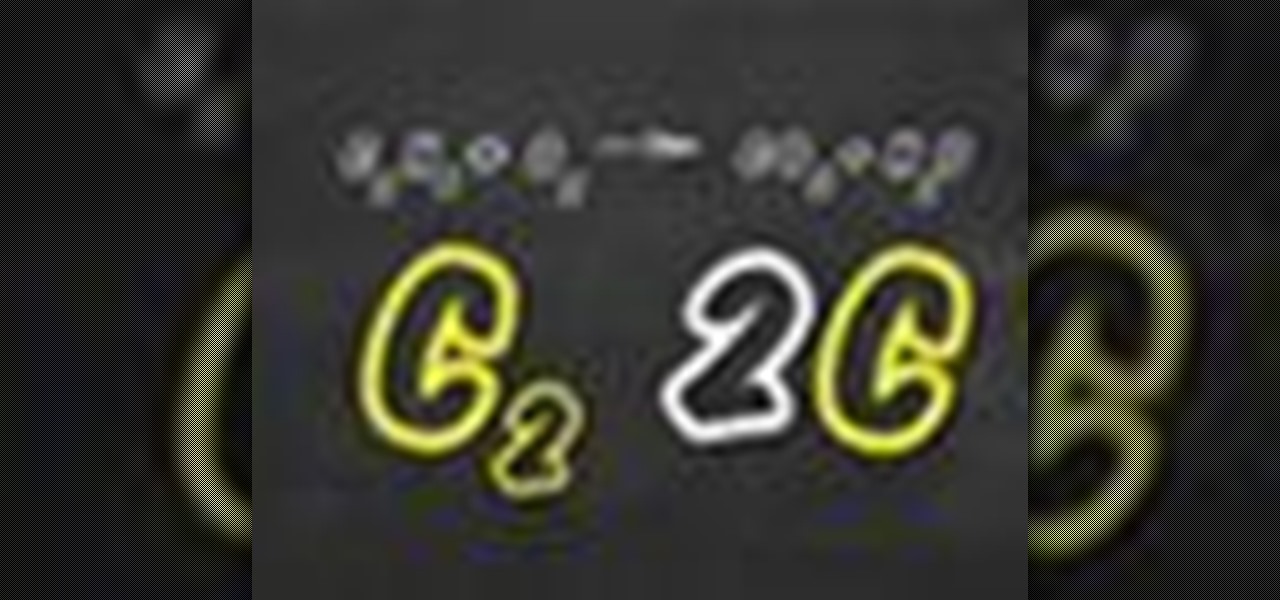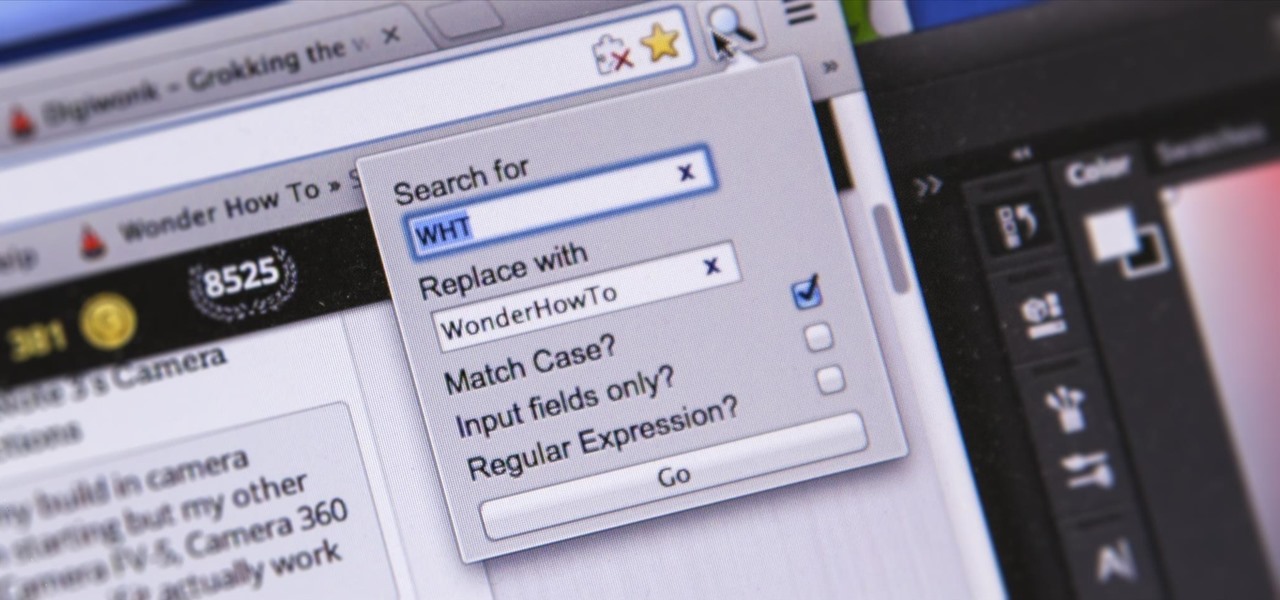
I'm sure you've been there—halfway through typing something out, you realize that one word you've been using more than any other has been misspelled. Perhaps it's a single word, acronym, or line of code that you find yourself typing quite often at work, but this one requires complicated hand gymnastics that you'd simply rather not perform over and over again.

