While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

Increasingly, cutting-edge platforms like blockchain technology and augmented reality are overlapping, forging new digital frontiers that promise to change the way we interact with the virtual and the real world.

Brace yourselves, because Siri has a trick up its sleeve that iPhone users have wanted for some time. Yep, that's right, I'm talking about the ability to use Siri without having to talk out loud for the whole world to hear. It's great for privacy, Siri-ing on the down-low when you're not supposed to, or ... you know ... if you have a speech disorder.

In a race to make self-driven cars mainstream, Intel announced today that they've bought Israeli microchip technology company Mobileye for $15.3 billion, setting the stage for Intel to dominate a large portion of the driverless market.

Hello guys, I recently made a how to about whatsapp but the problem with that script is that it is way to long and you need to copy and paste it so many times so I made a new one that works just fine and is more easy to use lets get into it (Here Is How The Code Supposed To Look)

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

Ready or not, the USB-C cable is about to take over your electronics. The new industry standard is fully reversible and packed with enough power to serve as a laptop charger or an HDMI cable, so it actually has the potential to replace every cord, wire, and connector in your house. In fact, the conversion has already started: The latest MacBook, Chromebook Pixel, and Nexus phones are sporting USB-C connectors out of the box.

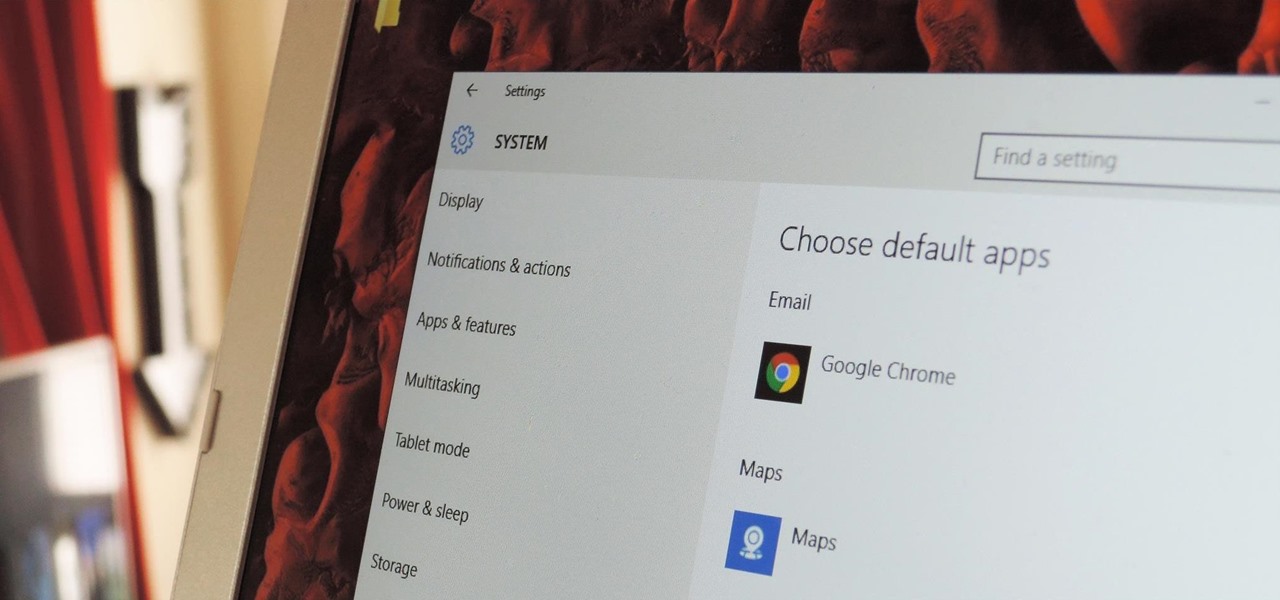
The first time you launch any type of file, Windows 10 will usually prompt you to select an app to open it with. Occasionally, though, this "Open with..." screen doesn't show up, and instead Windows will use a pre-installed system app to launch the file without ever giving you a choice in the matter.

