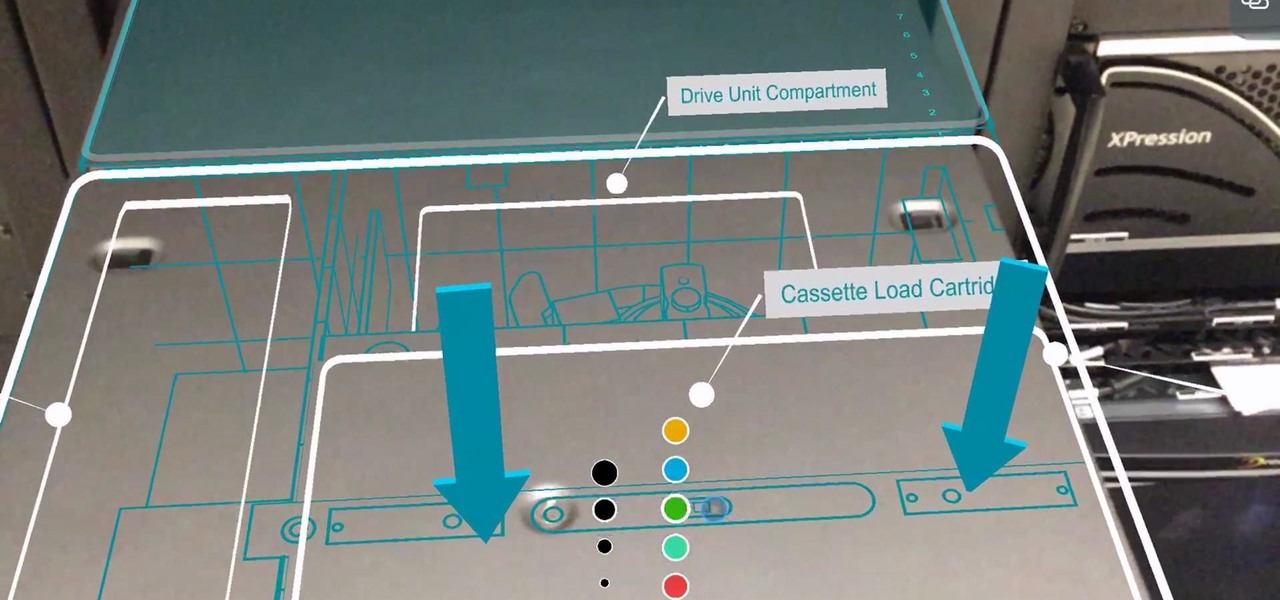
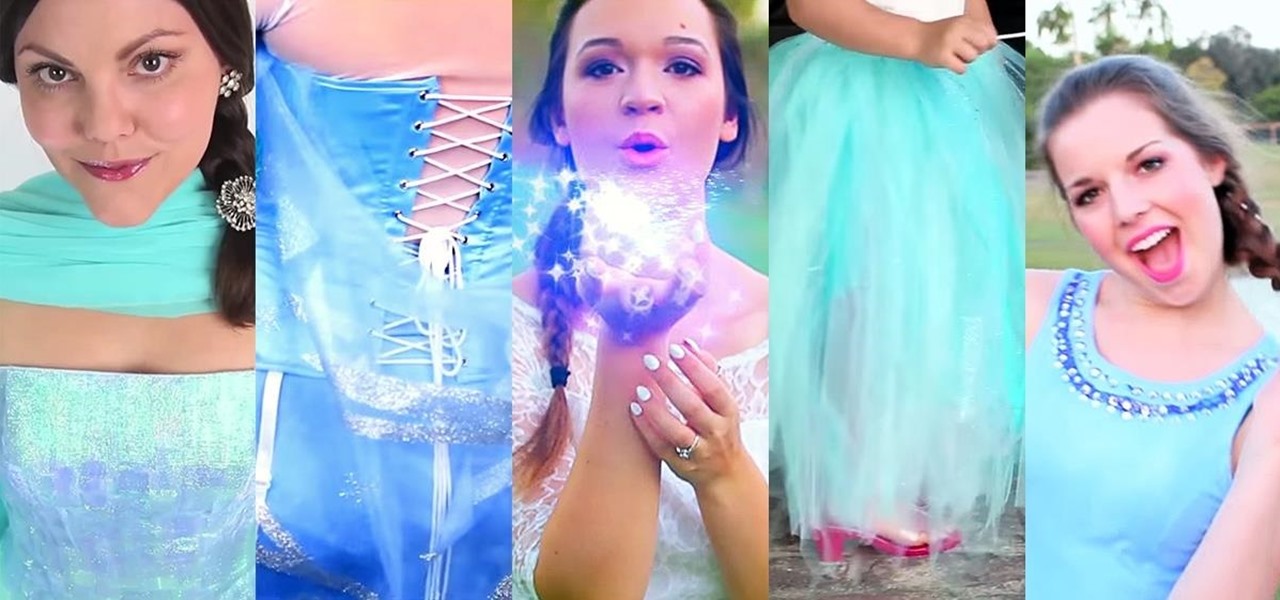The initiative known as Project Aria has been the focus of curiosity around Facebook's augmented reality plans ever since Mark Zuckerberg revealed the device around this time last year.

