This clip offers a quick tip on how to view the keys in the 3D View using Blender 2.49b or 2.5. Whether you're new to the Blender Foundation's popular 3D modeling program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look.
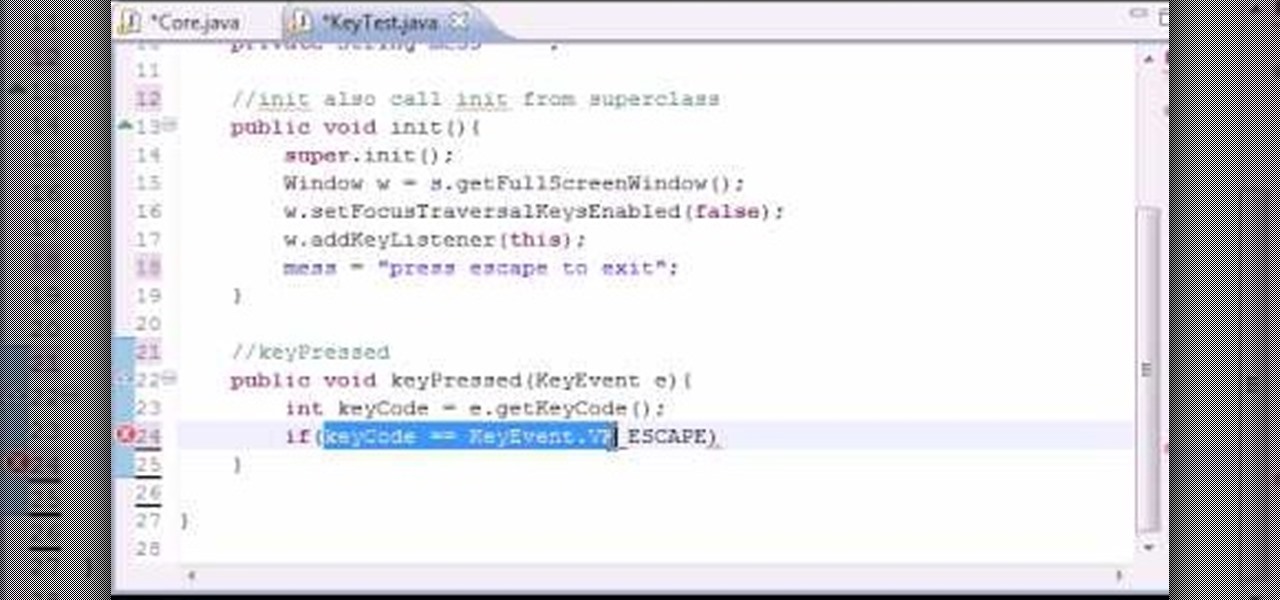
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to handle key events when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.

Strategy is key to being a proclaimed chess player. You need to know the ins and outs of situations and you have to be quick in your wit. This video emulates very good strategy played in a chess game giving you keys to build your own winning tactics.

Shown here is another video tutorial made possible through TutVid. In this video, you are learning the basics of Action Scripting in Flash. This lesson is titled "Action Scripting:101." Action scripting is one of the coolest thing about flash. The thing that makes flash special is the ability to make simple actions interactive. Flash possibilities are endless!
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install and enable Flash for Chromium on Ubuntu Linux.

A below elbow arm amputee demonstrates how to turn a car key with his body powered prosthetic hook. This adapted equipment video is helpful for handicapped, disabled or individuals whom have lost limbs due to amputation. He's using a prosthetic arm outfitted with a hook to start the ignition of his car.

In this episode of Hak5, Darren shows us a USB key, dubbed the USB Hacksaw, that instantly and silently installs on target Windows 2000 or higher computers with guest or higher privileges which will monitor USB ports for flash drives and automatically download their contents for silent archival and email. For detailed instructions on replicating this hack yourself, watch this video hacking tutorial.

You can add interest by changing from one key to another during your song. Garageband makes this easy using the master track.

