
How To: Unlock Haptic Feedback on Your iPhone's Keyboard to Feel Everything You Type
While Apple has included a vibration motor in the iPhone since the beginning, it's never let us use it for haptic feedback on its default keyboard — until now.


While Apple has included a vibration motor in the iPhone since the beginning, it's never let us use it for haptic feedback on its default keyboard — until now.

You're in a Zoom meeting, and you're click-clacking away at your keyboard, typing important notes from the call. More realistically, you're doing something unrelated to the meeting, such as browsing the web, playing a game, or messaging friends. Whatever it is you're typing, if your microphone is on, everyone on the Zoom call will be able to hear the sound of you typing.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.
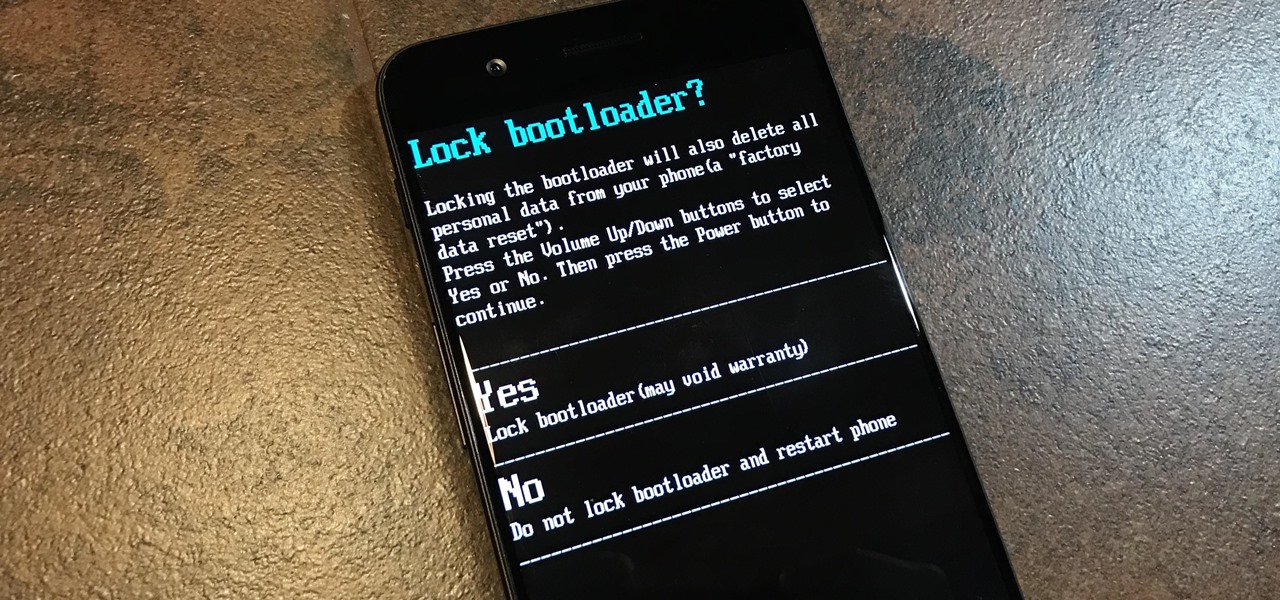
To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the firmware on your OnePlus 5 or 5T makes it hard to update to a new firmware such as Oreo when compared to stock.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

The bacteria in our gut — a community called the gut microbiome — have been in the spotlight a lot lately. What we're learning about how our intestinal bacteria adapt and grow with our bodies could help athletes perform better, according to researchers starting a company focused on creating probiotics that mimic athletes' microbiomes.
The reveal of Apple's new ARKit extensions for iPhones and iPads, while not much of a shock, did bring with it one big surprise. By finding a solution to surface detection without the use of additional external sensors, Apple just took a big step over many — though not all — solutions and platforms currently available for mobile AR.

