Puzzle games are great at giving your brain a workout while keeping things fun and killing time. They stimulate your noggin as you strategize and plan your next move, whether it's to keep your character from getting killed, or to get that special item to finally complete your collection and unlock a new feature within the game.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.
Smartphone manufacturers do their best to keep you tied down to their ecosystem, but the reality is that there's not much keeping you from switching. Transfer some files, install a few apps here and there, and all of a sudden, you're knee-deep in a new operating system.

You've spent untold hours playing your favorite games. You know what you love. More importantly, you know what can be improved upon. The distance between vision and reality is not as far as you think. You just need a bit of training.

Usually, flying into unknown territory would mean riding into the "danger zone", but Paramount and Snapchat are taking the trip anyway with one of Summer 2020's most anticipated movie sequels.

Germany-based Augmented reality software maker Re'flekt has added a new tool to its enterprise app development platform that makes it simpler to link AR content to physical objects.

When I'm with my friends on the weekend, we always end up Snapping shots of one another, adding in whatever stickers and lenses we've accumulated over the last week. But these filters are fleeting, so it's always a challenge to keep up with the best new ones. If you want to get a leg up on the competition, this is your one-stop-shop.

Magic Leap has reached a major milestone in the lead-up to the launch of its Magic Leap One: Creator Edition by opening access to its developer portal and software development kit (SDK) to all developers.

On Thursday, Snapchat opened up its walled garden of World Lenses to the masses of creators with the launch of Lens Studio.

While AR apps by Modiface and Perfect Corp. have made it easier for people to shop for makeup without setting foot in a store, MAC Cosmetics wants to give its brick-and-mortar customers the same experience.

Developers are really having a field day with Apple's ARKit, announced last month. Since it's release to developers, videos have been appearing all over the Internet of the different ways that developers are getting creative with the ARKit using iPhones and iPads.

This week, augmented reality spawns in the world of online role-playing games with a soft launch down under from an indie game developer. Meanwhile, in Asia, another startup wins a coveted award for its AR headset. Finally, an established player in the mobile AR touches up its feature set with an app update.

Here's another workday distraction for all you social media lovers out there: Pasted, launching out of beta today on iOS, is a simple collage and photo editing app mixing iconic '90s imagery with a love of the The Shins.

ModiFace, the makers of Sephora's Virtual Artist app which allows users to try on multiple different combinations of makeup through augmented reality, has just bumped up its augmented reality strategy. The company is now including a live-stream option for all those personal makeup trials you've been secretly admiring from the comfort of your own phone.

The Washington Post believes augmented reality adds an extra layer to stories, and they're doubling down on that belief by adding in new AR features into their already popular "rainbow" news (iOS and Android) and Classic (iOS and Android) news apps.

You might notice that there's been a few changes around here. All of us here at WonderHowTo have been working hard to create fun new spaces and topic areas to dig our heels into. We've created a few brand new websites, spiffied up our design, and today we're launching the WonderHowTo network.

Every day the young world of mixed reality is creating new ways for people to work with with computers. We are looking for, and finding, new ways for these head-worn computers to understand what we tell them. Sometimes it is with our hands, sometimes it is where we turn our head, sometimes it is what we say. In the case highlighted below, it's where we walk.

Origami is the Japanese art of folding paper, which has been around since the 1600s. The word origami comes from the two Japanese words ori, meaning "folding," and kami, meaning "paper."

In 4.74 seconds, I can barely bend over to tie my shoes, and somehow this guy managed to crush the human world record for solving the Rubik's Cube in that time exactly.

Many new developers are diving right into the Microsoft HoloLens, but augmented and mixed reality are fairly big subjects in terms of learning. There's a lot to cover and, unfortunately, very few places for someone brand new to Windows Holographic to begin lessons.

We at Food Hacks Daily freakin' love Halloween—it's the perfect time for weird and creepy food. The gruesomer, the better.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

We're all for heaping piles of shredded cheese on our tacos, but what if all that cheese could actually be the taco shell instead? Since this was perhaps one of the more profound food questions we've had in a while, we wasted no time getting to the kitchen and tackling this cheesy challenge.

It seemed appropriate that we announce the winner of the first White Hat Award for Technical Excellence on the Academy Awards weekend. This is, in essence, our "Oscar" here at Null Byte. Remember, this contest began on January 4th, 2016 and just recently closed on February 15th. In this contest, I was looking for:

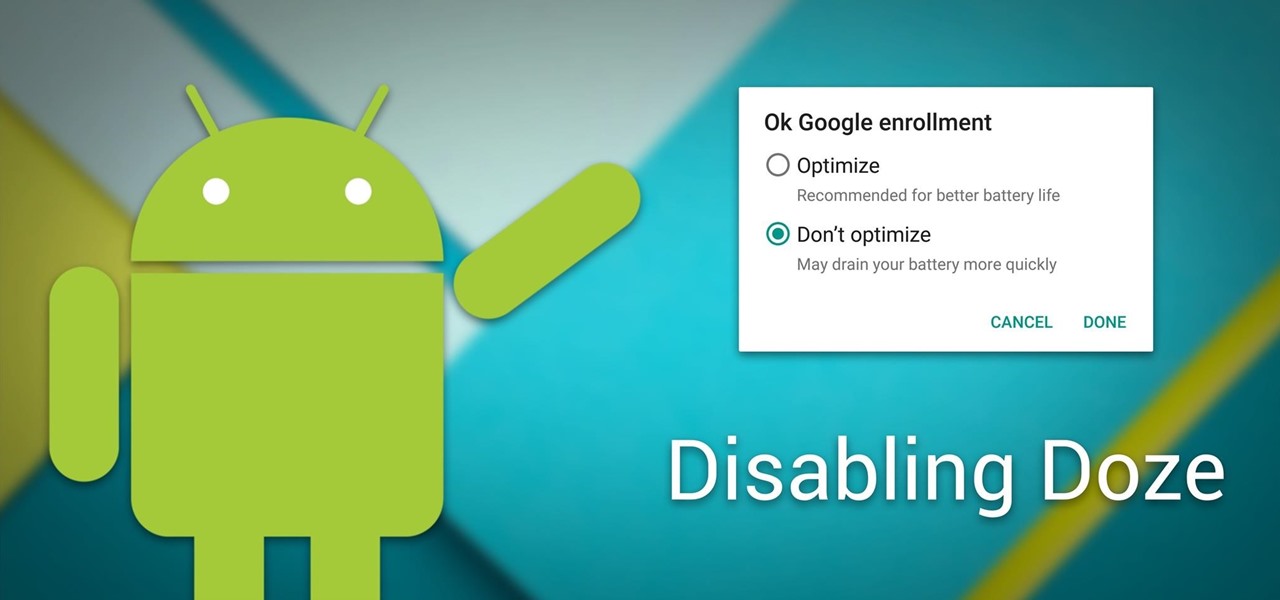
Android Marshmallow introduced a pair of new battery-saving features called Doze and App Standby, and according to the general consensus, both features are a rousing success. Average battery life has increased dramatically for virtually every phone or tablet running Android 6.0, so there's nothing to complain about here, right?

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

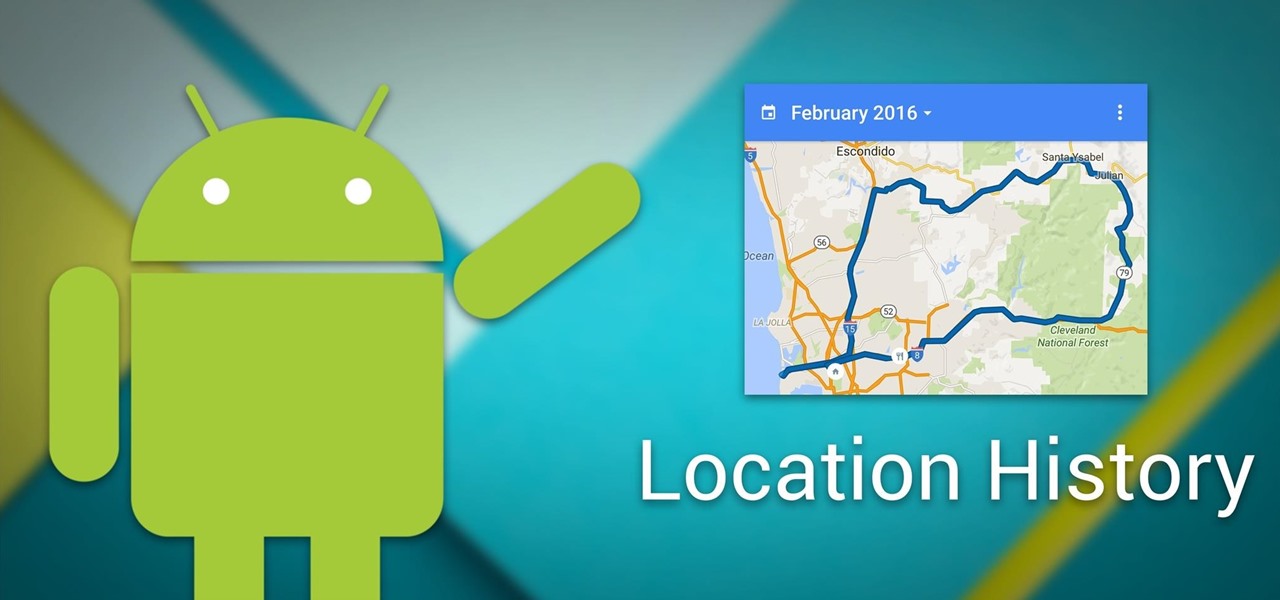
Your smartphone has a GPS chip inside of it that can pinpoint your location down to the nearest 4 meters, and this little device stays in your pocket or purse all day. Combine those two facts and you start to realize that your phone knows exactly where you've been during every moment that has passed since you've owned it.