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.
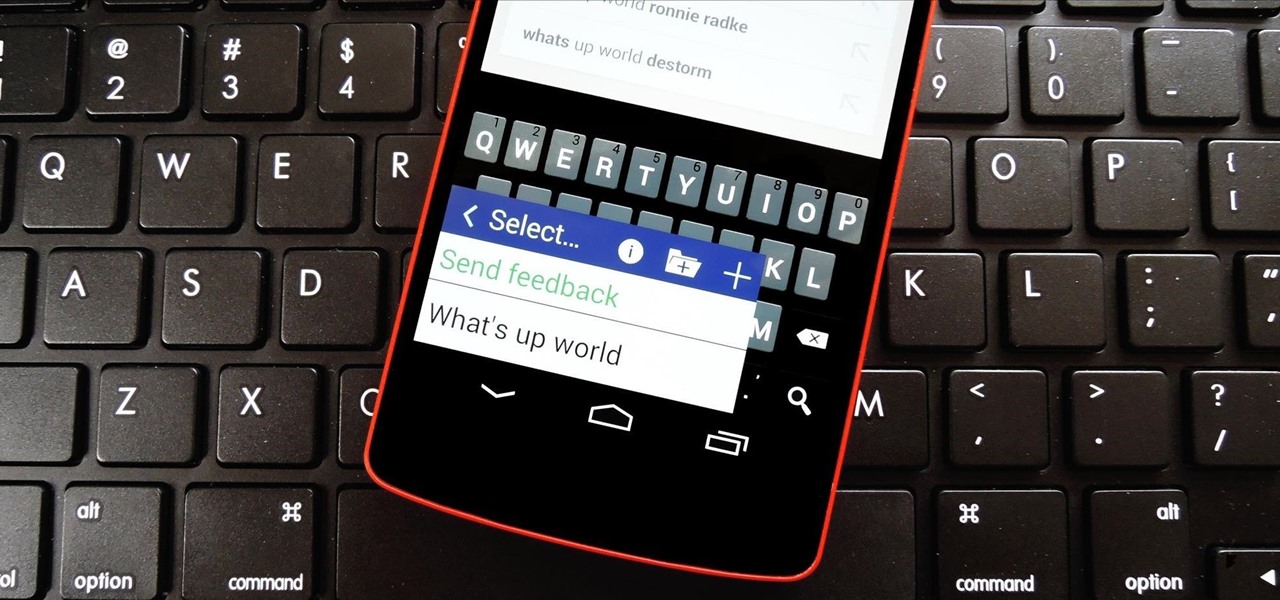
There are a lot of instances where we find ourselves typing virtually the same phrase that we've typed many times before. Whether it's the standard spousal reply of "I'll be home in a few", or a work-related phrase like "I'll have that to you by the end of the day", typing phrases like these can feel very redundant at times.

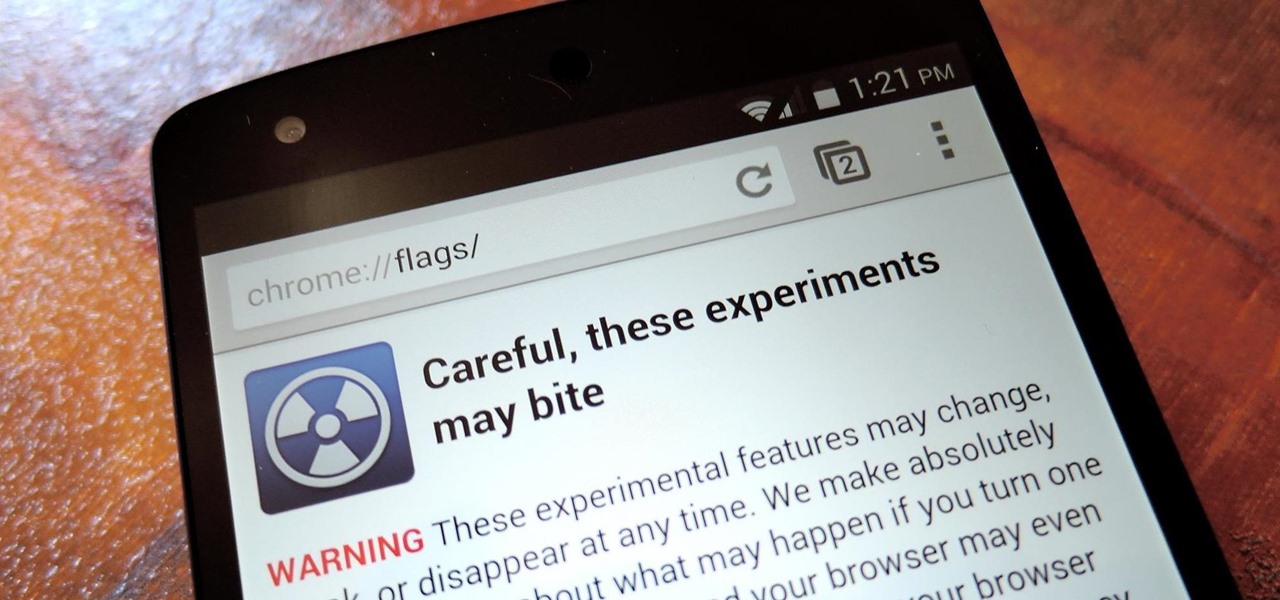
With the release of Jelly Bean, Chrome became the default web browser on Android. The wildly successful desktop browser was now fully entrenched in the world's largest mobile operating system.

