Interviewing lighting basic training tutorial provides easy to follow instruction in this step by step video. Set up the interview area to allow the best camera angles. Place your lights in key, fill, and backlight positions. Use back lighting spillover to fill subject area without camera spillover. Check your setup with the subjects and make any necessary adjustments to your camera or lighting angles. Place your crew and your ready for your interview. This scenario using key, fill, and back-...

In the GetConnected TV show BlackBerry expert Darci Larocque from Swirl Solutions gives an easy tip on how to call voicemail directly with one (1) key. This option can be seen in other cell phones also, but in a BlackBerry you can set a password for this. Hold the green button or call log , go to menu - Voice Mail, set your password, click escape and save. Now when you dial No.1 or hold it down you go directly to your voicemail.
Creating a motion tween in Flash CS4, which is moving one image from one position to another position.

Have you ever had to close an application with private info in order to let someone else use your PC? LockThis! is a windows application that lets you secure individual programs without the hassle of having to save your progress and closing the program. To use LockThis! just hold the control key and click on the application that needs to be locked and simply enter your password on the dialog that pops up and your done. Now anyone can use your pc without you having to look over their shoulder....

Grafting, also known as "top working," is simple-but-essential technique that enables you to change the variety of fruit a tree bears. In this tutorial, Stephen Hayes of Fruitwise Apples Heritage demonstrates the rind grafting technique, a useful method for grafting over a sound-but-unwanted apple or pear tree.
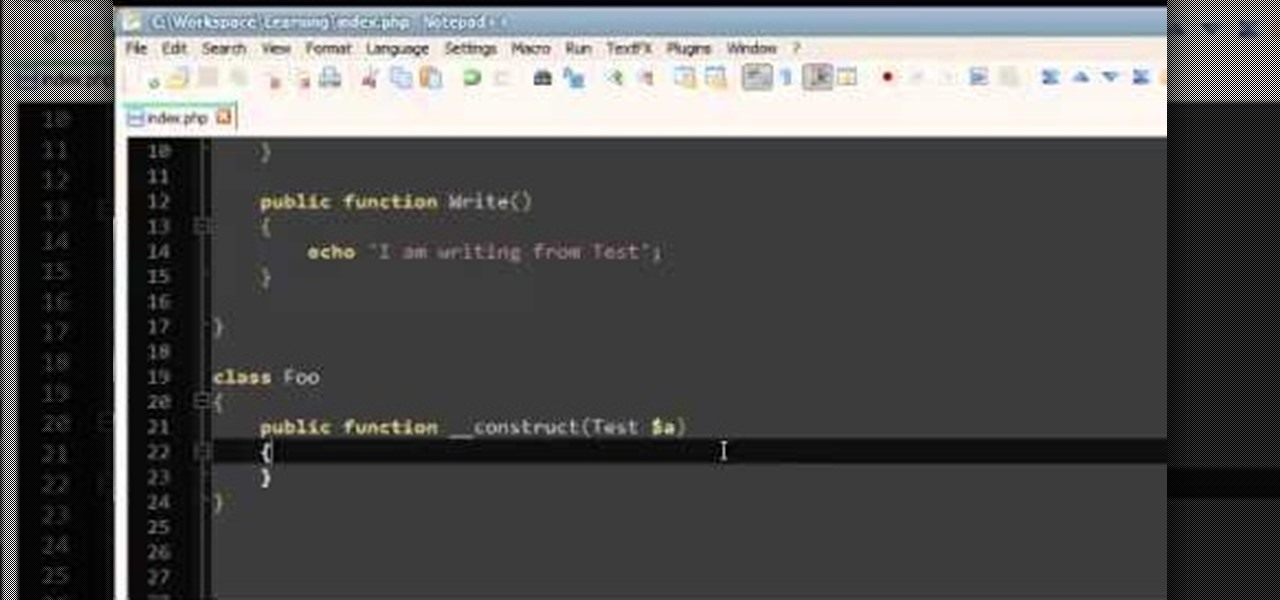
Type hinting in PHP appears frequently in design patterns but can be distinctively confusing unless you are totally familiar with it. This walkthrough from JREAMdesign raises your exposure levels to using type hinting in your parameter functions with objects and arrays.

