The origins of vodka are shrouded in mystery, with both Russia and Poland laying claim to its invention. Some say Genovese merchants brought vodka (then known as aqua vitae, or the water of life) in the late fourteenth century to Russia. For many years, vodka wasn't just an alcoholic beverage: it was also consumed as medicine.

Aluminum foil is one of those things that every cook, experienced or just starting out, has in their kitchen. And while we may think we know how useful this handy material can be, there are hundreds of ways we could be utilizing tinfoil to make our lives a whole lot easier.

The paper towel is a wondrous invention. It allows cooks to wipe up really gross stuff without having to constantly do laundry and drain fried foods so they're crunchy and crispy instead of oily and heavy. But did you know that your humble paper towel has several other uses besides the obvious ones? Read on to find out these essential hacks.

Foodies and big-time chefs like Thomas Keller go crazy for fleur de sel. This finishing salt appears in fancy eateries and cookbooks the world over, and in the early 2000s, it was not uncommon to see diners in a high-end restaurant sprinkle a pinch of fleur de sel on their plates from their own personal stash.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.
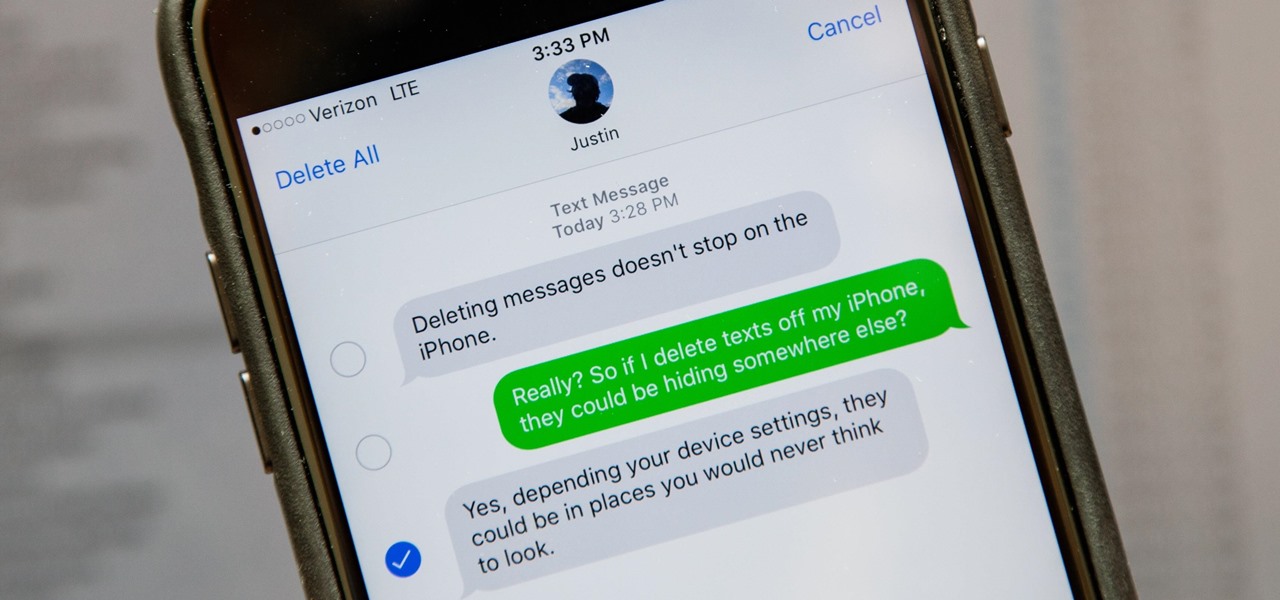
Deleting text messages on your iPhone may seem like a pretty simple task, but it's those really simple tasks that usually end up causing headaches later on. Data can stick around, even if you asked it not to, so there's always a slight chance that embarrassing and incriminating texts you supposedly deleted may end up in the wrong hands one day.