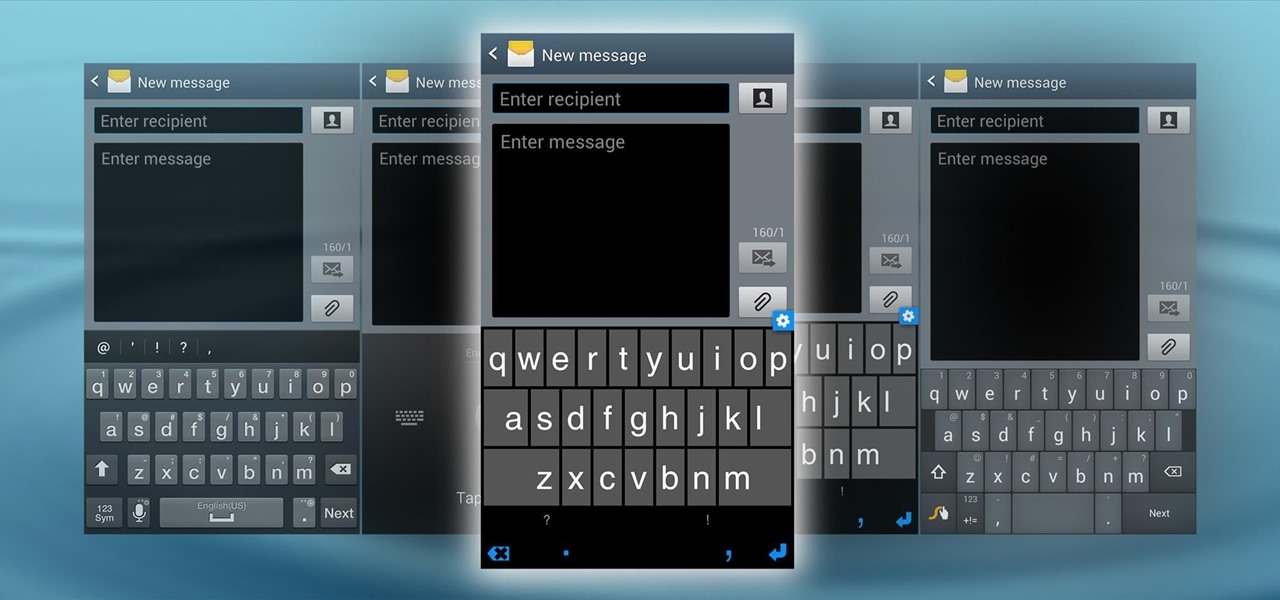
The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

The absence of a physical keyboard is both a gift and a curse. When it was announced in 2007 that the first iPhone would have a touchscreen only, people literally lost their shit. Now, almost 7 years later, you'd be hard-pressed to find a smartphone that still has a physical keyboard.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.

Who doesn't hate Auto Correct? There's nothing worse than hitting 'Send' only to realize that your phone betrayed you by changing a word so that your message doesn't even mean the same thing anymore—especially when it's going to someone like your boss or parents.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