Violin Lesson #32-33 -- 4 Types of Shifts. Todd Ehle discusses the four types of shifts on the violin in this 2-part lesson.

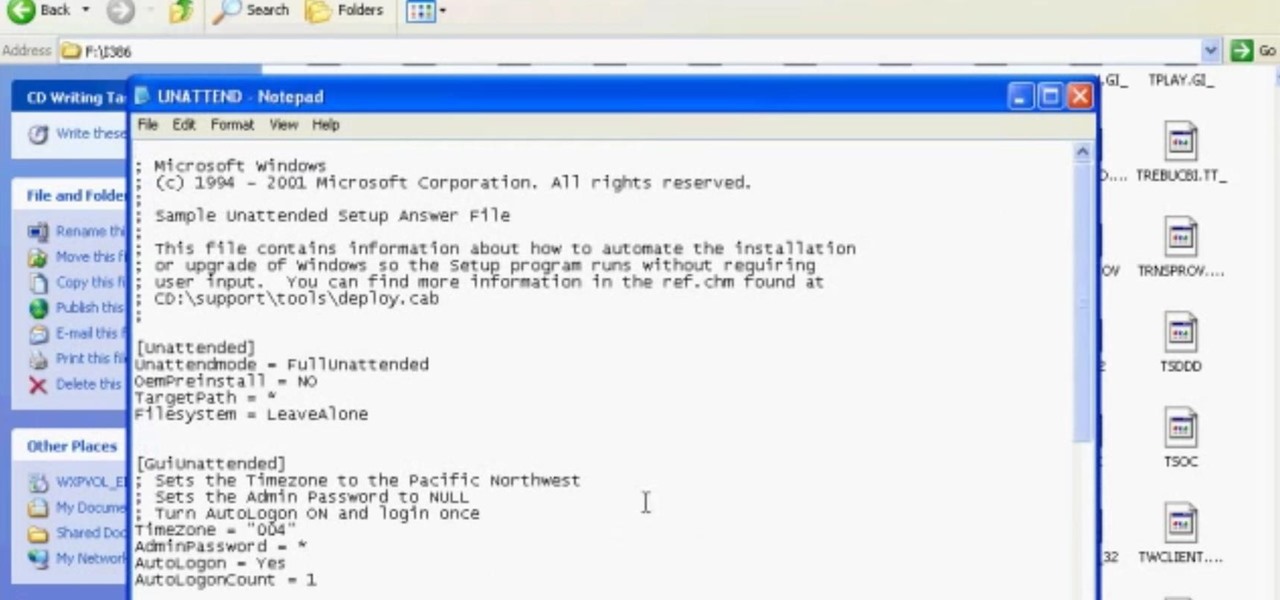
This will allow you to find the CD product key or serial if you have lost it so you dont have to buy another CD.

Michelle Harris shows you how to make key lime pie with tofu of all things! She also gives us some info on the benefits of tofu.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

For all of the flak that Windows 8 received from desktop users, it certainly had some interesting and unique features. For instance, the "Charms" bar allowed you to easily access several key menus by simply hovering your mouse pointer in the top- or bottom-right corner of the screen.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Losing important data is the modern-day equivalent of misplacing your wallet or keys. We have tons of vital information stored in our digital worlds, and losing any of it can be devastating. But if you've accidentally deleted something important from your Android device, there's still hope.

Update, November 12, 2014: Android 5.0 Lollipop is officially out now. If you haven't gotten the OTA yet, check out our new guide on installing the official Lollipop builds on any Nexus for download links and instructions, for Mac or Windows.

Rather than just use the stock Apple keyboard, iOS 8 now lets you use keyboards from TouchPal, Fleksy, SwiftKey, Swype, and more. I'll be showing you how to set up a third-party keyboard on your iPad, iPhone, or iPod touch, as well as giving you a firsthand look at TouchPal's keyboard for iOS 8.

Welcome back, my greenhorn hackers!

I regularly listen to music on my Nexus 7 while working or playing my Xbox. It's light and easy to carry around, and has basically become an extension of my body. The only thing that bugs me is having to constantly turn the screen on to pause or change music tracks. Even if I can do it from my lock screen instead of the actual music player app—I don't want to.

