People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

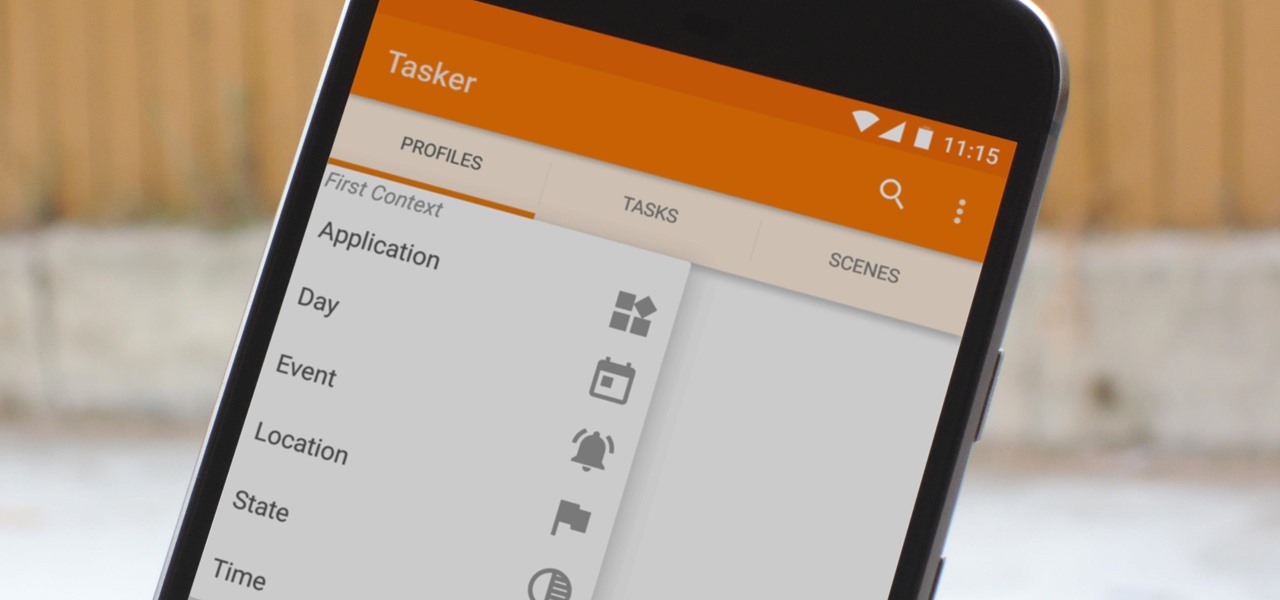
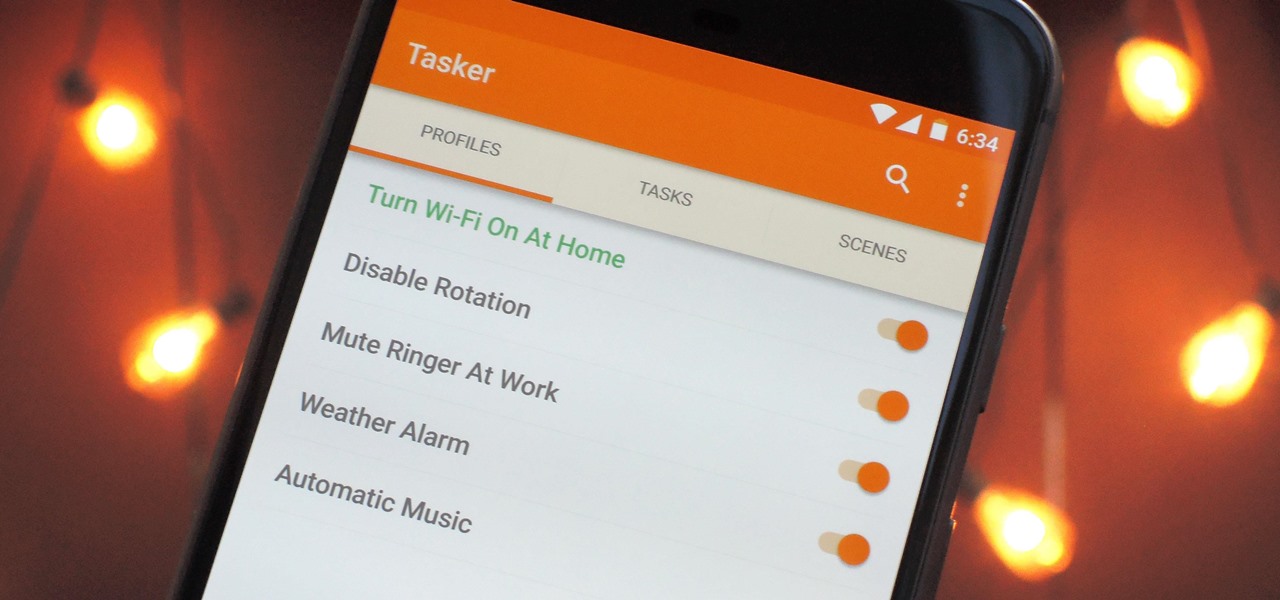
When you hear people say that Android is more flexible than iOS, it's because of things like Tasker. You can do virtually anything with the venerable automation tool, from saving battery life to controlling your smart home with your fingerprint. But before you get to that, you'll need a good understanding of all the basics.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

