Keyboards and mice work fine for computers, but in a holographic environment you'll want to do more than just point, click, and type. While we can still benefit from these input devices, complex hand-tracking methods are necessary for the evolution of mixed reality user interfaces.
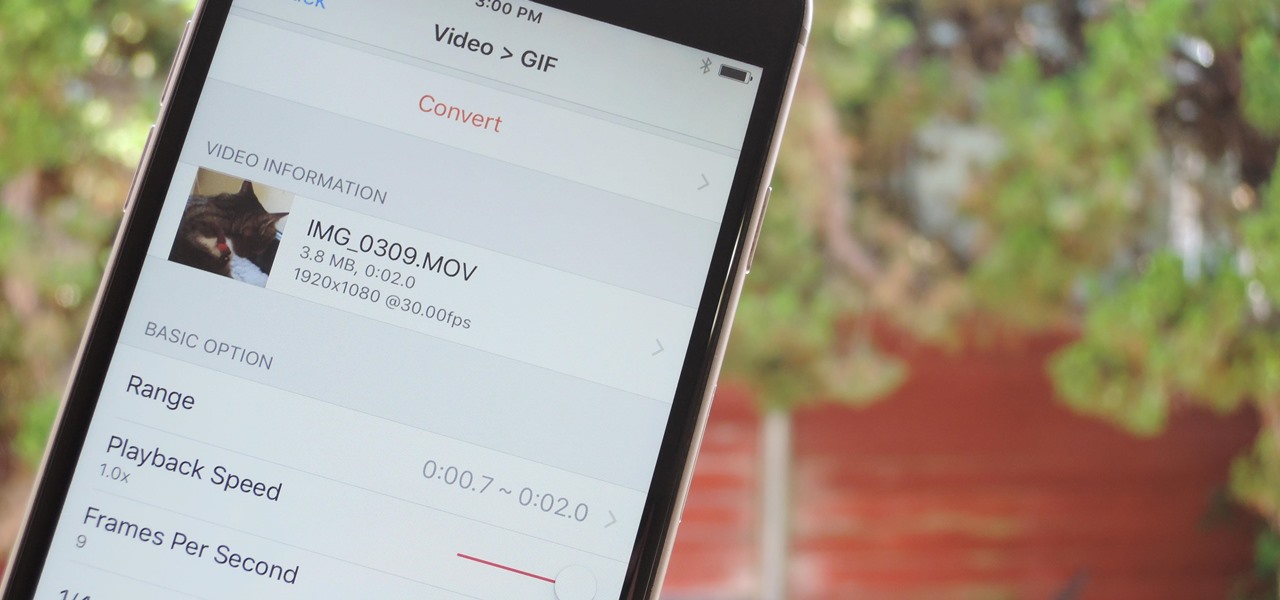
The internet has officially been taken over by GIFs—they're everybody's favorite method of communication these days, and nary a meme would exist without them. But even with the abundance of GIF-sharing websites, and even GIF keyboards, we're still a bit lacking in regard to creating GIFs on a mobile device.
Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem,