We'll show you how to use an attachment for a power washer called a "Foamer" - you'll never hand wash a car or boat again!

3D printing has been around for a while, but until recently it was used mostly for prototyping and research. Now, with technological advancements, it seems like everyone is using 3D printers, from crime scene investigators to garage hobbyists and hackers. Below are some of the most innovative uses people have come up with so far.

This video tutorial will show you how to apply four styles of lighting. This video teaches you how to apply four styles of lighting, namely Rembrandt, Beauty, Cameo and filling in from the Key Side. You will learn about high contrast lighting schemes, dealing with the amount of contrast used to highlight a person's face, as well as spotlight effects, and how these tend to draw the viewer into the scene. You will be shown how the Rembrandt Lighting setup contains three steps, namely taking a K...

In this video, we learn how to use the smart key for the 2010 Prius. You can use this just like any other keyless entry system. Press the lock button to lock the doors and the unlock button to unlock the doors. When you press unlock once it unlocks the drivers door, if you press it twice within 3 seconds, it unlocks all the door. After 60 seconds, the Prius will automatically lock itself. Press the red alarm key if you need to draw attention to yourself in an emergency situation. Make sure yo...

Knowing music theory never hurt anyone—not Bach, not Chopin, not Schoenberg. Even if you fancy yourself a musical iconoclast, the better you know the rules of music, the better equipped you'll be to break them down the line. In this free video music theory lesson, you'll learn how to determine the root or "home" key of a song. For more information, including a very thorough overview, watch this helpful musician's guide.

There are almost as many types of sutures as there are types of wounds that a human can sustain. This video instructs the viewer in performing one popular type of suture: the vertical mattress stitch. This type of stitch is relatively simple and strong, and thus a good choice for many types of wounds.

Assign custom shortcut keys to your most commonly used Adobe Photoshop CS4 functions to help speed up your workflow. Whether you're new to Adobe's popular graphic editing program or a seasoned design professional looking to better acquaint yourself with the new features and functions of this particular iteration of the application, you're sure to benefit from this free software tutorial. For more information, watch this designer's guide.

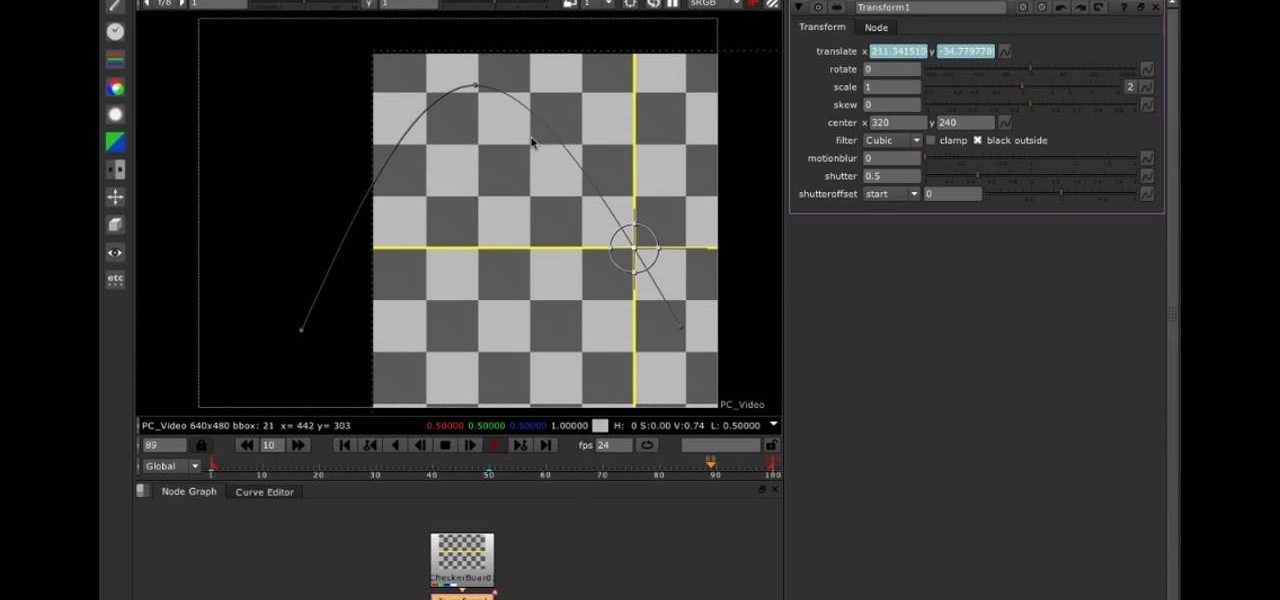
Learn how to use set key frames (or keyframes) working in Nuke 5. Whether you're new to the Foundry's popular node-based compositing application or a seasoned post-production professional just looking to better acquaint yourself with Nuke 5's new features, you're sure to be well served by this video tutorial. For more information, including a detailed overview, watch this free video guide.

