
How To: Make a Mai Tai with almond liqueur
Get ready to learn how to make this classic beachside rum beverage, the Mai Tai. The key to this big liquor, big flavor drink? You need to use almond liqueur.


Get ready to learn how to make this classic beachside rum beverage, the Mai Tai. The key to this big liquor, big flavor drink? You need to use almond liqueur.

Need to make your house more burglar proof? Here are some easy instructions on installing a deadbolt. This lock also is equipped with a key entry.
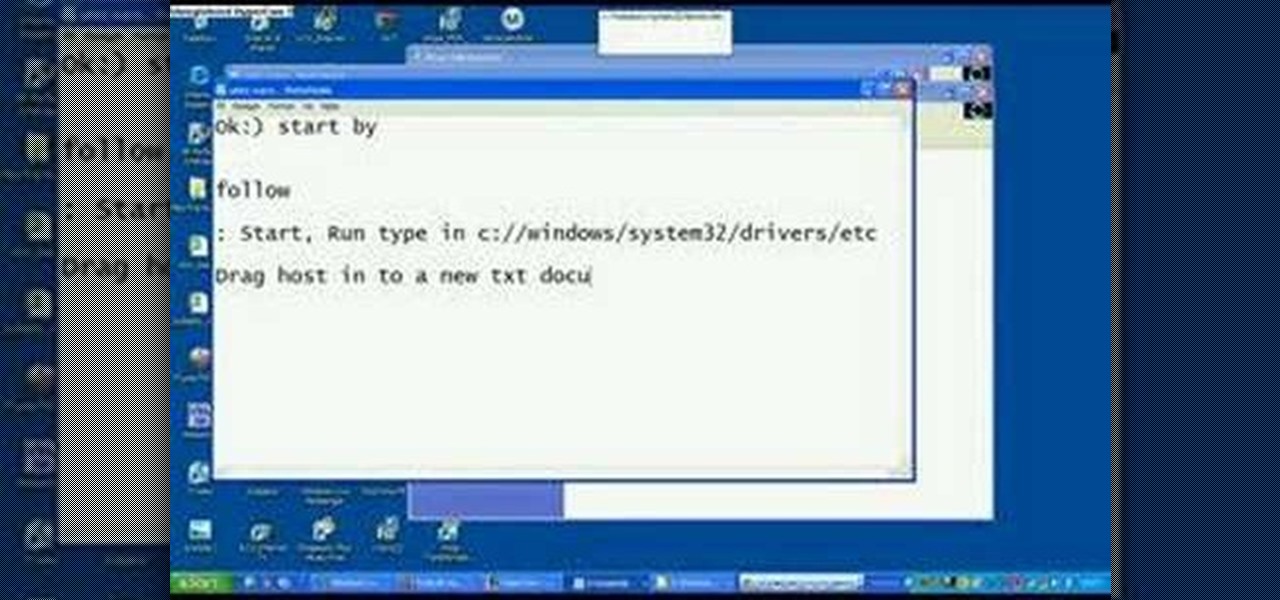
In this tutorial, we learn how to block a website. First, you will start by going to the start menu then go to "run". After this, type in "c://windows/system32.drivers/etc". After this, a new window will pop up on your screen. With this, you will drag the host into a text document. Then, type in the website that you want to block inside of this document. Once you are finished, type in the IP address of your computer next to that and save it. This will finish up the blocking of the website and...
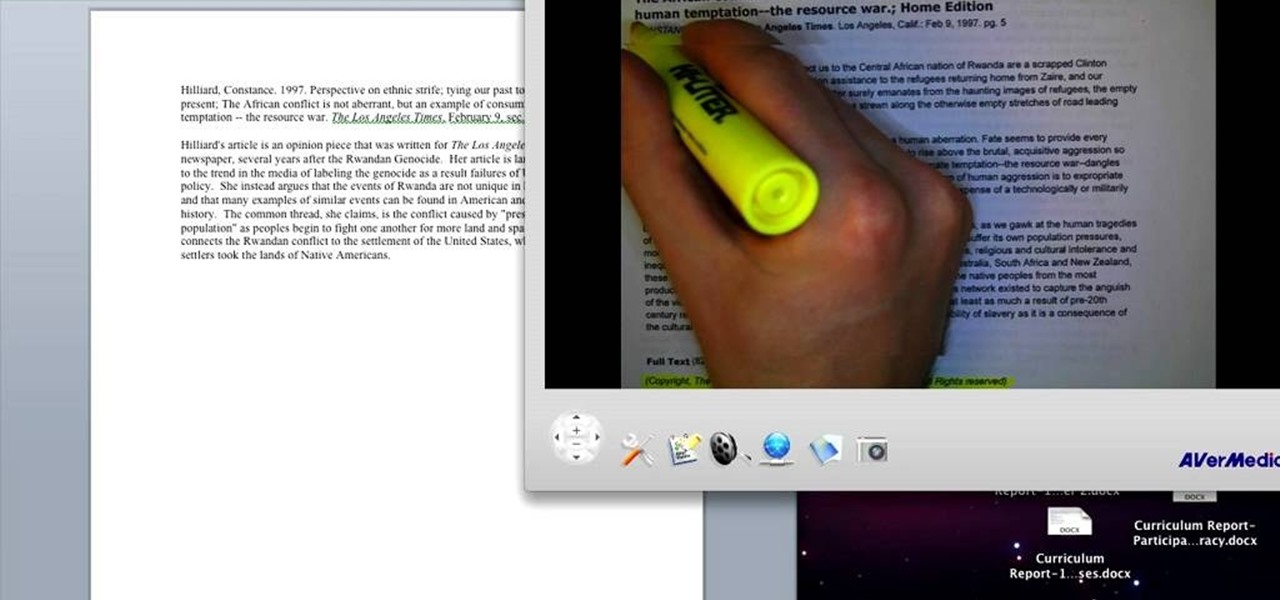
In this tutorial, we learn how to create an annotated bibliography. Make sure to highlight all your citation information, then type it into your bibliography page. After you have it written down, type it out again in the proper citation format, making sure you use the proper type. Make sure you have all the proper information, and you don't forget any of the crucial information. An annotated bibliography is different because it will give a summary underneath the citation. This is only about f...