Cats give us so much—companionship, loyalty, love... and now the bird flu. Several weeks ago, a veterinarian from the Animal Care Centers of New York City's Manhattan shelter caught H7N2 from a sick cat. According to a press release from the NYC Health Department on December 22, "The illness was mild, short-lived, and has resolved." This isn't the first time cats have passed infections on to humans, but it is the first time they passed on the bird flu—avian flu H7N2, to be exact.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them
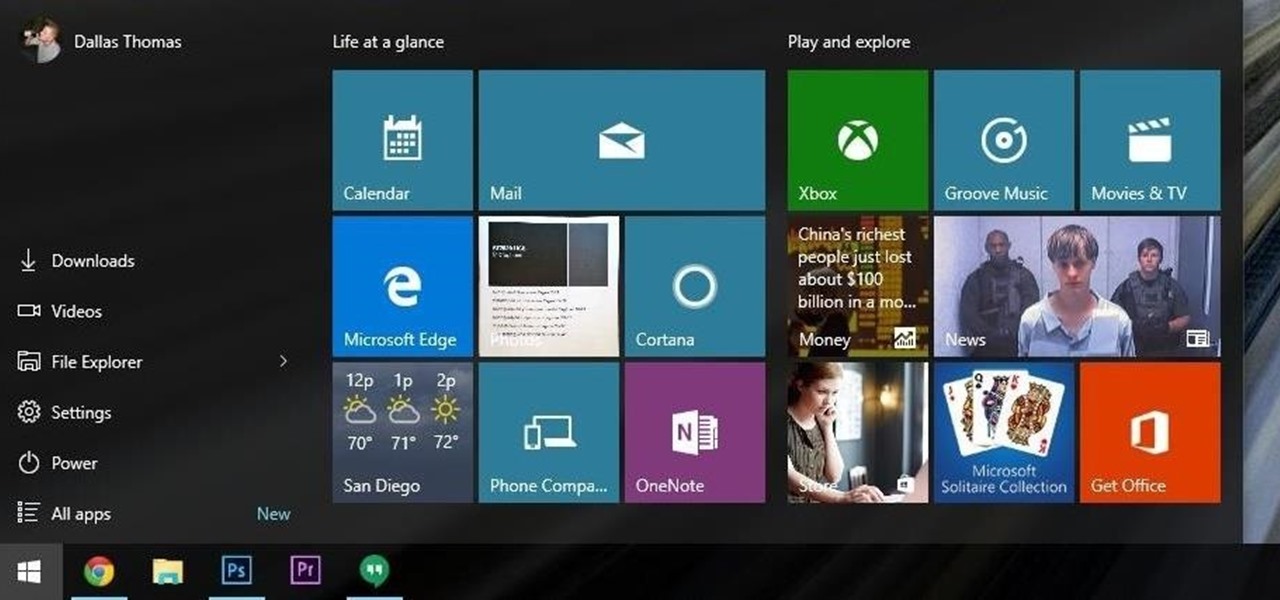
The desktop Start menu is finally back! After receiving a lot of negative user feedback, Microsoft ditched the touchscreen-first approach of Windows 8 and went with a more traditional setup for mouse-and-keyboard users in Windows 10.

From laptops to tablets, technology is taking over classrooms. Elementary schools offer kids tablets, and college students are bringing laptops into lecture halls, leaving their notebooks behind. Today, many students prefer putting their fingers to a keyboard rather than pen to paper, but are these helpful devices truly beneficial?

The key to simplifying fractions is to convert the fraction from a hamburger to a hot dog. In other words you change it from a fraction to a division problem, and then use Keep,Change,Flip to simplify. The video explains all of this and helps make complex fractions,simple.
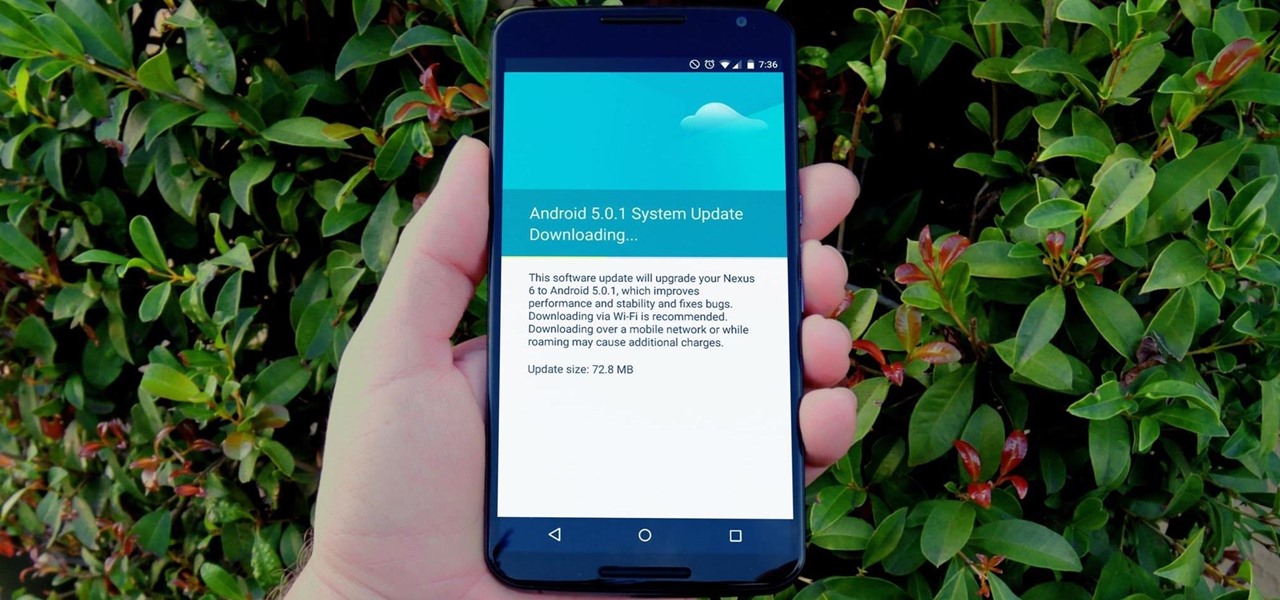
One of the main reasons to buy a Nexus device is the fact that they're always the first to get new Android updates. Another great selling point for the Nexus series is that the devices are amongst the easiest to root and mod. Unfortunately, though, these two features are somewhat mutually exclusive.

