While becoming the next Mark Zuckerberg may be out of reach for someone just getting introduced to code, the skill has never been more valuable. Just understanding basic programming language is a great thing to put on your resume, and if you know how to code, you’re golden. Software developers and programmers have been the most resistant to the recession, as jobs in the tech industry continue to grow.
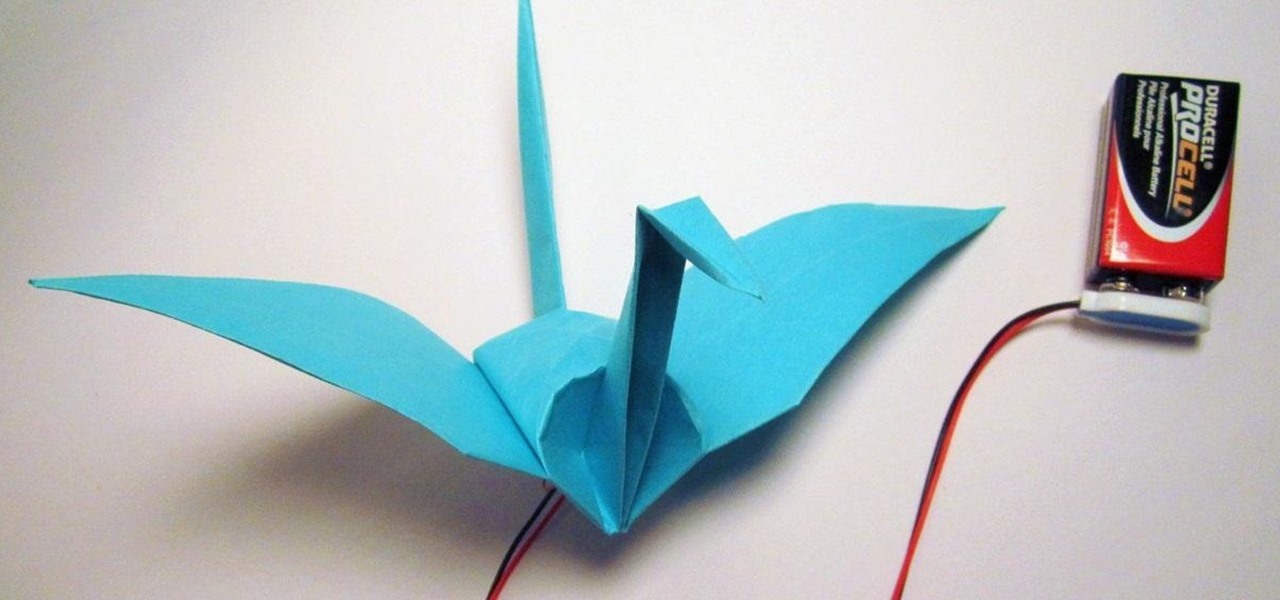
Want to spice up your origami cranes? MIT's High-Low Tech Group made two electronic origami cranes that flap their wings when you squeeze their tails.

