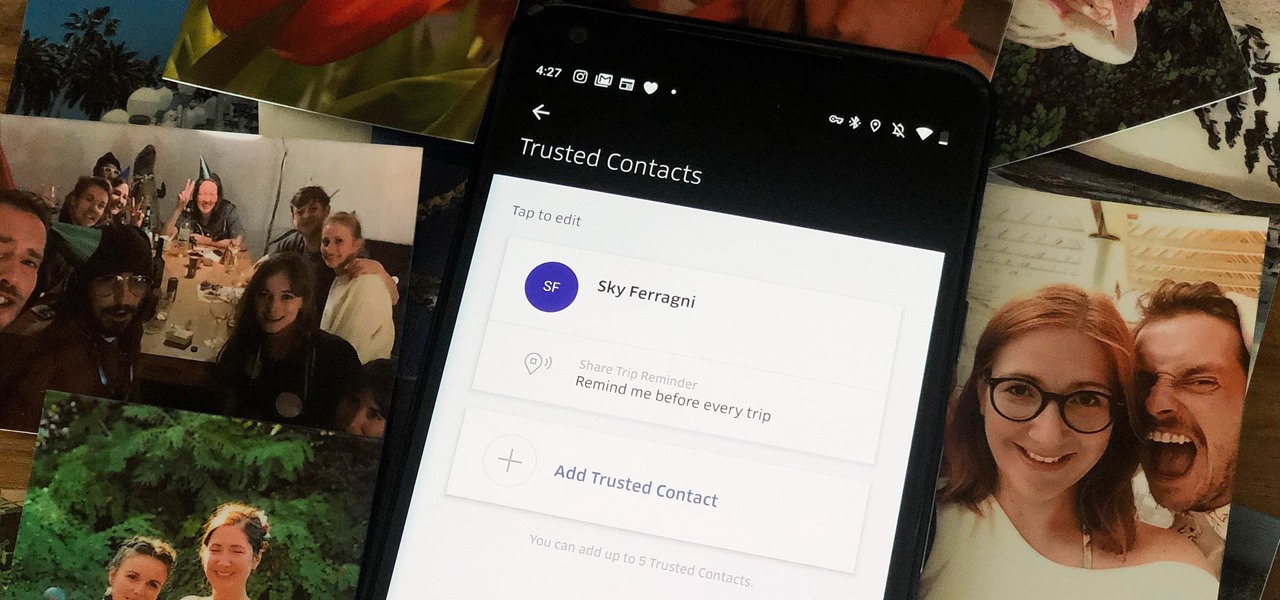
When you're riding in an Uber, on your way to meet family or friends, they may want to know where you are exactly to see how long until your arrival. On the other side of the coin, there may be times when you want to tell family or friends where you and your Uber car are without them asking, like when you're in a dangerous situation. Uber makes this easy, as long as you set it up first.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

Ever since Google CEO Sundar Pichai took the helms of the world's most valuable brand, he has made it his mission to bring smartphones to lower-income communities. Born in India, Mr. Pichai has created several programs to address the needs of the Indian market, particularly the lower income families.

Huawei's sub-brand, Honor, just announced a pair of new smartphones to help close out the year. We knew the midrange Honor 7X was on its way, but what came as a surprise was the announcement of the Honor View 10 and its impending release in the US. Thanks to Honor, US customers will have even more choices in the flagship market with this new device.

While not cuddly to most, bats are shy, skilled flyers that fill an important role in their environments. A new study reveals a deadly disease decimating North American bat populations has stepped up its attack on vulnerable bat populations in the summer months.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

As summer heats up, new maps from the Centers for Disease Control and Prevention (CDC) gives us our best guess at where Zika-carrying mosquitoes could be hanging out this year in the US.

The ability of one microbe to adapt is giving it a whole new career as a sexually transmitted disease. Usually content with the back of the throat and nose of those who carry it, the dangerous pathogen Neisseria meningitidis has adapted to cause an illness that looks a lot like gonorrhea.

On October 17, 1943, a story in the New York Herald Tribune read "Many laymen — husbands, wives, parents, brothers, sisters, friends — beg Dr. Keefer for penicillin," according to the American Chemical Society. Dr. Chester Keefer of Boston was responsible for rationing the new miracle drug, penicillin.

Yellow fever has emerged again in Brazil, causing death and disease to people unprepared for this mosquito-borne illness.

Have you ever had the stomach flu, aka the 24-hour flu? Well, chances are high that you never had influenza, but an intestinal infection called gastroenteritis.

Even as health authorities describe the symptoms of Zika infection in the general population as mild, a new surveillance study finds serious side effects are more common, and serious, than previously thought.

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...

Avian flu is making the news again with new human cases in China reported in January. What does "avian flu" mean to you—and how dangerous is it?