Hello again, reader! In this post, we are going to cover some data types and how to declare variables. It shouldn't be too hard so just sit back, relax, grab some popcorn and enjoy the ride (while you still can!).
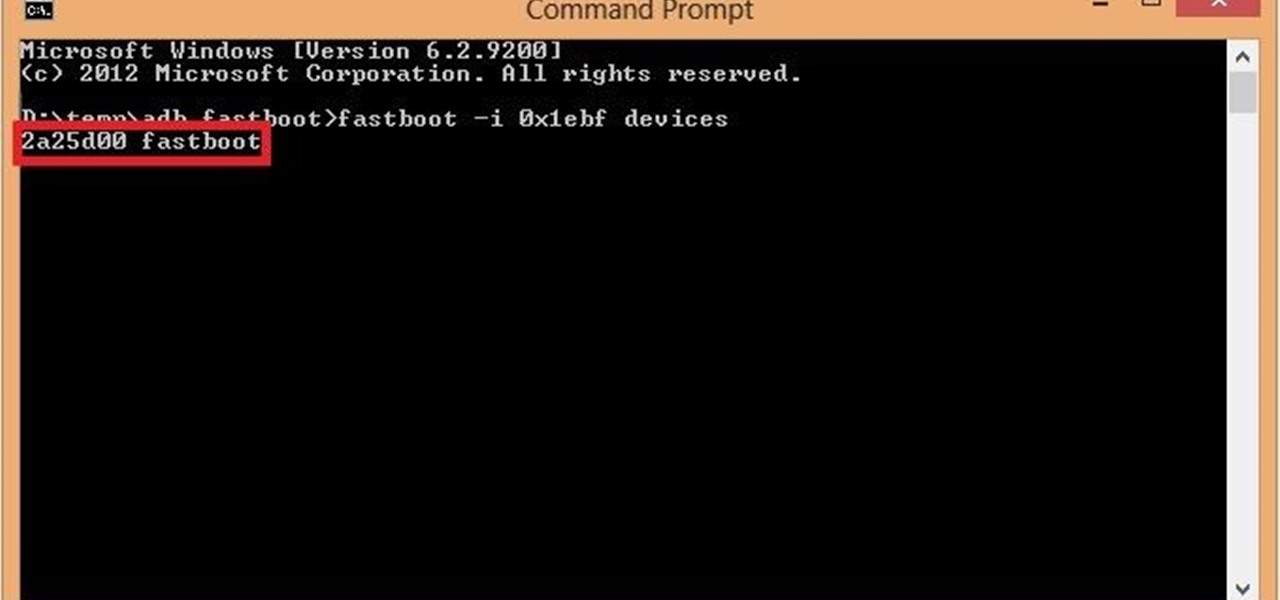
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

For some strange reason, not all variants of the Samsung Galaxy S6 and S6 Edge have a menu option for changing the backlight timeout for their capacitive keys. According to user reports, only the AT&T variant of these phones has such an option.

If you are among those lucky ones who got a chance to pickup the Yu Yureka from Amazon and looking for a detailed guide on how to root your yureka, then I doubt that there is any better place than this. You might have visited some XDA threads for the same but those are generally brief explanations and you might miss something or the other. Moreover, in most of them, ported Clockworkmod recovery has been used which is less stable and lacks features. So keeping your worries aside, look nowhere ...

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Google debuted YouTube Music Key in November, and for $10 a month, this essentially turned YouTube into a music streaming service. With ad-free music videos and background audio playback, YouTube serves as a viable alternative to Spotify or Pandora for Music Key subscribers.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