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

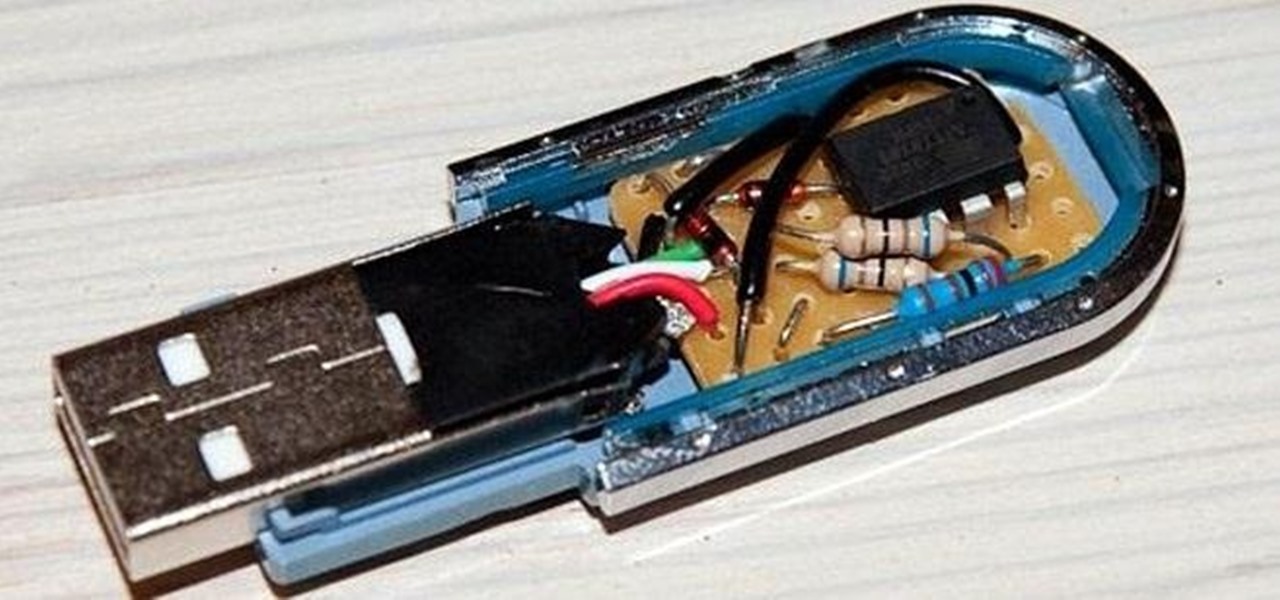
In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

The Xposed Framework was just recently made available for Android Marshmallow, but everything isn't quite back to status quo just yet. Sure, some Xposed modules function properly, but others are a bit buggy, and several don't even work at all. This is mostly a result of changes to the Android system that Lollipop modules relied upon, and such modules will need to be updated for Marshmallow compatibility.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

If you're just starting out with Android—or smartphones in general, for that matter—there are a lot of little things to learn. One of the first terms you'll likely encounter is "Wi-Fi," which is a wireless internet connection served up by a router in your home, office, or local coffee shop. This differs from your smartphone's regular "Mobile Data" connection, which is provided by your cellular carrier and included as part of your monthly bill.

Now that the Xposed Framework has finally been updated for Android Lollipop, we're starting to notice that some modules function properly, while others are a bit buggy or even worse—don't work at all. Most of this is a result of changes to elements of the Android system that KitKat modules relied upon, and such modules will need to be updated for 5.0 compatibility.

Ever since Android 3.0 Honeycomb, Google has been trying to push phone manufacturers to do away with physical menu buttons. Samsung has been one of the lone holdouts, retaining the menu key up until the Galaxy S5, where they finally replaced it with a "recent apps" multitasking button.

We use ADB and Fastboot for so many things in our softModder tutorials, and to get them, you normally have to download the entire Android SDK and install them. But not anymore.

Thanks to HTML5 and dedicated video apps, watching your favorite shows, movies, or video clips on your Samsung Galaxy S4 couldn't be easier. However, there are still times when you'll run into a website that requires Flash to play a video or interact with its content. Although its mobile life has been dead on Android for 2 years, Adobe Flash Player still lives on in the desktop world, fueling millions of websites such as YouTube, Vimeo, ESPN, CNN, and more.

As you may have noticed, many of our tutorials cover topics that require you to have root access. When your phone is rooted, backing up apps doesn't require you to connect to your computer, and installing custom ROMs lets you get more useful settings. Rooting also lets you get rid of the Sense-style menus and status bar, and even upgrade to a newer version of Android.

I'm still amazed by all the things some people just don't know. Script-kiddies often refer to Metasploit if someone asks them how to hack a computer because they think there's simply no other way. Well here I am today trying to increase your set of tools and -of course- skills.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

No matter how many PSAs are published on the topic, studies continue to show that we are generally terrible at creating secure passwords and PINs. Using the same password (or variations of it) for multiple sites is another huge no-no that the majority of people ignore, and even though you should change your passwords frequently, most of us don't.