If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.
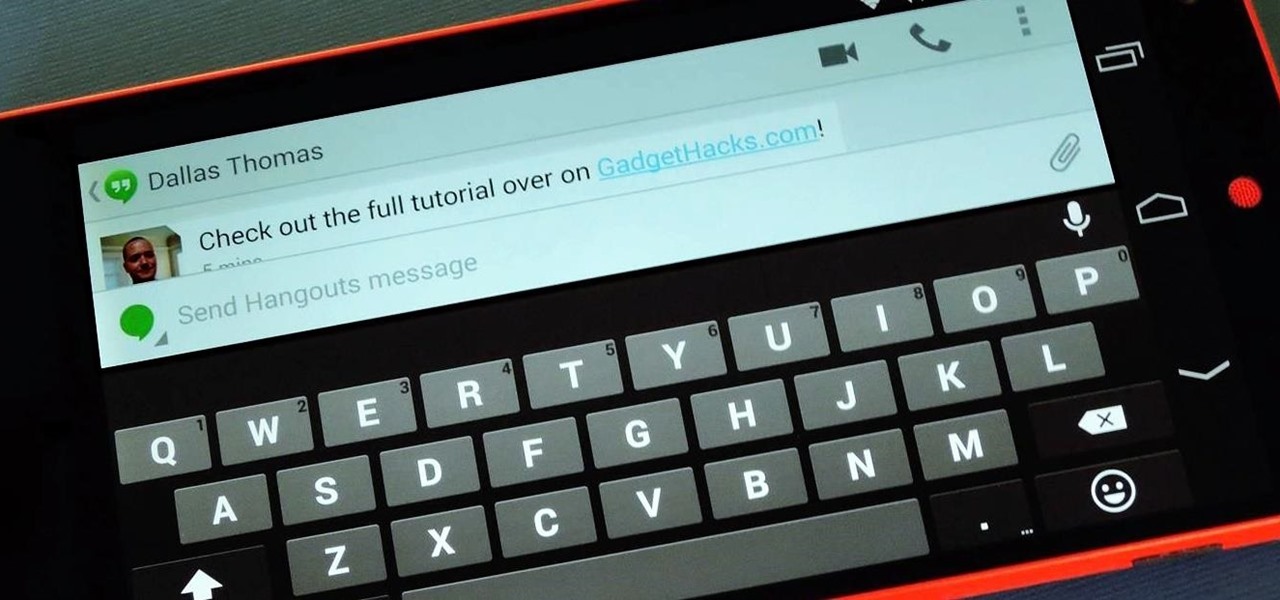
For some reason, when you're typing in landscape mode, Android extends the text input field to cover every bit of the screen that the keyboard's not occupying. This gets pretty annoying sometimes, especially with messaging apps where you might need to reference what the other person just said in order to properly form your response.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.
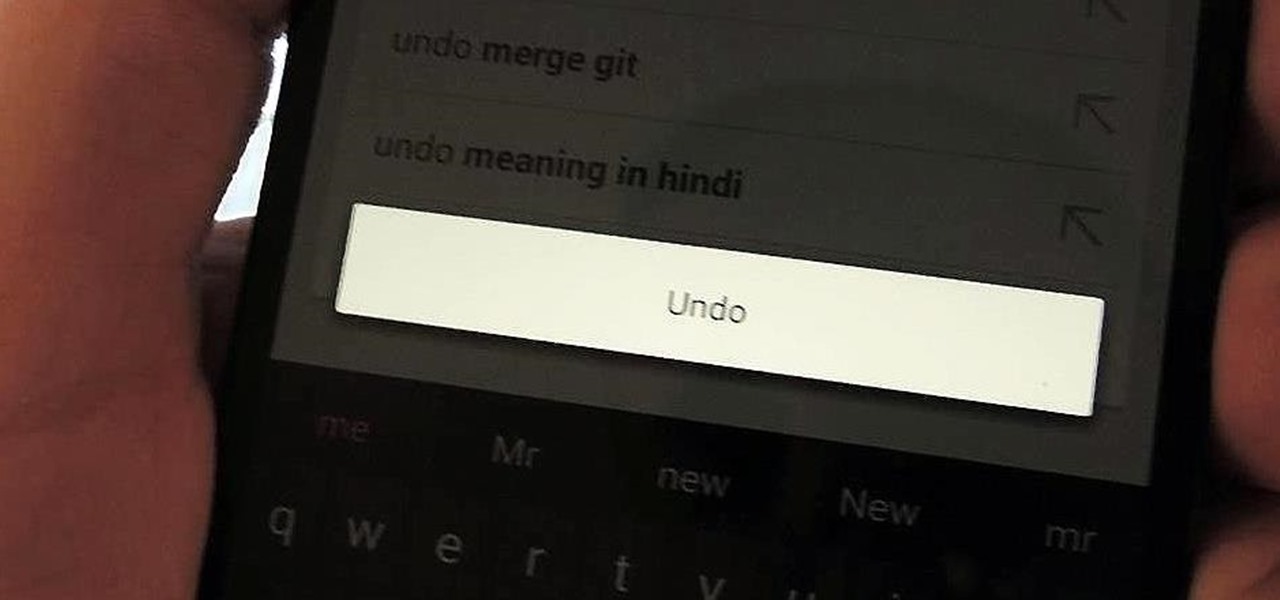
Over the years, we've probably all complained at some point about Android's lack of an "Undo" feature. When you're typing something out, there are times when you might want to go back a step.