If preorder delays are any indication, the iPhone X certainly has some buzz. But does the X have the quality to support that buzz in the long run? After all, a $1,000 (or more) iPhone feels more like an investment than a smartphone purchase. The question on any prospective buyer's mind should be, "Is this thing worth it?"

This video shows how to make a small woven puffy heart. It Measures approximately 3 inches of yarn and 8 inches across. Use sufficient yarn and a size G crosha. Make a knot and attach the knot with the crosha. Make a chain of 3. Twin with the beginning chain to form a loop. Now make 9 rings with the center of the loop. This completes round 1. Now round 2 will have 18 rings around round 1. This completes round 2. Likewise work for two more rounds with 12 or 18 rings. Further round 4 will have ...

This is the end of the Xbox 360 game Darksiders. It's the last level, the last quest, your last mission… the Destroyer. You'll need to summon Ruin to stand a chance against the Destroyer. Hold the Focus button to target lock onto the creature so you can keep in in view as you move around. The idea is for you to ride in close enough to the dragon and slash it with your Armageddon Blade. Watch out when you see the Destroyer's front claws glow red as this means he's coming to slash at you. Eithe...

Ryan demonstrates how to make a twin hearts origami with a ten dollar bill. First, you fold a ten dollar bill into several rectangles. By the end, you will have a nice heart shaped ten dollar bill.
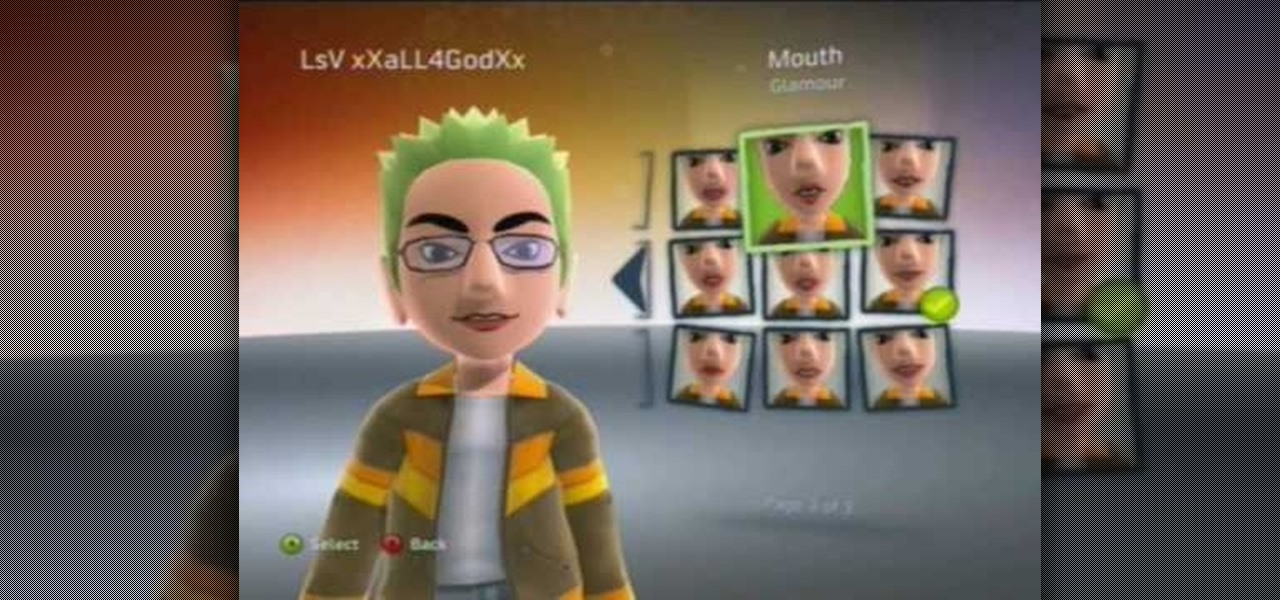
This how to video shows you how to make your avatar look like the Joker from Batman Arkham Asylum. First, go to the avatar edit menu. Hold the button down for 60 seconds until the box tilts. Now, search for spiky hair and choose a green color. Now, move on to the eyes. Choose evil eyes and select any eye color. For the eyebrows, choose a curved shape for an evil look and select a black color. For the ears, choose long ears. For the nose, select a wide or defined nose. For the mouth, select a ...

