Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continue to thrive despite the developer's best efforts to root them out. While the latest updates have blocked users from running modded versions of the game, like Pokemon GO++, that feature built-in joysticks to move your pla...
Usually, we think of vaccines as preventative, a shot we get to prevent the flu or some childhood disease like measles or mumps. But there are vaccines for other purposes, such as the ones studied by researchers from the Netherlands.

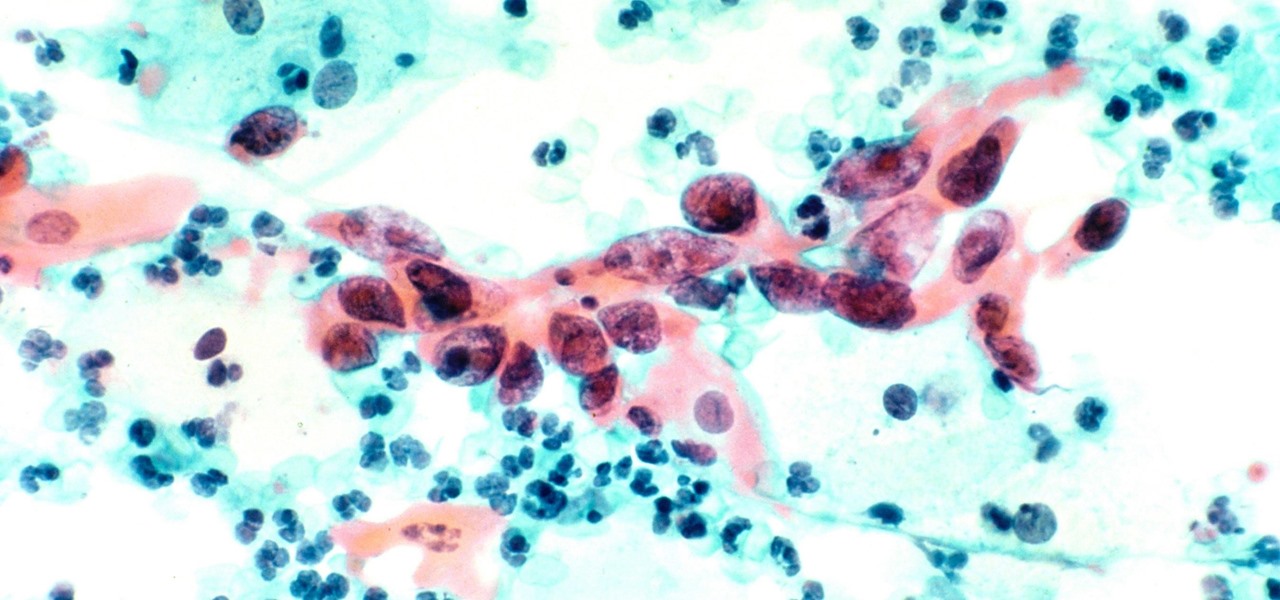
Two viral liver diseases could help us find the path toward the cause of Parkinson's disease. Researchers from the University of Oxford and UCL Institute of Neurology in London have reported an association between hepatitis B and C infections and an increased risk of Parkinson's disease. Their findings were published early online in the journal Neurology.

We all know you are what you eat—or so the expression goes—but it's good to remember that what you are (at least intestinally) is mainly bacteria. A new study has shown that what you eat, and how your gut microbiome reacts to that food, might be a key player in your risk of developing a certain type of colon cancer—and changing your diet can help decrease your risk.

Most of us equate feeling cold with catching a virus—but we've also heard plenty of debunkers proselytizing that being cold isn't what gives you the flu.

With the Game Developers Conference (GDC) in San Fransisco just a few weeks away, Microsoft Senior Program Manager Vlad Kolesnikov has announced via Channel9 (Microsoft's developer news outlet) that not only will new low-cost virtual reality headsets be coming in March to developers, but that they will be at GDC, too.