In this video, we learn how to use different brush types and colors in water coloring. While you are creating a painting, you will notice that you need to use different types of brushes to create different effects on your canvas. There is nothing wrong with this! You can use many different strokes and brush sizes to achieve what you want on your painting. Pay attention to what stage of the painting you are in, as this will help you decide what types of brushes to use, depending on the style y...

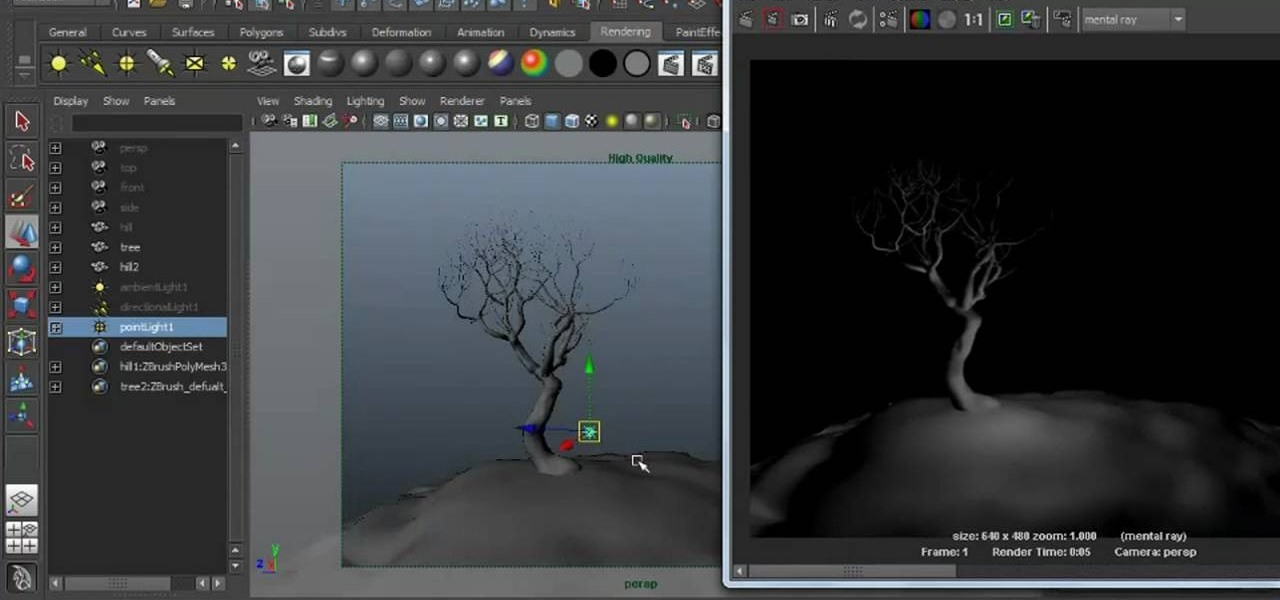
Learn about Maya 2011's various CG light types. Whether you're new to Autodesk's popular modeling software or a seasoned 3D artist just looking to better acquaint yourself with the Maya 2011 workflow, you're sure to be well served by this video tutorial. For more information, and to get started using CG light types in Maya 2011 yourself, watch this free video guide.

In this tutorial, we learn how to write with upside down text. To do this, go to the website Funicode. First, type some text into the box and as you type it, you will see code pasted underneath in different styles. You can use this text on any website that supports Unicode text. There will be several types of lettering styles, including an upside down text. This is a great website to use if you want to spice up the text that you write, and want to change things up! When you type in something ...

The iPhone can actually be annoying sometimes, especially those little sounds it likes to make when you click on anything. When you're typing, it can really be just too much for your ears. So how do you stop all the noise? Best Buy has answers. The Best Buy Mobile team explains how simple it is to eliminate the typing sounds on your Apple iPhone.

Shaking your cell phone is no longer a bad thing with the iPhone. Now, shaking is an actual feature, rather than a risky move. It really comes in handy when you're typing and you misspell a word. So how does shaking your iPhone work? Best Buy has answers. The Best Buy Mobile team explains how simple it is to shake to undo typing errors on your Apple iPhone.

