A DeAuth hack attack against a wireless network, as shown in this how-to video, will disconnect any and all users on a given WiFi network. The attacker does not need to know the WEP or WPA key or be connected to the network. For step-by-step instructions on running a DeAuth hack yourself, watch this simple how-to guide.

The Aeolian mode is the sixth mode of the Major scale and has the formula 1, 2, b3, 4, 5, b6, b7. Its tonic chord is a m7.(Am7 in the Key of C). This video shows you how to play it on the piano.

Many people like to interview subjects outside because they enjoy the look of sunlight over tungsten lights. However, it can be difficult to work with such an uncooperative key light. In this Israel Hyman video are some ideas which can help you improve your outdoor interview imagery.

The doubles team of Mike and Bob Bryan discuss doubles strategy with tennis pro Brad Gilbert. Movement, communication and proper positioning are key. Tips are given throughout the video in the form of popups. Easy to understand.

Do you ever lose your house keys? Well here is one extreme way of dealing with the problem, create your own lock pick! To create your own lock pick, you will need your own dremel, an electric grinder, and some hack saws. Follow along with this instructional how-to video to learn how to hack open locks with homemade lock picks.

French braiding is the perfect example of something pictures and words just can't seem to convey. This video shows in great detail the steps and finger placements... which is the key to a great French Braid!

The axel kite trick is basically a 360 degree flat turn on the center (axel) of the kite. Watch and learn how to do this core freestyle trick. It's absolutely key to learning advanced tricks. This is a sample from Prism Designs' Freestyle Pilot instructional DVD on dual-line kite tricks.

In this tutorial, we learn how to create an Alicia Keys inspired bright light blue look. First, apply eye primer to your lid, then apply a blue eyeliner to the entire lid. Next, take a fluffy brush and blend the blue out around your eye. After this, apply a bright blue eyeshadow to the entire lid, blending the dark in at the end of the eye. Next, apply black eyeliner to the upper lid, then apply mascara. Next, apply black eyeliner to the water line of the bottom lid, as well as a thin coat of...

Learn how to play blues rock guitar licks. In this video, you'll see how to play a couple of Gary Moore licks in the key of B. Regardless of your preferred style of music, if you want to be great, you'll need your head and hands on the same page. And there's no better way to get your head and hands on the same page than to practice. Happily, the Internet is awash in video tutorials like this one.

This video shows you how to use the satellite view on your blackberry. First highlight the Google maps icon. By default, the program goes to map view, in which you can see the roads and even railroad tracks. Satellite view gives you a different perspective on the way you see maps and you can see things you wouldn't normally be able to see in map view. Click the blackberry menu button, scroll down to satellite view, push the track ball or touch your screen if you have the blackberry storm. Now...

The following are the steps to be followed to boot Windows XP from a CD: 1. The first thing to do is switch on your computer. Before your computer starts loading windows, you need to hit the F12 key.

First make sure that you have a boot able disc and insert it to your optical drive. Shut down your PC And start it up again making sure to press the special key to enter the setup dialog. Go to the boot sequence and select the CD ROM as the first bot device as shown. Save the settings and exit the setup console. Wait for the PC to boot up and during the loading hit any key to boot from the CD.

Do you know how to cook beef short ribs? How about a point off natural brisket? In this video, Andrew Zimmerman, offers simple and easy recommendations on his favorite methods of preparing and cooking various cuts of steak. Zimmerman lets you know what kinds of steak work best with a sweet marinade or a saltier one. He also lets you know about different methods of cooking steaks such as pan frying, grilling, and even poaching. Zimmerman's key to a perfect steak, however, is its rest time. He ...

No matter what your shape is, follow this advice to make sure you strut your stuff with style. You Will Need:

This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus cell phone.

