Minecraft is the surprise indie hit of 2010 and it's still only in Alpha! And one of the mainstays of the name, "mining" is a key element to not only survival but advancement in the game and the construction of bigger and better items, tools, armor, buildings, ect. If you're confused on how to find the materials, or maybe an effective way of actually creating a good mining tunnel, this video tutorial will guide you. You'll learn what types of materials you'll need, as well as what some of the...

Google loves their little Konami Code Easter eggs. The Konami Code is famous among gamers for letting you cheat in video games. The latest one they come up with lets you try it out on Google Docs. All you have to do is open up Google Docs, and type in with the following keys: up, up, down, down, left, right, left, right, B, A, and then enter!

Interested to know how many times you've clicked your mouse of the course of the past month? How many keys you've typed? This clip will show you how it's done. With WinOMeter, it's easy! So easy, in fact, that this handy home-computing how-to from the folks at Tekzilla can present a complete overview of the process in about two minutes' time. For more information, including detailed, step-by-step instructions, take a look.

When using Swype to send faster than life text messages on your mobile phone, you may need to capitalize something once in a while. Luckily, it is just as quick to add proper caps to your messages as it is to type out a super speedy text.

The Star Wars universe is vast and diverse, and for the Lego Star Wars-modeling enthusiast, knowing how to make the dizzying number of different types of figures from the series is key to creating accurate-looking scenes. This video features detailed instructions for making a shadow clone commando custom Lego minifigure. Complete your set!

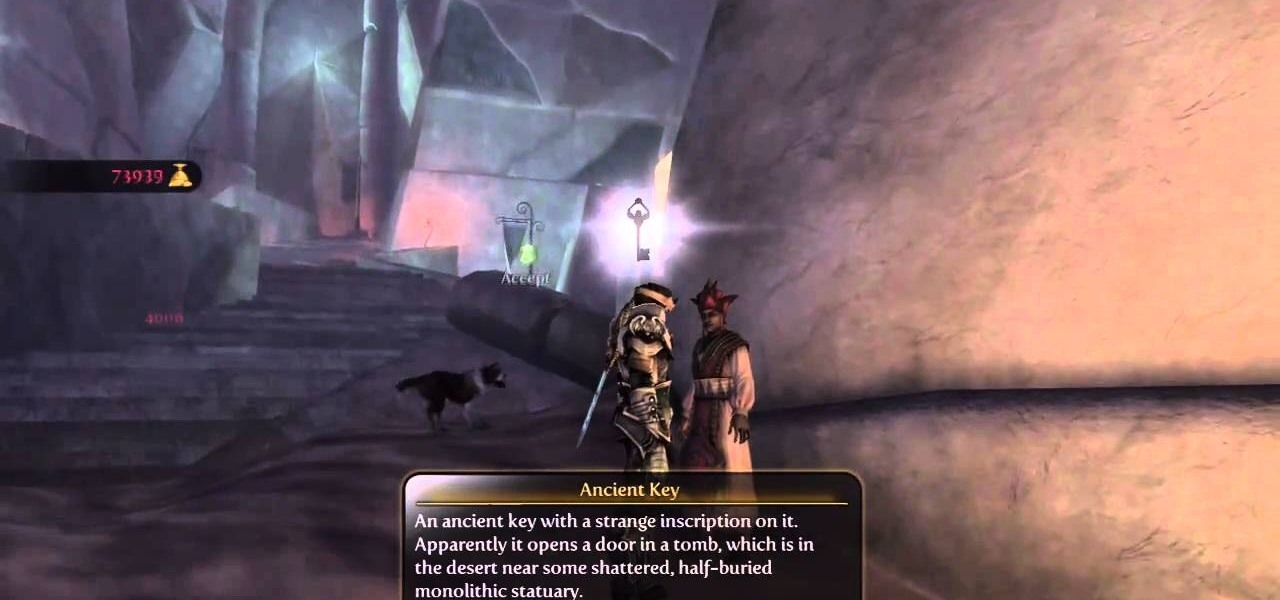
Ever wanted to learn how to make a rekey a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... key making. Just watch this video tutorial to see how to properly make a replacement key for a lock.