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

After dipping its toes into the AR cloud arena last year, Ubiquity6 is now jumping in with both feet this year.

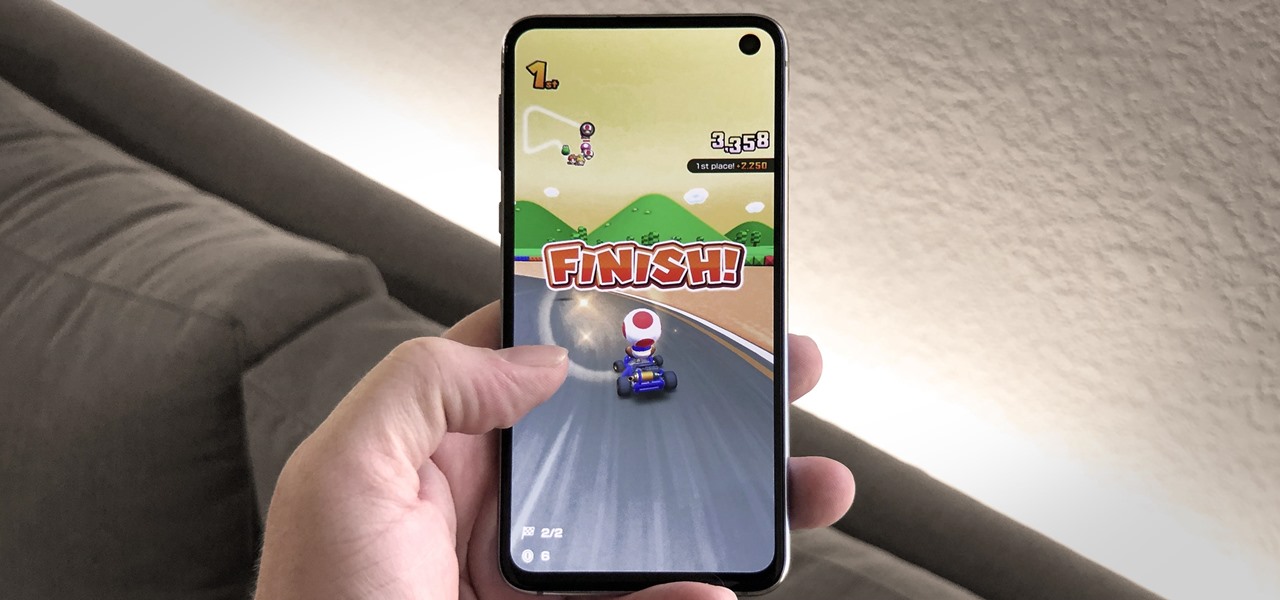
So you can't seem to win in Mario Kart Tour? Whether it's your first game in the Mario Kart series or not, Mario Kart Tour can be challenging, especially when you don't know the tracks. Instead of struggling your way through the cups, try out these five tips to get a leg up.

There have been a number of rumors about the iPhone 8 over the past couple of months, but the latest speculation about the device's dual FaceTime camera, that could take 3D selfies, has definitely grabbed our attention.

Tech companies are embroiled in controversy this week. No, not the hearings on Russian interference in last year's election; in this case, it's all about the burger emoji.

Lenovo unveiled the latest Motorola smartphones, Moto Z and Moto Z Force, today at Tech World '16. As expected, both models include strong magnets on the back that allow users to snap on various Moto Mods attachments such as a battery pack, projector, or JBL speakers.

The iOS 7 release brought with it many new aesthetic upgrades, from new flat, vibrant icons to a sleeker text messaging interface. Another small, yet noticeable, difference is the minimal and clean lock screen, which removed the overbearing "Slide to Unlock" background bar in lieu of just the text.