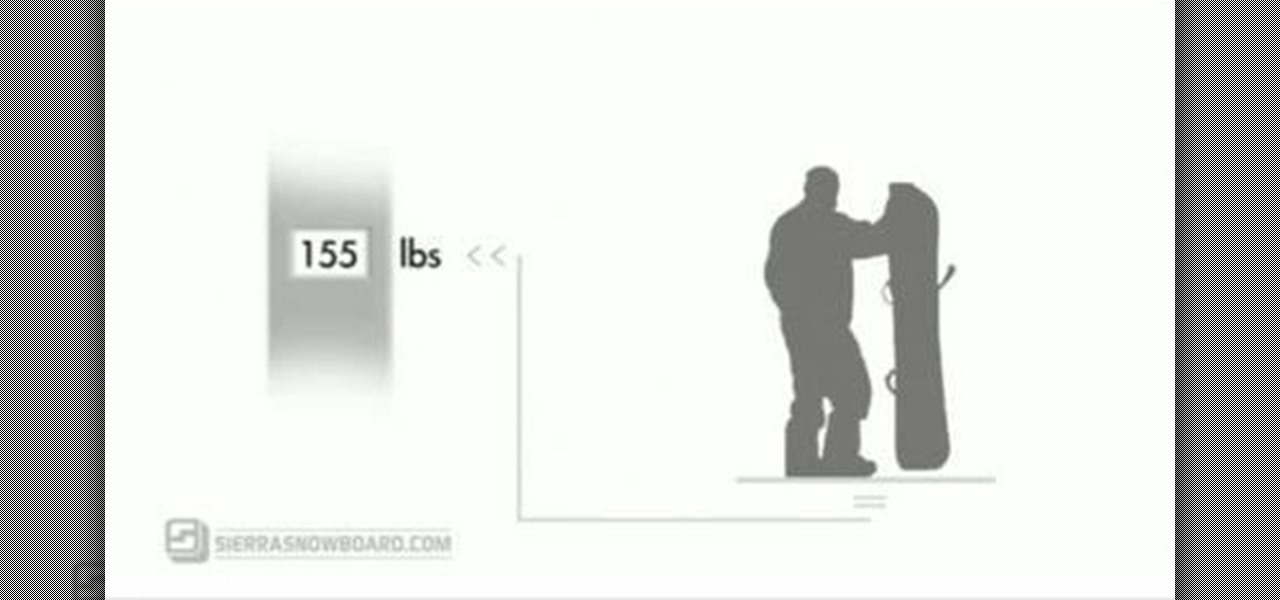
In this video, Sierra Snowboard gives us some tips on how to select the snowboard that's right for you. Each board comes in a number of different sizes, and most boards come with a size chart specific for that board. These charts can be vague, but are good starting points for selecting your size. One thing to consider is your bossy type. The weight of the rider is the primary factor in selecting the size of a snowboard. You'll notice that the height of a rider is not listed on a size chart. I...

If you need to know how to make an arrangement on an acoustic solo fingerstyle guitar, you've come to the right video tutorials. This three-part instructional guitar lesson will show you want you need to know about arranging.

With the Galaxy S20, Samsung has officially removed the Bixby button from its flagships. While it was a controversial key, in its later days, it did give us the ability to launch an app or custom action at the press of a button. There's still a way to do something like that, but now, you'll have to use the power button instead.

If you've been paying attention to the smartphone industry, you've certainly noticed a rise in dark mode lately. With most phones now sporting OLED panels, which use less power to display darker colors, users have been begging developers to include a dark theme in their apps. Lately, Google has been happy to oblige.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

While the Galaxy S10 is a beautiful phone, its software isn't for everyone. One UI makes huge strides toward undoing the mess known as TouchWiz, but for purists, it's still not quite on par with stock Android. Fortunately, the beauty of Android is you can change this with a few apps.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

You can easily deck out your favorite phone with great wallpapers, ringtones, and icons, but what about fonts? Not all Android skins let you change the system font, and even when they do, the options are often limited to a few choices. Certain root apps can open up the system font to customization, but some of these can cause problems now that Google introduced a security measure called SafetyNet.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

This week, Samsung officially kicked off the Oreo Beta Program for the Galaxy S8 and S8+ in North America and several other markets. The full list of changes is quite substantial, so we'll be running through them in a series of posts detailing what's new. First up, the Galaxy phones inherit notification channels from Android 8.0.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

ARKit and ARCore generate excitement among various segments of the tech industry for spurring adoption of augmented reality with consumers via mobile devices.

The iPhone has a handy feature called AssistiveTouch that lets you quickly adjust volume, lock your screen, rotate your display, and even navigate through the phone's interface using a virtual home button. In a way, it's a lot like the on-screen navigation bar that you'll find on some Android devices, but with a lot more functionality, and bundled together in a floating bubble interface.

With certain apps and games, it's all about the settings. In order to get your money's worth with one of these, you simply have to take the time to tweak and adjust various options, which is something a lot of users don't necessarily want to do.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

Welcome back my friends !! Today we'll go through the second part of this C# series

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

Welcome back Java programmers! In this tutorial we'll being going over Variables/DataTypes and Type-casting

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

If you exceed your monthly mobile data limit, your cell phone bill can skyrocket pretty quickly. This is why a lot of people vigilantly monitor internet usage and even uninstall apps that use too much background data.
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!