Learn how to operate the latest Blackberry 8330 in simple steps. Follow the steps below to overview the Blackberry 8330: 1. First switch on your Blackberry by pressing the power button on its top. 2. Use the 'Trackball' to navigate around the menu options and press it to select an option. 3. The 'Send' can be used to call a contact, the 'Menu' key opens a list of options, then the 'Escape' key is used to end an application and the 'End' key is used to end a call. 4. You can find on the left s...

To open the body of an HTML first open the HTML document, to do so write an open bracket, then html, the close the bracket. Next press enter. Type another open bracket, then type the word body, then type a closed bracket. Next press enter again. Now you can type an open bracket, then a backwards slash. Next type the word body again. Now type a closed bracket. Press enter once again. Now type another open bracket and then type html. Then type a closed bracket. Now you have just opened and clos...

Go to DJTUTOR computer where you can download the latest firmware for free. Once downloaded you need to either burn it to a CD-R or use a USB key. Unzip the file and download it to a fat formatted USB key with nothing else on it. The firmware upgrade consists of two files. Eject any disks from the MEP and remove any USBs and make sure the unit is turned off. Next insert your USB key and push and hold USB 1 and USB 2 and turn on your unit. The MEP will then tell you when the firmware is comple...

Step by step tutorial video on adjusting the neck of your guitar. First you need to remove the truss rod cover to gain access to the truss rod. Make sure you have the correct Allen key when adjusting your truss rod. If your guitar came with it's own Allen key make sure you use that one. Put a capo on the first fret. To increase the tension on the truss rod turn the Allen key to the right. To decrease the tension turn it to the left. Always check the gap between the frets and the strings.

