
How To: Send a text message through email
Learn how to send a text message through e-mail. Just follow these steps. First step is to open a browser like Mozilla Firefox and other like Internet Explorer etc.


Learn how to send a text message through e-mail. Just follow these steps. First step is to open a browser like Mozilla Firefox and other like Internet Explorer etc.

This video is about how to make fine hair thick and wavy with a flat iron. This technique is done with an Ed Hardy iron. Before you start, it's good to put heat protector on the hair. Taking small sections, as you run the iron down hair make sure you are turning the iron. It helps that this particular flat iron is good at creating this type of look. As you are working, you should add hair spray so that the curls stay in place. This type of look is great for those women who have little or thin...

Have a small fear that your car might stall and you'll have a freak out? Stay calm. If you are driving down the road and your car suddenly dies, you need to know how to avoid a crash.

Learn how you would bypass a school’s web filters so that you can go to content sites that are always blocked in examples of YouTube. Click the ‘Start’ button and then click on ‘Run’ and type in cmd and hit enter on your keyboard. This will bring up a command prompt where you type in ‘ping’ and then when that populates the next prompt you enter in the website to bring up the IP address. By entering the populated number you can get into a website from the search field of a web browser. It incl...

This video shows you how to change you Mozilla Firefox page to look like Safari. -First go into your Mozilla Firefox page and go to Google.

Is you radiator acting up and making impossibly loud noises? Does banging in the pipes sound like someone's running a sledge hammer? Try this easy do-it-yourself fix with this video on how to bleed your radiator.

Keep your possessions safe from thieves with these tips. You Will Need

If you've been playing Fallout 3, you may have discovered that picking the locks in Fort Constantine is fairly difficult. Thankfully, this video clarifies how you can pick these locks without going through a bunch of bobby pins.

Some artists don't even deserve a full star. Learn how to give them the half-assed rating they deserve.
Got a digital camera, but no idea how to share pictures with friends and family? Try the photo-sharing site Flickr.

You've drafted a promising team, and the season's under way. Now increase your chances of making the playoffs.
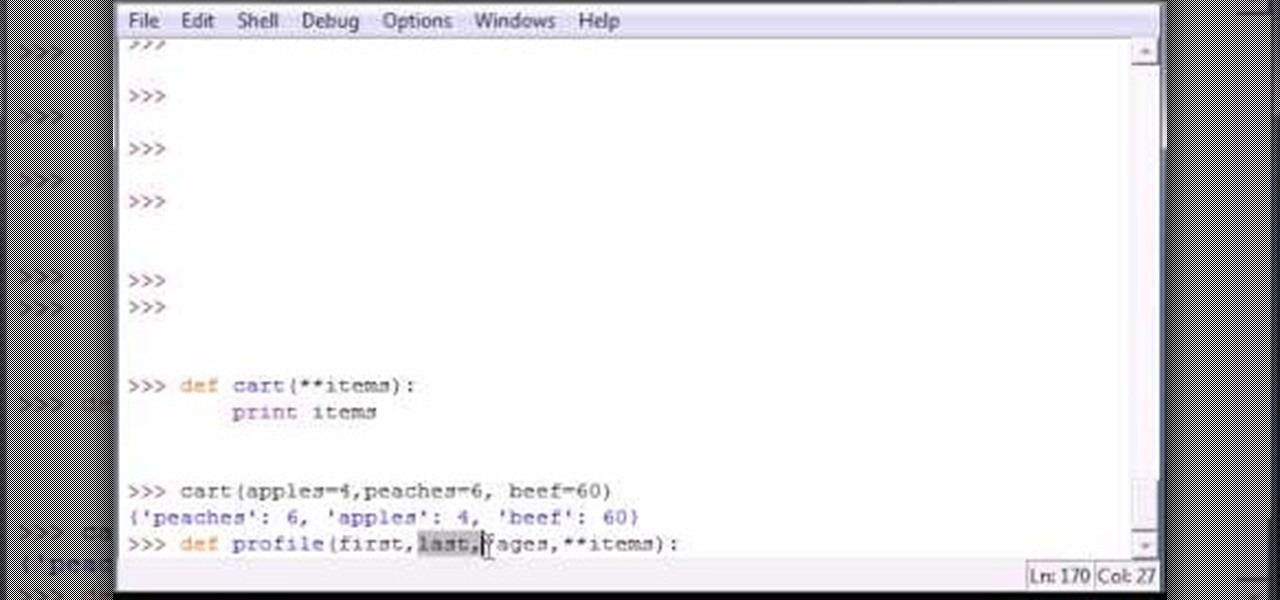
Bucky from The New Boston serves up this Python video tutorial on how to program parameters in Python. This is the program you use to write all of your Python code down. Different parameter types in the same function!

