There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

There's no TV show that stands out quite like American Horror Story. With its crazy characters and nightmarish storylines, there are countless costume ideas hiding in its episodes.

Screenshots are all the rage. From sharing high game scores with friends to placing conversation threads online for the world to see to secretly capturing Snapchats, this function of smartphones is prevalent through modern society.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Back when 4.1 Jelly Bean came out (boy, how time flies), Android introduced expandable notifications. Depending on the notification, a simple swipe down with your finger could expand it and show extra content, like Delete and Reply buttons for Gmail messages.

Day of the Dead, or Día de Muertos, is a Mexican holiday celebrated on November 1 or 2 each year to honor the dead. It's often lumped in with Halloween, and while some people do dress up in costumes, the day is much more focused on remembering the lives of friends and family members who have passed. People who are unfamiliar with the holiday sometimes consider one of its most pervasive symbols, the sugar skull, rather morbid. And special makeup effects artist Rick Baker is no stranger to the ...

PowerPoint Tutorials for Microsoft PowerPoint presentation software. In this introduction tutorial we will be using PowerPoint 2010 and will focus on the interface workspace by reviewing the ribbon, slide pane and slide tabs. The ribbon is designed much like a website navigation menu bar and has multiple categories to separate all of the tools into an organized bar. By default the Home tab is selected and will include most of the tools that are commonly used when editing and creating a PowerP...

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

In this web design tutorial, you will learn to modify and create various styled quick shapes using info bar and tool modes. As you follow through future tutorials, you will start to realize how important the info bar is for using the Xara Web Designer software.

This Windows 8 guide is for those who are new adopters of the Windows 8 operating system. Maybe you just bought a new PC with Windows 8 and you need to learn your way around, then this tutorial is for you.

There are plenty of ways to create decent looking special effects on a budget. You can use basic, inexpensive materials to make ground explosions or realistic looking alien landscapes. But nothing says Hollywood quite like your own green screen.

This tutorial is for those who are new to Windows 8.

Thanks to its open-source platform and easy-to-use hardware and software, there's literally thousands of Arduino projects detailed online for anyone to make—a magic mirror, DIY polygraph machine, and hotel-hacking dry erase marker just being a few examples. Hell, you can even make the Daft Punk helmet.

This is one of the most fun designs I created this valentines day for girls who needed something easy and trendy to flaunt on their nails on this special day of the year !

This is a very adorable looking nail design that I tried a few days back on my valentines day list of 'nails to do' ! It worked out exactly as I had planned , though during the execution it looked as if it may not, and I was happy enough to post this design online and share it with my viewers!

I have been getting requests for this one since a really long time. So finally a few days back I decided to step up and create a video on nail care and help lots of girls out there who are facing nail issues on a daily basis.

This is a very cute combination of black and white striped with red glitter and red sequins! Video: .

This nail design kind of reminds me of sunrise as well as of sunset at the same time! This nail art is not only incredibly stunning, but also so very easy that you would not believe it! I have shared the video link below for you to have a look and decide what you think of this nail polish design in gradient look for yourself!

In this video I shall be doing a very easy nail design using the sponged gradient technique for nail art designing to get a very effective background for a flakes back nail design pattern over it, which is even easier to create !

This is a very interesting puzzle nail design that I did the other day ! It is super easy to create and uses a combination of matte nail polish and glossy nail polish to create a light crisp effect !

Striping tapes are very popular these days , among nail enthusiasts. One of the main reasons is that not only is it super easy to use, but you can literally create hundreds of styles by using them right !

