Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

At last, what you all finally waited for! Hi! Fire Crackers,

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

If you utilize strong passwords—which you absolutely should be—you've probably had to go back and forth between keyboard screens multiple times to input various letters, numbers, and symbols.

It's pretty logical for your MacBook to sleep when you close its lid, but under certain circumstances, you may not necessarily want this feature to kick in.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

One of Android's strengths when compared to other mobile operating systems is its ability to set third-party apps as the default handler of certain file types. Instead of being stuck with pre-installed system apps when it comes to opening files and links, you're free to choose a better-fitting alternative.

In a world where mobile devices are the new norm for interacting and staying in contact with one another, it's important to make the experience as smooth as possible, and typing is the biggest problem for me.

HTC pulled out all the stops when designing the HTC One M8. From it's sleek body, to it's incredible sound quality, this thing just oozes sophistication. While all of these add-ons are great, they can be incredibly taxing on the CPU, in turn causing some serious lag.

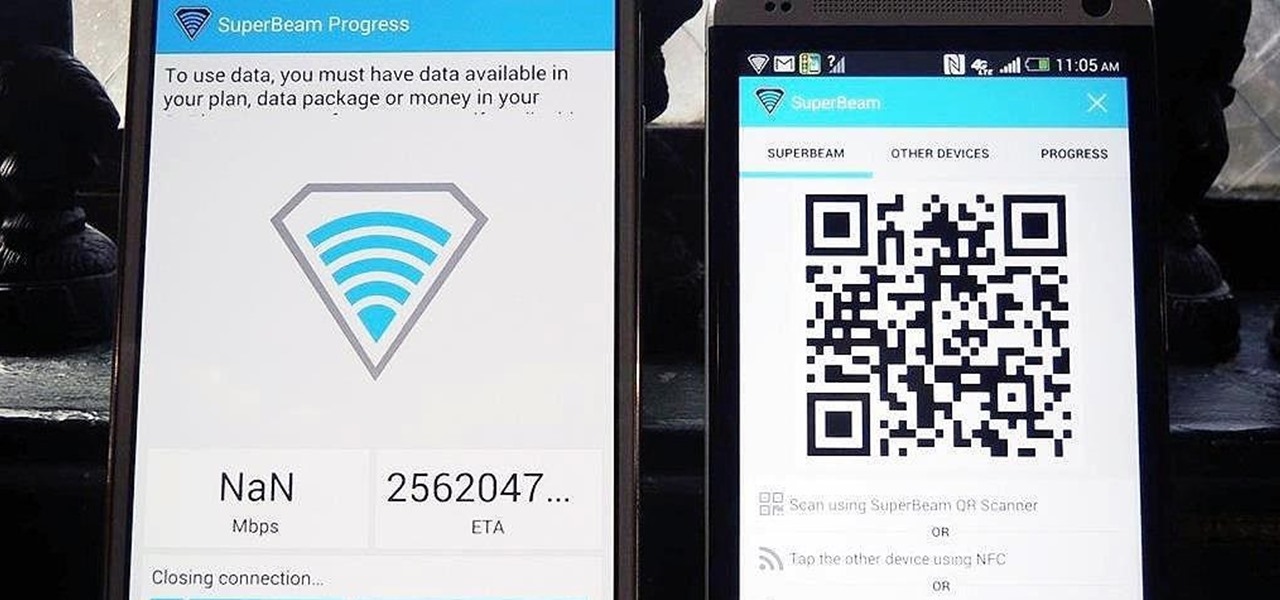
Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use.

Like insurance, it's always better to have a computer mouse and not need it than to need it and not have it. Honestly, I don't want to carry around a clunky mouse with my laptop, so I don't. I do something else, something more convenient. I use my Nexus 7. If you want to give it a try, I'll show you how it's done right now. All you need to is a Wi-Fi network and a specific Android app to control your computer with your Android tablet.