Using the mechanism of a door knob you can easily set up this practical joke on friends and family. You'll need a piece string and some tape to pull this off. Just remember to have a spare key to be able to undo this prank. For further instructions on how execute this prank

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

When it comes to passwords, the longer and more complex they are, the better the security. Even professional hackers say so. But if you've ever tried to type in such a password, you've surely noticed that it can be a bit of a pain. Mistype one character, and you're probably going to have to clear the field and start all over again.

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

As long as your friend's cup is made of styrofoam or paper then you should have an easy time pulling off this practical joke.
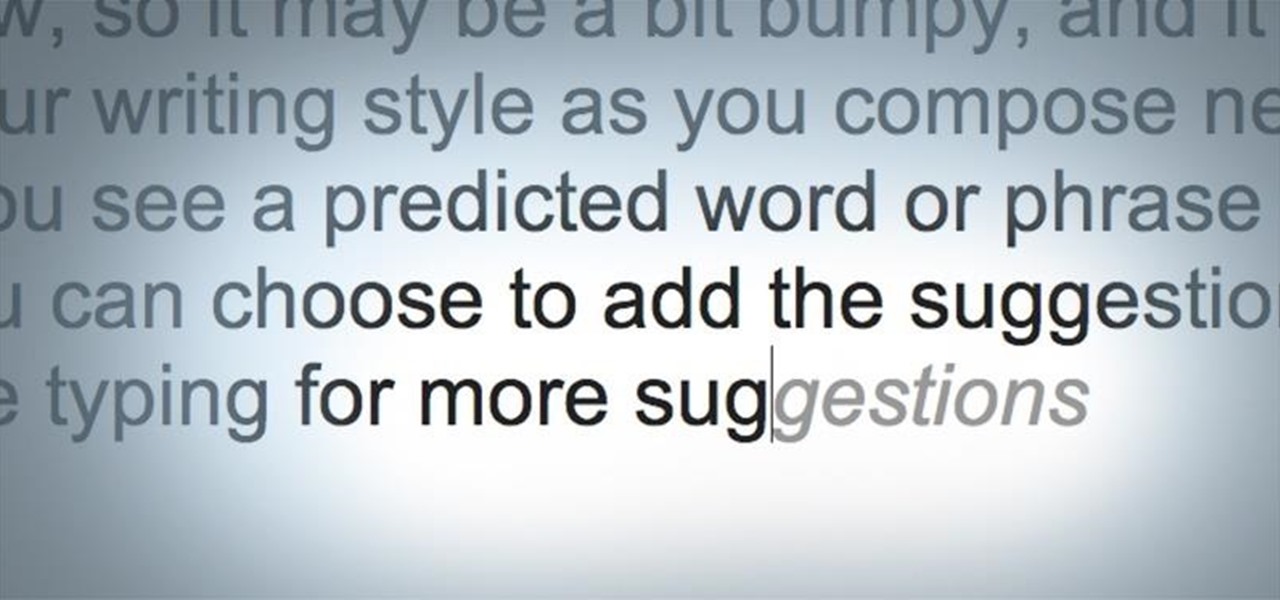
Android has had predictive text for a while now, both with stock and third-party keyboards such as Fleksy, SwiftKey, TouchPal, et al. Apple is even getting on board, with stock predictive text and third-party keyboards for iOS 8, slated for public release later this year.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.
This video shows top 10 useful tricks in windows 7. This video includes window key application, inserting program or folders in start menu or task bar, enabling or disabling windows7 features, notification area customization, reliability history etc. These tips will help you to operate windows 7 more efficiently. So please watch the video.

You know what's awesome? You own a Nexus. That means, with Google's blessing, you have easier access and control over your device than other manufacturers allow. You can really dig in and do some interesting things if you root.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

10 Life Hacks: 1.Wifi Booster

For this project, you will need a magnet, two AA batteries, two keys, a metal plate, and a copper wire coil.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevolent dictator's computer and temporarily disabled his nuclear launch capability, we have to think about covering our tracks so that he and his minions can't track our good works back to us.