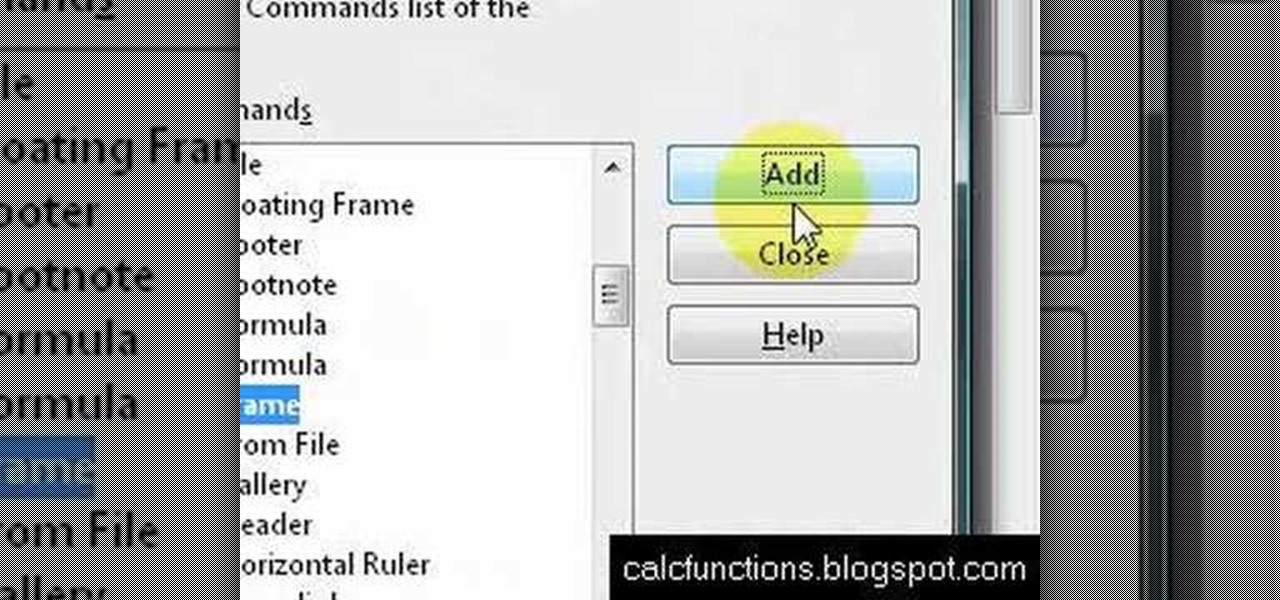
In this Software video tutorial you will type math equations in Open Office Writer. Double click and open up the writer. First you got to add a button to the toolbar. For this, click on the arrow at the end of the toolbar and select 'customize toolbar'. On the window that pops up, click on 'add'. Then highlight 'insert' (on left hand side) and 'formula' (on the right hand side) and then click add > close > OK. You can now see the formula button on the toolbar. To add a mathematical equation t...

With feminine florals being one of the hottest spring and summer trends, it's often recommended by the fashion elite - including Tim Gunn - that more masculine elements be included in your outfits to balance out floral girliness.
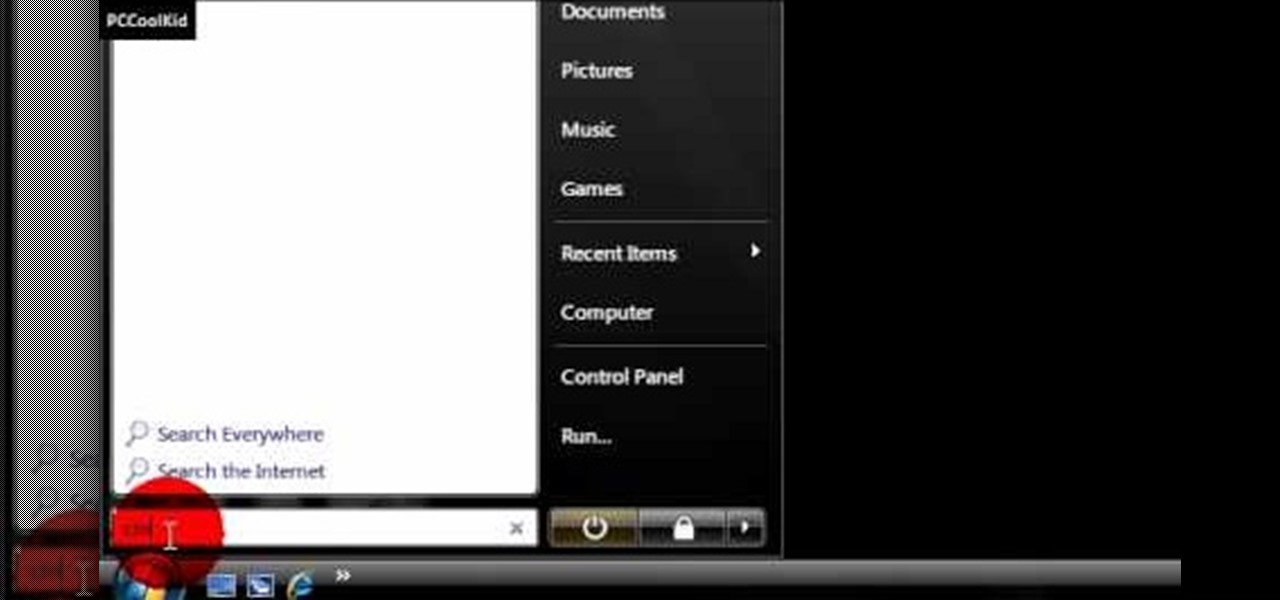
In this video, we learn how to enable the Windows default administrator account to appear at the log in screen. First, go to your "start" menu and type in "cmd". Right click "cmd" and click "run as administrator". Now click continue and type in "net user administrator /active:yes", (making sure you put the appropriate spaces), and press enter. Now it will say your command was done successfully on the space underneath where you just typed your text. When you restart your computer you will now ...