When it comes to automation apps on Android, Tasker is still the king of the hill. For a price of $2.99 on the Google Play Store, it's a great buy for any would-be tinkerer that would like to get into automating actions on their Android device. Then, when you consider that there's a free 7-day trial version available, there's almost no reason that you shouldn't at least test the waters with Tasker.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

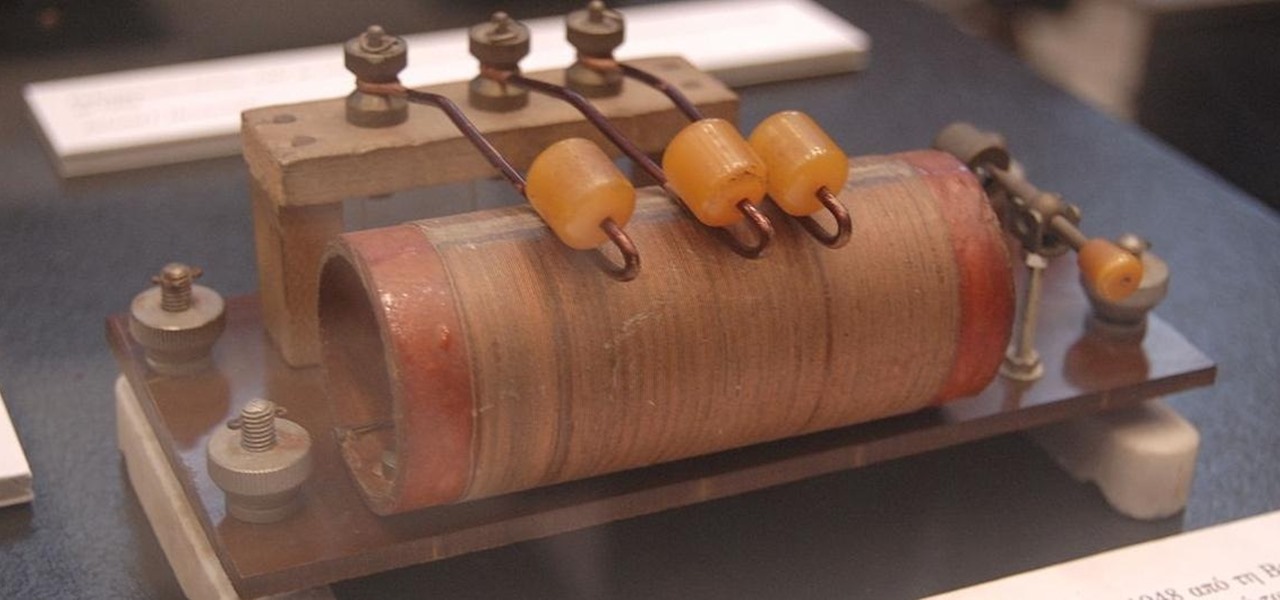
There's a lot that goes into making a nice crystal radio set, so this is going to have to be broken down into two parts. The first part is the actual making of a functional radio, and the second part is making the whole arrangement look nice. In this part, I'm actually going to tell you more than just how to make a crystal radio, but I'm also going to explain how and why they work. Crystal radios are pretty Steampunk in and of themselves, since they were first developed in the late 19th centu...