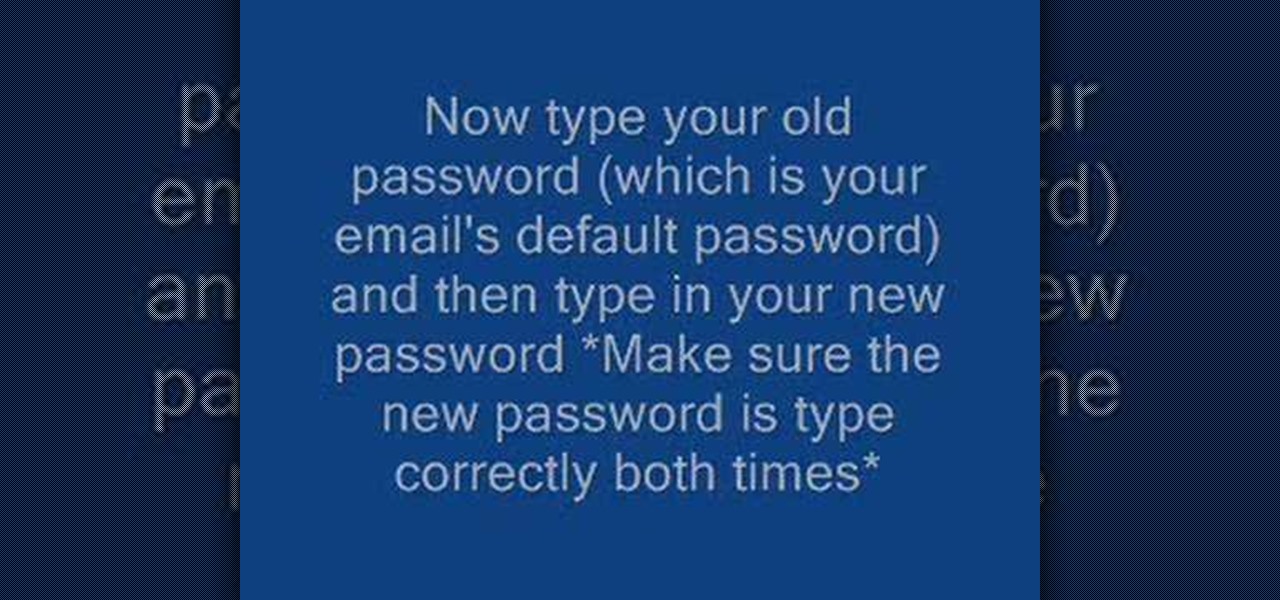
This video demonstrates how to set up a password for Microsoft Outlook. Begin by opening up Microsoft Outlook. Next, go to "GO" and scroll down the "Folder List." Click on this. Then right click on "Personal Folder" and then on "Properties." Next, you will need to click "Advanced" then "Change Password." You will then type your old password. This is your default password for your email. Next type in your new password. You will need type it in twice, so make sure you type it in correctly in bo...

In this how to video, you will learn how to create a diagonal sum in Microsoft Excel 2007. First, open the program and make a large selection. Type in =int(rand()*500) and then press control enter. This will create random numbers for the cells in the selection. From here, click conditional formatting and select new rule. From here, type in =column(A1)-row(A1)=$H$1. For the format, choose a contrasting look, such as a purple background and bold numbers. Click okay. If you type -1 or -2 in this...

To download the different types of screen saver using net, first to navigate in to "www.wallsaverapp.com". In this screen you have a "download" button that appears in the right of the screen. After download this program, run the program. Now you have to download different types of screen saver in website like "www.macupdate.com". In this site you can search different types of screen savers. Enter the website and type "matrix saver" in the search dialog box. Download the required screen saver....

This video tutorial in Computers & Programming category will show you how to delete temporary files in Ubuntu, Linux Mint or Debian. For this you will need the program called bleachbit. You could get it from Bleachbit Sourceforge/ or from Synaptic package manager. For synaptic manager, click on ‘package manager’ in the ‘start’ menu and log into the program by typing your password. Then search for ‘bleachbit’, download and install it. Go to ‘terminal’, type in ‘su’ and enter, then type in your...

This video discusses how to find the right type of bike for you. There are four different types of bikes: road racing, multisport, comfort sport and flat bar road bikes. Road racing bikes typically have lighter weight frames. They have steeper angles for more aerodynamic positions and higher components. Multisports also have light weight frames and higher components. They also have more aerodynamic tubesets in the fork and airwires which allow for a more aggressive position for races. Comfort...