Michael talks through the coloring options for different types of hair pointing out that the darker the hair is the less color you can see of course, so it's key how you choose a color and how you use it when coloring dark hair.

This video explains how to add a bulleted or numbered list in Microsoft Word 2007. The shortcut to create a bullet-list is simple holding Shift and pressing the "A" key. After you hit the space bar or type a character the bullet will appear, and when you hit the Enter key it will continue the bulleted list. For numbering you just need to type the number you want and a dot after it and it should begin a numbered list. The list will continue if you press enter just like a bullet-list will. If y...

In this ten-step video tutorial, you'll learn how to quickly copy keys using a camera, printer and Dremel tool. With this ten-step process you'll learn the necessary steps to copy almost any key... even if you only have access to it for a brief period of time.

Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good.

Today, learn the basics of lock bumping. Lock bumping is a lock picking technique for opening a pin tumbler lock using a specially-crafted bump key. One bump key will work for all locks of the same type.

The Sanctuary menu system in Fable 3 has spawned some controversy, but it's pretty novel when you consider that there are a hidden Gold Chest and Gold Key right there in your pause menu! Watch this video to learn how to unlock and find the Gold Key and then the Gold Chest in your sanctuary.

The Gold Keys in Fable 3 are needed for unlocking all sorts of fun legendary weapons and such, but finding them all is appropriately challenging. If the tedium of searching for them has gotten to you, watch this video to learn where to find and unlock each and every one of the gold keys.

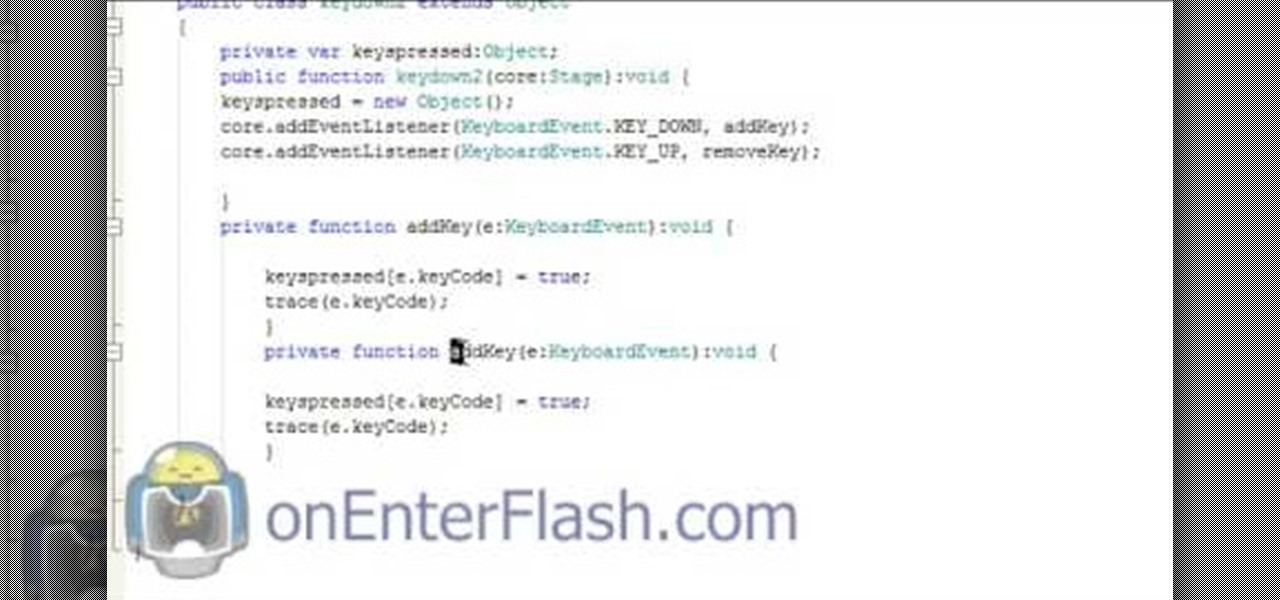
Flash Actionscript 3 is a wonderfully powerful, but somewhat obtuse, tool for creating websites. This video will teach you how to use one particular function in the language, creating a class that has multiple key detection enabled. This will allow you to create a website where users can key in multiple inputs and the website will respond appropriately.

