Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

Designing for mixed reality, especially for the HoloLens, can present unique challenges. Dong Yoon Park, a Principal UX Designer at Microsoft with a passion for typography, recently gave a talk to the Windows Holographic Users Group Redmond (WinHUGR) about the pitfalls he ran into trying to convert what started out as a 2D iOS app 5 years ago to the newer 3D Holographic frontier with Unity.
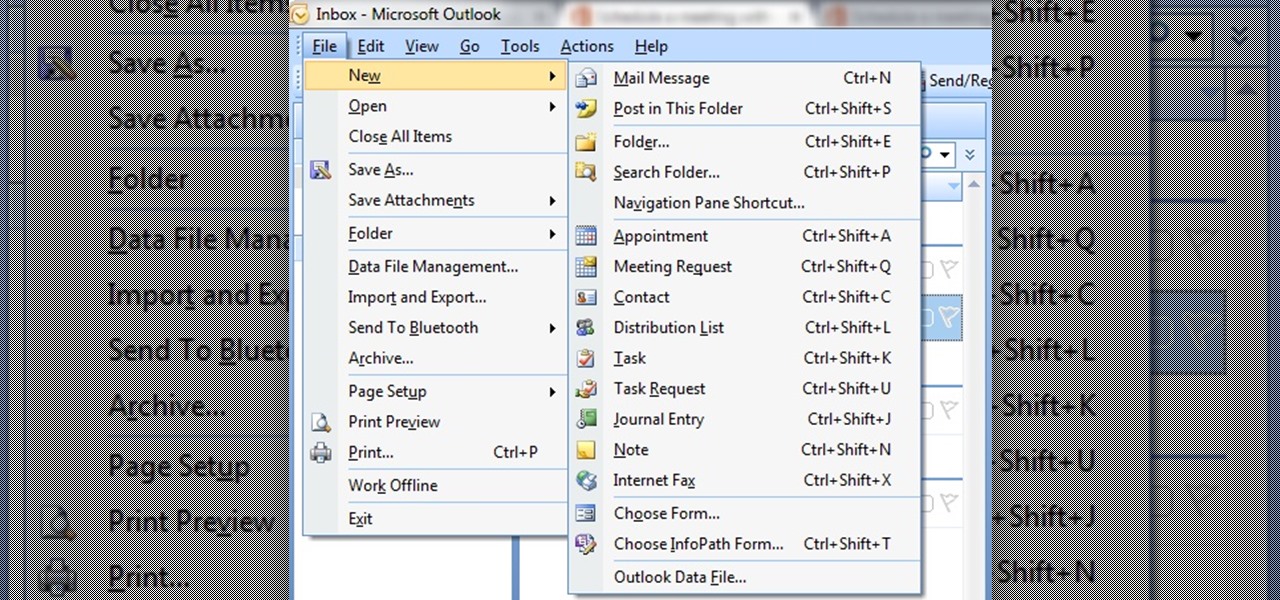
In this tutorial First, we will discuss what a meeting is, How can we schedule it in Outlook. A meeting can be defined as a mass of two or more people have a common motive. All the people present in a meeting can share their ideas and exchange information, to carry out the actions to achieve their goal. This tutorial helps those people who are looking for the steps to Schedule a Meeting in MS Outlook.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Make no bones about it—having an "undo" option is a freaking godsend. Whether you accidentally deleted an entire essay, screwed up the shading on a Photoshop job, or sent an email that wasn't quite ready, having the option to undo a click or button-press can definitely be a lifesaver.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

As soon as third-party keyboard compatibility was announced for iOS 8, Apple loyalists and the newly curious both looked to the popular Android third-party keyboard developer, SwiftKey, to see if they'd be offering their services to iOS.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

THis video shows you what types of videos you can make, why you should make videos and exactly whant you need to get started.

This video from ESPN walks you through the different draft modes available for picking a fantasy football team using the ESPN fantasy football site. The different draft modes available are:

You don't need to pay a stylist or even get a friend to help you with this hairstyle! It's easy, elegant and looks good with nearly any type of long hair. Here's how to create an elegant bow updo for your next formal event!

New to shooting video with a DSLR? In this video tutorial from renowned DSLR cinematographer Philip Bloom and the staff of Vimeo, we receive some tips on how to work with different lenses when using a DSLR like the a Canon 7D, T2i (550D) or 5D Mark II.

Add text and titles with Windows Live Movie Maker. There are three options for adding text in Movie Maker. This tutorial provides an overview for each type: title (which goes before the selected clip), caption (which is superimposed over the selected clip) and credits (which goes after the selected clip).

This is perfect for someone who wants to keep their hands warm but still work with their hands (such as typing, sewing or crafting). Start with medium weight worsted yarn and a size I crochet hook to make these fun wrist warmers.