Imagine two stakes in your backyard. Now draw an east-west, north-south coordinate system on your lawn. Measure the east-west distance between the stakes and also the north-south distance. Take the square root of the sum of the squares of the two measurements and, voilà, you end up with the "distance" between the two stakes.

Want to learn a valuable skill? Well, just watch this video tutorial to see how to cross one eye or speak with an echo.

Remember the Wonder Twins from DC Comics? If you're familiar with the extraterrestrial superheroes, then you know all about those rings they wore. They would touch rings and says "Wonder Twin powers, activate!" to ready their superpowers.

There's 14 verses in this chapter in the Xbox 360 game Bayonetta. In Chapter 5 - The Lost Holy Grounds, combat Grace and Glory, Durga, and Alfheim. Near where you start you'll find the book "Crescent and Sunrise Valleys." Walk along the path and it will crumble as you go.

Need to get your books digitalized? Well, BookDrive DIY is the solution to scanning them for the web. This video will show you how to use it to get your books in your computer.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

Sure, they have personal trainers and chefs to help them shed their postpartum pounds. But here are a few of their other secret weapons.

As if the swollen, painful joints of rheumatoid arthritis weren't enough, the disease is the result of our immune system turning against cells of our own body. Ever since this realization, scientists have worked to find the trigger that sets the immune system off. Scientists believe that gut bacteria may have a role in initiating the abnormal immune response. Now, a team of researchers from Boston has figured out how that might occur.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

I can imagine you sitting there thinking to yourself, "I've played a lot of games! I bet he won't have any that I don't know about!" Well, that's entirely possible. I'm only drawing from my own personal experience here, so you may, in fact, know of all these games.

Legendary drum-and-bass artist Squarepusher, the Warp records labelmate of fellow electronic music legend Aphex Twin, is back with his fifteenth album called Be Up a Hello, which is set to drop on Feb. 1.

What if you went to an art installation at one of the coolest venues in New York that you could then take with you anywhere in the world?

After testing the waters with a few pop-up stores along the West Coast earlier this year, North is bringing its smartglasses to more cities across the US and Canada.

Over the past year, two trends have emerged among augmented reality development software: make it easier to create AR content, and give AR apps better environmental understanding with just a smartphone camera.

Enterprise augmented reality software maker Scope AR is bringing the powers of its two productivity apps together like the Wonder Twins into the form of a single app.

The Google Chrome browser for Android is packed with many great features, but it definitely has a bad rep for being slow and laggy on low-end or midrange devices. Without a top-notch processor, you'll likely notice some stutter with choppy scrolling, and pages can take too long to load in general.

Verizon Wireless executives recently cooked up a plan so devious that it could have only come from one of the four major US carriers. Apparently, they aren't satisfied with simply loading every Android device they sell with their own bloatware, so now they're reaching out to big brands to see who would be the highest bidder for a spot on your home screen.

When I was young, I wanted nothing more but to be able to freeze things just like one of my favorite X-Men characters, Iceman. Now, Disney's most successful animated film to date, Frozen, brought another icy childhood favorite to the scene—The Snow Queen. And with Halloween right around the corner, all of the princesses out there can get their chance at being ice royalty. While Princess Anna and Olaf the Snowman were the biggest characters in Frozen, Elsa is one of the movie's most memorable ...

One of the best-selling video game consoles of all time is the Nintendo Entertainment System, better known by its acronym, NES. However, cartridge-based gaming consoles are a pain now when compared to the newer download-and-play alternatives.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Imagine… being able to watch television on your PC. And imagine being able to stop, pause and record those television shows. Well, in Windows 7 it's totally possible. This video shows you the possibilities of Windows Media Center.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

While Apple's tech used for Face ID on the iPhone is impressive, it's debatable whether it's more convenient than Touch ID. There are also concerns that your face could be used to track shopping patterns or be seen during mass surveillance by intelligence agencies. More importantly, it could be easier for law enforcement, and even thieves, to force you to unlock your iPhone.

Some of the products I have been looking forward to seeing the most during CES 2017 has been the upcoming Windows Holographic virtual reality headsets. These are VR headset that will run a version of the Windows Holographic platform, which will allow users to have a similar experience as the HoloLens with a mixed reality environment. Of the six headsets that could have possibly made it to CES, five had shown up. Unfortunately, most of them are behind glass.