Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

The point of ice in your cocktail is to make it cold, right? Yes and no.

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Welcome back, my greenhorn hackers! I've been writing these Linux tutorials in an attempt to fill the void in the education of some aspiring hackers into the Linux operating system. There is a lot to know, and in this tutorial, we'll look at Linux file permissions. Step 1: Checking Permissions

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

Glow sticks, a popular favor at parties and outdoor events, and a must-have on Halloween, can be traced back to the United States Navy in the mid-1960s. The military desired improved visibility during night operations, and glow sticks, with their small-size portability and lack of batteries, were a perfect tactical solution.

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

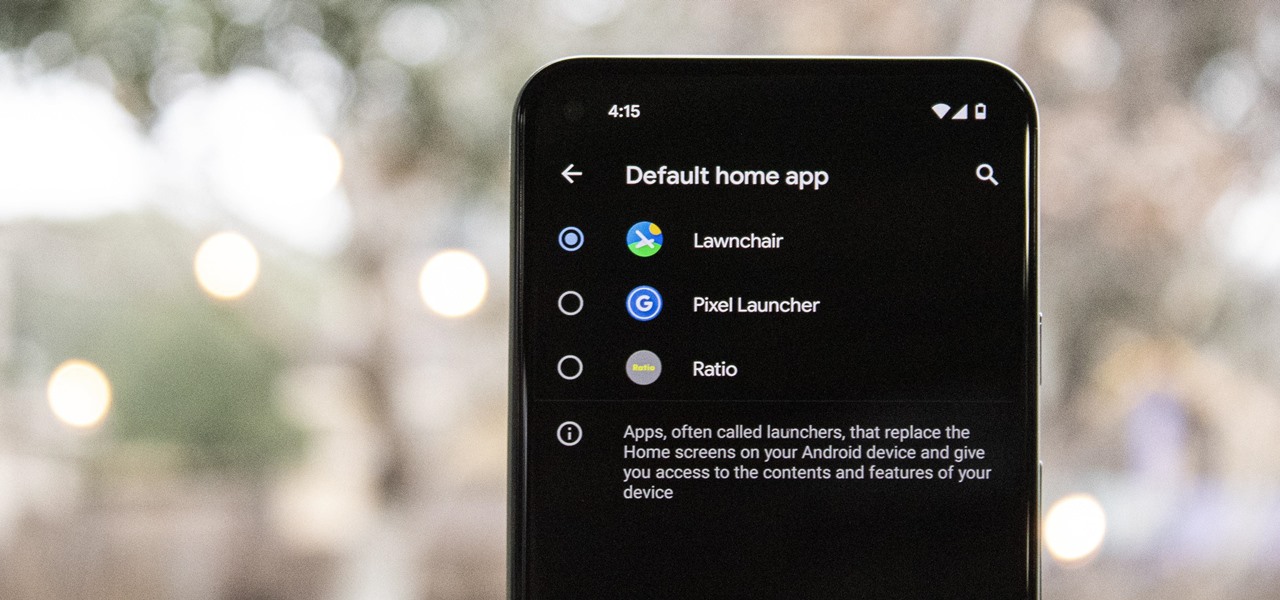
One of the easiest ways to change up your Android experience is by swapping out the stock launcher with a new one. The word "launcher" is Android lingo for "home screen app," and it's a common term because of how easy it is to switch to a new one. So if you're looking to revamp your home screen, this guide's for you.

We all want to be healthy, but in practice, it can be tricky, especially from the fitness angle. Our lives seem busier and busier, which makes hitting the gym quite the challenge. What if we told you there was a real way to work on your fitness in the comfort of your own home — in just seven minutes a day? All you need is a chair, a wall, and a 7-minute workout app.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

The LG V30 is an amazing device that will contend for best smartphone of 2017. It has all the major features you'd expect from a high-end flagship, and it even includes what's become a rare commodity these days — a headphone jack. However, for the purists out there, the LG UX skin strays too far away from stock Android. Have no fear, for with the LG V30, you can have your cake and eat it, too.

In the previous section of this series on dynamic user interfaces for HoloLens, we learned about delegates and events. At the same time we used those delegates and events to not only attach our menu system to the users gaze, but also to enable and disable the menu based on certain conditions. Now let's take that knowledge and build on it to make our menu system a bit more comfortable.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Since Android is an open source operating system, that means anyone with a little know-how can download, view, and even alter its underlying code base. Manufacturers do it all the time, which is how we end up with skins like TouchWiz and Sense. But when Android's awesome third-party development community gets their hands on this code, we end up with custom ROMs like LineageOS and MIUI.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

With T-Day on the horizon and approaching rapidly, you are probably in one of two camps. The one that is eagerly awaiting the holiday feast with barely-contained drool. Or the one that involves breathing heavily into a paper bag while worrying about your lack of oven and stovetop real estate, while also bemoaning the lack of multiples of you to get all the prep work done.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

With a November 2013 release, Disney's Frozen just missed Halloween. That means that everyone had to wait an entire year to dress up as their favorite princess or snowman — and that time has finally come.

I am an English major physically allergic to all algebraic formulas, so you're unlikely to get any help from me when it comes to solving any expressions. But in the glorious technological age we live in, there are plenty of apps that actually make math and problem solving fun, even a little bit addictive.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

The tech world was taken by surprise this week with the unexpected unveiling of Snap's augmented reality Spectacles smartglasses.

Compared to Apple's products like the iPhone and iPad, Android phones and tablets are very flexible devices. For instance, you can set a new home screen, replace the lock screen, or even beam files using NFC — but that's just the software side of things, and the flexibility goes well beyond that.