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

Sourdough is a delightful twist on your traditional bread, but creating and maintaining a sourdough starter can be a headache for many home bakers.
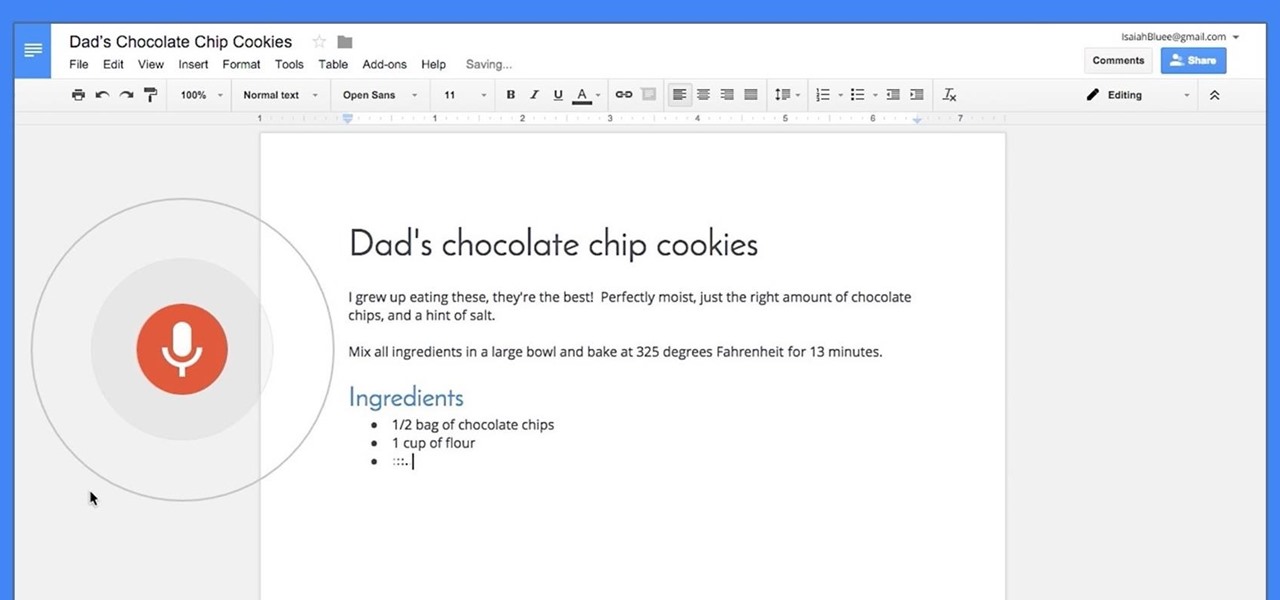
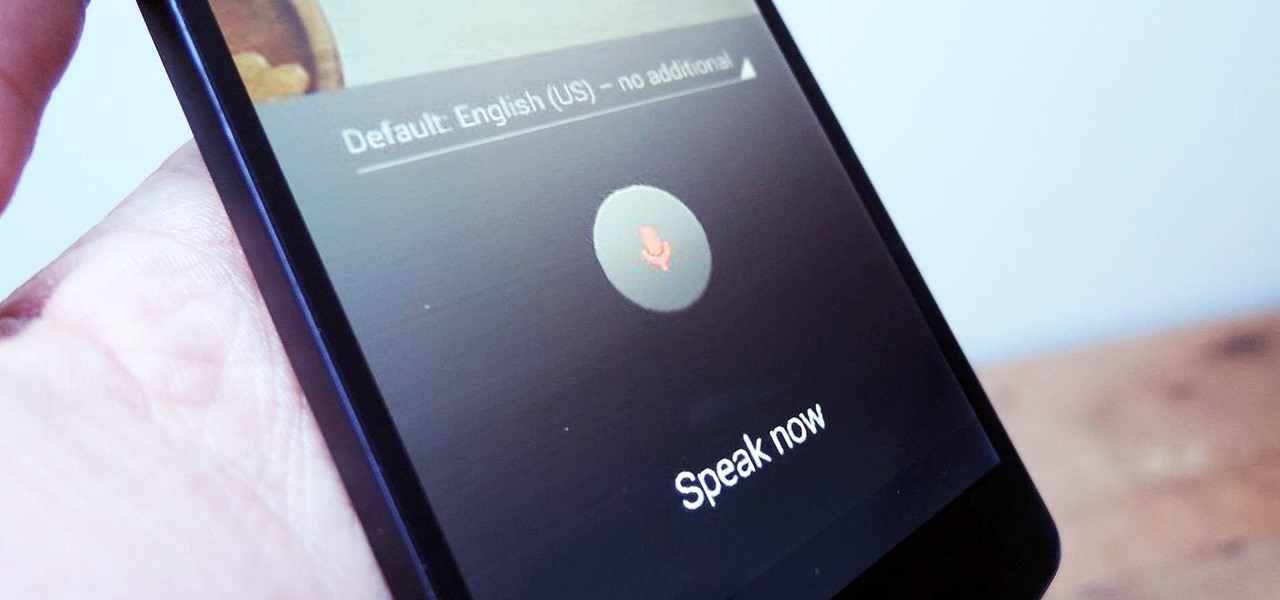
Google launched voice typing for Google Docs last Fall, and followed that up about six months later with voice commands that let you format and edit text as well. You can do things like select text, apply format settings like alignment and headings, and add and edit tables—all with your voice.