When it comes to the user interface, you're pretty much limited to the stock one that comes on your Samsung Galaxy Gear smartwatch—a carousel of large black and white icons representing the features and applications on the watch.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Like many other smartphones, the HTC One has a few capacitive keys on the bottom of the device, but that's the problem. It only has a few keys, meaning two, which are the Back and Home keys.

Let me start out by saying that Steampunk isn't about being historically accurate, and that everything I'm about to tell you is entirely optional. That said, let's take a look at the history of screws! What many people don't realize is that before we had metal screws, wooden screws were in wide use for things like wine and oil presses. Generally, the invention of the screw is attributed to Archimedes in the 3rd century BC. That was a long, long time ago. Metal screws and even screwdrivers hav...

What time is it? It's a question that you'll find yourself asking a million more times throughout your life, but one that hardly goes unanswered. When you're on your phone or at your desktop, there is almost always some type of clock available to immediately give you the time.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Compressor 3 is part of the Final Cut Studio package and sports a brand new interface. So if you're new to the software, or haven't played with the newest version, you're sure to learn some good hot keys and interface tips.

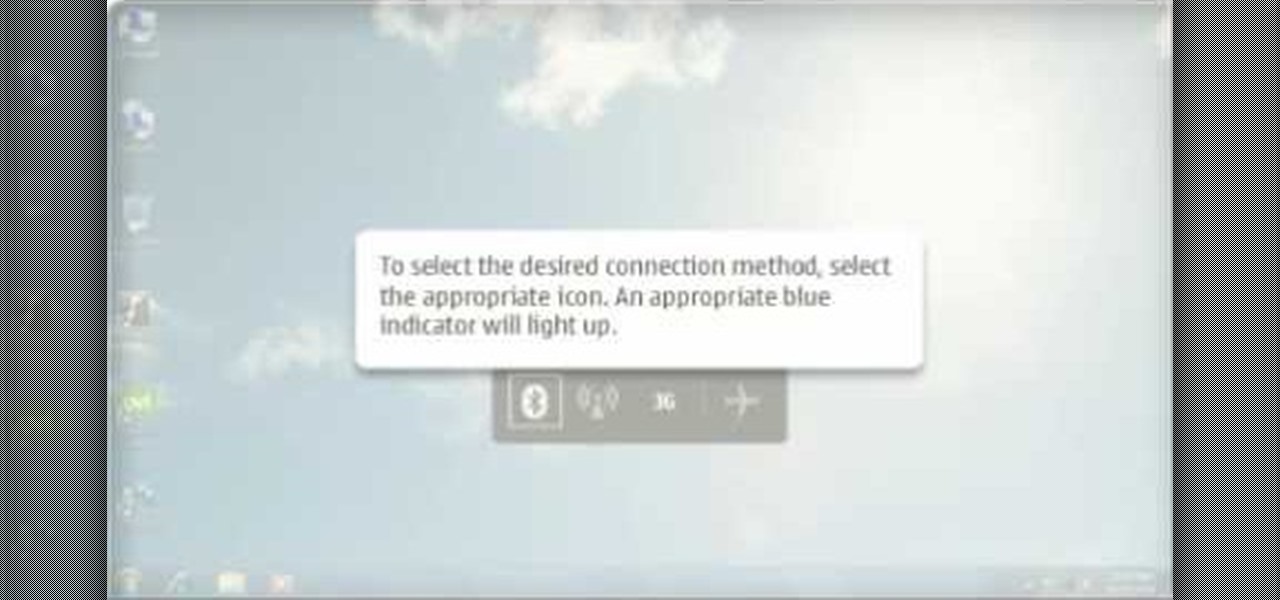
If you hit the FN + F10 keys on your Nokia Booklet 3G, you'll see the available internet connections methods for your netbook including Bluetooth, wifi, and 3G.

Grab a thin tension wrench and a thicker tension wrench, combine them with your favorite pick, and you'll be ready to unlock that 700 series American Lock that you, or someone you know has lost the key to.