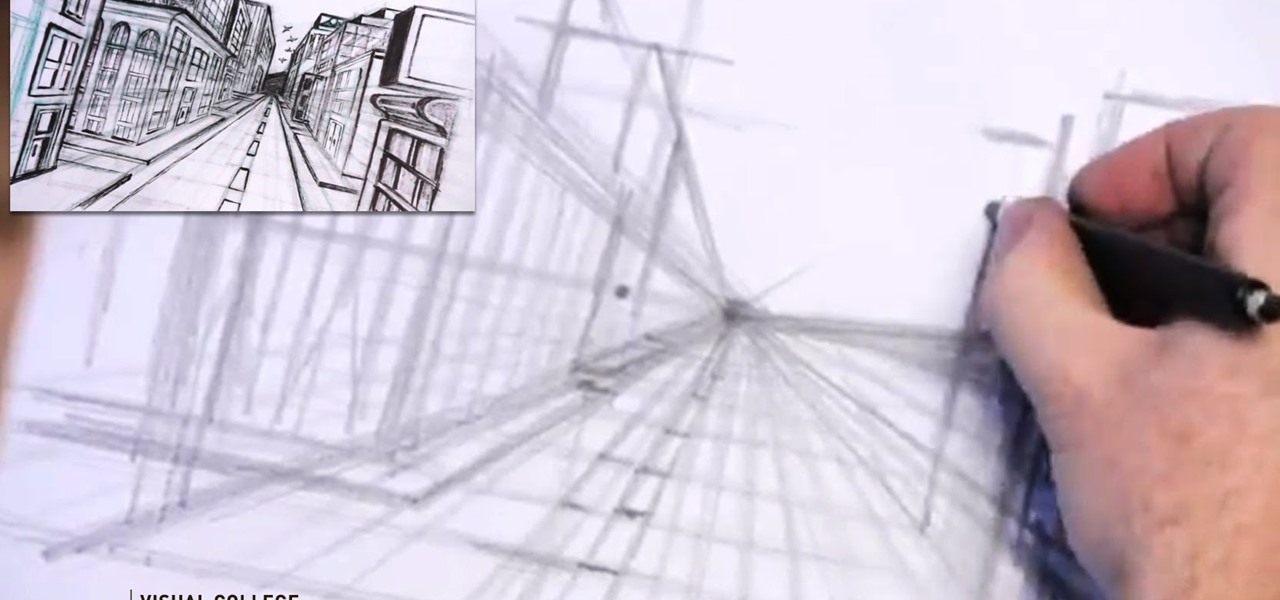
Video: . Step 1: Today We Are Going to Draw a City in One Point Perspective -- Buildings in the City Going into One Point Perspective. Let's Start Our Drawing with the Vanishing Point and Horizon Line. In Order to Get the Feel of the Drawing We Need to Determine Where Vanishing Point Will Be. Feel Free to Improvise and Change It Depending on What You Want to Achieve. Start Mapping Lines in.

Not that long ago I wrote an article discussing what it would be like, realistically, if you were to accidentally travel back in time to the Victorian era. At the end of that article, I mentioned that the best thing you could bring with you on a time-traveling adventure is a Kindle, or similar e-reader, stuffed full of the knowledge of the 21st century. Why a Kindle? Well, I own a Kindle, and I love it. However, there's far more to it than that.

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

Safari has a new feature that helps you discover the most beneficial aspects of a webpage without having to dig through the page or read the entire thing — and it works on iPhone, iPad, and Mac. It can make web browsing more efficient and websites easier to navigate while ensuring the visibility of important details.

A massive new feature just hit Apple Music, and it's the biggest thing to happen to Apple Music since Apple Music was even a thing.

A massive new feature is about to hit Apple Music next week. Anyone can check it out, but only Apple Music subscribers through an Individual, Student, Family, or Apple One plan can take full advantage of the new perk that's been years in the making.

There has been drag-and-drop functionality for iPhone since at least iOS 11, but iOS 15 adds a new ability that makes essential emails even easier to find when you need them.

For most mainstream users, LiDAR sensors for precision depth sensing remain the exclusive domain of Apple iPhones and iPads, but Google is helping Android device makers close the depth gap on the software side via its ARCore toolkit.

It's almost impossible to use Apple News at night without having to mess with the white point and zoom filters. That might sound a bit dramatic, but it's really not when you consider that iOS 13 has a perfectly good Dark Mode that should work for News. So why are we stuck reading most news stories in Light Mode? We're not, but you have to put a little work into it going dark in News.

An attacker can create three, five, or even ten new Netcat connections to a compromised MacBook with one command. Performing complex post-exploitation attacks might otherwise be difficult from a single shell without this essential trick.