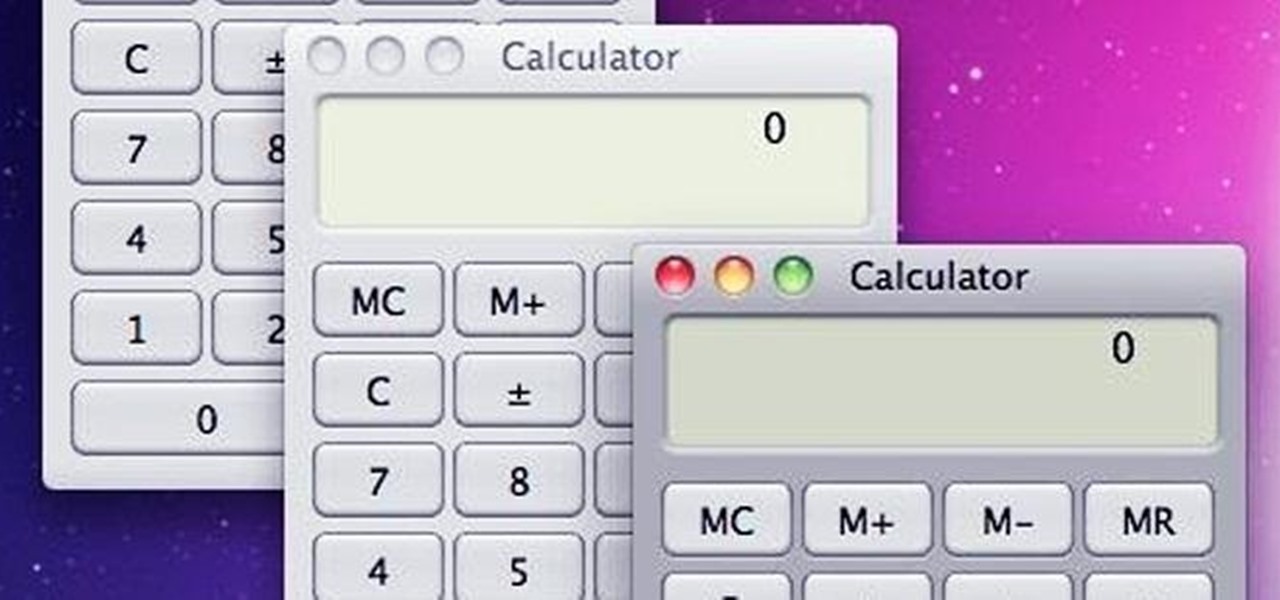
With the use of Terminal, anyone can run multiple instances of the same application on a Mac. When you have multiple windows open in a web browser, the windows are all running under the same Process ID (PID). But, with multiple instances, each has its own unique PID. So why would you want to run multiple instances of the same app? There are several reasons a person may run clones of the same application, but the most popular would be so that the user could multitask. Some applications, like t...

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

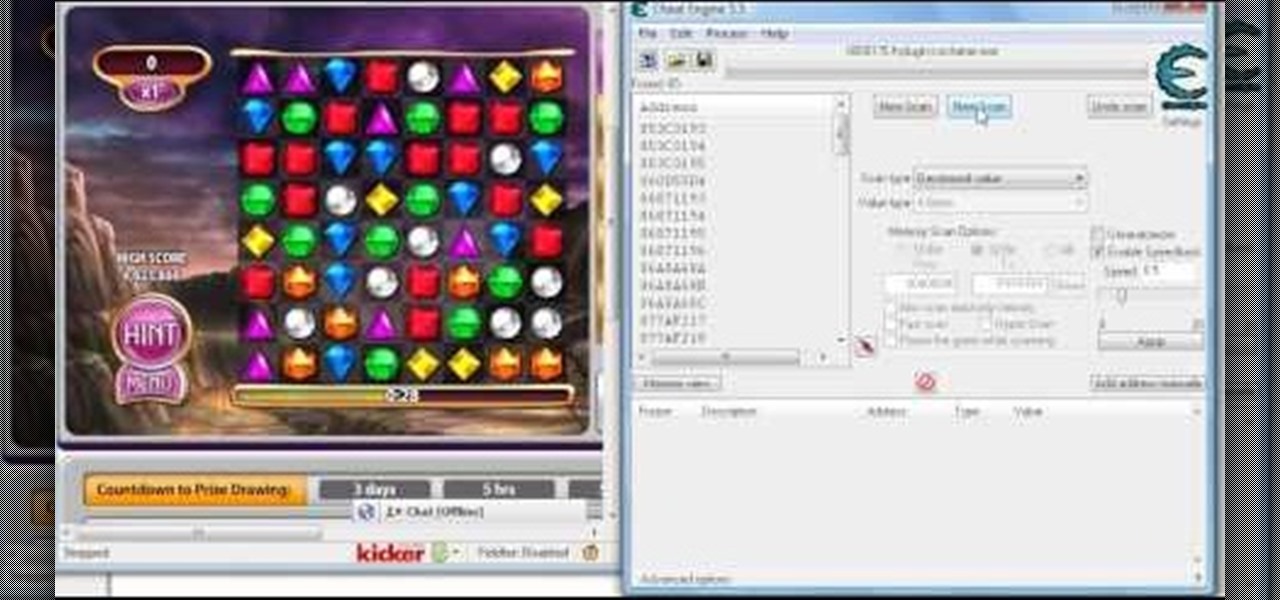
Don't let Bejeweled Blitz get the best of you. Show it who's boss and get the highest score possible. Of course, you'll need Cheat Engine to overpower the game, so make sure you have Cheat Engine 5.5 or higher and check out this video for the hacking Bejeweled Blitz (10/09/10).

This video will show you how to use the ‘find’ and ‘replace’ text buttons in Microsoft Word 2007. Microsoft Word 7 is slightly different from the Microsoft you might be used to but with these instruction you’ll have no problem finding the buttons.

This video will go over how to insert a check box in Microsoft Word for printing or for electronic distribution. With just a few clicks you can get a check box. You can even add different symbols or styles for your check box.

It's like magic. Creating a .LOG file has never been easier. And all you need is Notepad on your Windows PC. After creating this LOG file, Notepad automatically inserts the current date and time after the last line. Check it out. If you've ever wondered about LOG file types, this Notepad trick is must.