The rapid advance of Lens Studio as a platform for easily developing augmented reality experiences is just one indicator that immersive computing is becoming the norm.
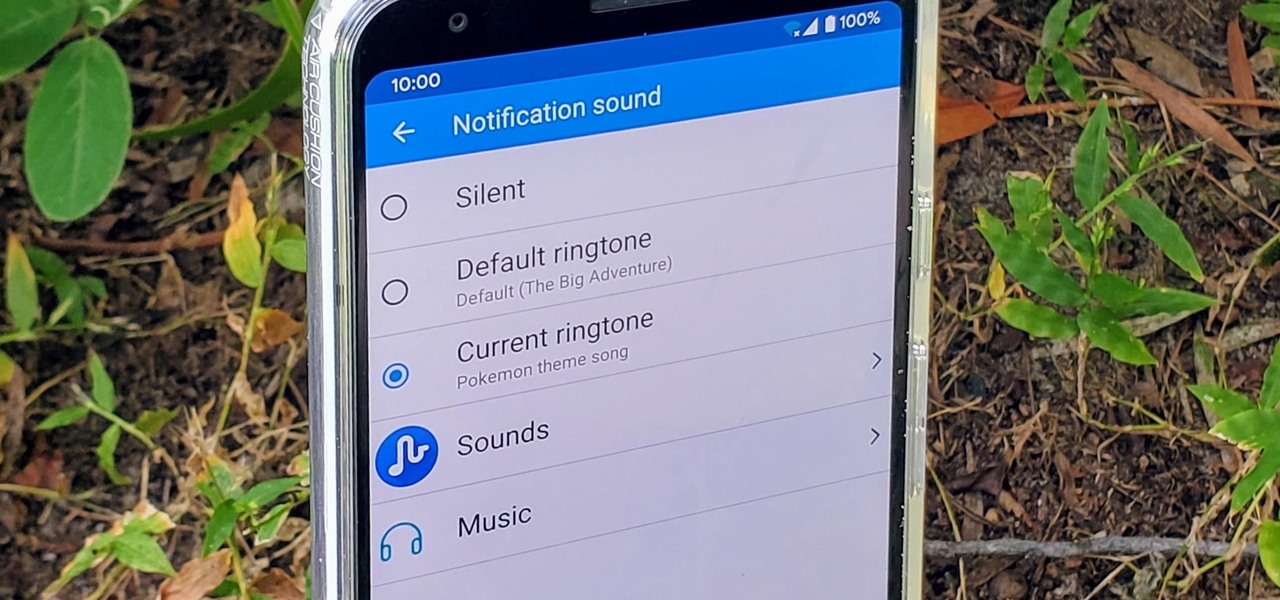
Have you ever walked around in public and heard the same handful of default ringtones over and over again? How do these people know who's calling without looking first? It's tough to tell when they all sound the same, but there is something crafty you can do to help with that. Using a different ringtone for certain contacts will allow you to differentiate between them instantly.

Augmented reality developers who have exhausted their treasure trove of video tutorials and panels from the recent Magic Leap developer conference can now shift their continuing education attention to Unity.

A fresh batch of developer info has been revealed on Magic Leap's Creator Portal. On Thursday evening, the normally secretive company gave the general public perhaps the closest look yet at Magic Leap One's Lumin operating system.

Google, Facebook, and Huawei have made an investment in nurturing the future of augmented and virtual reality through $6 million in contributions to the opening of a new center at the University of Washington.