A bump key is a method crooks use to pick locks. This idea is not new, professional theives have been using it for years, and now you can make your own.

Looking to up the ante in the home secuirty department? If you are concerned about the safety of your family and home, consider purchasing a burglar alarm system by following these helpful tips.

Want to play Canned Heat's "On the Road Again" but your harmonica's in the wrong key? No problem: in this elaborate instructional video you'll learn how to tune your harmonica to the key of A by raising the pitch in draw hole 6. And remember: before attempting to adjust the tuning on your favorite harp, it might be wise to practice pitch adjustments on an old, used, broken or cheap harmonica.

Woodturning is creating items out of wood on a lathe. Learn how to create key chains and light pulls from a woodturning expert in this free crafts video series.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

One of the biggest hurdles for making touchscreen text input easy on the user has been finding a simple way to move the cursor around. With all the advancements in mobile technology, we're still left fumbling around with tiny arrow indicators or magnifying glasses when we need to add a letter to a word we've already typed. But thankfully, developer Ouadban Youssef has found a better way.

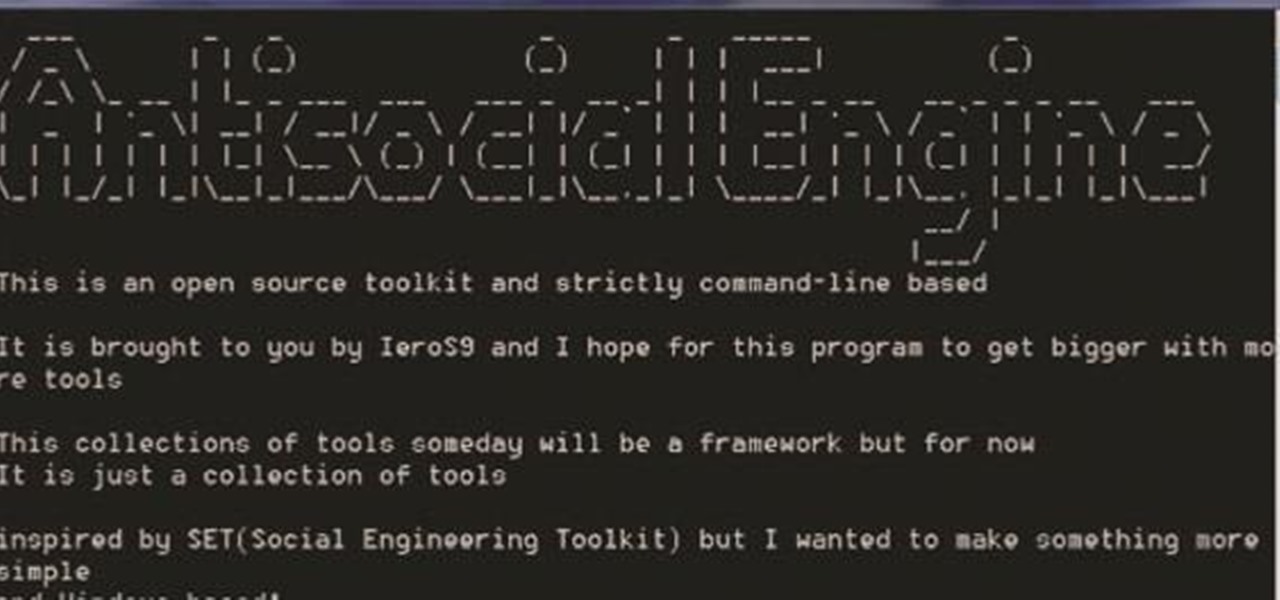
Hello there Nullbyte users! This will be my first article here.