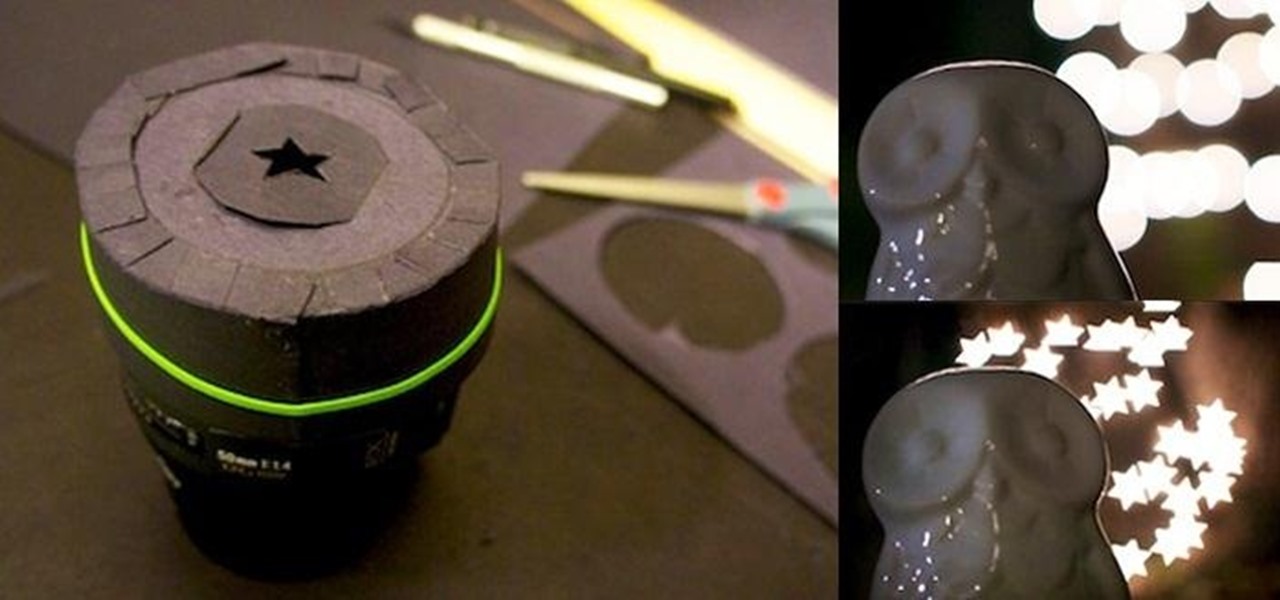
In photography, bokeh refers to the blurry or out-of-focus parts of a shot. Bokeh can be good or bad—it all depends on how you use it. There are tons of ways to create a bokeh effect, whether you go the traditional route with lens filters, digital with Photoshop, or even from your iPhone. With filters, you can use the blurred spaces to produce different shapes and colors. If you have a DSLR and want to experiment with bokeh, this tutorial by Chris Perez over on Apartment Therapy will show you...

Rock, Paper, Scissors is a classic childhood pastime, but some people take it a little more seriously than that. There's the ultimate version, which has 25 gestures instead of the traditional three, and there are even tournaments and championships for those who consider themselves real pros.

I seriously cannot get enough of these sweet ass emblems for Call of Duty: Black Ops 2. Thanks to the new emblem editor, there's just so many possible designs to be made.

Wet-plate collodion photography is a process that lets you develop a photo onto a piece of glass. It has some neat applications, but it's not a simple process, and most people use a special camera to do it because the silver nitrate used to process usually ends up leaking, which would ruin a regular camera.

Forgot the passwords to your email or your other favorite websites? If you typically store your passwords in Internet Explorer (IE9 or other versions) it can be tricky to get your passwords back -- but this tutorial makes it really easy!

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

You've probably seen the classic fruit battery science experiment a thousand times, but I doubt you've ever seen it turned into an art project! Photographer Caleb Charland uses everyday objects like apples, coins and vinegar to create makeshift batteries, then takes these gorgeous long exposure photos. For the apple tree photo, Charland got about 5 volts for every 10 apples, so he had to wire 300 apples to power the lamp for several hours. He used a zinc-coated galvanized nail and copper wire...

If you've ever been on your way to a party and felt that your outfit just wasn't flashy enough, engineering student 'Rambo' has got just the thing for you. His homemade LED suit lights up and dances to the beat of the music, and can even be controlled via Bluetooth.

Cropping images can be a huge pain if you have a bunch to do at once. Even if you have Photoshop or a similar program, the process of opening each individual photo and cropping them one at a time can take forever. A free web-app called Cropp.me makes that task a lot easier by auto-cropping your photos to whatever size you choose. All you have to do is upload an image, choose what size you want it to be, and click Cropp My Images. You can choose from a list of sizes or input a custom size of y...

Motorola launched a new webpage on Friday that tells Android users how to unlock the bootloaders on a limited number of new Motorola smartphones and tablets. This new 'Unlock My Device' page helps demystify the process and make it easier for users to customize their phones.

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

Playing Angry Birds on a computer just got a lot more interesting. Design students Andrew Spitz and Hideaki Matsui made this awesome slingshot controller for one of their classes at the Copenhagen Institute of Interaction Design.

Many Minecrafters think that Minecart Traveling with many rails is the fastest (most efficient) way of travel. They are wrong. There is one other way of traveling with carts on rails, Forward, Backward, and Upward. And it can take you places up to 6X Faster than the traditional Minecart Design, and, its just as simple to make.

One of the most annoying things about summer is mowing the lawn. Depending on how big your yard is, it can mean spending hours out in the hot sun while you could be doing something a lot more fun like watching the Olympics or making giant soap bubbles. Reclaim your summer with this remote control lawn mower that does all the hard work for you.

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.