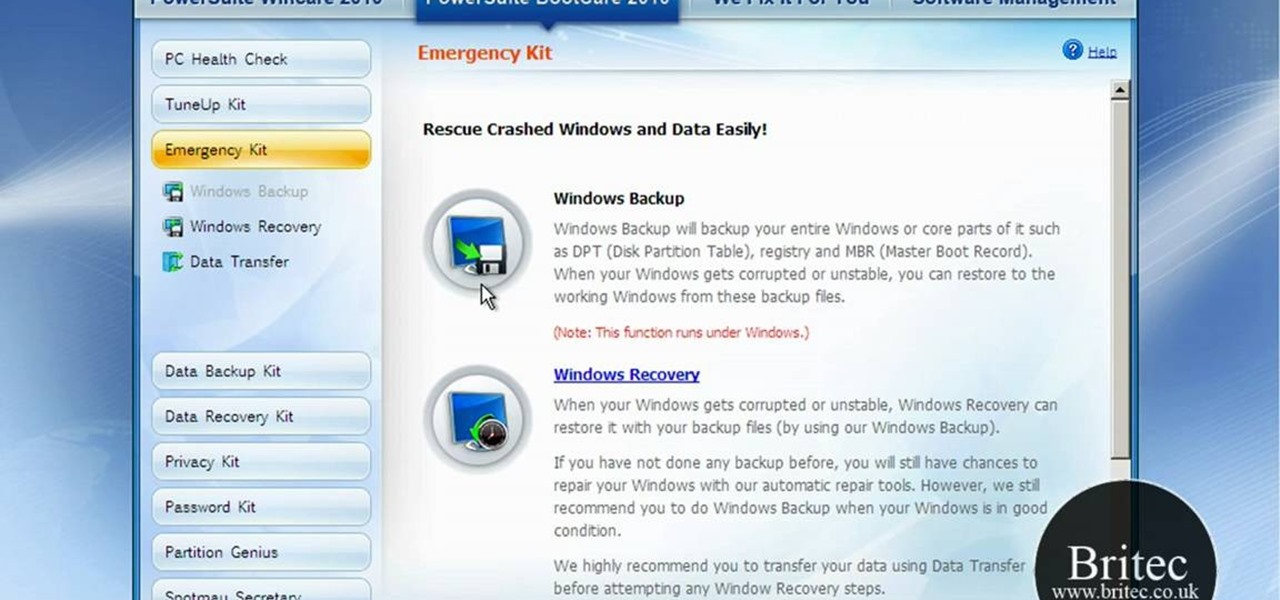
Have you ever gotten the error message, "BOOTMGR is missing" on your PC? Well, if you have check out this video. In this tutorial, learn how to remedy and fix this problem in no time.

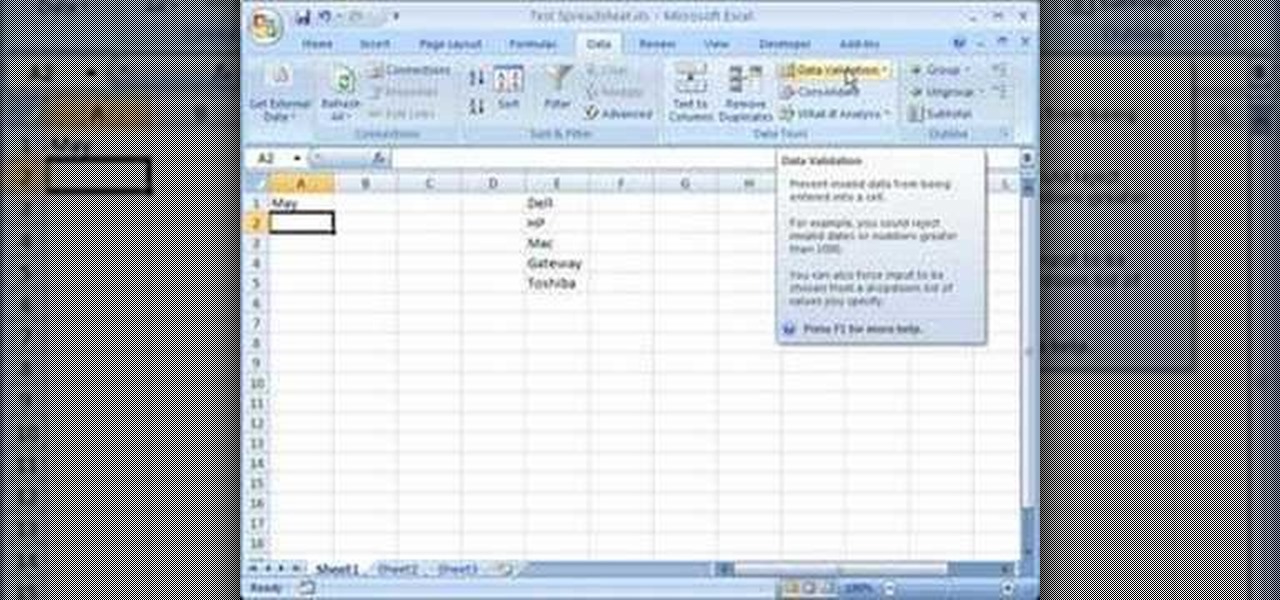
This video is a tutorial on how to create drop-down menus in Excel 2007. Select a cell on your spreadsheet and click on the “Data” tab. Go to the “Data Tools” section and select “Data Validation”. In the window that opens select "Allow" and choose "List". You will create a list of the values you want to allow. Type in the values, separated by commas, and click OK. Now you will see your selected cell has an icon to right that indicates there is a drop-down menu containing the value...