The key to building a great Minecraft world is efficiency. This video will show you the most efficient way to kill mobs, a four-way mobvator that attracts mobs to spawning pads and elevates them to a killing mechanism so you can capture the loot. This is up to date for Minecraft beta 1.6.

Check out this video to learn how to get the Wunderwaffe in Call of the Dead, the zombie map from the COD: Black Ops Escalation map pack. Whether you play on Xbox 360, PS3, or PC, this video has the key to picking up the Wunderwaffe, one of the best guns in the game.

Are you playing Minecraft on a Mac? Would you like more functions and better performance from chat? Check out this video, you'll need to download Modloader and improved chat. You'll be able to bind keys, so that your most used commands are only a single keystroke away!

Live in a place with severe winter? You may eventually find that your car door lock has frozen solid. You can try jiggling the door handle, but if that doesn't work, then bring out a butane lighter and heat up your car key. Take care to not get burned!

The key to getting a perfect synchronization on this level is being able to complete it in less than eight minutes. This video shows you a walkthrough for this level so you can complete the entire thing in the time allotted.

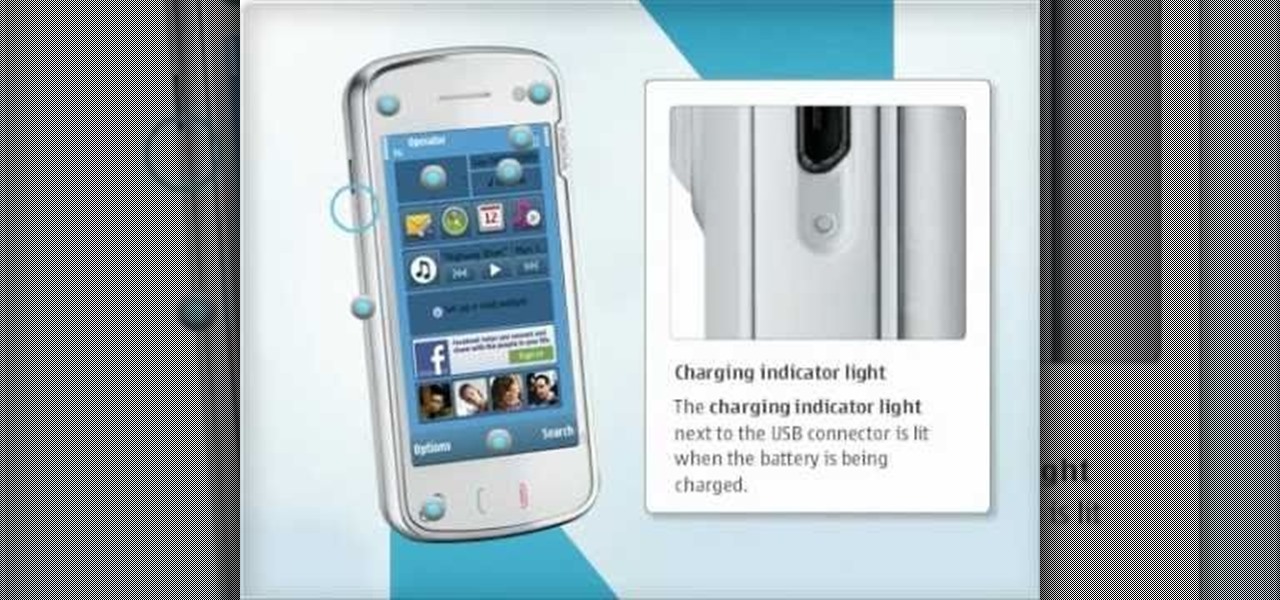
Get familiar with the keys and parts of the Nokia N97, and with the elements on the home screen. It's an easy process. And this clip will teach you everything you need to know. For all of the details, including complete, step-by-step instructions, watch this brief, official N97 owner's guide from the folks at Nokia!