Google is rolling out an update for Google Drive that streamlines the online file storage/sharing app, and finally gives you access to the Trash folder that had only been available on the desktop version.

Facebook just keeps coming up with more and more diversions to help you ignore your responsibilities. At least this diversion is a little more intellectual than most of the other things that can easily distract you on Facebook.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

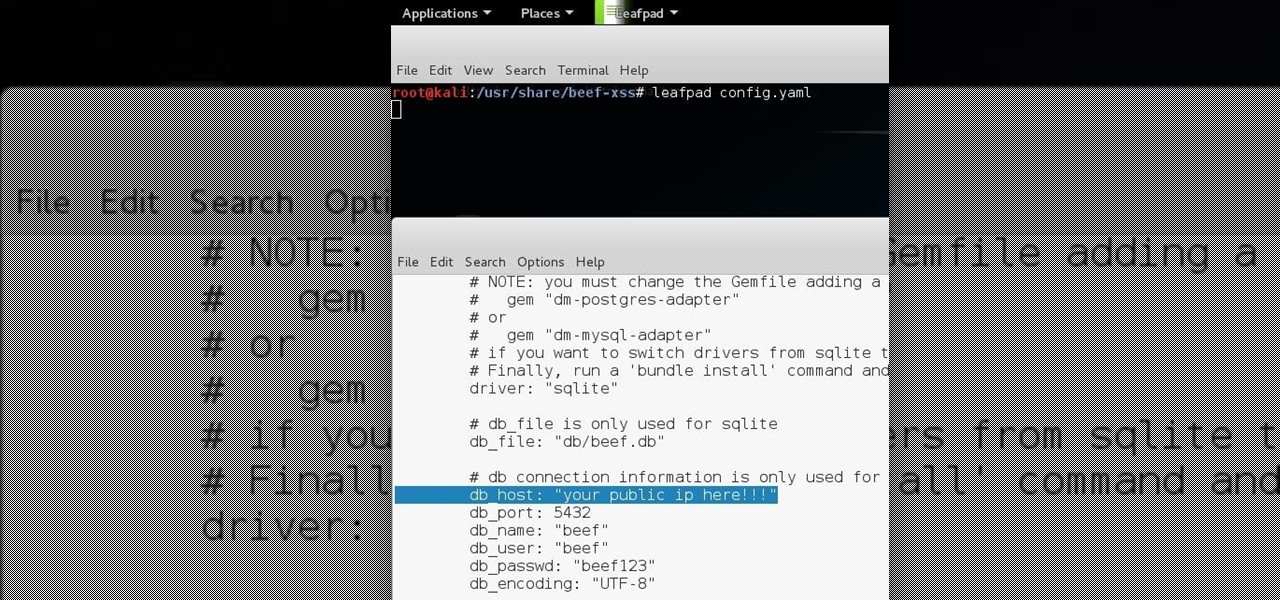
Hello all Just thought id share how ive managed to get beef working over the internet.

The notification light on phones and tablets is slowly disappearing. The once staple feature is now only found on a few devices, and a bevy of other notification systems have sought to fill the gap. The most popular of these systems is Ambient Display, which has grown in popularity with OEMs over the last couple of years; even Google's own Nexus line of phones have made the plunge.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

In python, or any scripting language for that matter, there are certain things that you will carry with you throughout your entire scripting career. Some of the most basic things that you will keep with you are output, variables, and their value types. We'll start by going over output, then cover variables and their types. So, let's get started!

You're at your friend's house. All you've heard about all day is his new laptop. He's got a brand new top-specced MacBook Pro, and he won't stop going on about it. It particularly annoys you as all you've got is a 4 year old cheap laptop, even if it is running Linux.