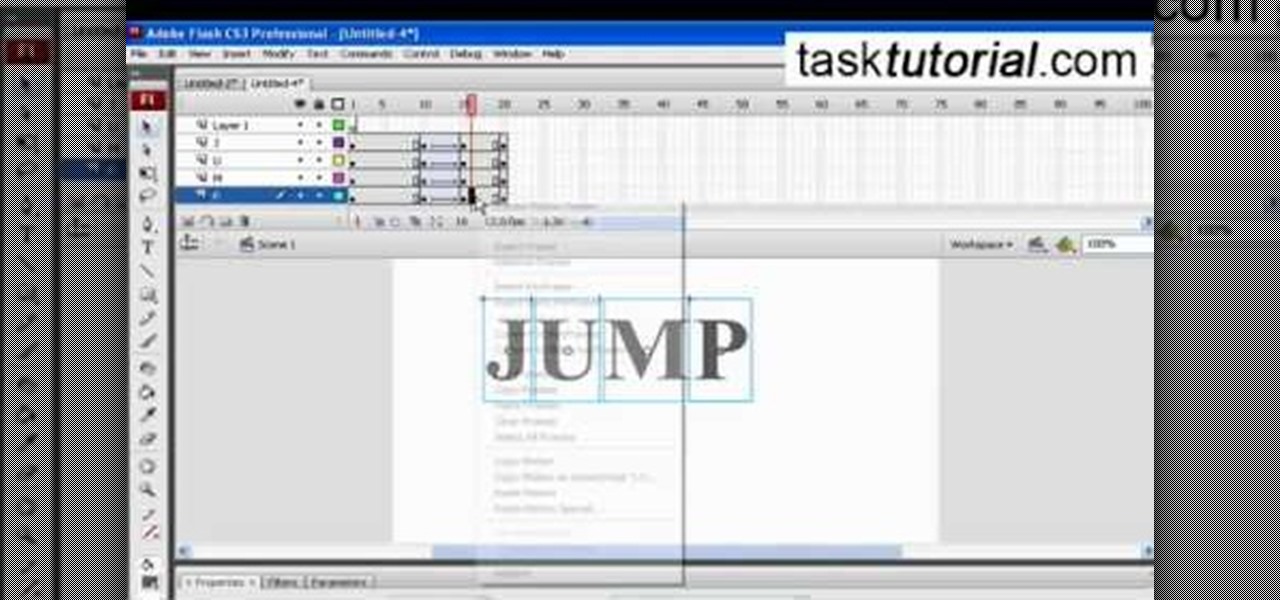
This video describes how to create a jumping letters in Flash, first create the text for example "JUMP" and using Break the letters each and then make the layer and now convert the letters into "Movie clips" and now we should add the key frames to our "time line”. Then moves the letters up by using the up arrow now copy the key frames from font end and paste on the back again for go up and come down the letters again and add the "motion between" for each letters and now skip the key frames by...

This tutorial will show you how to create a cool image animation using mask in Flash. First lets import image file and now lets create a new layer. Choose oval tools and now lets draw a shape just outside our scene. Then go to frame 30, and add the key frame and select transform tool. Now lets re-size our shape and go to 50 frame and add the key frame. Then go to frame 80 and add the key frame, re-size our shape and use free transform tools. Now lets create shaped in frame over 30, 50,and 80 ...

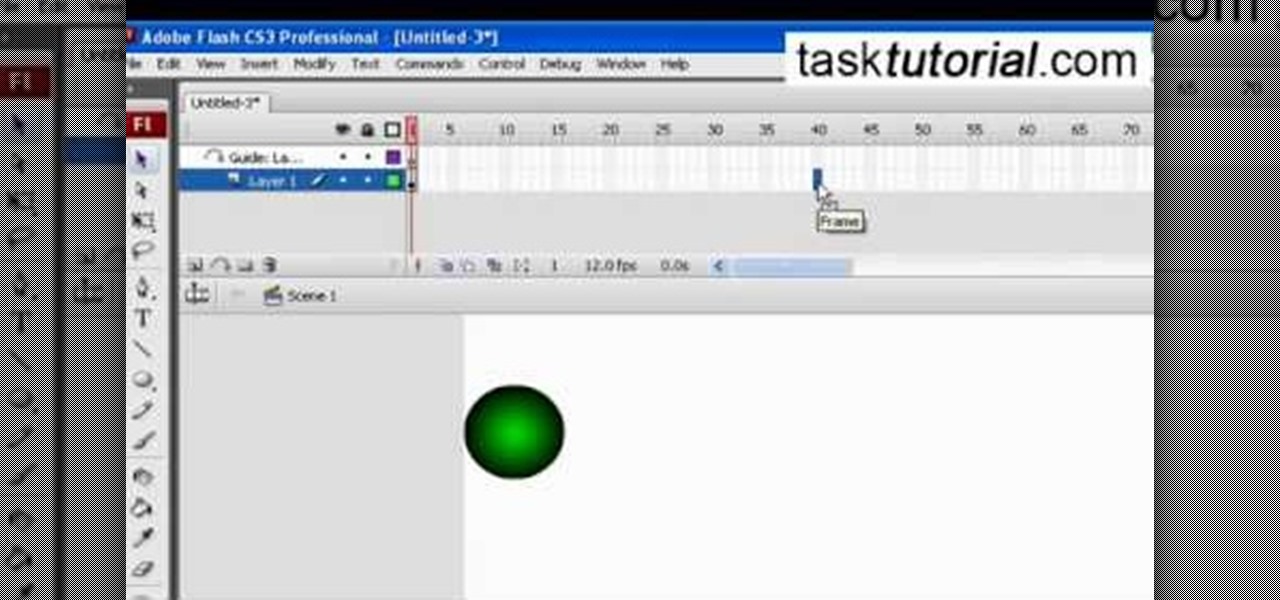
This tutorial video, from tasktutorial demonstrates how to create animation using the motion guide function in Flash. You will learn how to create an object, in this case, a ball, and create an animation that makes it appear to bounce. The guide shows you, how to add a motion guide by selecting a key frame and drawing it in. Then you will learn how to snap the object to your guide line, and add motion to it by selecting another key frame between the first and last frames, and snapping the obj...