Oftentimes a friend will send you a PDF, MP3 or some other type of document such as a spreadsheet. When you open the file, an application opens. But sometimes it's not the application you wanted to associate with that file. In this video tutorial, you'll learn how to define which programs open what sorts of files. For more, and to learn how to set filetype application defaults in Mac OS X, watch this video tutorial.
Whether you're a social type with a loooonnng list of friends or a PR gal with a bunch of people you've got to contact all at once to notify them of an event, it can often get time-consuming to type out the name of every single person you have to send the same email to.

This instructable aims to show you how to cut any type of disk to a desired shape. It is particularly useful in cutting down cheap 12cm DVD-+R 's into more expensive (can be up to 10 times more) 8cm DVD-+R disks. The technique shown here works with all disk types. The video below shows us cutting a music CD into a heart shape, and also illustrates the basics of cutting 12cm disks into 8cm ones. The actual cutting of a disk (and the guide) can be seen here:

Chef Don from HouseCallChef demonstrates how to grill mushrooms, asparagus, zucchini and yellow squash. You can also grill other vegetables such as parsnip, rutabaga, potatoes, tomatoes or peppers, and even some fruits like pineapple, watermelon, apples and oranges. You can use any type of grill that you want.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to transform a photo into a flashy poster in Photoshop.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:
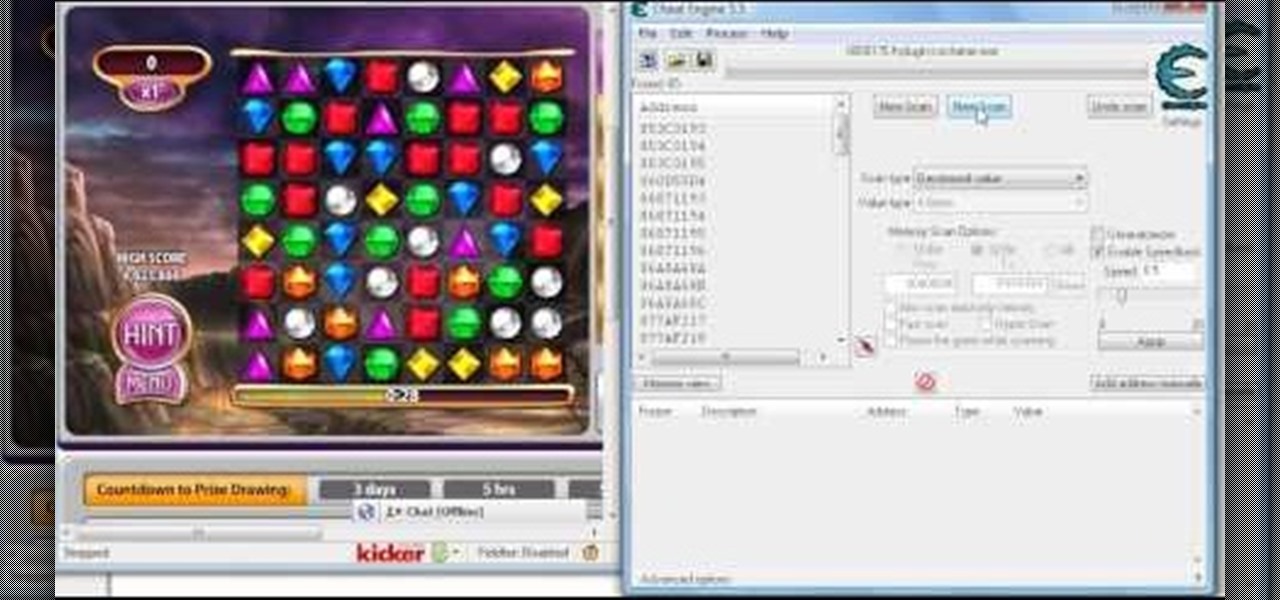
Don't let Bejeweled Blitz get the best of you. Show it who's boss and get the highest score possible. Of course, you'll need Cheat Engine to overpower the game, so make sure you have Cheat Engine 5.5 or higher and check out this video for the hacking Bejeweled Blitz (10/09/10).

Whether you are protecting your children or hiding personal information, there are ways to block unwanted websites from your computer. Follow this tutorial and learn how to accomplish this on a Windows PC easily.
This video will show you how to use the ‘find’ and ‘replace’ text buttons in Microsoft Word 2007. Microsoft Word 7 is slightly different from the Microsoft you might be used to but with these instruction you’ll have no problem finding the buttons.

This video will go over how to insert a check box in Microsoft Word for printing or for electronic distribution. With just a few clicks you can get a check box. You can even add different symbols or styles for your check box.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

Samsung removed the Bixby key on the Galaxy Note 10 and Note 10+ and gave the power button dual functionality. In the process, they changed the way you power off the phone and made taking screenshots a bit tricky. Fortunately, it's not too hard once you get used to things.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Waking up your Apple Watch to see "your heart has shown signs of an irregular rhythm suggestive of atrial fibrillation" might come as a shock. While your watch can send you warnings if it detects a fast or low heart rate, those messages are pretty vague, while the abnormal arrhythmia alert can downright scary. So what should you do if you receive one of these AFib notifications?