This tutorial by the Floral Design Institute demonstrates how to create a hand-tied Calla bridal bouquet. The key to creating this bouquet is to make sure your flowers are properly prepared. The flowers should be fully hydrated (in water for at least two hours). Take each flower and mold each stem to to reflect the natural curve of the flower. Lay them side by side so they are lined up in a parallel fashion. Give even pressure on the stem to prevent bends or kinks. Some stems may be straight ...
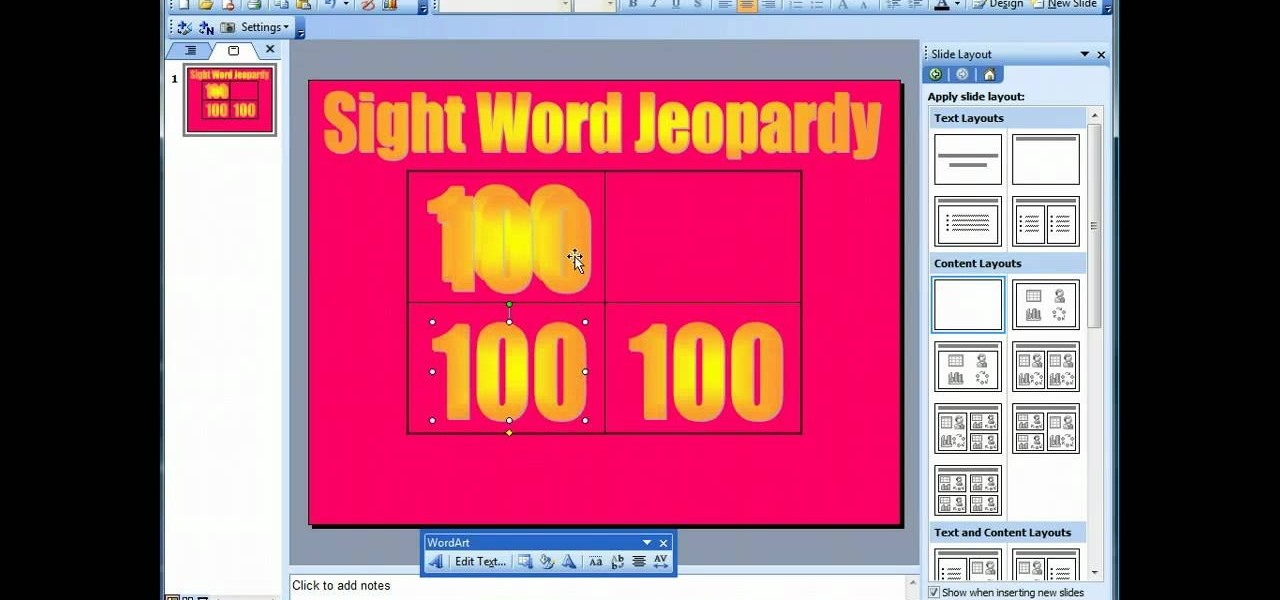
This video demonstrates how to make a basic Jeopardy game in Microsoft PowerPoint. First, choose a background color by clicking Format on the top bar menu. Select Background and choose the color you wish to have. Click Apply To All to apply it to your entire PowerPoint presentation. Then, click Insert on the top bar menu and select Table. Fill in the number of columns or rows you wish to have for your table and then click OK. In this example, create a 2x2 table. Make a title for your game by ...
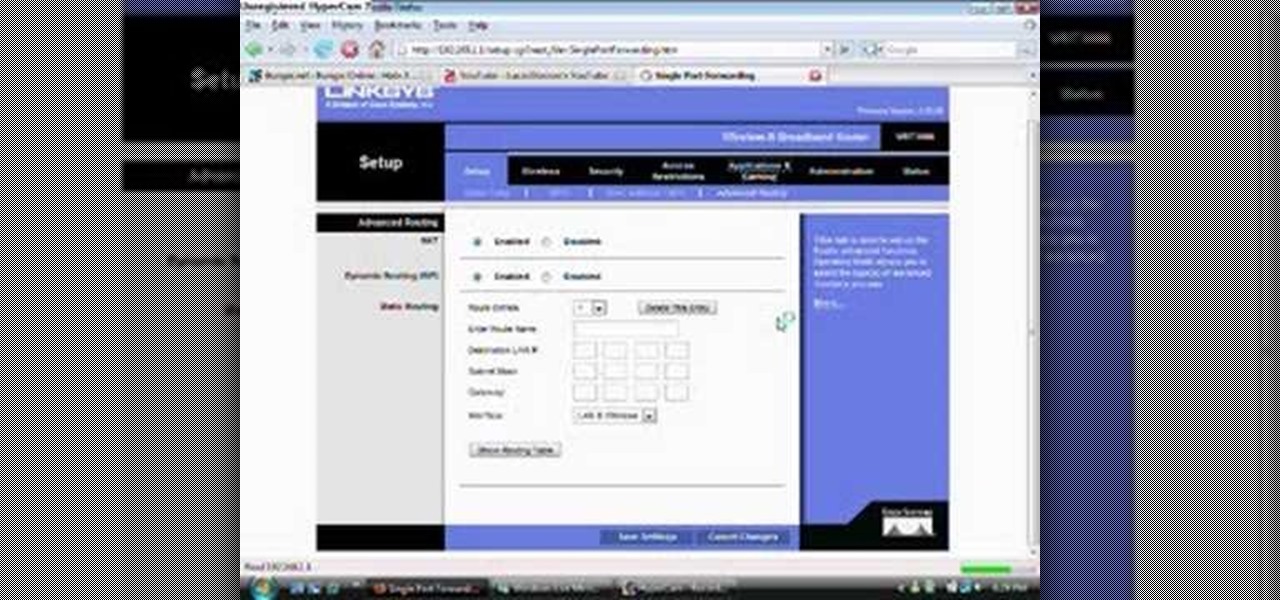
Need to change the NAT type on your wireless Linksys router to play games over the Internet on Xbox Live? Boy and/or girl, have you ever come to the right place. This home networking how-to will get you up & gaming in no time flat.