A recent pathogen outbreak in Illinois is just one of many outbreaks of an underappreciated, but serious, viral infection passed from rodents to humans. These hantaviruses have been cropping up more frequently in the last decade or so, giving us more reason to clean out our dusty attics, basements, and garages.

If you could save the world by eating a burger, would you? Two companies, Beyond Meat and Impossible Foods, are on a mission to redefine veggie burgers and eliminate all of the downsides of animal farming on our planet. With over five years of research and product testing, they've finally figured out how to make a plant-based burger look, feel, and taste just like real meat.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

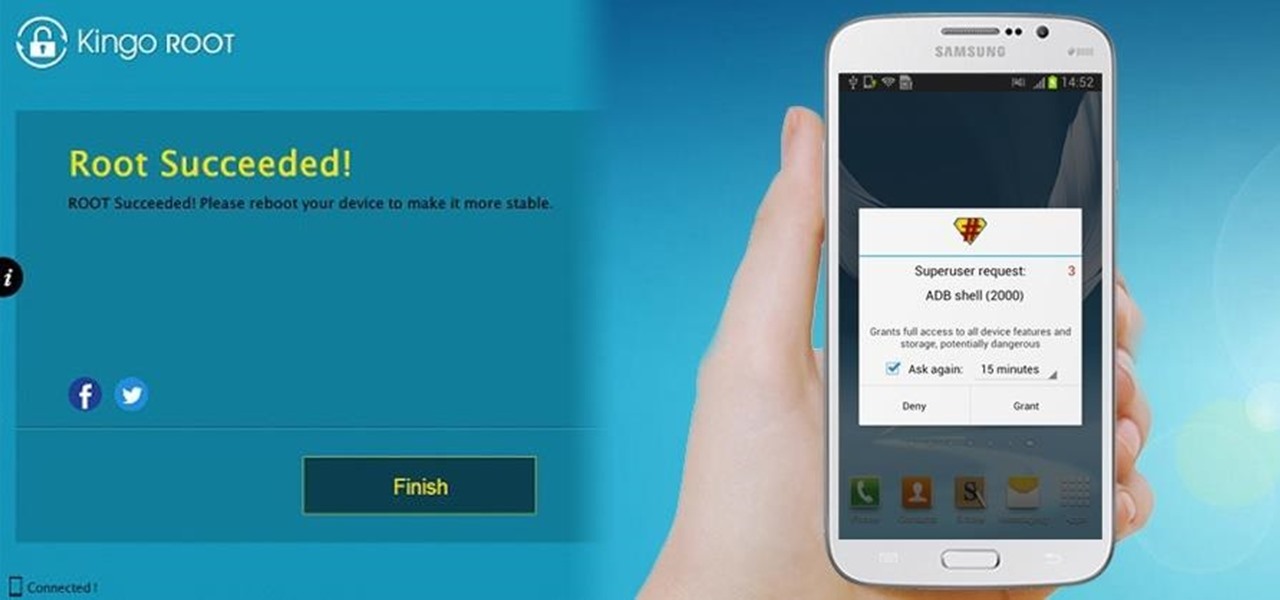
To Android users, especially advanced ones, rooting their phones or tablets is becoming a necessity. Rooting Android could be complicated, if you do it all by yourself, even with a step-by-step tutorial. However, what Kingo Android Root offers you is a true one-click experience when rooting your Android.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Earlier this month, AT&T quietly introduced a new "Mobility Administrative Fee" which levies a $0.61 monthly charge to all postpaid contracts. While it's a seemingly small amount on an individual basis adding up to $7.32 per year, with its huge customer base, AT&T stands to make around half a billion from the tight-lipped move. AT&T has stated that the fee will "help cover certain expenses, such as interconnection and cell site rents and maintenance" that's consistent with other phone carrier...

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Amongst the many rumors emerging about the upcoming Samsung Galaxy S4, one that seems like a fairly sure bet is the inclusion of Google's Photo Sphere feature.

A Steampunk's Guide to Sex was the subject of a recent successful Kickstarter campaign, and I now hold the finished book in my hands. As such, I can say (mostly) unreservedly that you should buy this book. Allow me to tell you why, before I get into the nitty-gritty about the book itself. Sex is something of an odd topic in America because it's perfectly legal, and yet taboo. Unlike things that are illegal and not taboo, like drug use, murder, theft, etc. What this means is that children can ...

Learn about the career of a professional tour director in this free series of world travel videos from our tour guide authority. Cherie Anderson suggests that you start your career by guiding tours around your area, then move up to tours in other parts of the United States; before you know it, you’ll be traveling the world! She also tells you how to get hired as a cruise ship director. Plus find out such insider information as what to wear, how to focus your tour narration and how much you sh...

One of the best recent outings in the Marvel universe is the animated series What If...?, which explores alternate universe takes on various superhero storylines that deliver fascinating scenarios if one single factor had been different in the story.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.