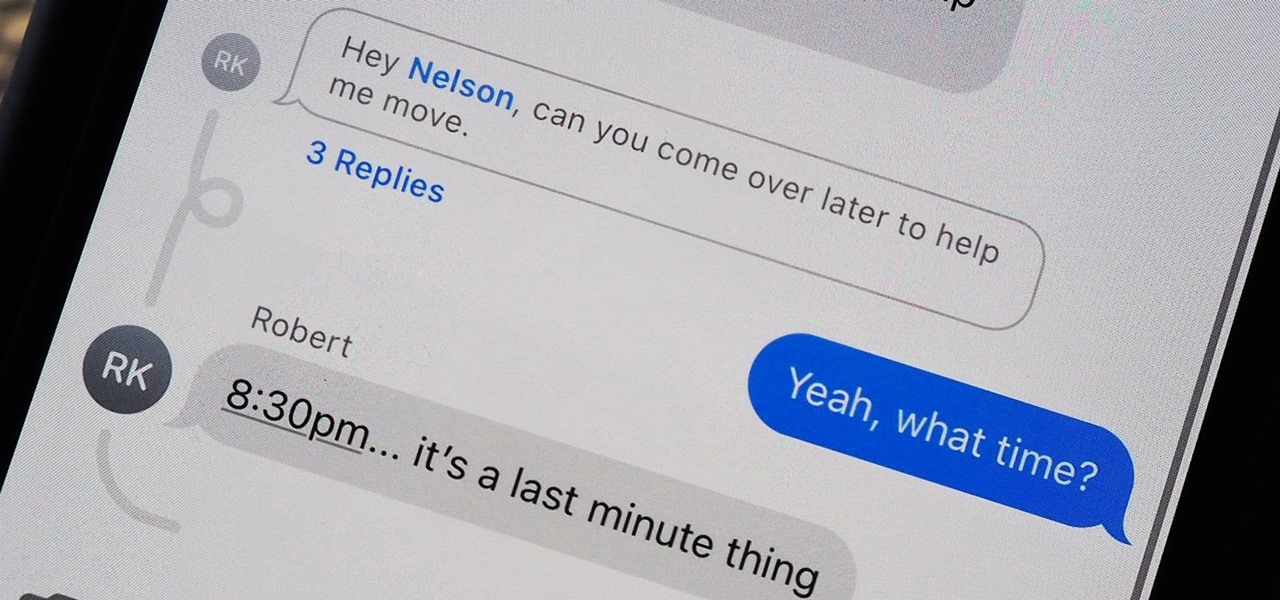
A group conversation can be a chaotic place. Even with a small number of people, you still may get more messages than you can keep track of on your iPhone. What makes it even worse is trying to sort through all of the conversations within conversations. Apple, however, wants to make things easier on all of us, which is why iOS 14 allows you to respond to specific iMessages using inline replies.

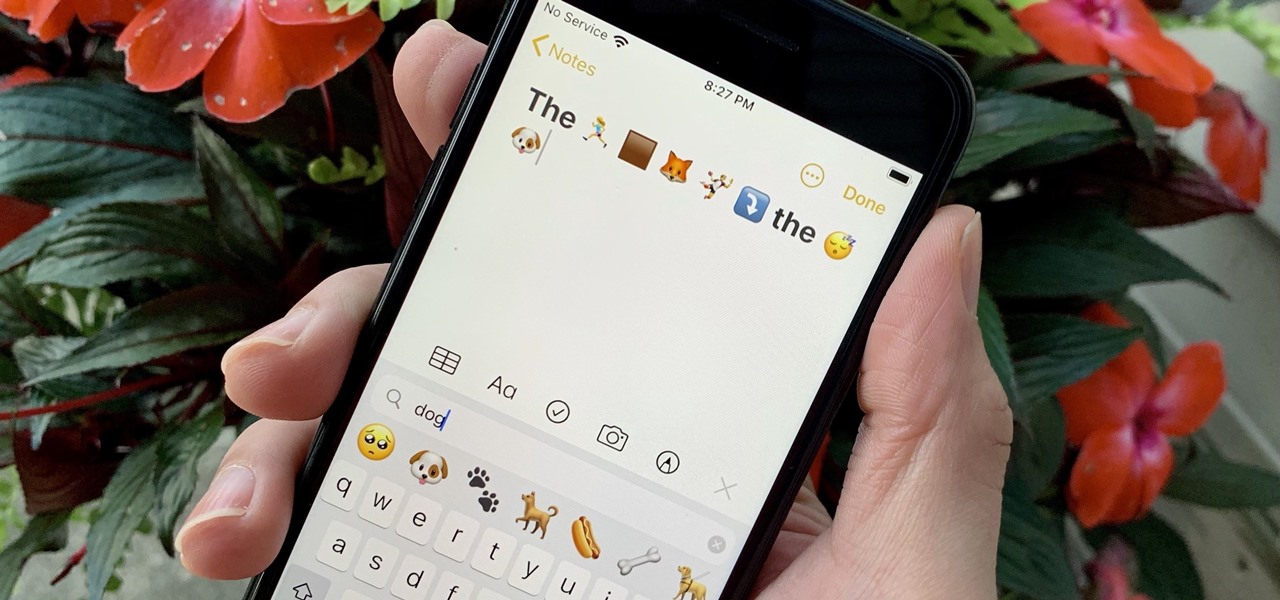
Since their introduction, emoji have become as essential to the iPhone as the touchscreen itself. While the original set of emoji was manageable, finding a particular emoji these days has become a chore. Apple tried to make it easier in past iOS versions, but it has avoided adding the most sensible option — until now.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for an official announcement to get an idea of what new features and changes are coming to iPhone this year.