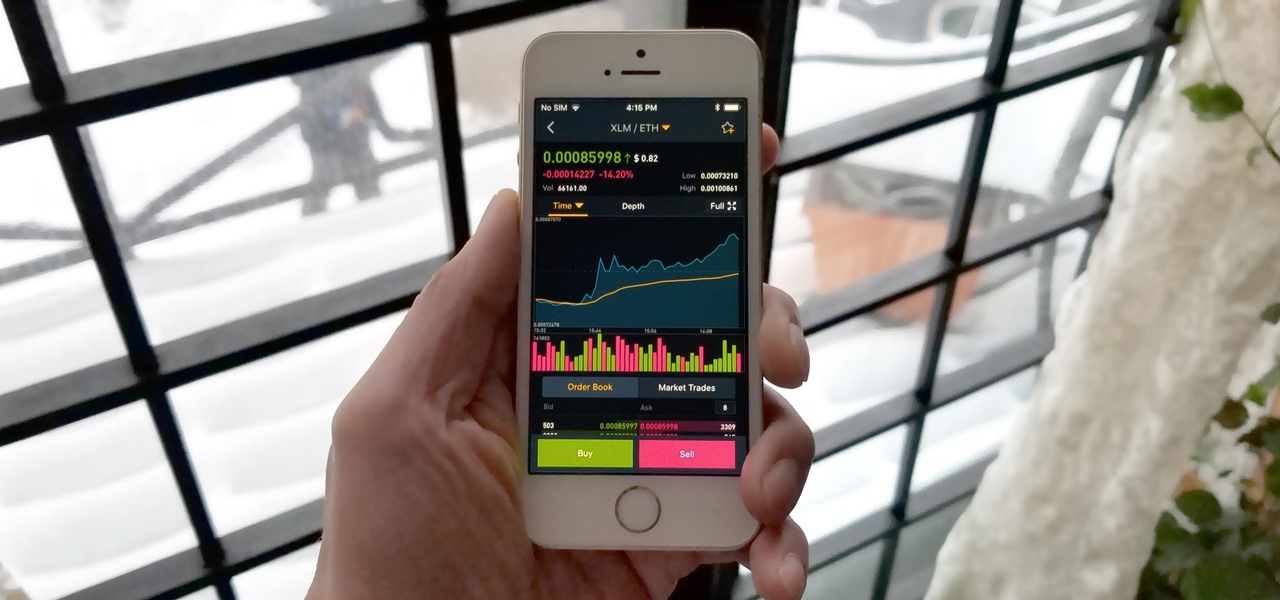
Binance, a China-based cryptocurrency exchange, is rapidly gaining popularity thanks to the sheer selection of digital currencies you can purchase — Ripple (XRP), Tron (TRX), IOTA, and Stellar (XLM), to name a few — using both Bitcoin (BTC) and Ethereum (ETH). Binance has an iOS app, and there are a couple ways to install it. Either way, you can trade cryptocurrency from your iPhone today.

With an eye toward future iPhone X-focused augmented reality functions, Apple's new investment in one of its components vendors will increase production capacity for the technology behind its TrueDepth camera, but could also apply to its future AR ambitions.

They say if you don't believe, you don't receive. Therefore, I'll choose to believe that this holiday season, Santa's elves have learned how to code in Unity and leverage ARKit to deliver these jolly AR apps for helping children of all ages virtually decorate their homes.

Eventually, we all get tired of our home screens. There's nothing wrong with it, but after hundreds of times seeing the same thing, it all starts looking a bit stale. You can rearrange icons and widgets, or even just pick a new wallpaper — but sometimes, your layout is perfect and you still want a fresh look. Well, thanks to Action Launcher and icon packs, this is really easy to accomplish.

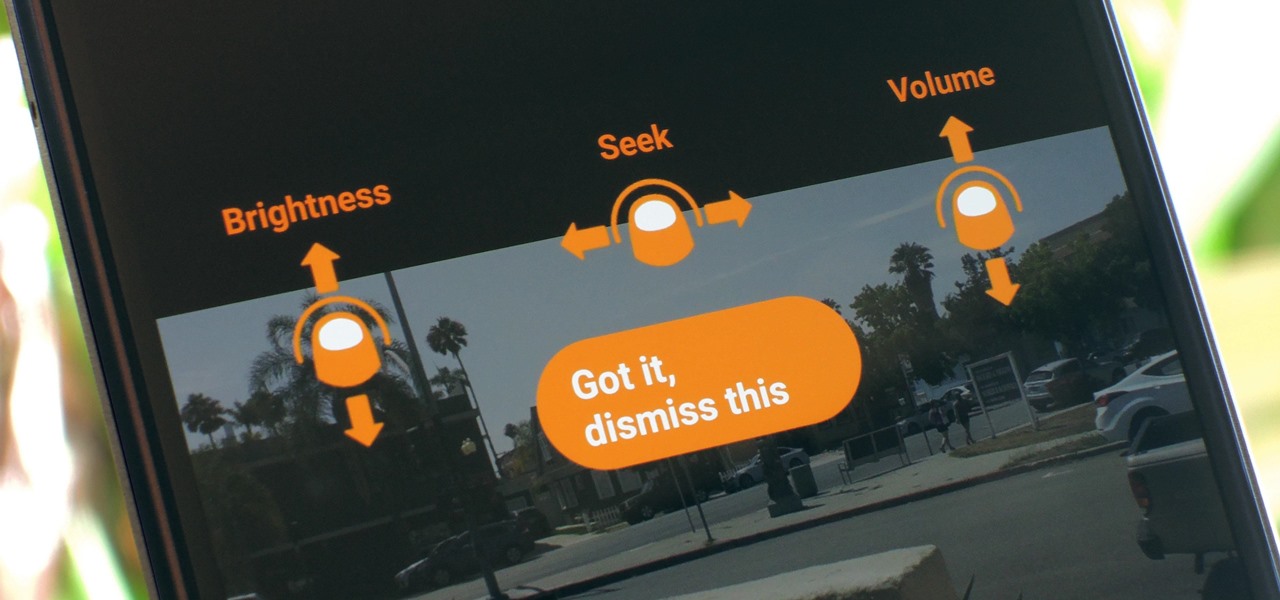
For a long time now, VLC has been the go-to media player for Windows and Mac — but it's fast becoming the best third-party video player on Android and iOS, too. Aside from its ability to play virtually any file type, one of VLC's best features on mobile is the fact that you can control playback using simple swipe gestures.