FROMAN1115 teaches you how to change your NAT type to Open on your PlayStation 3. On the PlayStation 3, go to Settings-Network Settings-Settings and Connection Status List and write down your IP. Go to your PC and start your internet browser. Type in 192.168.1.1. This will bring up the router settings page. Go to Applications and games and then DMZ. Check the first box that says Enabled. Enter your IP address below and click ok. Your settings have been saved and you can enter a new internet m...

Blip TV user Mr. Root teaches you how to mount an ISO image file using the Unbent Linux terminal. To do this and have access to the files inside of an ISO, without unarchived it, start the terminal. Type in dirk CD. Make sure the ISO image is on your desktop. Then type in sud o mount -o loop -t iso9660 and then the name of your image file, followed by CD/. This will create a new disk drive, which can be seen on the desktop. You can explore that disc like a real one. To unmounted your image, s...
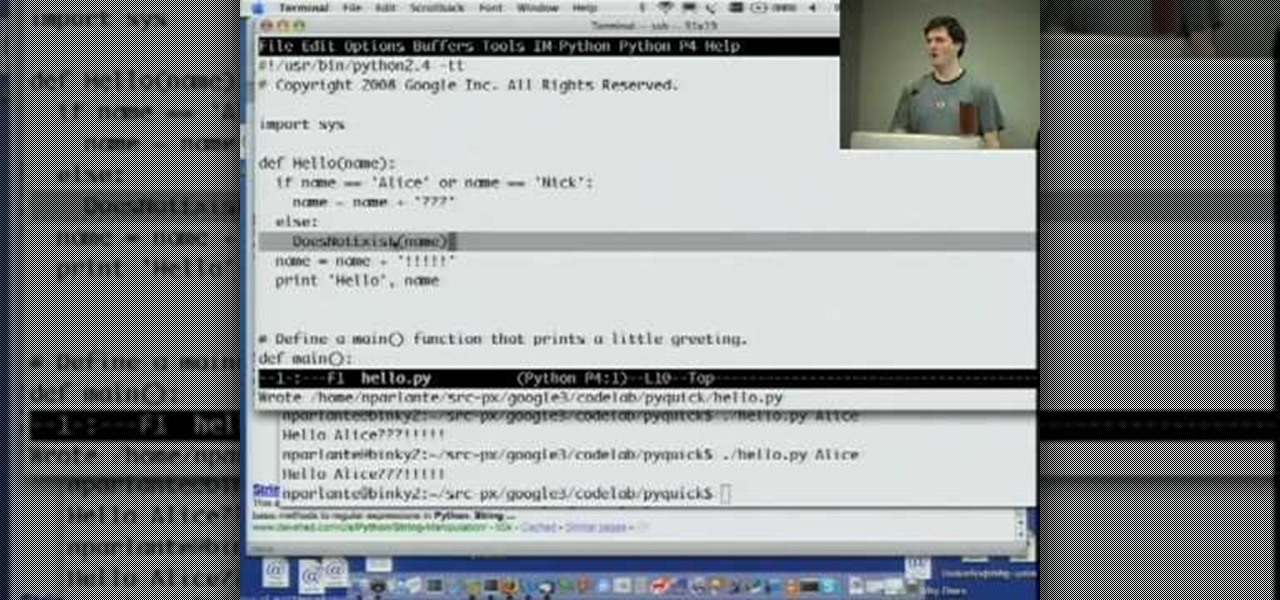
Welcome to Google's Python Class – a seven-segment, two-part free virtual class for people with a little bit of programming experience who want to learn Python. The class includes written materials, lecture videos, and lots of code exercises to practice Python coding. The first exercises work on basic Python concepts like strings and lists, building up to the later exercises which are full programs dealing with text files, processes, and http connections. The class is geared for people who ha...
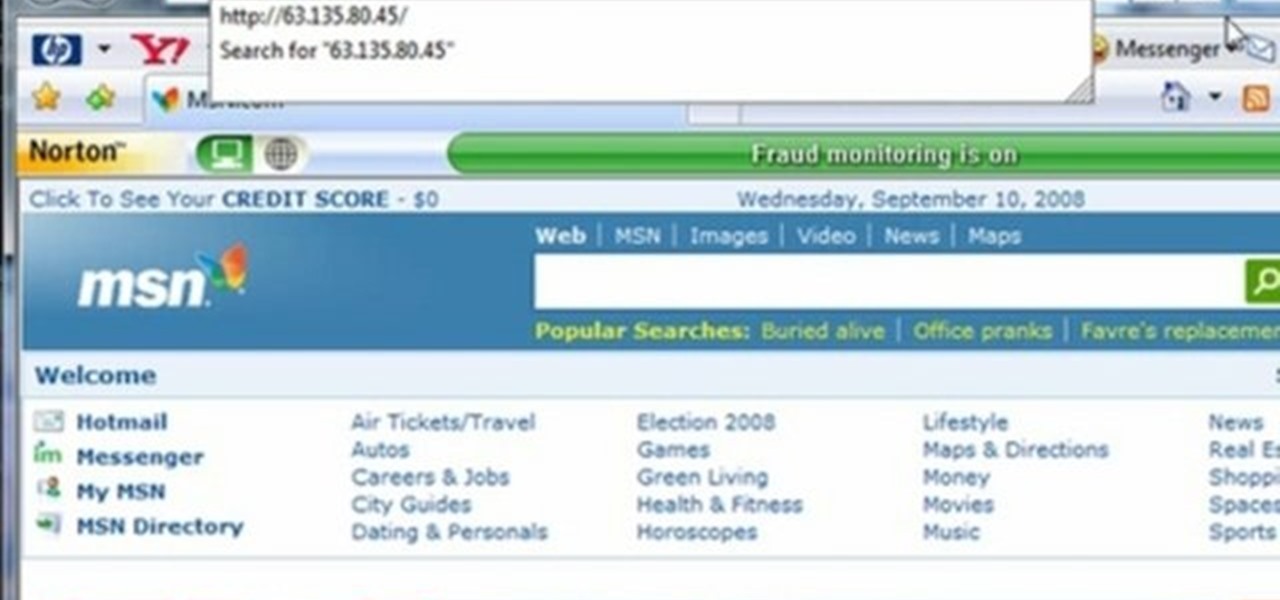
This video tutorial gives you a way to access websites that you can not normally access because of a web block or filter. What you need to do is click on the ‘Start’ button and then click on ‘Run’. In the small window, type in ‘cmd.exe’; this then opens a black window. Then type in ‘ping’ and the website; this gives you an address that you type in directly to your web browser, granting you access to a normally blocked website. This comes in very handy when you are in such locations like schoo...