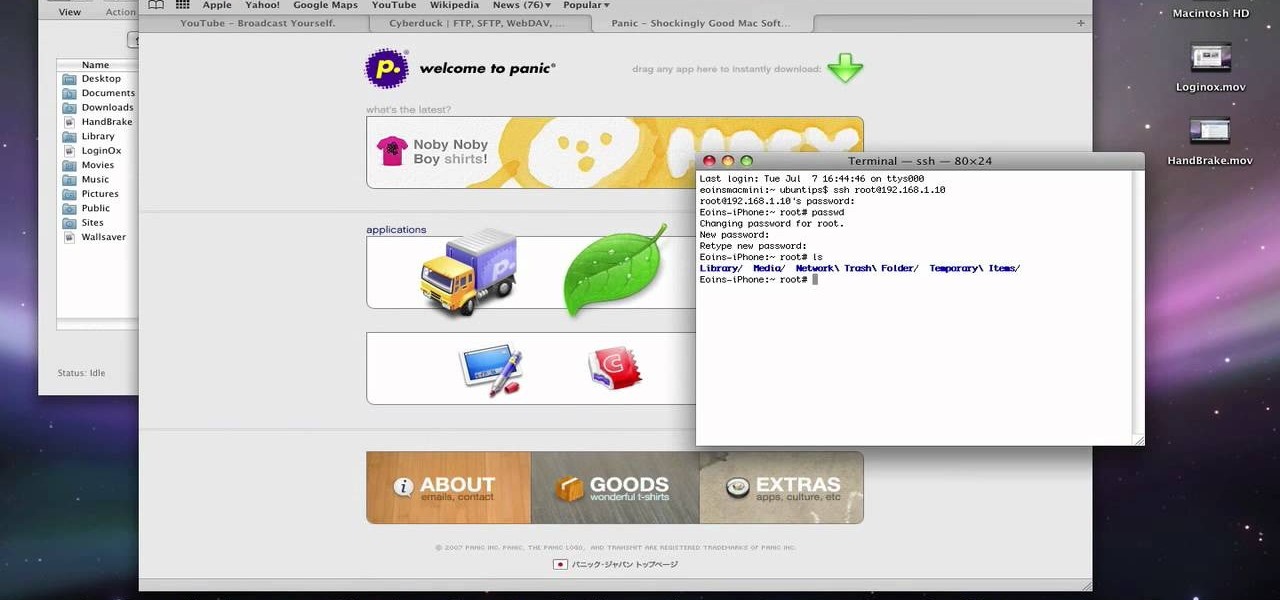
This video describes about accessing an iPhone in Ubuntu using open SSH, cyber-duck, Netatalk. For accessing using SSH, make sure your iPhone's Wi-Fi connectivity is on. Now open your terminal and type "SSH root@'address'". Here address refers to the IP address of your iPhone. You have to type a password to access the iPhone contents. Once you are authenticated type "ls" and you will be shown with the contents of the iPhone. The second method is using cyber-duck. In it, choose SFTP as the con...