A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

If your PC setup includes a mouse and keyboard, you'll be happy to know that most of the touchscreen-first features of Windows 8 have gone by the wayside in Windows 10. Where it once required awkward gestures to access key features, Windows now recognizes when you're using a traditional desktop or laptop, then responds by making sure that all features can be easily discovered with clickable buttons and menu entries.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

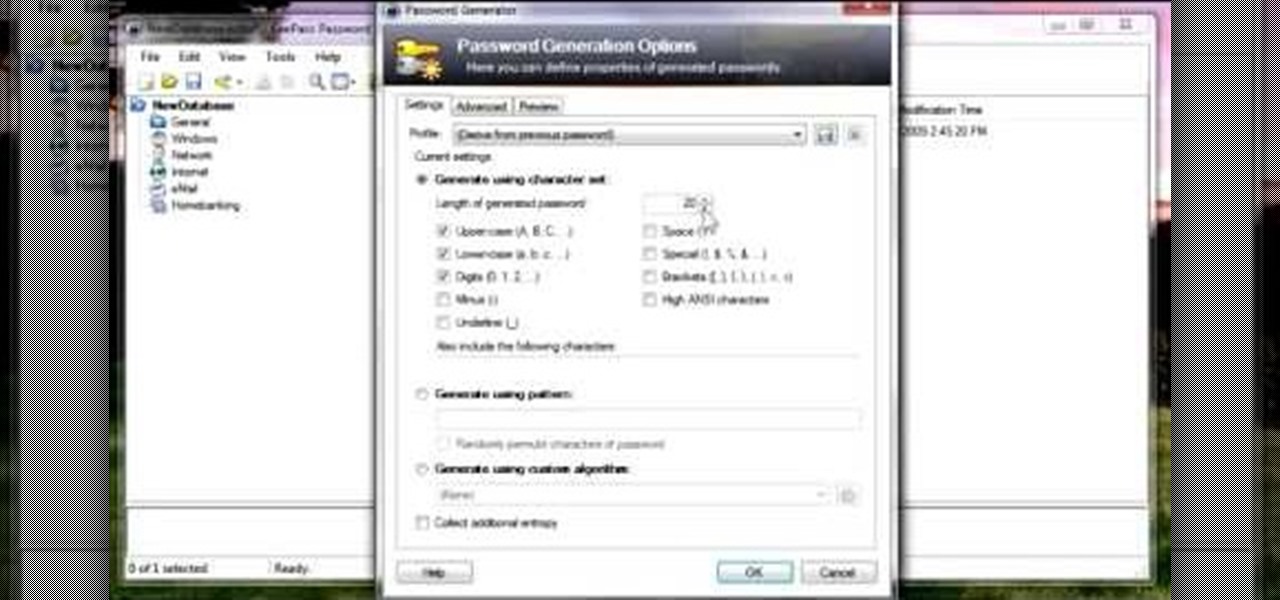
In this video, we learn how to use KeePass password generator. First, open the entry to edit the existing password and type in your username and e-mail address. Type in notes if you need it, then click on the bottom key icon. This will generate a password for you when you click on it and cover it up. If you click it once more, it will uncover what the password is. You can decide what kind of password you want and make one specific for the account you're using. When finished, you will have a n...

This walk-through video tutorial shows you how to find out your IP address for XBox live. First press the start button and search for run as shown, click the result, bring up the dialog and type in the given command to open the command prompt window. Type the command in the given window and hit enter. The number that appears is your IP address, use it as the key for XBox Live. In the case of XBox 360, it automatically detects it.