Even though your phone has a built-in media player, it's got nothing on VLC. The popular third-party video player supports virtually every codec and file format, and even better, you can use it to stream movies, shows, and other video files from your computer to your phone.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

Lightform might just be the thing to have at your next party. The San Francisco-based company just created the first computer ever able to connect to a projector and instantly scan 3D scenes to mix reality with projected light.

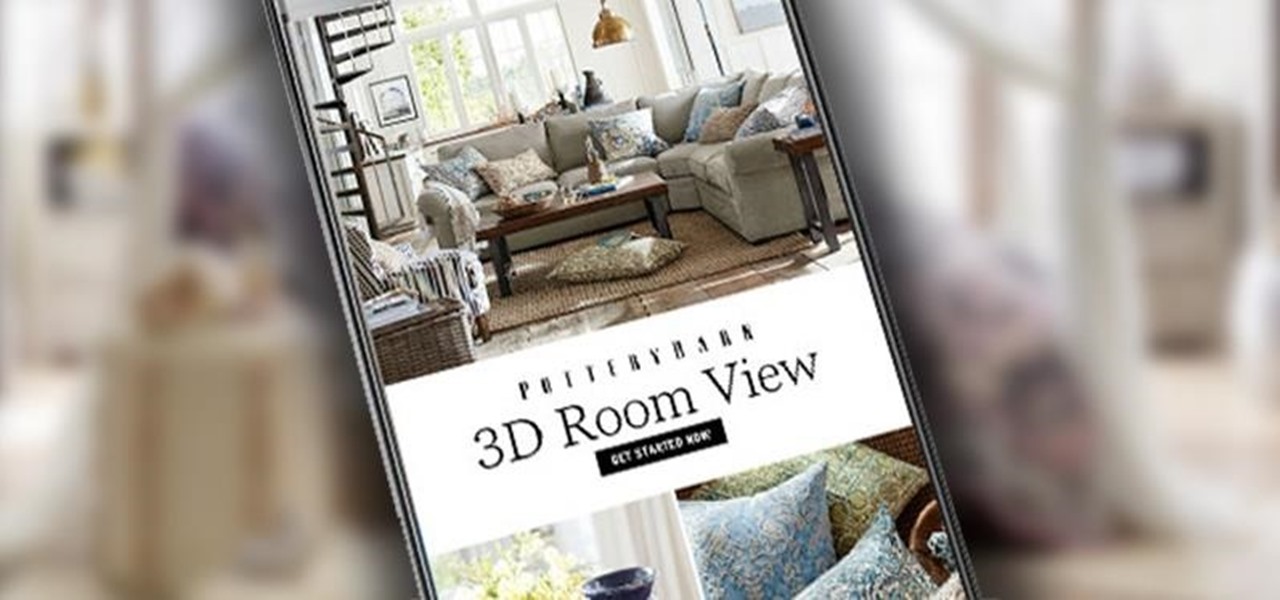
Pottery Barn has teamed up with Google to create 3D Room View, a new mobile app to allow all wannabe interior designers (like me) to pick out the perfect couch, table, or whatever, and then overlay it onto a spot in his or her house.