In this flash tutorial the instructor shows how to make a black and white mask animation. To do this, first start by importing your image into the flash tool and bring it on to the scene. The image should be wider than the scene. Now select and distribute the layers. Now convert those images into movie clips. Now go to frame 80 and add all frames. Get back to the first layer and create a shape that is the your mask. Now go to frame 40, select key layer and add free transform tool. Now, mask t...

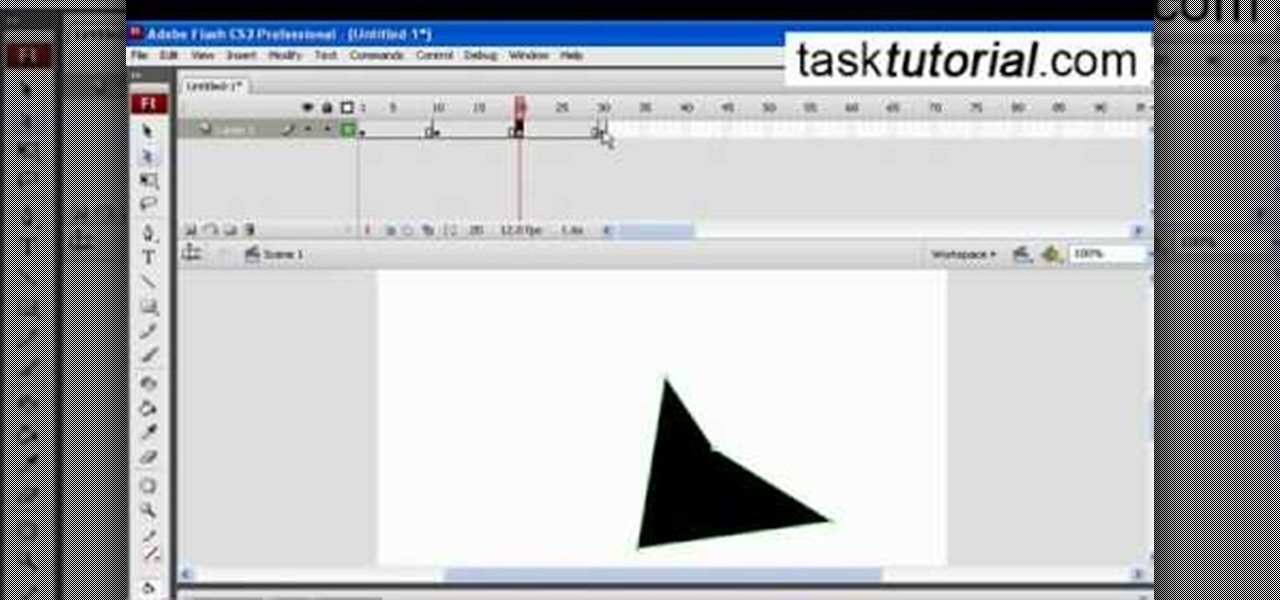
This simple video tutorial teaches you how to create an animation of basic shapes transforming from one shape to another when using Flash.