Since the release of Windows 8, Microsoft has been heavily encouraging users to use Windows with a Microsoft account. According to Microsoft, the main benefit of using a Microsoft account is the ability to sign in and sync your information across various Microsoft devices and services. Furthermore, you have access to a singular cloud storage solution which can contain documents, pictures, settings, and more on whatever system you're using with the Microsoft account.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

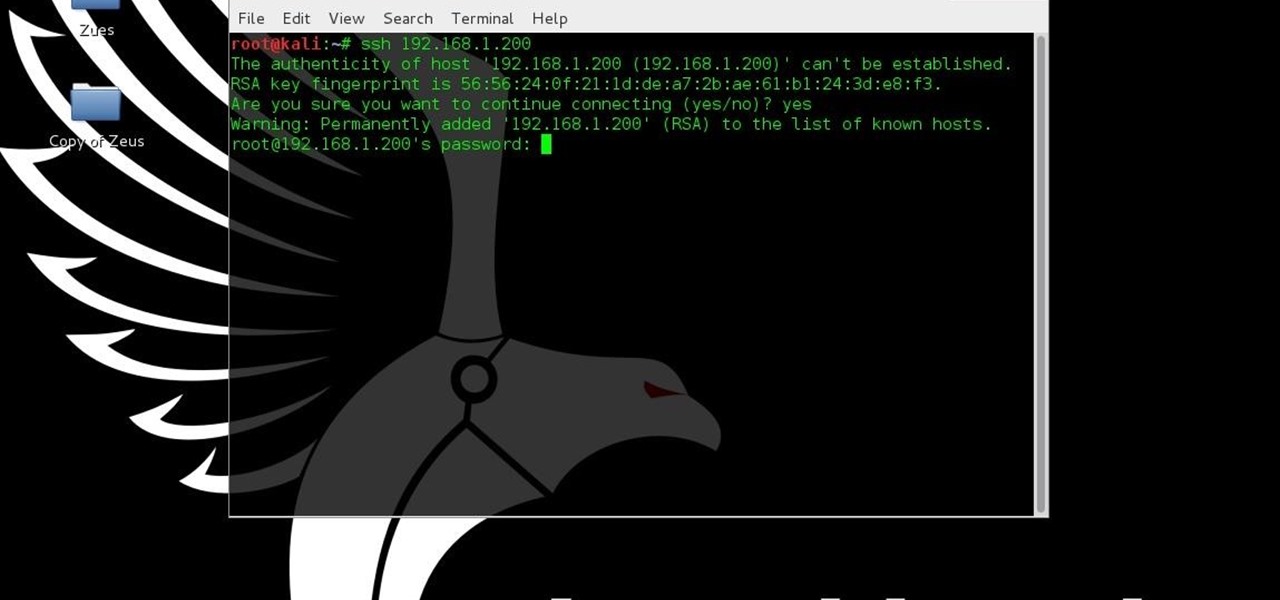
Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

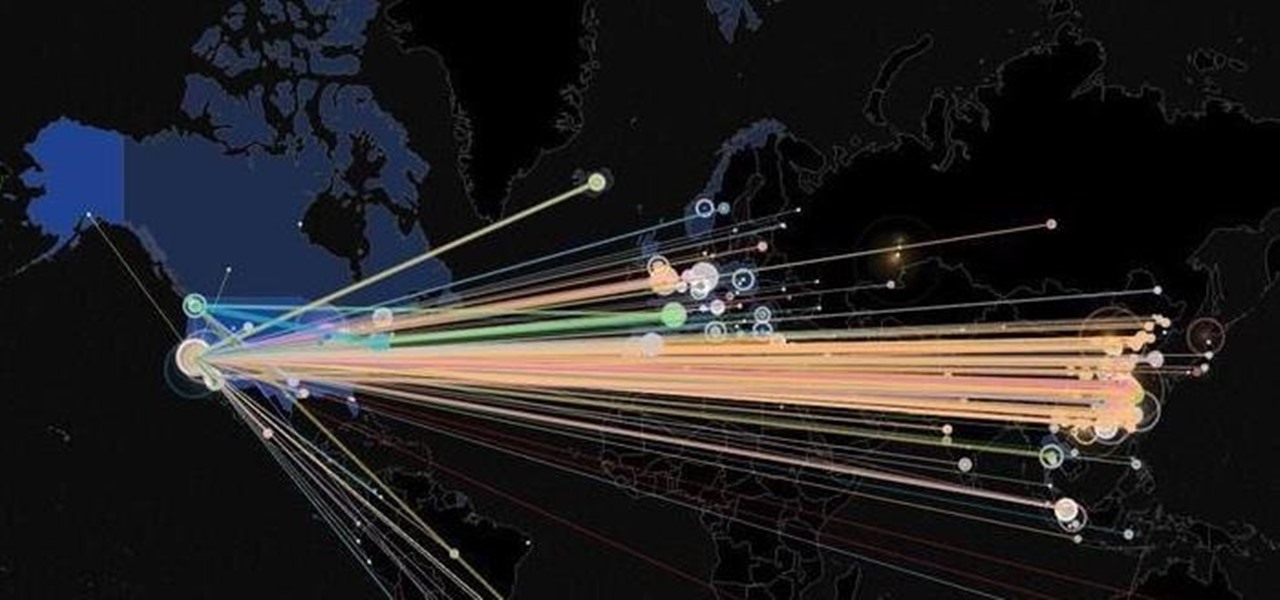
With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