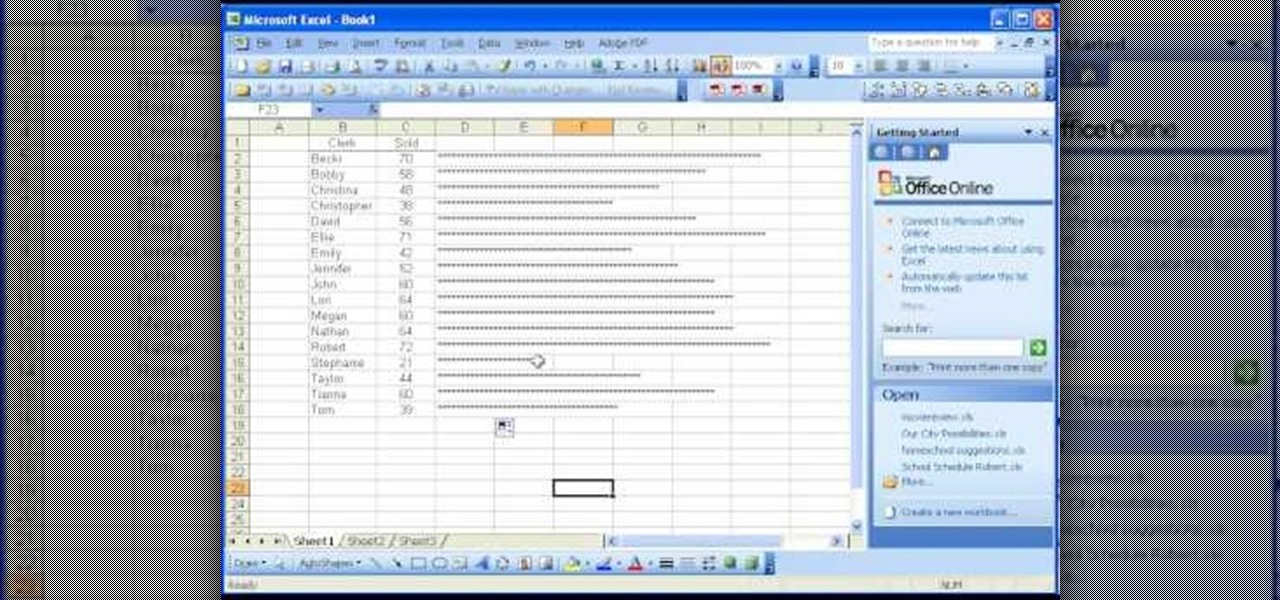
There are many functions in Microsoft Excel. One function that people rarely use is the Repeat function or REPT. In this video, an example used is a chart of people and their sales of a certain item. Just looking at the numbers, it is hard to compare the different sales easily, but a more visual approach may work better. Next to one of the cells, type in "=REPT(" which is the repeat function. A popup should say "=REPT(text, numbertimes)". For "text", type in *** or anything, really. For "numb...

Master your tennis serve progressions. Be sure to click on all the video chapters to view the entire tutorial.

Tim Carter discusses the different types of wood and how they are recognized and how their attributes are utilized. Informative video will help to make sure you use the proper wood for your build.

There are two main types of shafts for horse dawn carriages, U-Shaped fixed shafts and independent shafts. watch this video to learn how they work.
Managing Panoramas (henceforth known as panos) and HDR photos in Lightroom is an important step in making your life a lot easier if you like that type of photography. What happens after shooting a lot of either type of photography is that your library becomes really cluttered. As if the clutter wasn’t bad enough, it just becomes flat-out difficult to start processing these types of photos. So instead of ditching Lightroom when you shoot at pano or HDR set, check out this week’s video and give...

This is a tutorial on how to edit type in a layered file and a flattened file in Photoshop.

From pirates to playboys to Village People, there are as many types of mustaches as there are types of men—but all of them need a good trim every once in a while.
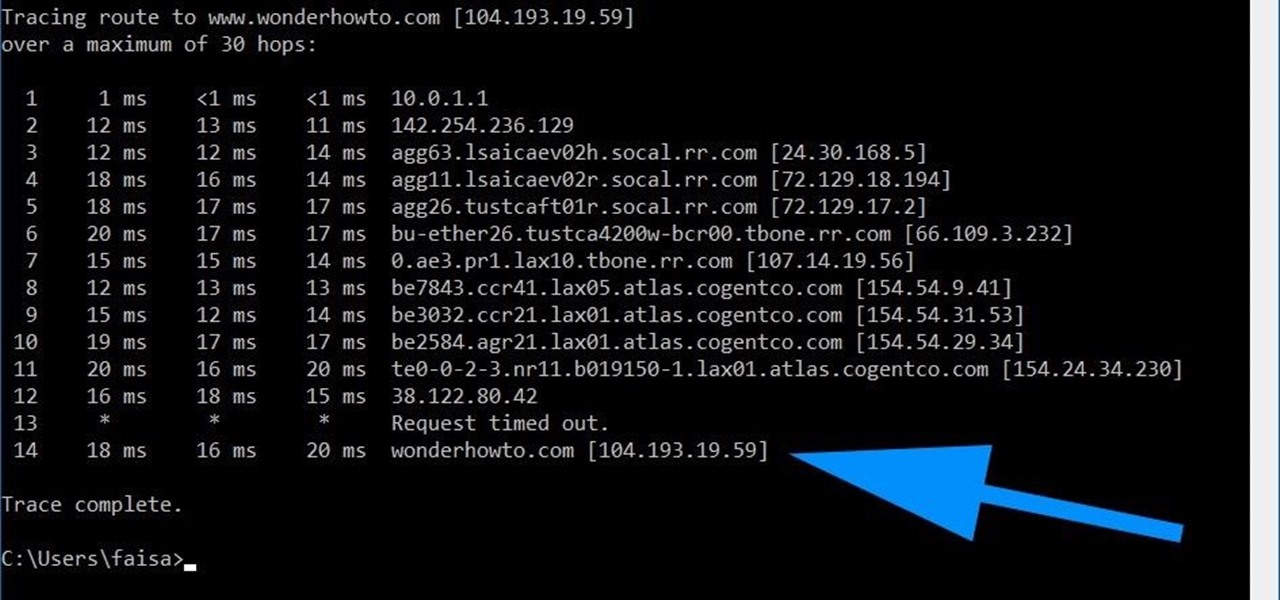
Using a simple trace trick, you can easily look up the IP address and its location for any website. This method uses a command line command to first find the IP address of a given website, and then uses a free online tool to get that IP's location.