In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and helpful productivity apps is a must if you want to get things done successfully.

UPDATE: The OnePlus 8 Pro has been released! Check it out on the official OnePlus website or read through the rumored specs we've left below for posterity.

Phones these days are expensive. The iPhone 11 Pro is presumed to start at $999, following the iPhone XS and iPhone X's leads. One way to bring down that cost is to trade in your old iPhone, but there isn't one clear-cut way to do that. You could trade your iPhone into a participating website or put yourself out there and sell the iPhone on your own. It's all about what's best for you.

Navigating and editing text is an essential part of any operating system, and with iOS 13, Apple has made some significant changes. Some things remain the same when working with text, but there are many updates to moving the cursor, scrolling, and selecting, cutting, copying, pasting, undoing, and redoing text.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

While our smartphones are many things, one of their primary functions is to make calls. Many of us try to avoid ever having to make calls, but there are situations when it's a must, such as wishing your grandma happy Birthday or calling 911 — and in those times you want stellar call quality.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

The music and sound effects that play in the background of any videos you edit helps set the tone, so it's essential to get it right. Enlight Videoleap, an extremely powerful and popular mobile video editing tool for iOS, lets you quickly and easily add audio from your iPhone and the cloud, but things can still get a little confusing when you have a timeline full of clips.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Planning a vacation overseas can sometimes feel overwhelming with the number of things you need to remember before heading out. Since smartphones keep us connected at all times, it's essential that you have everything you need here as well. Unexpected events can arise while on your trip, and you should be prepared for anything like a survival expert.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.

The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better comprehend.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

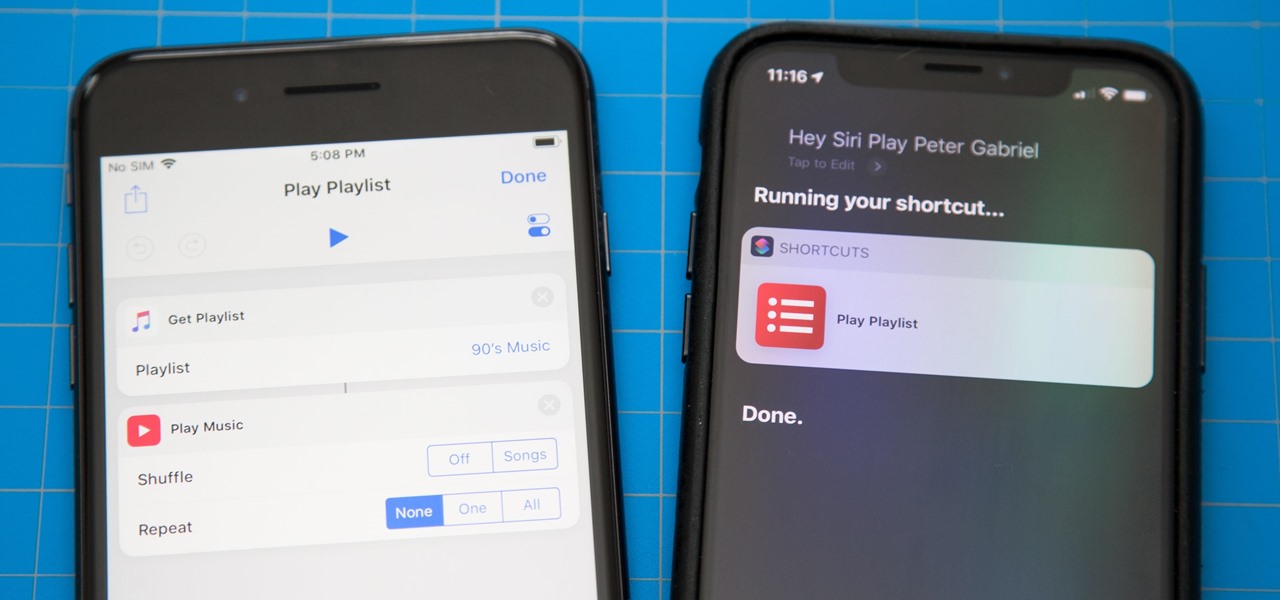
One of the most exciting additions to iOS 12 for iPhones is called Shortcuts, a tool integrated with Siri to help you get things done faster. While there are a few recommended shortcuts available to you in Siri's settings in iOS 12, the Shortcuts app brings the functionality of Workflow to Siri so you can build your own custom actions or select from the gallery of available shortcuts.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.