Beware of large rooms! The key to defeating the first boss in Dead Space 2 is to shoot the yellow markers on its arms. As long as your aim is good, you'll defeat it easily. Also learn more about Isaac's lack of memory.

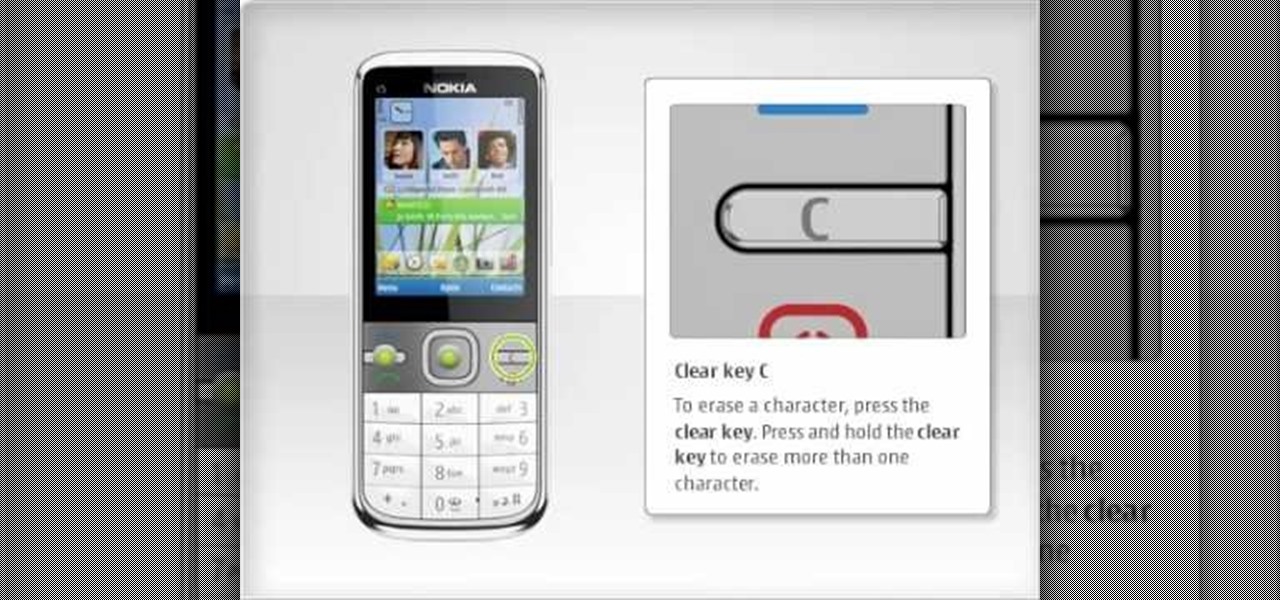
In this clip, we learn how to use the Nokia C5's various buttons and ports. The C5 is the first offering in Nokia's new "C" series of mobile phones. It runs on Nokia's Symbian OS and features a 2.2-inch screen and 3.2-megapixel camera. Want more? Search WonderHowTo's sizable collection of C5 video tutorials.

The key to being a good PvP (player vs player, or player versus player) character in World of Warcraft boils down to one thing: resilience. Here is how to be a good PvPer in WoW without turning into a griefer.

Even if you're just a new player, or a casual player, you can still earn this achievement. It's one of the first achievements in the Shadowfang Keep heroic on World of Warcraft. The key is in having a spare tank in your party.