It's 2017 and finally ordering "fries with that" at McDonald's is an even easier prospect for all you lovers out there ball and chained to the fast food game. The great big golden arches are moving one step closer to making your order as golden as it ought to be through a mobile ordering app using geofencing technology to track your location.

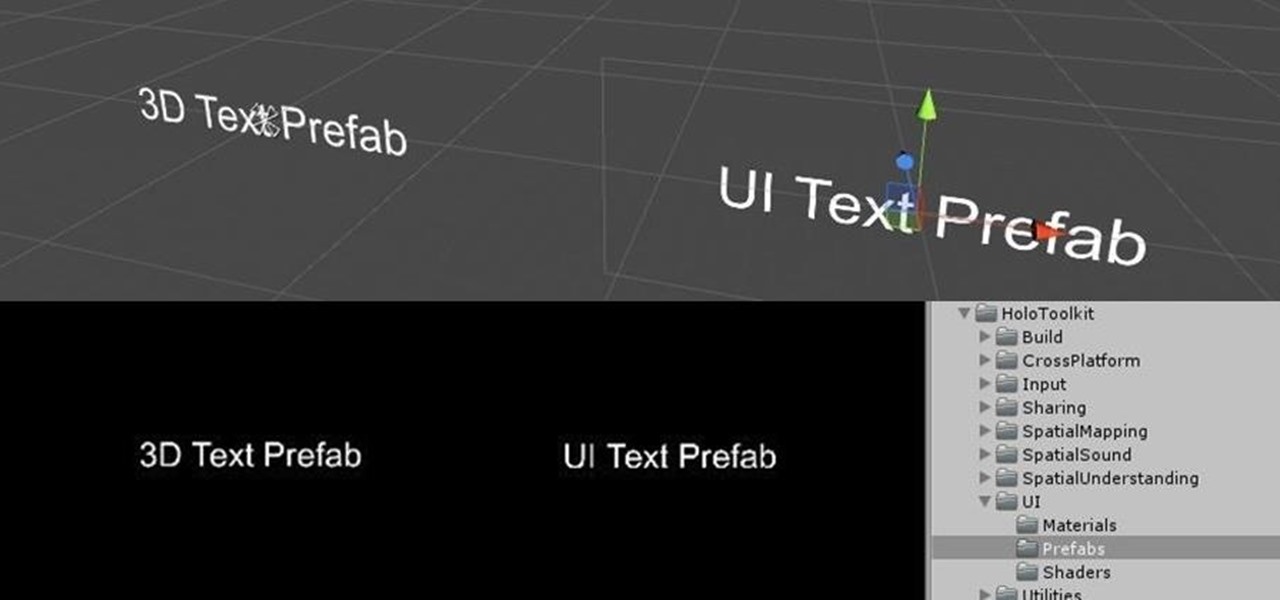
You may remember my post from a couple weeks ago here on NextReality about the magical scaling ratios for typography from Dong Yoon Park, a Principal UX Designer at Microsoft, as well as developer of the Typography Insight app for Hololens. Well, his ideas have been incorporated into the latest version of HoloToolkit, and I'm going to show you how they work.