Apple's stock keyboard for iPhone has gone through many changes over the years. Some have been significant, and others more subtle. Overall, most of these updates have been fairly obvious, so you're probably already using them — but there are more than a few interesting features that were slipped in under the radar that you may not know about.

If you're using the default Samsung Keyboard on a Samsung Galaxy smartphone or Gboard on a Google Pixel or any other Android device, here's a cool trick you should know about.
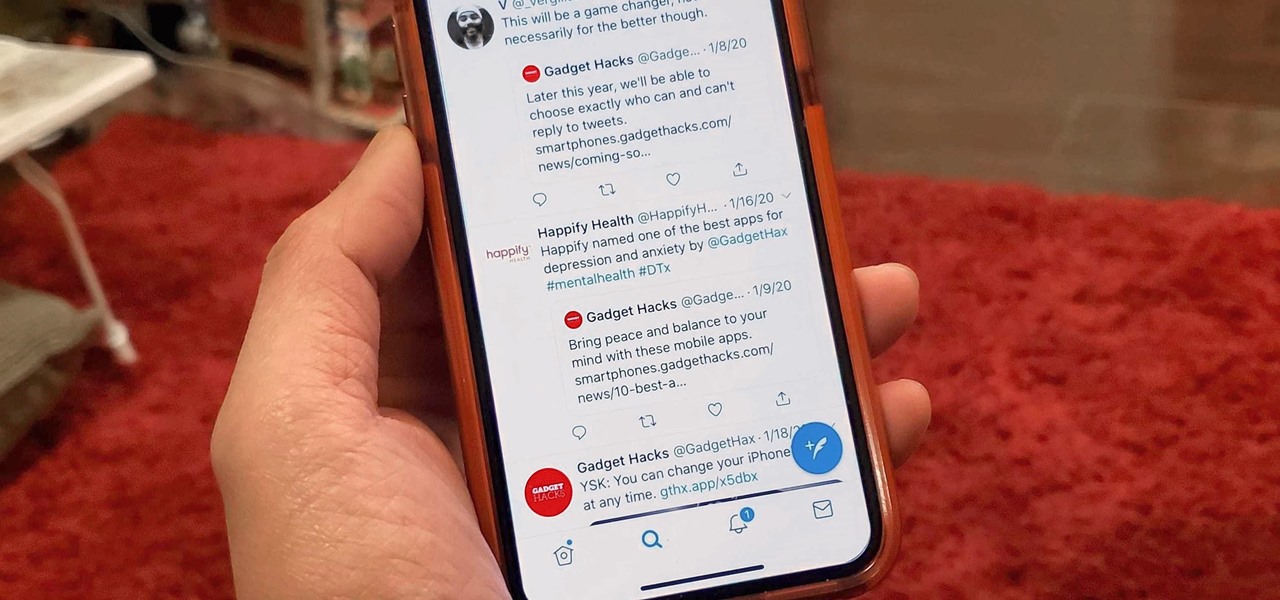
If there's an influential tweet, you can see what people are saying about it by reading its comment thread. But what about quote tweets, aka tweets someone posted on their own timeline that quote the initial tweet? These don't show up in comment threads, but there is a way to find them.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.
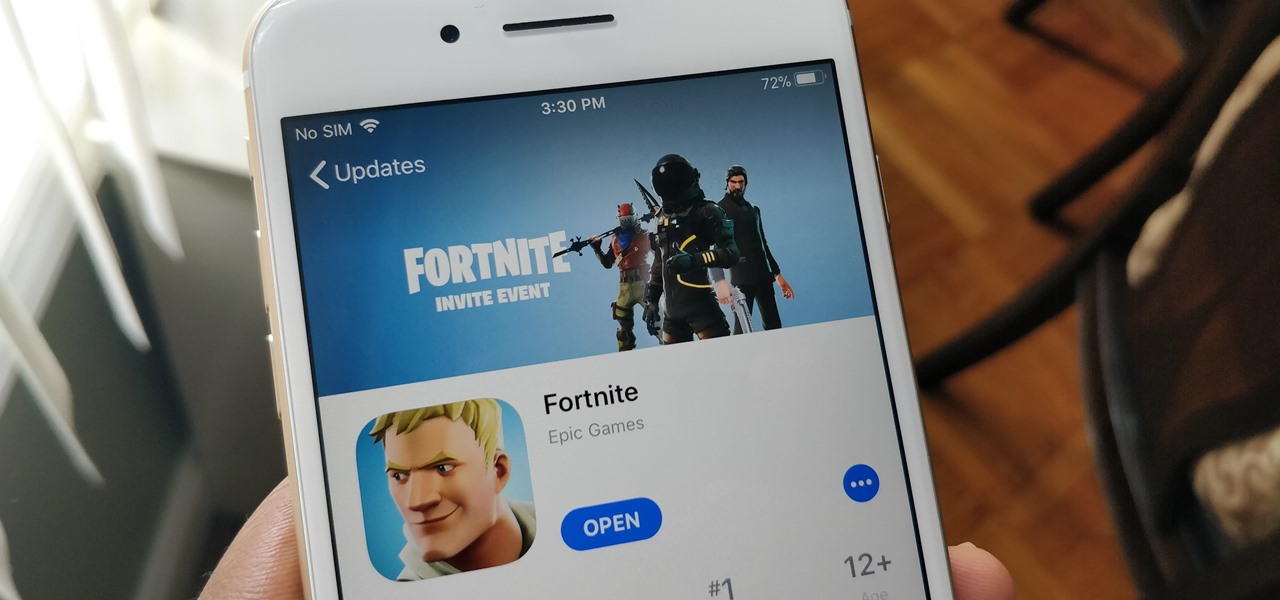
If you're a console or PC gamer, you may be quick to ignore the mobile version of Fortnite Battle Royale. The lower graphics and the switch to touchscreen controls may be enough reason to dismiss this version of the game. But don't be so quick to judge — there are actually some clear advantages to playing on mobile.