In this Software video tutorial you will learn how to make your own Adobe CS4 logo in Photoshop. Open Photoshop and click ctrl+O to open a new document. Set the height and width to 500 pixels, select ‘transparent’ under background contents and click OK. Create a new layer and with the rectangle tool draw a rectangle. Right click on the shape layer > rasterize layer. Hold ctrl and click on the thumbnail of shape1 layer. Open gradient tool and make a light to dark gradient as shown in the v...

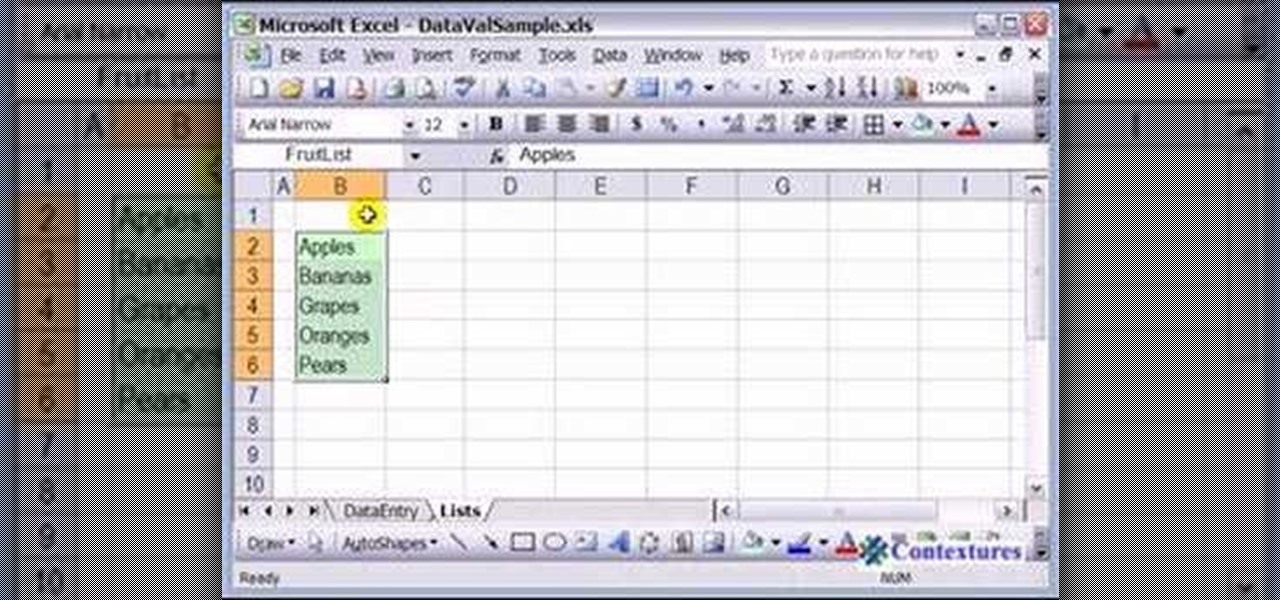
This how to video shows you how to use drop down lists in Microsoft Excel. This will be useful for stores and avoiding people ordering items that are not available. First, type the items in a column. Select them and then click in the name box. Type the name of the list. Note that it must be one word. Now, go back to the order sheet. Select the cell where you want the list to be placed. Go to data and select validation. On the settings tab, choose list and type in = and list name. You can pres...