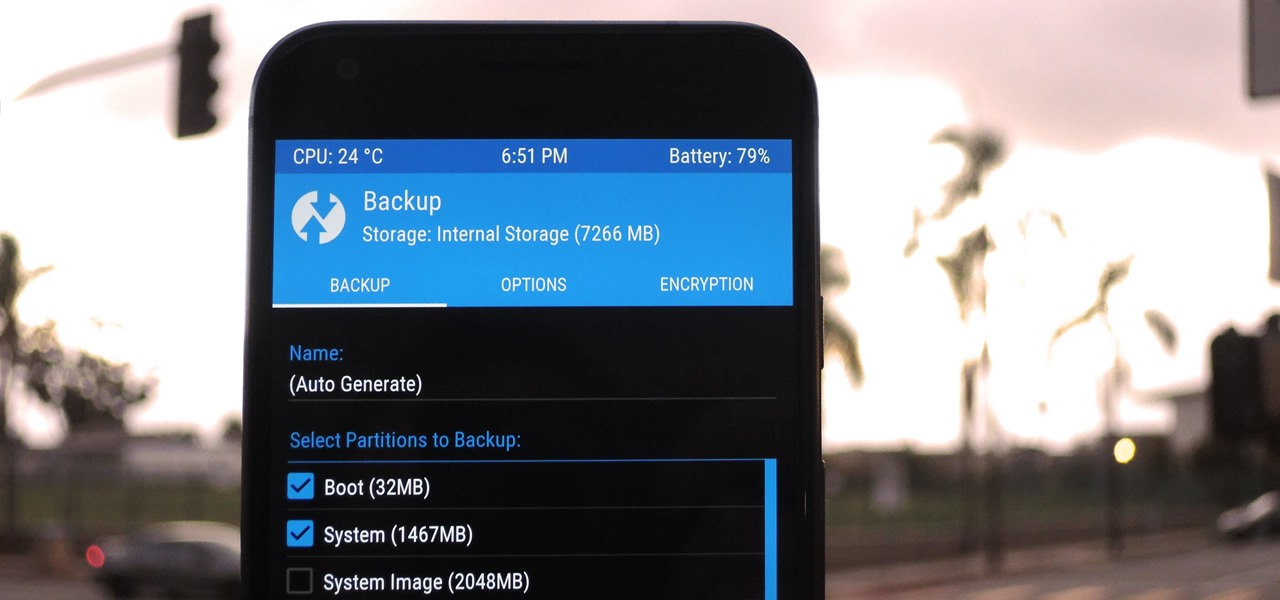
A custom recovery is a very powerful tool. You can flash ZIPs that modify your Android device in ways that not even root can accomplish, and of course you can use it to install custom ROMs. But when you're applying all of these cool mods, there's always a chance that something could go wrong, and you might even end up bricking your device.

Don't let the lack of owning a HoloLens stop you from joining in on the fun of creating software in this exciting new space. The HoloLens Emulator offers a solution for everyone that wants to explore Windows Holographic development.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

Android's personal assistant is more than just a sassy backtalker—it's a full-on suite of all the information you could need at a given time. Google Now, as it's called, uses data from various sources to predict what you'll want to know before you even search for it, and it's an amazing experience once you've got everything set up.

The first time a friend or family member asks if they can borrow your phone or tablet, you probably just hand it over without a second thought. But the second, third, and fourth times? Now it's starting to become a habit, and something probably needs to be done about it.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

In my last post I introduced how to use ncat to connect to your Pi remotely, but what's the point to if you can't actually hack? This tutorial I'm gonna show you how to use very simple tools for a much bigger purpose. With that said, boot up our Pi and lets wreck havoc.

Unless you're in law enforcement, you won't usually have a flashlight on hand for those rare moments when you need to sift through the dark. However, it is very likely that you will have your phone on you, so you'll have fast access to a bright light with just a few easy taps.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

Here at Food Hacks, we're very fond of finding ways to regrow food. That means taking things like carrot tops and leftover bits from garlic, onions, chives, and other herbs and aromatics to create mini reusable herb gardens.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"