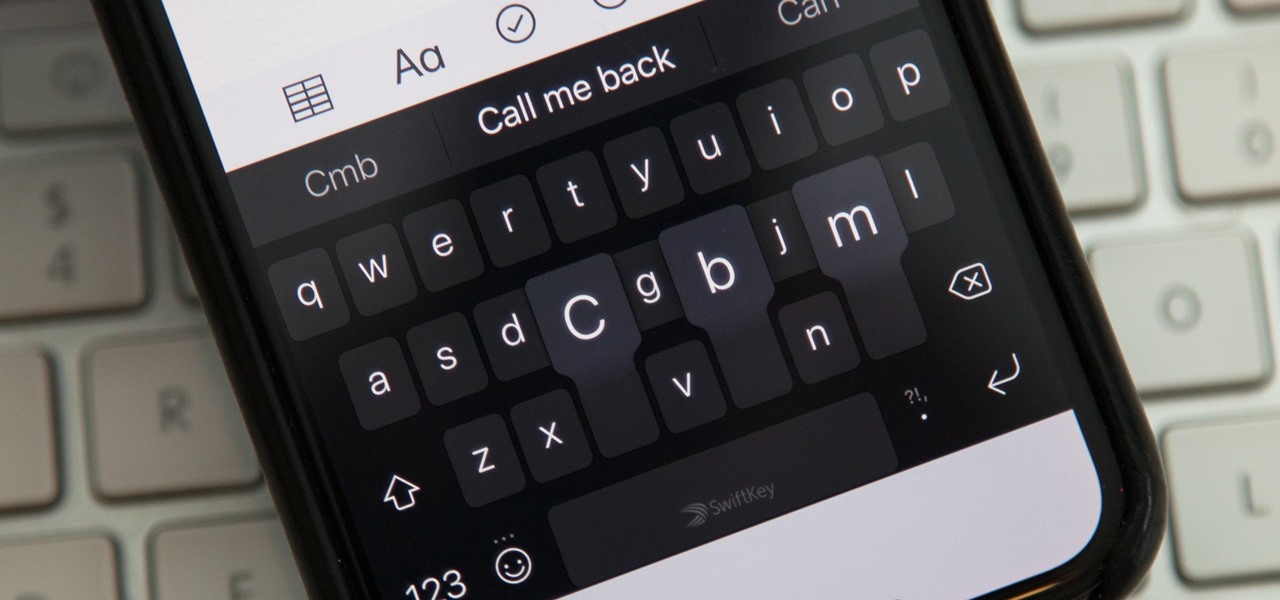
While you're probably already used to the keyboard on your iPhone, you'll likely never be able to type on it as fast as you can on a computer keyboard. But that doesn't mean you can't get any faster at typing on your iPhone. By using keyboard shortcuts to auto-populate commonly used phrases, email addresses, and other big-character items, you can drastically speed up your virtual keyboard skills.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.
Speakers have been an integral part of smartphones since the beginning. Razer's concept Project Linda even uses the speakers from the Razer Phone to power the faux laptop's audio system. But what if Google's next Pixel phone didn't even have speakers? What if it didn't need them in the first place?

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

With the raw, visceral feeling of zooming around on the open road, it's easy to get carried away when you're out for a ride on your chopper, super bike, or scooter. This increases your chances of getting lost, plus routes can differ slightly for motorcyclists and cagers, unbeknownst to most drivers. Luckily, Waze has rolled out a feature that caters specifically to bikers.
It's an ongoing saga, and it's on the verge of ruining one of the most anticipated smartphone releases this year: LG's new POLED displays certainly seem to have a few issues. But the biggest issue of them all — an apparent susceptibility to screen burn-in — may not be the problem we thought it was.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.
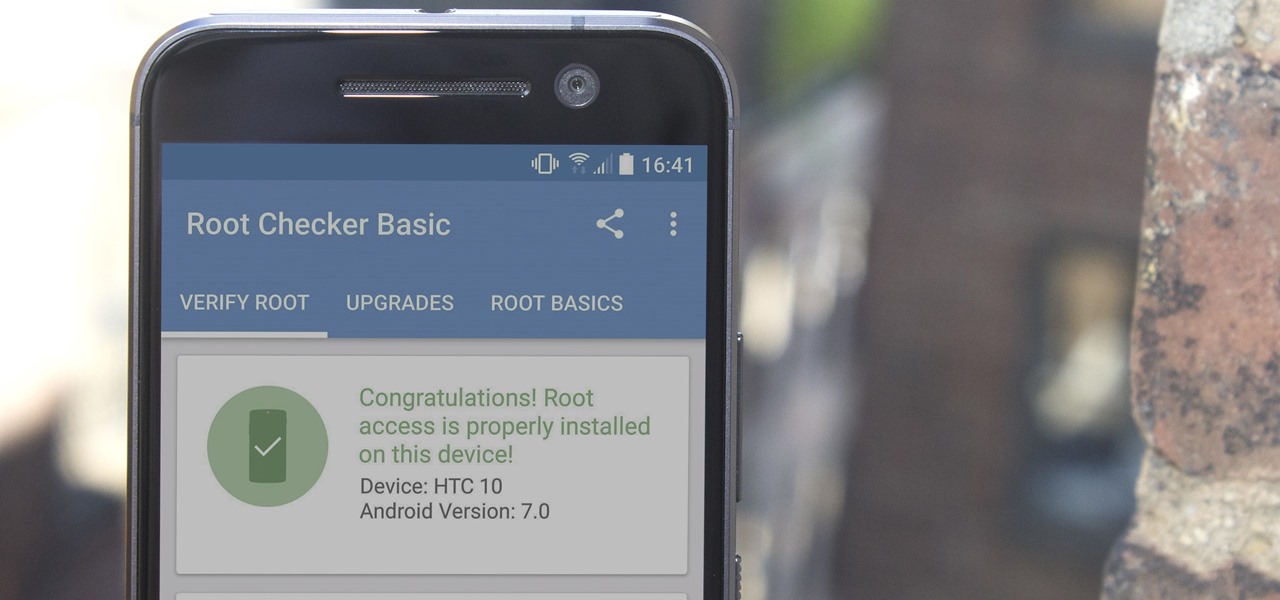
There are many great reasons to root your phone, but if you're not experienced with tools like ADB and Fastboot, it can seem like a daunting task. Fret not, because if you want to root your HTC 10, we're here to walk you through the process.