On an Android device, you can download almost any file type into a neat and tidy "Downloads" folder, and those files can then be accessed with an appropriate app, shared via email, or transferred over to your computer. On an iPhone, there is no such folder, and saving files from Safari is almost impossible unless you're jailbroken.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

One of the many additions that appear on Android 5.0 Lollipop is a handy menu that lets users correct for or simulate different types of color blindness. While Google didn't flip the switch on this new feature until Lollipop was released, it turns out they had been working on it for quite some time.

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

If I told you that people who use emojis in their conversations have more sex than plain-text users, would you believe me? According to a recent study launched by Match.com, men and women that use emojis have more sex than those who do not. If you were looking for an excuse to increase your emoji output, you may not find a better one than that. To make your emoji typing as smooth and seamless as possible, I'm going to show you how to create shortcuts in iOS 8 for all your favorite use cases. ...

UPDATE NOVEMBER 2015: The root process has changed for the Nexus Player now that the device is running Android 6.0 Marhsmallow. I've updated this article with detailed instructions on the new root process, but the video below still depicts the old process for Android Lollipop.

Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

Each morning, we spend a significant portion of our time staring into the mirror. From choosing clothes and accessories to perfecting our hair, we try to make ourselves attractive. Yet catching others' attention doesn't have to rely on preening and primping. There's some truth to the maxim of beauty in confidence—all you need to make yourself more attractive is spray on your favorite scent.

Video: . Marley Hair is Super Cute Curled so I decided to Curl it.

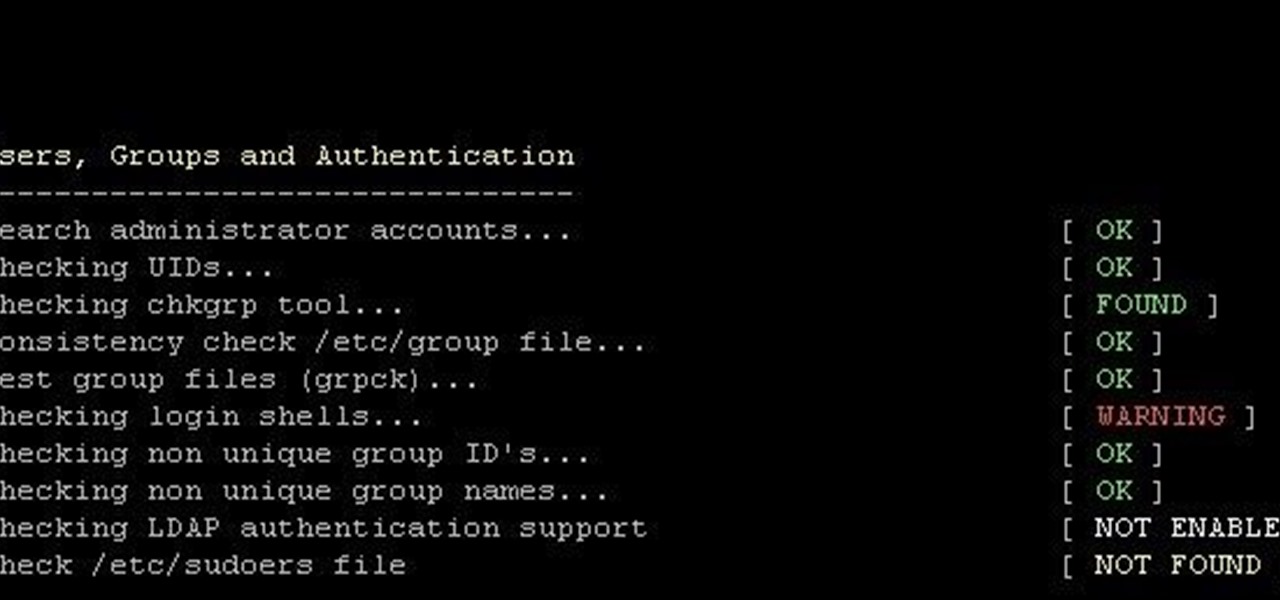
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