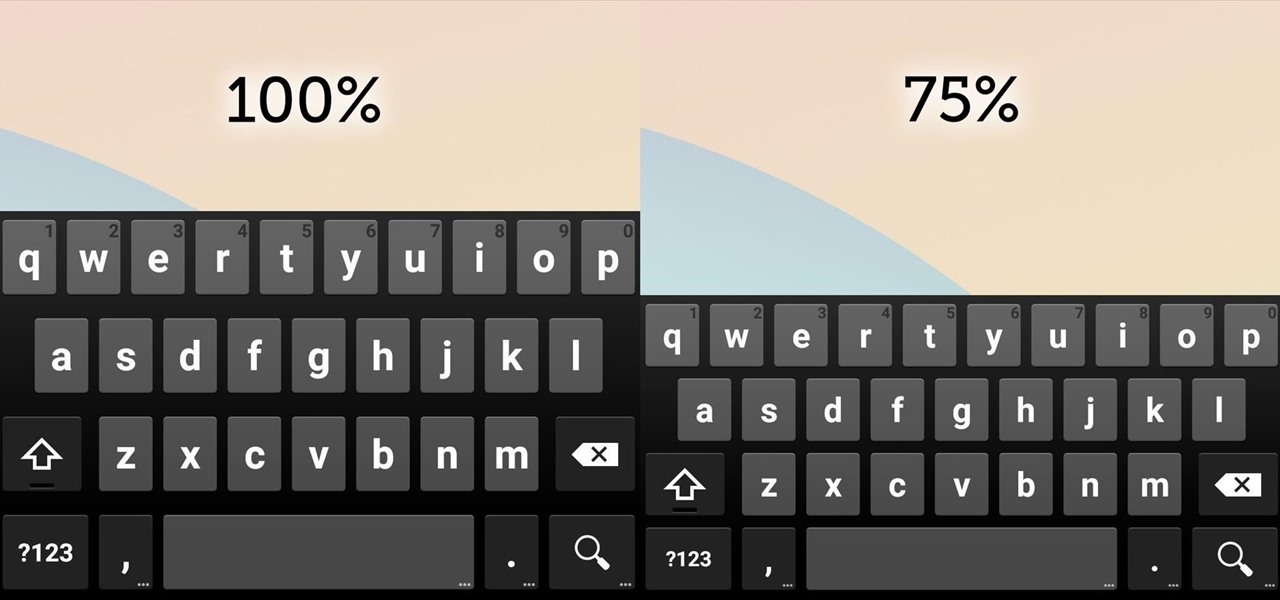
Google Keyboard, which comes pre-installed on Nexus devices (and is available for all others from the Play Store), is one of the most functional keyboards currently available for Android. With features like gesture-based typing, next-word prediction, and even text expansion macros, it's a very capable form of text input.

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

If you had the original Microsoft Surface with Windows 8 and a Type or Touch cover, you know how big a pain in the ass it was to change the scrolling direction of the trackpad.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

PUT THE PHONE DOWN!!! Don't call the locksmith just yet! Watch this video and l will save you at least $100.00

If you have an iPhone, you probably already updated to iOS 6.1, which was released earlier this week. The new release came with some very subtle updates, including LTE support for more carriers, the ability to purchase movie tickets from Fandango via Siri, some security patches, and more.

I love my Mac just the way it is. Well, minus the fact that I accidentally deleted iPhoto and would now have to pay $14.99 to get it back. Other than that, my Mac is pretty sweet.

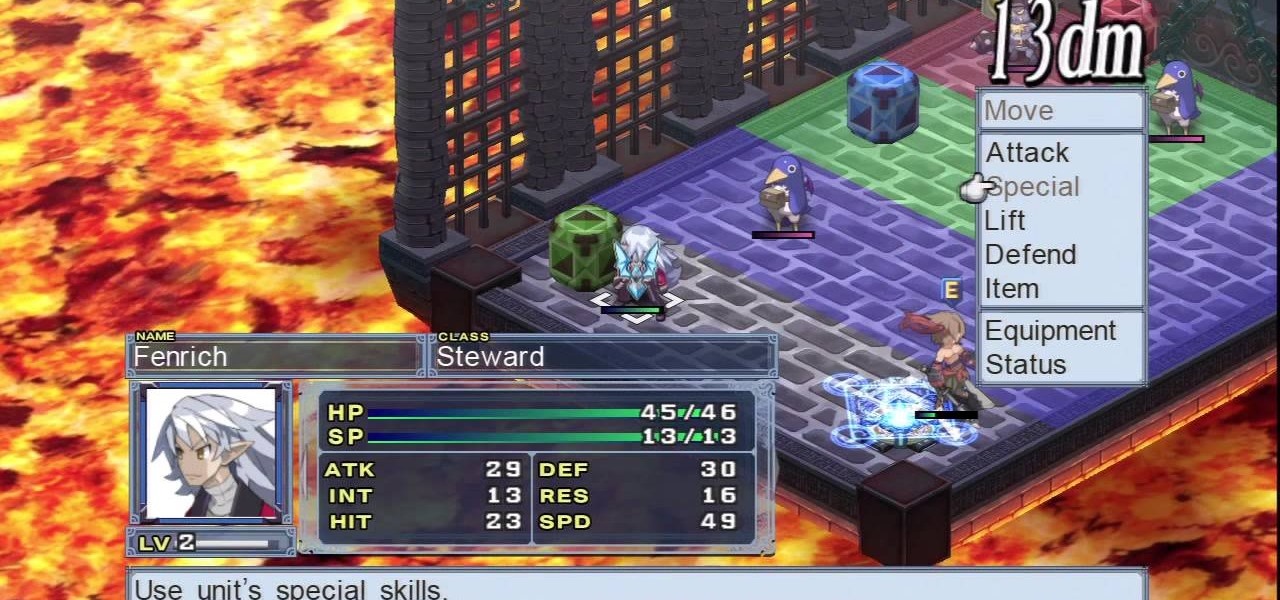
The effective use of Geo Blocks in Disgaea 4: A Promise Unforgotten is key. They provide buffs and stat increases to your players and can help turn the tide of battle against your enemies. Take a look at this Geo Block tutorial to find out how to leverage them effectively in Disgaea 4.