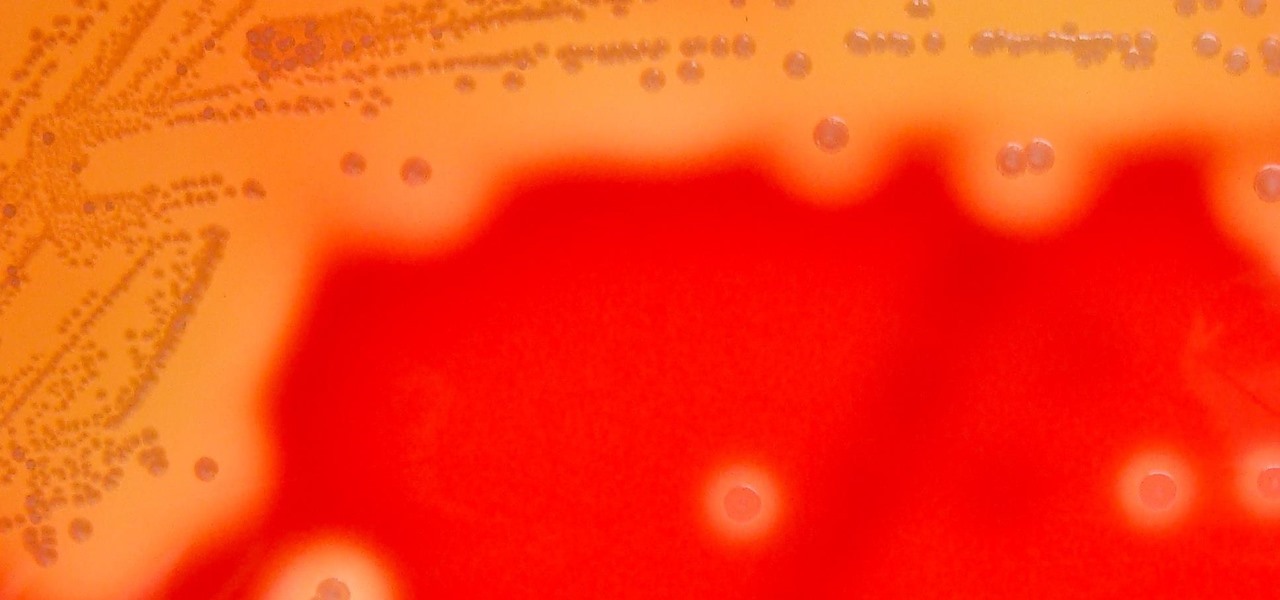
Streptococcus and staphylococcus bacteria produce toxins that can cause toxic shock syndrome.
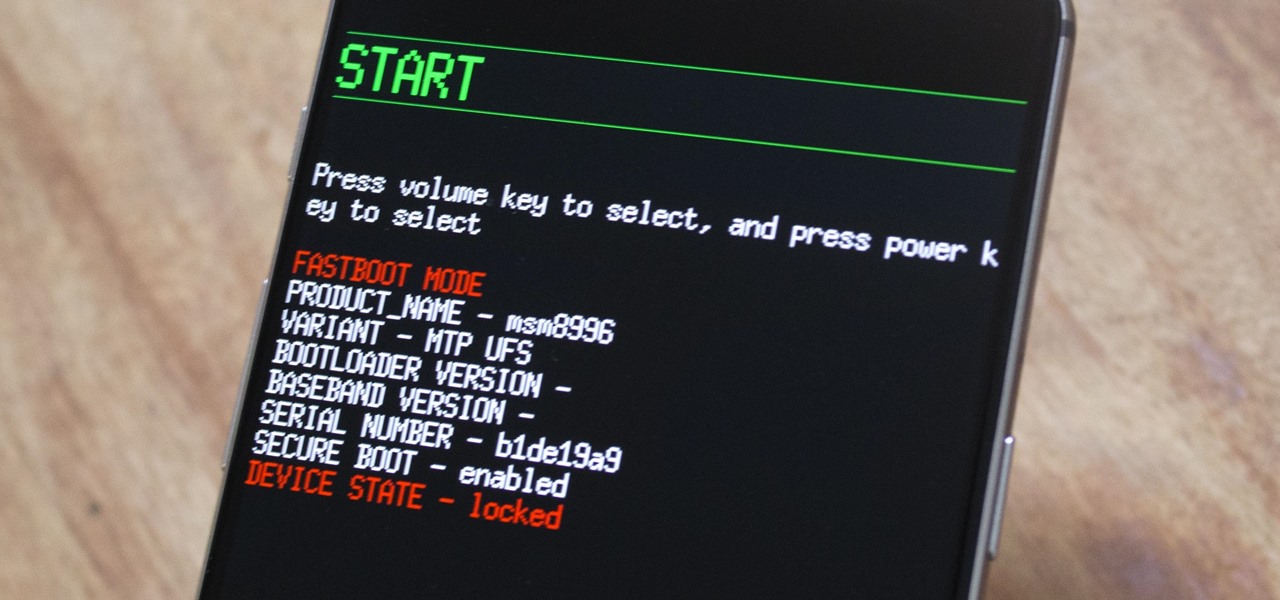
The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.