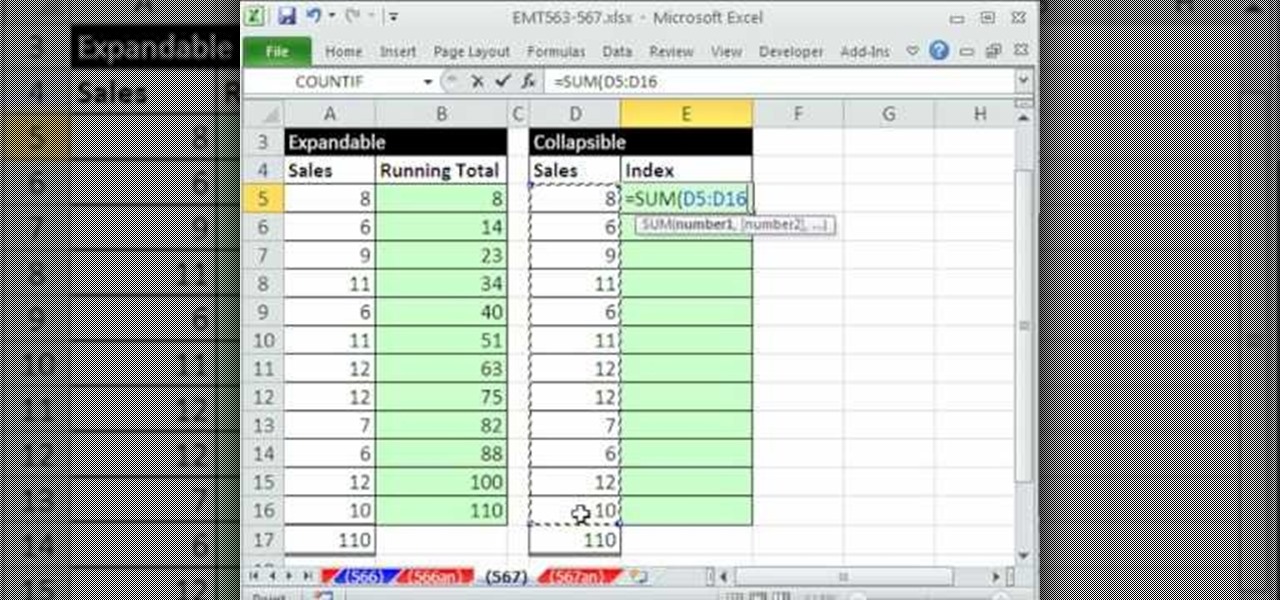
This video demonstrates how to create collapsible and expandable cell ranges in Excel. The first thing that you will have to is to prepare your Excel worksheet that contains the data which you need to be expandable and collapsible. On the first cell under your Running Total column, type in the function, "=SUM". Select the Sales cell corresponding to that cell then type in Shift+Colon. Click on the first value and hit the F4 key to lock your row reference. The result will automatically show. Y...

Steps to Configure Your Modem/Router are: 1. Open Network connection and click properties

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

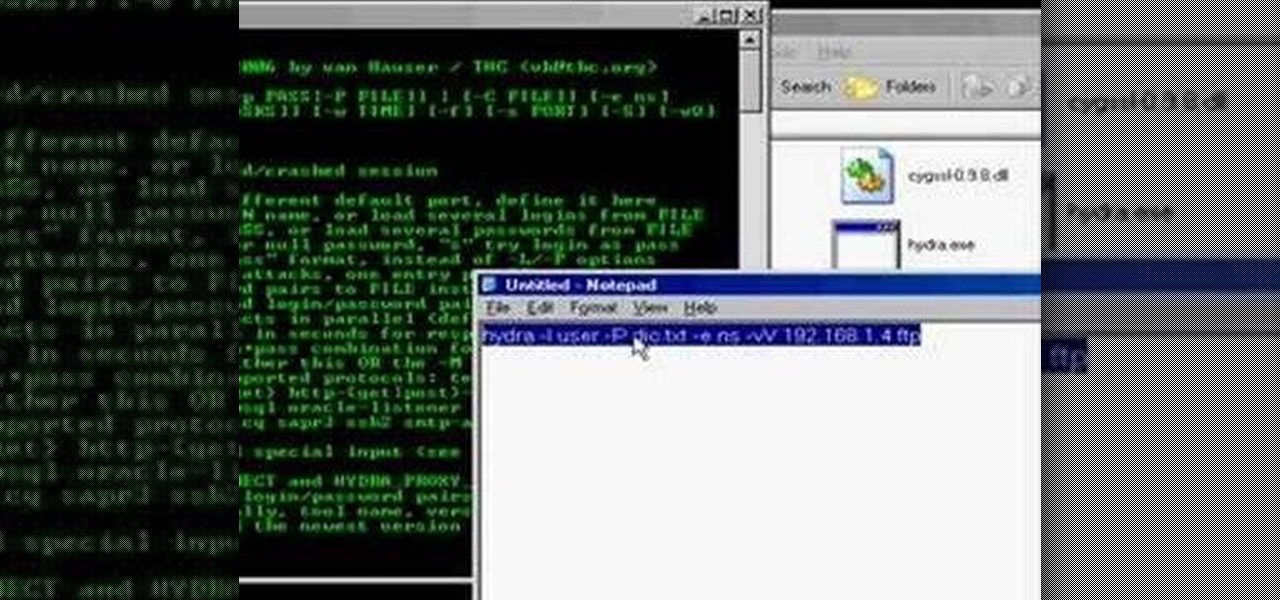
This is a how-to –video on using hydra 5.4 to crack FTP passwords. This video is intended for educational purpose only. It reveals the basics of hacking a FTP server using dictionary search technique. Here are the steps involved.

Open up dreamveiwer and click HTML on creat new. If the new page opens then go to design view and then go to insert and then layout object and then diff tag in that then click ok for that. There we have to create a scrollbar content. Then we have to right click there and go to css styles and then go to new. There go for selector type and click class and then name it as you want. Here he just named it as scrolldivstyle then go to go define in and take this document only and then click. Next yo...