A strong core is the key to a healthy, strong body. And who knows more about core strength than the elite Navy SEALs? Check out this workout video to learn three simple exercises that will get your abs, lower back, glutes, and more in top shape.

Even songwriting greats like Alicia Keys and Stevie Wonder had to start somewhere. If you're interested in playing the piano but aren't sure where to begin - and also not too interested in playing nothing but scales all day - then start your melodic musical journey now by playing "Mary Had a Little Lamb."

Getting locked out of a bedroom or bathroom can be a real bummer. Fortunately, these locks are easy to "pick" and get yourself in. This how to shows you clearly what to do to get yourself back inside so you don't feel frustrated all day long. This excellent video takes you step by step through the process. This video talks about 2 different types of locks and the two different types of tools you'll need.

Low budger project? NO budget project? Lighting is a key part of any film, so you don't want to skimp on it. This tutorial shows you how to set up some inexpensive lighting systems when you're filming a documentary or interview.

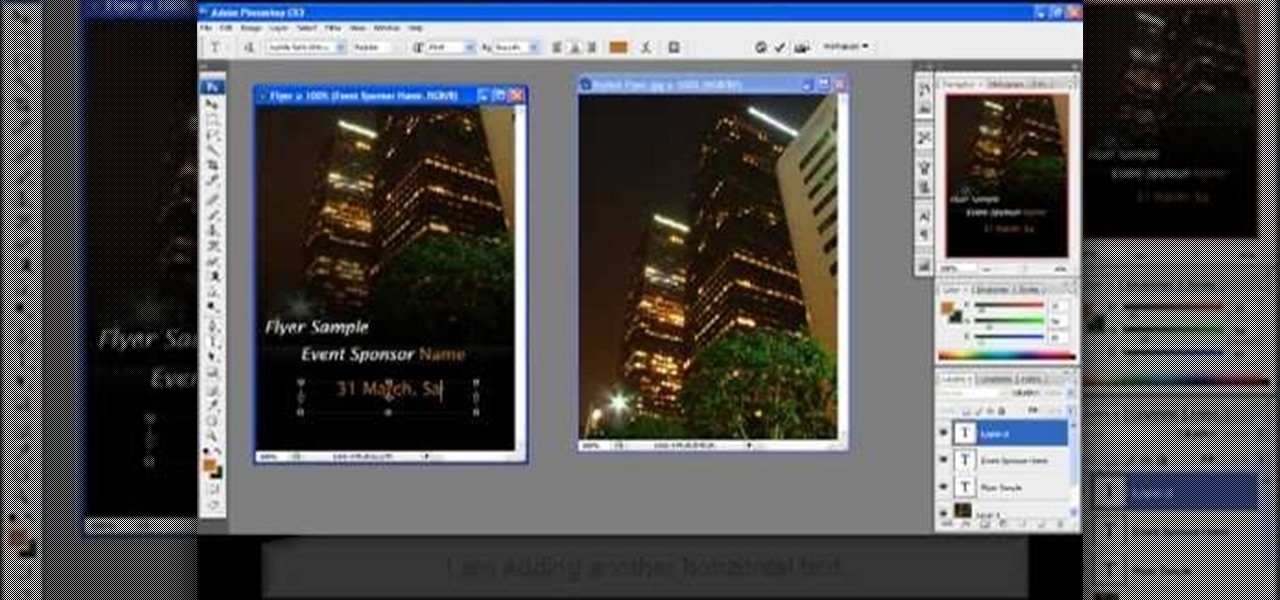
Having a clean, stylish, and visually appealing layout is the key to effectively conveying information on flyers. In this Photoshop tutorial, we will plan, layout, and construct a good looking flyer that can be used for virtually anything. Learning how to create a flyer is a skill that can come in handy often, and after watching this tutorial, you should be able to create your own.