Need a smooth, polished, and glossy surfaced piece of acrylic for your next project? Then check out this video for a handy guide on how to sand, cut, and polish Perspex, a type of acrylic, for a high-gloss finish. Perspex is thick and difficult to work with, but this video will give you tips for a professional look.

Got a cake or cupcake-obsessed friend? Then she'll simply swoon over this "You Take the Cake" birthday card. The greeting card depicts a triple layered cake crowned with frosting.

Just because when you bought your jeans it said that it was just one type of jean - bootcut or skinny - doesn't mean you can't wear it in different ways by either rolling them up or by slashing in holes to make them look worn.

If you want to create the type of makeup look where the makeup IS the costume for Halloween, then look no further than this video. You'll be guided step by step through creating a facial prosthetic from latex. This prosthetic can be shaped any way you want to form rotting flesh for a zombie costume, scars and wounds, even bullet holes.

You can make jewelry out of chainmail! It will be bulky, unless you use incredibly tiny rings. This tutorial shows you how to make the box chain out of many small metal rings, which you can expand to a necklace, bracelet key chain or any other type of jewelry you can think of.

There are lots of key parts to creating beautiful makeup, but if you had to ask us for the most important step we'd without a doubt say foundation. Good skin looks good no matter what other type of makeup you decide to you put on, whether it's smoky eyes or red lips. That's because beautiful, flawless skin acts as a smooth, pretty base.

Sandpaper is one of the essential tools of woodworking and carpentry, and there are many types with different applications. This video is for woodworking beginners and will teach you a lot of the basics about sanding so that you can give your pieces the finish they deserve.

You don't have to know what kathal pulav means (jack fruit pulao, or jack fruit plus rice pilaf) to enjoy its mildly sweet and rich flavor. Jack fruit is a supersized fruit (the largest tree-borne fruit in the world, in fact ) comes from a Southeast Asian tree that grows in tropical regions.

Google's Goggles mobile app was a big hit on the Android market, and now they've given iPhone users the chance to enjoy the awesomeness of Google Goggles. This iPhone app only works on the Apple iPhone 4 or iPhone 3GS, and it's available in the App Store for download. Simply type in "Google" or "Google Mobile App" and you'll find the app with the Google Goggles feature built in.

Have you seen odd, square codes on some specific merchandise? These are called QR codes, or quick-response codes, and they are a type of bar code which your smartphone can read and then take you to a particular website, give you coupons or even a business card. Here's how you can get the most out of QR codes.

This is an Alicia Keys makeup look, inspired by some pictures of her wearing some gorgeous green eyeshadow. This look works great for any skin tones, but works especially well with skin types that are dark or tan. It's also a good makeup look that transitions well from summer to fall. Follow along to see how to apply this green smokey eyes and bright lips look.

Halo: Reach has gotten a completely revamped version of the Forge where you can truly let your imagination run wild! If you miss the old Invasion game types and want to make your own, this video will show you how! In this video you will learn how to create objectives, set up spawn points and many other options to create the perfect Invasion game for you and your friends!

If you're a Penelope Cruz fan, then this makeup tutorial is a must-see! You'll learn how to recreate her makeup look seen in these pictures. The makeup she dons is very classy, but also wearable for any woman, no matter the skin type or color. Her seductive eyes draw in all the attention, as well as her defined, neutral pouty lips.

Tutting is one of the most versatile types of popping, and has become popular in the rave community because it's emphasis on hand and finger moves translates well to light shows. This video is a basic tutting tutorial for ravers to get acquainted with the theory of tutting and some basic moves to get started.

Tutting is a popular type of popping focused on 90 degree hand movements inspired by depictions of King Tut. This video will show you how to do one very cool tutting combo step-by-step, giving you another piece that you can use to build your tutting routines and kill the dancefloor

Google is always moving one step closer to pretty much controlling everything in the world, in a good way ofcourse! The latest feature added is Google Instant Search, so for anything that you're searching all you have to do is start typing in the search term and Google will immediately begin giving you results on the fly. In this video you will get a quick hands on demo on how to use the new feature.

One of the newest and most effective types of dry powder asmtha inhalers is called a Diskus. They can be confusing to use for those used to a more traditional inhaler. This video will show you how to use a Diskus to treat your Asmtha symptoms and make sure your device stays clean and effective for a long time.

One of the most annoying of the many annoying types of errors on Windows computers is when you computer won't recognize parts that have always been a part of it, like the drives or keyboard. If your computer has stopped recognizing your CD or DVD disc drive, watch this video. As long as the drive is still connected, the steps in this video should allow you to fix the problem and continue using your drive.