You've probably used Google to search for recipes, or to find out what the heck that mystery food on the ingredients list is. But with all its built-in features, there are plenty of other ways the search engine can help you out in the kitchen.

Alright, I'll admit it, iOS can be quite nice. Android loyalist that I may be, I'm not so stubborn that I can't recognize a good thing when I see it. Apple's iOS has a lot of strengths, and our Nexus 4s, god bless 'em, are growing a little long in the tooth.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

It's always the snack you're most looking forward to that ends up being moldy when you open the fridge to grab it. Always. That slice of leftover pizza or chunk of cheese you've been thinking about all day? We've all been there. What separates us is how we choose to deal with it. Personally, I toss anything that has even the slightest hint of mold, but not everyone errs on the side of caution. Some people don't mind the risk and just cut off the green or fuzzy parts and eat the rest.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Most recipes don't specify what type they mean when they call for onions. While using whatever kind you already have won't necessarily ruin a dish, using the best one for what you're cooking will definitely make your food taste better.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

"Enter your email address. Confirm your email address." I absolutely hate seeing those two sentences when I'm signing up for something online, especially on my Samsung Galaxy S3. The less keyboard work I have to do on my mobile the better. Luckily, there is a way to enter your email address without having to type it all out, and I'm going to show you how it's done.

No matter how much of a gamer you are, typing with your PS4 controller is a bitch. Let's just be real. Having to move left, then right, then down, for every single letter can make writing a message very time consuming; so much so that I usually avoid messaging altogether.

Ways to Blocking a Website on a PC Open the “Control Panel” by click “My Computer” on your PC

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Just because you wanted a stable, stock Android version on your HTC One doesn't mean you have to miss out on Sense because you bought or softModded to a Google Play Edition. As long as you have the Android SDK tools and you've unlocked your bootloader, you can turn your HTC One into the Developer Edition, a Sense version free of carrier bloat.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Despite being disgusting, houseflies are actually beneficial to humans in a few ways. As scavengers, they help the environment by eating rotting organic matter, and make great food for pet tarantulas. Regardless of the advantages to their existence, having them in your home can be infuriating. There are countless sprays, traps and devices made to kill or deter the little pests, one of the most common being flypaper that hangs from the ceiling. These sticky strips are incredibly easy to make a...

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Previously, if you missed a call or text on your old Samsung Galaxy S3, there was a white LED notification to let you know. It's a nice feature that most smartphones have, but wouldn't it have be nice to know what kind of notification it was before picking up the phone?

Tired of your Samsung Galaxy S3 being a square? Make it more well-rounded by ditching those 90-degree corners on your screen for new adjustable round corners instead. It may be a minor tweak to your device, but the psychological effects of a more circular screen may help you feel more connected, safe, and, well…perfect. If you're the type that prefers the logic, order, and security of a sharp-cornered screen, then stick with your standard Android interface. Otherwise, keeping reading.

There is nothing worse than losing valuable information or programs on your computer. And if you've ever accidentally deleted a file or document, you know how agonizing that entire process can be.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

Frankly, I never cared about the care labels on my clothing. They supposedly held some secret key to keeping clothes clean and bright, but who wants to look at little icons and a bunch of fine print for every single garment they wash?

This is a very fun and happy cat nail design that I wanted to show how to create through the following nail art video :

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

This is a very cute and simple gradient or ombre sequinned nail art with hearts nail polish design that a did a few days back and just wanted to share with all you girls here.

Humans clearly demonstrate altruistic tendencies towards other members of groups with which they identify.

For many busy people, time is of the essence, and for others, it's simply just being impatient. But no matter what your vice, having your computer start up as quickly as possible is usually a plus for anyone.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Whether you're making a poster, drawing a logo or designing a website, the font you use can make a huge difference in any visual design, and the ones available in most word processors can get pretty boring. There are thousands of sites online where you can download free fonts, and even a few that let you design your own. Here are some of the best.

Yanik Chauvin shows viewers how to add a reflection using Photoshop. This tutorial focuses on how to do a reflection on a white background. You can do this with objects as well as people. Bring up your image with a white background to add the reflection to. First, you should press ctrl+j to add a second layer. In order to do a reflection, you need room, so you need to increase your canvas size. To do this click image, click canvas size, and click the bottom arrow so it can expand downward. Yo...

Bugle cords are used as elaborate ornamental leashes on bugles and trumpets, but they are also used as snazzy ornamentation, called aiguillettes (a type of fourragère), on uniforms worn by certain members of the military. While you could buy one pre-made, you could also make one yourself. But this should not be confused with the infantry blue cord of the U.S. Army, which is another type of fourragère only with more elaborate knotting.

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

This video explains how to use jumper cables to jump start a car. First, determine that a dead battery is the reason your car is not starting. If the engine cranks when you turn the key, the problem is not the battery and jump-starting won't help. If the windshield wipers, lights and heater blower all work, the battery is probably fine and you may have a bad starter. A jump-start won't help if you have a bad starter. If you hear no sound at all when you turn the key or if the engine cranks ve...

Want help playing slack key on the ukulele? Check out this video for a long lesson. Part 1 of 6 - How to Play the ukulele in slack key.