Finding the motivation to make a change can be tricky. It's difficult to resist the urge to procrastinate, or even give up when goals seem distant and difficult. If you wish you could stick to your New Year's resolutions, or maybe even just commit to pursuing smaller goals, you might want to consider making a small change to start: just create a new password.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

As smartphones become increasingly integral parts of our lives, so does data throttling. Personally, I try to save data any way that I can, so to stave off unnecessary usage, I use the GoogleOfflineVoice to limit the amount of data consumed by voice typing.

Most of us know how to make a sandwich, but how many of us know how to make a sandwich correctly—i.e., so that the slippery ingredients like tomatoes and cucumber don't come gushing out the other end when we take a bite?

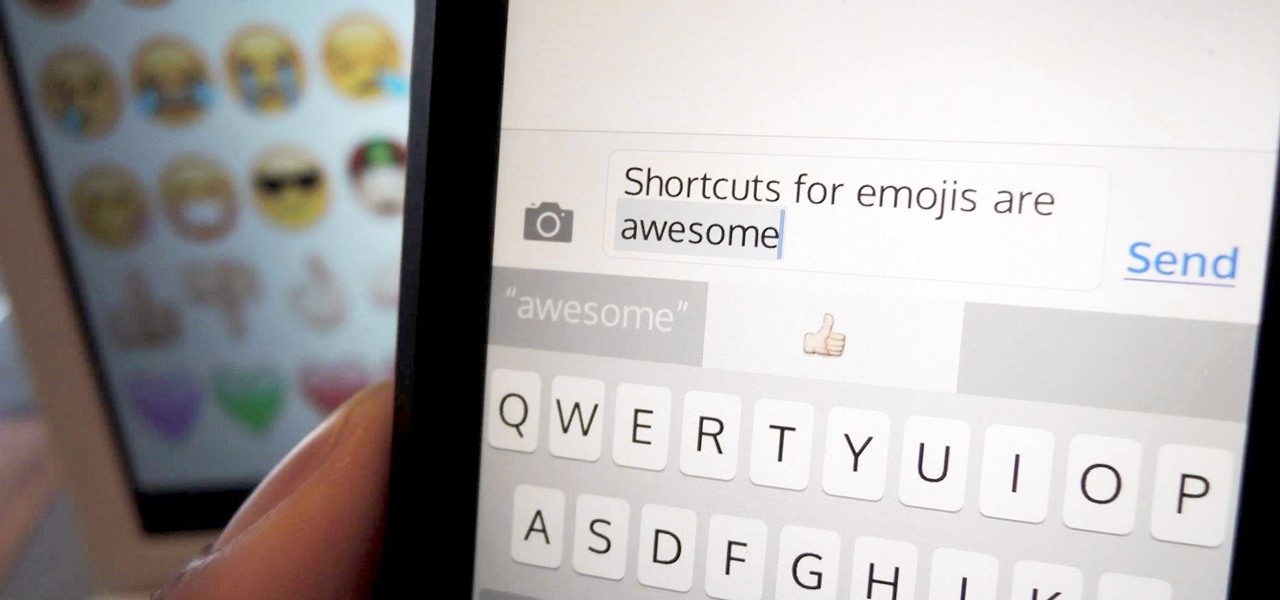
I'm a long-time and loyal Android user, but one iOS feature that I'm truly envious of is their keyboard shortcuts, which lets you assign a short macro that inputs a longer phrase. For example, typing "home" can input your home address.

Spotlight is awesome for finding items in the stock Apple apps, but what if you want to search through the rest of the apps on your iPhone?