If you've been to a convention of any sort before, you know that there are good and bad panels, and that their inherent goodness or badness often has little to do with the actual content being discussed. That's because giving a panel is a skill that not everyone has. However, it is a skill that everyone could have! In this article, I'll tell you how to give a good panel on practically any subject. Image by Shannon Cottrell

After a few months and a couple of beta versions, Android 11 is now ready not only for Pixel devices, but also handsets from OnePlus, Xiaomi, Oppo, and Realme.

Python is commonly touted as one of the best programming languages for beginners to learn, and its straightforward syntax and functionality makes that hard to argue with. But a lot of tutorials still use Python 2, which is outdated now. Python 3 introduces many new features, and it's important to be aware of them going forward, as well as the key differences between Python 3 and its predecessor.

Apple previewed new cognitive, speech, and vision accessibility tools for the iPhone back in May, and they've finally been realized with the iOS 17 release. But there are more accessibility features than that hiding in Apple's latest software update — and they're not just for users with disabilities.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Many tutorials show you how to use Cheat Engine to execute one function of one particular game - but not this one! This tutorial gives you a good understanding of what Cheat Engine can do, and how you can use it to hack nearly any game!

This video will demonstrate all of the necessary steps needed to master 4 corners. Learn the right moves in these step-by-step tutorials that are designed to help anyone, both professional and amature, to pick it up fast and get right on the dance floor.

Ethan of Dead Fish Tutorials demonstrates how to make a sword from "Eragon." Eragon was given his sword Zar'roc by the wise Brom. All you need to have Zar'roc for yourself are some sticks you find in the woods, a bit of spraypaint and other cheap supplies, and a lot of geeky gumption.

First in a series of many tutorials on "retro" architectural drawing as it used to be done pre-computer. This sequence will teach you how you can draw basic shapes and other textures in order to draw an architectural structure.

Learn how to make your videos well under the 100mb limit using virtual dub and learn to break the video into pieces if the video is much too long. Learn from the master of humdrum tutorials!

This tutorials shows you tips and strategies for winning the flower cup on the Waluigi Pinball track on Mario Kart DS for the Nintendo DS.

Having trouble with your green screen? You may not have it lit right, or it may not be secured properly, or you might not be using your editing software right when using chroma key. If you want to learn a few tips on how to fix a bad green screen, this is the place. Watch this video tutorial to learn how to improve your green screen skills.

There may be a time when you want to run a program for 24 hours straight. If that app happens to quit unexpectedly, you have some options to get it going again without having to manually reopen it. Check out this video on how to restart a crashed program automatically on Windows. You need WatchDOG.

What? YouTube videos without Flash? No. It can't be. Well, it can be. There's a little program for Mozilla Firefox called YouTube without Flash Auto.

The Shim Sham Shimmy, Shim Sham or just Sham is a particular tap dance routine. This four part how to video teaches the four moves to the Shim Sham dance. Learn how to do the Shim Sham, the Push and Cross, the Tack Annie, and the Half Break with these tutorials. Follow the steps in this video and you will be dancing the Shim Sham in no time.

In this series of video tutorials you'll learn how to use Apple's iDVD software. Expert Matt Nichols shows you how to use all the basic features of iDVD, including how to create a new project, how to select a theme, how to add graphics, how to use the menu tab and much more. Watch these free video software tutorials and learn how to create your own DVDs today!

In this series of online video tutorials you'll learn how to use Reason 3.0 music recording software. Expert Jerus Arte demonstrates how to use the program, from installing it on your computer and setting it up with the right preferences, how to control the master volume, and how to use features like the NN-19, the NN-XT, the Dr, Rex loop player, and the Redrum machine. He shows you how to use effects like the compressor and reverb, and how to mix down your song into a format that can be burn...

The Thread Heads viewers come together to present a series of tutorials on DIY fashion. Learn how to sew and make other homemade clothing.