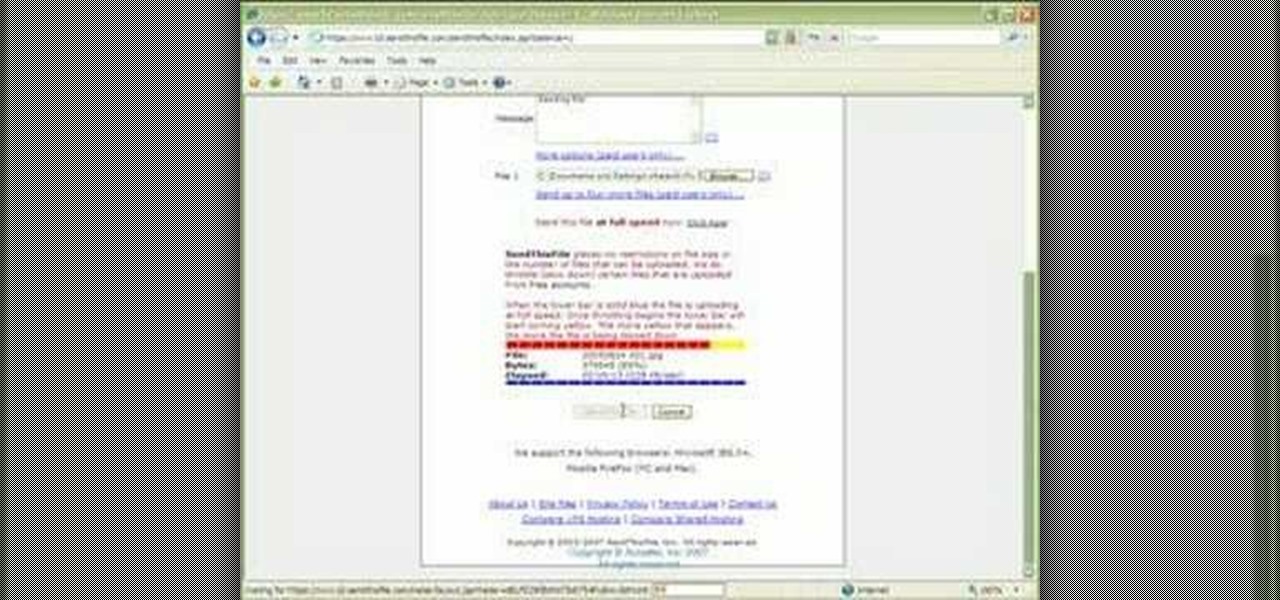
1. Type in WWW.sendthisfile.com in the web toolbar and press enter 2. Click on Register found on the top right side

In this how to video, you will learn how to speed up your Azureus Vuze program. First, open up Azureus Vuze. Next, go to advanced, option, and click preferences. Select preferences and change the port to a number between 49152 to 65535. Once it is changed, go to transfer and make sure that these are set to zero. Once that is done, open your web browser and type in your default gateway. To find this out, go to system preferences, network, and router. Next, enter your user name and password to ...

First of all you have to open the 'notepad'. Now you have to type in "<html>" in first line. Write "<head> in second line. Write "<title>this website contains text wrapped around images</title>". In the fourth line you have to type '<body bgcolor="#999999">'. This shall add a light orange color. Now find out the name of the image. Here the name of the file is 'image.png'. Then in the next line you have to type in "<img src="image.png">this text should hopefully wrap around the outside of the ...

HighQuality Tutorials demonstrates how to change your iPod Touch alpine default password. Changing the default password is useful when using your iPod Touch in a public setting to make it less vulnerable to hacking. To change the default password, first open up your internet connection and search for Putty. Download the Putty program. Open and run the Putty program. Your host name will be your IP address for your iPod Touch. Select port 22 and SSH and open up the program. Log in as root and c...

Shaun will teach us how to create a 3D video game compatible with MAC or PC with no prior programming knowledge. First download Alice, a 3D World program that can be turned into a video game. Open Alice, click on "add objects", click on "more controls" and select your choice of aspect ratio such wide screen. Now you can import your own 3D models that Shaun will show you at the end of the tutorial or choose from a wide selection that comes with Alice. In addition, if you click on "home," "web ...

This video shows how to change the advanced settings to make Firefox faster on Mac and PC.

If you've received the "hal.dll is missing or corrupt" error message from your Windows machine, then you're in luck! This video will show you how to correct that problem with the Recovery Console tool that comes with the Windows 2000 and XP CDs.

Not sure how to balance a chemical equation? According to the rules of chemistry, matter must be conserved in chemical reactions. When you balance a chemical equation, you account for all of the matter in the reaction.

There has been an update with the NES emulator, so you have to put the ROMs in the /var/mobile/Media/ROMs/NES folder, and not the /var/root/Media/ROMs/NES folder.

Hello everyone, In this video I will be going over what in my opinion are the top 10 bukkit plugins to make a great minecraft server. First thing I would like to state is that Essentials or commandbook was not featured in the video because I didn't want to feature something that big (or essential). I would also like to say it really does matter what kind of server you are going to be running becuase different types of server need different types of plugins.