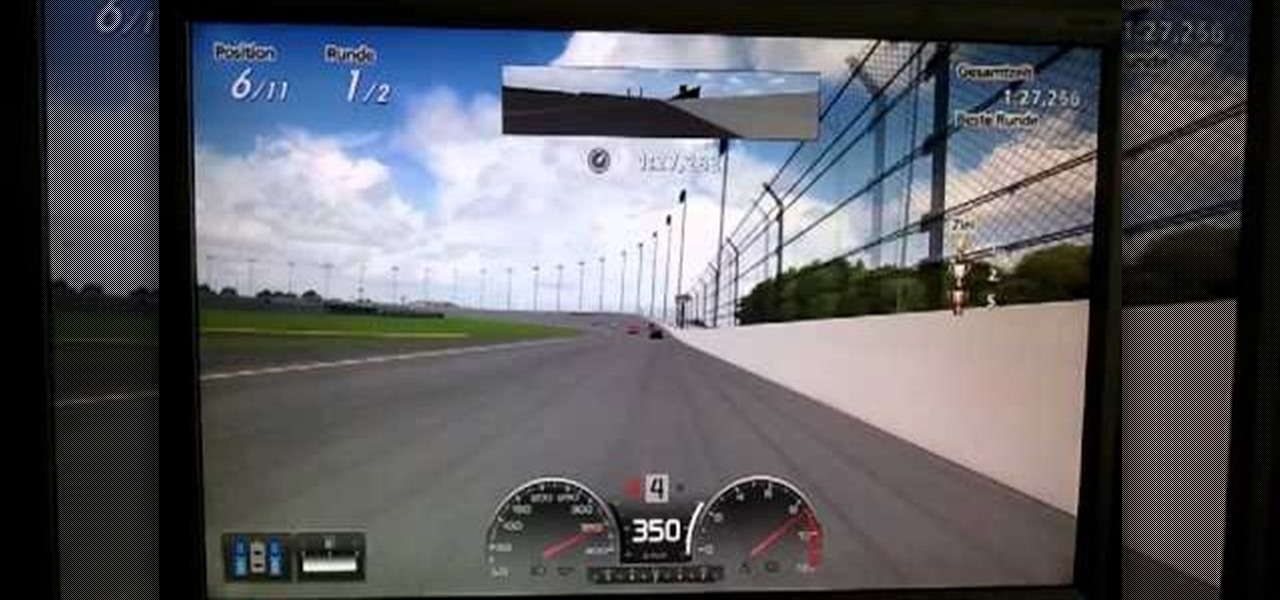
As any NASCAR fan worth his beer and fried food knows, drafting is the key to achieving high speed and ultimately success in NASCAR. If you're having trouble with the NASCAR Special Race in Gran Turismo 5, watch this video for a demo of how to run it perfectly, with tips on proper drafting, braking, and other techniques.

Think you might like to set up a green screen? It's easy! All you really need is a big green sheet. This video production tutorial presents a complete guide and will see to it that you know everything you need to know start incorporating green (or blue) screen work into your own video productions.

In this video tutorial, you'll learn how to use keyboard shortcuts within Google Gmail to speed up common and repetitive tasks. For all the details, including step-by-step instructions, and to get using these useful key commands yourself, take a look.

In this tutorial, we learn key commands that will allow you to sleep, restart or shutdown an Apple computer running the Mac OS X operating system. They're easy to use and remember and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

In this tutorial, we learn how to set up and use custom key commands on an Apple computer running the Mac OS X operating sytem. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

Don't hunt for that icon, make any Windows program you want launch at the stroke of a key. For more information, including detailed, step-by-step instructions on how to create your own custom keyboard shortcuts on a Microsoft Windows PC, watch this helpful home-computing how-to from CNET.

PhotoKey is a cheaper alternative to Photoshop if all you want to do is work with green screen effects. This tutorial shows you the basic Chroma Key functions available to editors in PhotoKey, so you can start adding your own backgrounds and special effects.

Aimed at Flash developers who like making games or other applications, this tutorial shows you how to use keyboard mapping so users can control the game using specific keys. This is also useful for photo galleries or slide shows, so users can navigate using their keyboard.