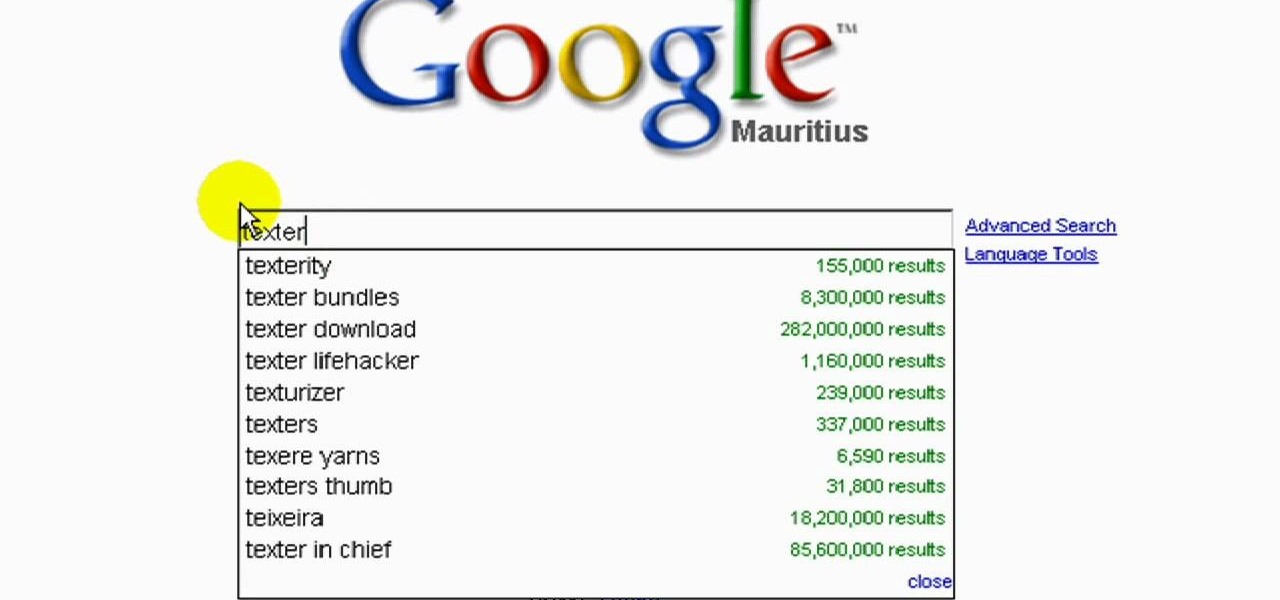
Speed is essential to being a successful programmer, and this tutorial shows you how you can easily and quickly double your coding output. The key is in a program called Texter, which you can easily download and install completely for free.

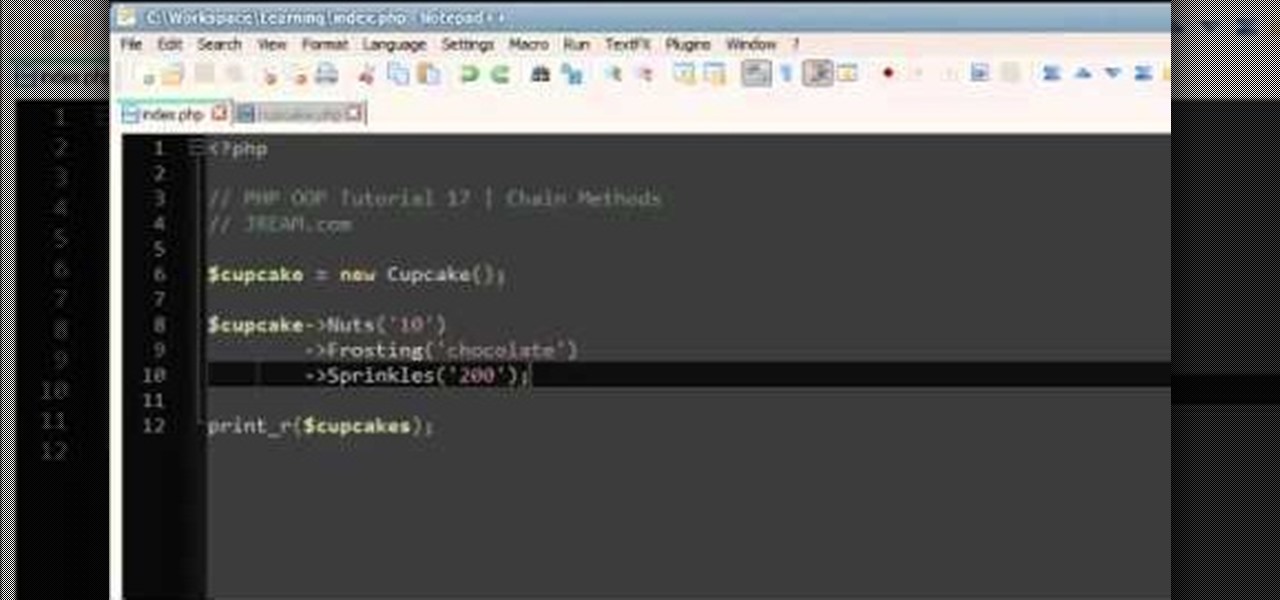
Chaining methods in PHP can be simple and straightforward if you follow along with this informative video tutorial on PHP OOP methods from JREAMdesign. The key action is to return the object after running the function so that you can run another function to the object directly afterwards.