In this video tutorial, viewers learn how to dress to flatter their body shape. The female body has three key physical inflection points. These points are: the chest, waist and hips. There are four basic body types. These body types are: apple, pear, hourglass and banana. The apple shape has a full face, broader shoulders, fuller breasts, undefined waist, narrow hips, flat rear ends ans shapely legs. The pear shape has slender neck, narrow shoulders, narrow back, small or medium bust, defined...

In this video tutorial, viewers learn how to use the Sticky Keys feature in a Mac OS X computer. The Sticky Keys feature is found in the Keyboard tab in the Universal Access menu. To turn on the sticky keys, check the On option. Underneath, users are able to set some options for how the modifier keys are treated. Sticky Keys will allow users to press the keys in a sequence, instead of all at once. This video will benefit those viewers who use a Mac computer and would like to learn how to conf...

Any dope can play “Heart and Soul.” Now you can be one of them. Use your pointer finger to hit the 2nd F key up from the middle C briskly three times, then hit it once more before moving down to play keys E, then D, then F three times, briskly. Then F once more, before bouncing down and playing keys E then D.

Always losing your keys? A big bulky key chain might feel annoying in your pocket, but it's not likely to get lost in your purse or in all that trash you carry around. This video tutorial shows a real simple key chain ring you can make and keep those keys easy to find. All you need is the key ring, two shoelaces, a pair of scissors, and a lighter.

Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a few useful tips.

Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open.

In this video tutorial, viewers learn how to use the Slow Keys access tool in a Mac OS X computer. The Slow Keys feature is located under the Keyboard tab in the Universal Access window. Once Slow Keys is turned on, users also have the option of using key click sounds as additional feedback when a key is pressed . Users are able to set the Acceptance Delay to determine how this feature behaves. The delay of the sound can be set from long to short. This video will benefit those viewers who use...

In this video tutorial, viewers learn how to use the Sticky Keys feature in Microsoft Windows 7. To use the Sticky Keys, click on the Start menu and open Control Panel. In the Control Panel window, double-click on Ease of Access and click on Change how your keyboard works under the Ease of Access Center. Then click on Set up Stick Keys and check the option Turn on Sticky Keys. This video will benefit those viewers who have limited dexterity and find it difficult to use complex keyboard shortc...

In this video tutorial, viewers learn how to use the Filter Key features on a Windows 7 computer. Begin by opening Control Panel and select Ease of Access. Under the Ease of Access Center, click on Change how your keyboard works and click on Set up Filter Keys, at the bottom of the window. Now check the box beside Turn on Filter Keys. Users are provided with several options for he Filter Keys such as: turn off the Filter key wen Shift is held or 8 seconds, display a warning message when turni...

When picking a padlock, the only part you need to worry about is the part where the key goes into the lock. The locking mechanism has pins attached to springs. The key pins are on the bottom and the driver pins are on the top. The key turns when the pins of different heights are separated, flush and aligned. Stick a tension wrench into the keyway and put pressure on it. Take a pick to push the rest of the pins up until they are flush with the shear line. Stick the tension wrench into the bott...

In this video, we learn how to find your Windows product key. Start off by going to Magical Jellybean Keyfinder. This website has a download that will find your product key for your Windows program. This is a great and necessary tool if you happened to loose the product key that came with your computer. This is also great for computers that already had Windows installed, and you never had the product key in the first place. Once you install this on your computer, you just open it up on your d...

In this how-to video, you will learn how to do the adult Blatt call. This call is made by an adult deer about 18 months old. There are many types of Blatt calls. The Estrus Blatt is the most effective in getting a Buck to respond. The key is to keep the call short. This call will be made by a Doe when in peak heat and looking for attention from a Buck. Turn the calling device quickly. This will be done several times in a row. Do not make a loud alarm Blatt. Keep it short. This video gives you...