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.
Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in.

The rumors are still hot that Apple might include an 18-watt USB Type-C power adapter with the upcoming iPhone lineup so that there's fast-charging capability right out of the box. Leaked photos have surfaced that substantiate this rumor, though, they could also be fake. But how would ditching the old-style 5-watt USB Type-A power cube affect you if it's true?

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.
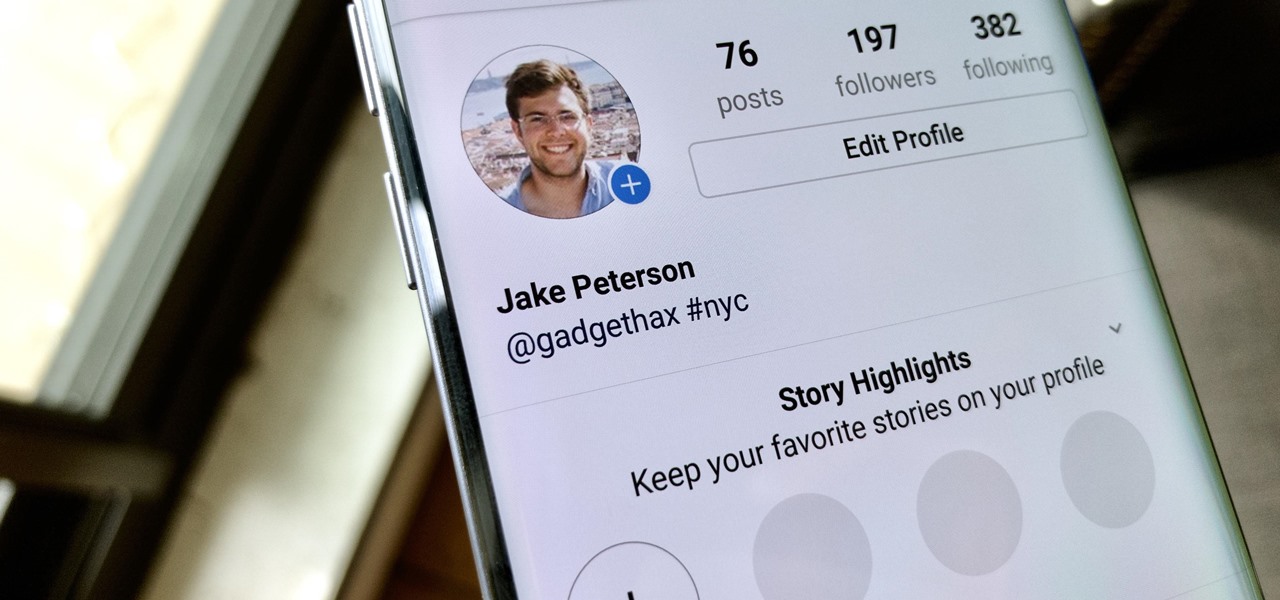
Your Instagram bio could always be used to link to other websites or profiles or just to show off your witty personality. Now, you also have the ability to use this section to tag other Instagram accounts as well as add tappable hashtags. Whether you want to link out to your best friend, company, or the latest trend in your city — if it has a profile name or tag, it can be in your bio.

Now that we finally have vertical plane recognition in ARKit (at least on a developer level until the spring iOS 11.3 release), the real promise of mobile augmented reality is beginning to come into focus on iOS. But a new report indicates that a major near future advancement of ARKit that could change everything has been put on hold by Apple.

Android used to have a notification ticker, but those days are long gone. Now, important new messages pop up on the top half of your screen with what's known as a "heads up notification." If you're in the middle of something, these popup notifications can be pretty annoying — luckily, it's pretty easy to turn them off.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

A vaccine against HIV might prevent the disease that we can't seem to cure. Some HIV patients make antibodies that can take down the virus, much the way a vaccine might. But, scientists haven't been able to provoke that type of response in other people. However, in a process that might work in humans, a group of researchers has successfully generated antibodies in cows that neutralize multiple strains of HIV.

Typing out thirty hashtags on Instagram is always such an annoying process. Figuring out the best hashtags to use to get more likes is also tricky. You can't just keep copying and pasting the same hashtags on every post — that's like attacking the same tribe every time. You got to diversify, which takes a lot of conscious effort to be on top of the current best hashtags to use.

Dramatic new research may change the fate of the hundreds of people who wait for a kidney transplant every year. The study hinged on the ability to cure hepatitis C infections, a possibility that became a reality in 2014.

As headlines focus on melting glaciers and rising water levels caused by global warming, climate change is quietly taking its toll on the nearly invisible occupants of this planet, the microbes.