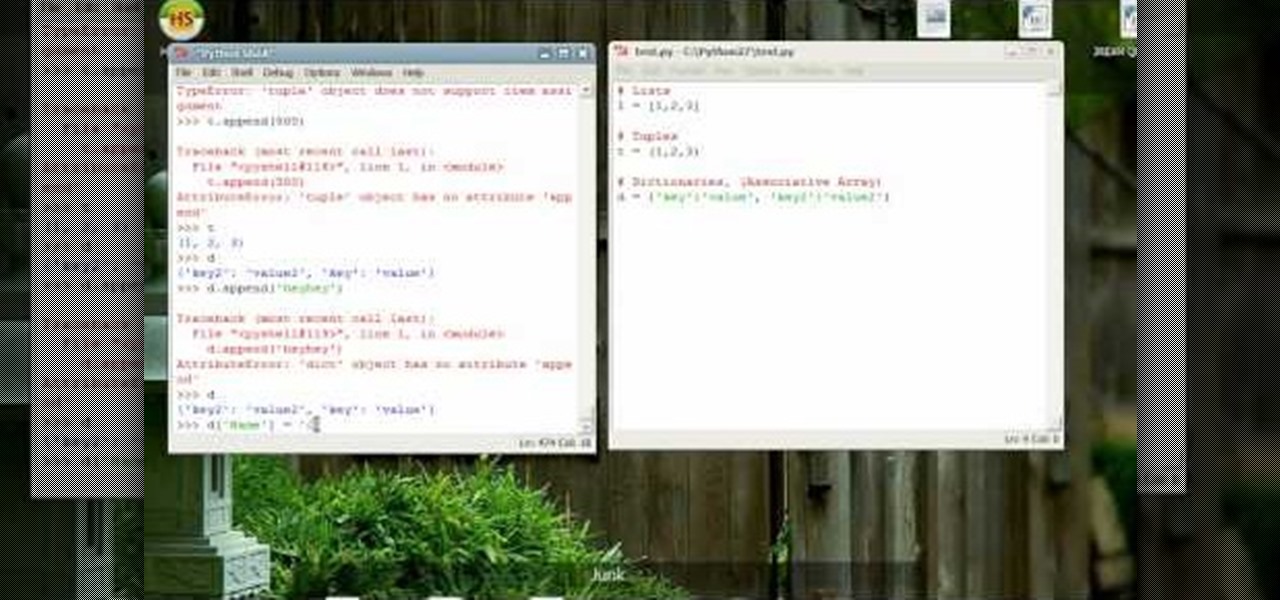
A tuple's value cannot be changed at all within your Python-based program, whereas a dictionary is more like an associative array where every item has a key and a value. Here is how you can use both tuples and dictionaries within your Python program.