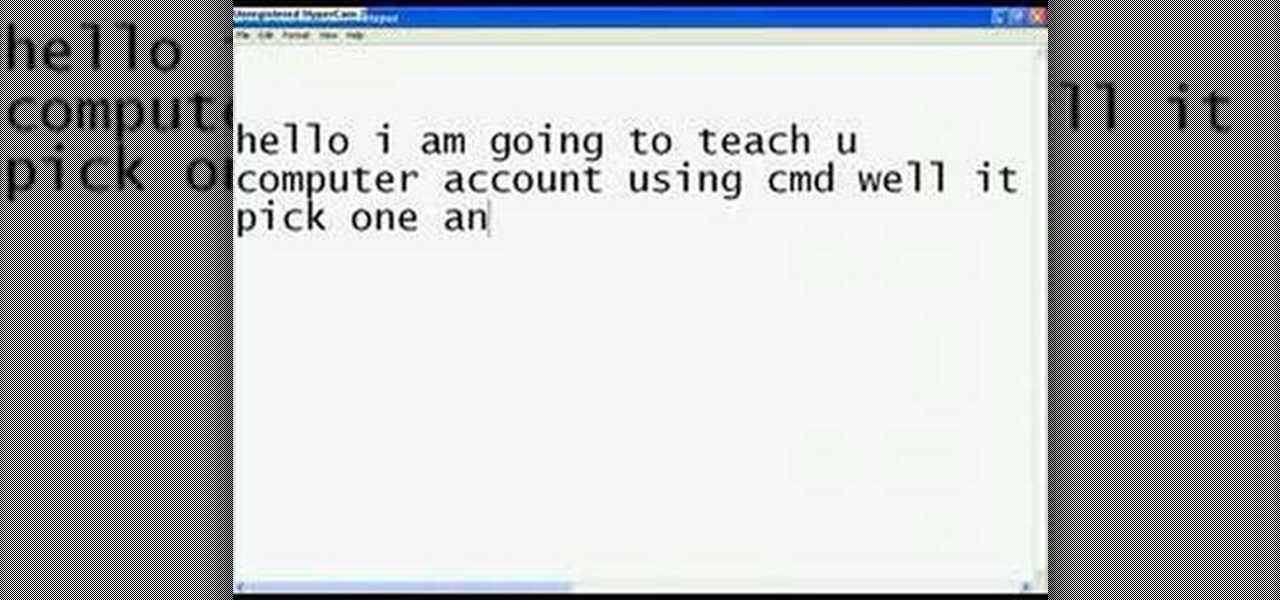
This video teaches you how to change your computer's account password using the DOS command prompt. The first step is to get to the command prompt, you can do this simply by clicking run in the start menu and typing "cmd." You next type "net user" which will show you all of the user accounts on the computer. Choose the one you would like to change the password for and type "net user (account name)." It will then ask you for a new password, you may type anything you like here keeping in mind t...

The Facebook is one of many social community website with many features. To break into Facebook at school there are many ways. Some of them are listed below.

How to replace a fork seal on a motocross dirt bike. Cartridge type fork, fork seals are easy. Rocky Mountain ATV/MC] is the largest off-road retailer in the U.S. Check out their how-to videos on WonderHowTo. Search Rocky Mountain for more videos.

Check out this cool Tinkernut video on typing upside down. This will drive people nuts!

Phil Macdonald and Trent Munro discuss how you can identify wave types for surfing. There are two types of waves: rolling and clenching waves. Rolling waves break far from the shore while clenching waves are more dangerous.

Seventeen years ago, Apple released iPhone, the first mainstream consumer phone with a touchscreen as its main typing input method. Apple has been perfecting its onscreen keyboard for almost two decades, and it's built with some fantastic features that make typing faster and easier. But it's easy to overlook some of these features, so here are some tips and tricks you need to be using if you aren't already.

One of my favorite iOS hacks is Type to Siri. This lets you type your queries to the iPhone digital assistant without needing to use your voice. Unfortunately, Type to Siri replaces the typical Siri voice prompt on the Home or Side button, meaning you need to choose between one or the other. That is, until iOS 13.

One core theme with each new iteration of iOS is the introduction of at least one or two features that fans have been hoping to see for years. With iOS 13, that feature is swipe typing, a first for the native iOS keyboard. While some of us have been getting our glide-typing fix with apps like Gboard for years, you might find swiping isn't quite your style. Luckily, the feature is easy to disable.

Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good thing, there is a way to get rid of the icon.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Another day brings another Apple ARKit demo, this time for a first-person role playing game that inserts villagers, vendors, and villains into real world locations.

A few years ago, the Hilton hotel group unrolled the Digital Key, a feature of the Hilton Honors app that allows you to unlock your hotel room with your smartphone.

In addition to trying to give Pokémon a life on the HoloLens, Sky Zhou, a founding member of mixed reality studio Matrix Inception, won Microsoft's Actiongram Fantasy Contest Quest last month for his video concept on slaying dragons. But fantastical creatures aren't the only thing Sky can whip up on the HoloLens.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

The new Google phones, which are rumored to ditch the Nexus moniker for Pixel, will most likely come with an Android feature that 7.0 Nougat doesn't currently have—a new set of navigation keys.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

In the second part of this tutorial, we are going to crack the hashes that we've captured previously. I'm going to explain how to do it with the powerful John the Ripper. It comes with Kali by default, so no need to install!

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.