You can use the FreeForm plugin to create the look of cloth blowing in the wind - like an animated ribbon, or a banner waving in the wind. The key is in designing the displacement map to get a truly realistic effect.

D minor may be the saddest chord ever, but where do you go from there? In this comphrensive lesson by Andrew Furmanczyk, you'll learn how to do minor to minor transposition to bump up your musical composition skills to a whole new level. If you can't sing it, or don't want to play it in the key the song is in, you need to watch this. Try it and make your sadness go to 11!

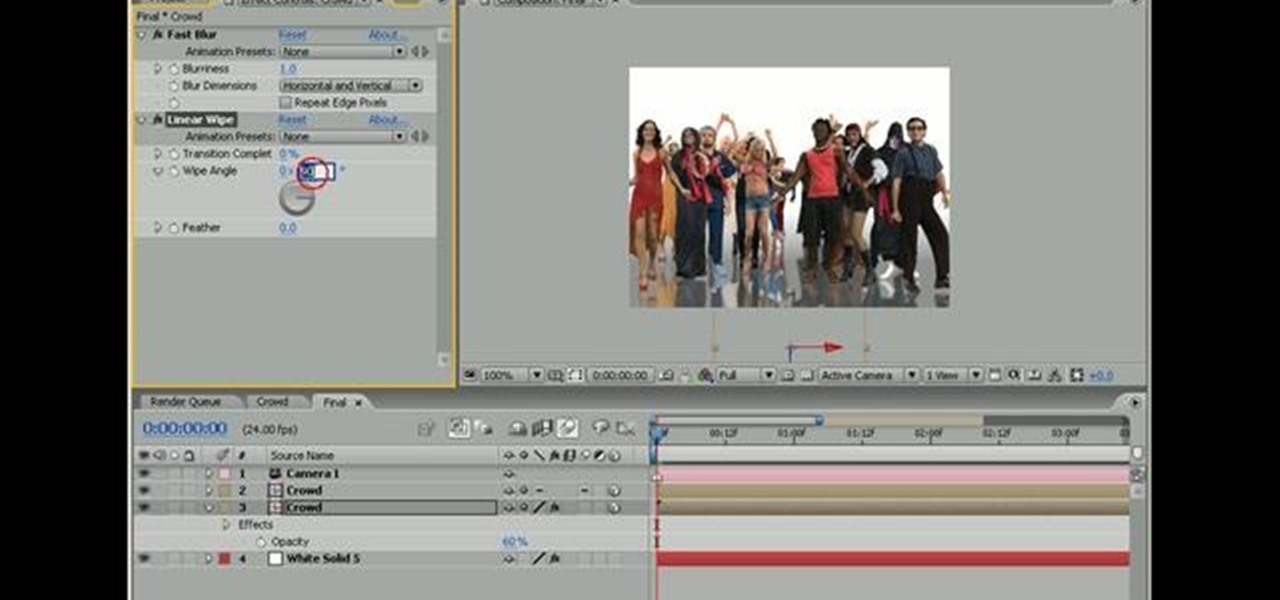
Create simple reflections in Adobe After Effects with keyed footage. In this video tutorial, Aharon Rabinowitz of All Bets Are Off demonstrates its use with video footage of both crowd and individuals. In addition, some potential issues with Collapse Transformations are also addressed.

Recently, China shut down access to Google in the country because their Propaganda Minister didn't like the results when he Googled himself. Since you probably can't do that, watch this video for tips on how you can keep information about yourself off of Google. The key: if you don't want it to be shared, don't put it online.

The less time you spending futzing with your mouse, the more time you can spend making music. Learn how to save time in Reason 5 with a number of useful keyboard shorcuts. Whether you're new to Propellerhead's virtual music studio application, Reason, or their newer DAW app, Record, you're sure to find much to take away from this brief, official video software tutorial.

You know all those t-shirts that you accumulate randomly? Like that XXL t-shirt you got from Subway during their holiday promotion, or that Key Club t-shirt you wore once and never touched again?