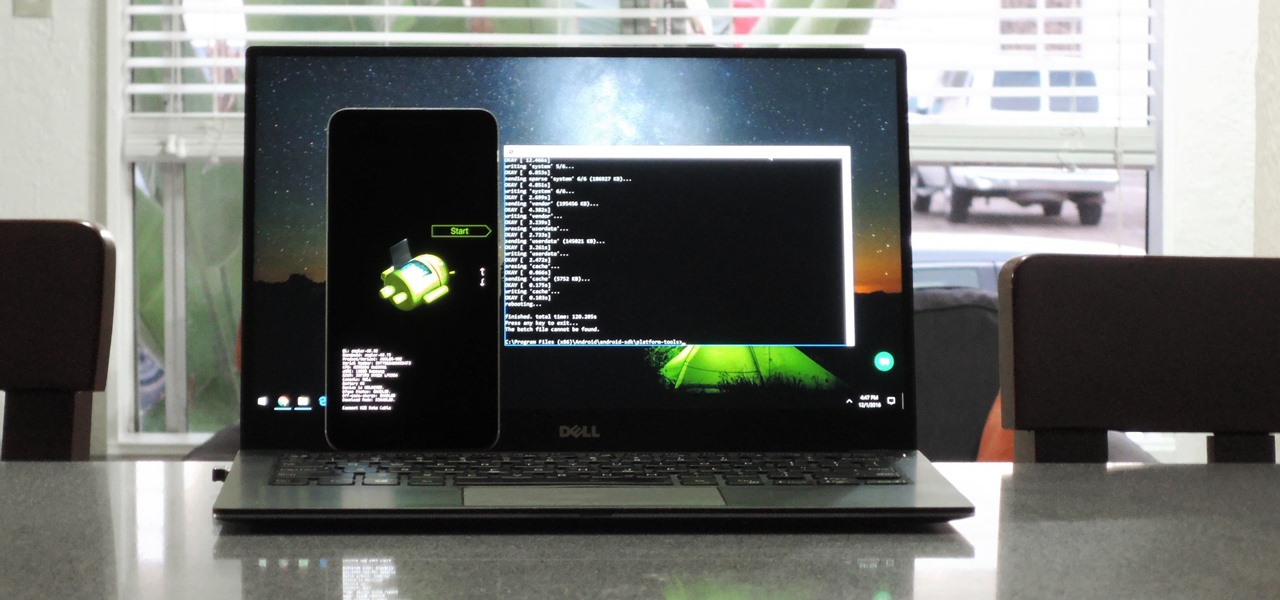
If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or even getting new Android updates before everyone else.

If you just can't wait to see the Pixel and Pixel XL, the new Google-branded smartphones expected to be announced tomorrow, you're in luck. After weeks of rumors and blurry images, a smartphone sales company called Carphone Warehouse just accidentally dropped the entire ball. The UK business accidentally set the product pages for the Pixel and Pixel XL live a couple days early, and for just long enough for them to be archived before they were taken down.

Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using an Xposed module to modify the YouTube app itself and force it into not showing ads.

We like to think of ourselves as caprese connoisseurs. When we made our first batch of the iconic tomato salad, we became obsessed with the classic combo of fresh basil, sweet tomatoes, and creamy mozzarella cheese. But after a while, we wanted more than just the basic, layered Italian summer staple.

Finding Pokémon in the wild isn't the only way to add to your collection in Pokémon GO—you're also able to hatch your own from eggs that you've gotten from PokéStops.

You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

If you have no desire to get a separate Mac desktop computer, but want to either supersize your laptop's screen for gaming or need to get additional screen real estate while you work, then connecting your MacBook, MacBook Air, or MacBook Pro to an external display is the right call.

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

The awesome thing about Android is that you rarely need to settle for what comes stock on your device. If your music app sucks, switch it. If you don't like your home launcher, swap it for a better one.

These days, operating systems are becoming more and more touch-oriented, or at the very least, heavily mouse-driven. Nonetheless, while novice users will find it easier to tap and click their way around, power users know that keyboard shortcuts are still the fastest way to get things done.

In the U.S., smartphone users spend more time on Facebook and Instagram than on any other app. If this sounds surprising for any reason, it shouldn't. Anyone that's browsed Instagram in a moment of boredom knows that a few minutes can quickly turn into an hour down a rabbit hole filled with Likes, Follows, and straight-up lurking.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

The next time you're out camping, whether it's outdoors in the wilderness or right outside in your own backyard, try this hack out for an effortless campfire all night long. While there is definitely some prep work involved, it's well worth it if you don't need a huge bonfire, and more so if you plan on cooking meals over the flames.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Saying that I was obsessed with Pokémon as a child would be a serious understatement, and even though I'm not the Pokémon fanatic I once was doesn't mean I don't love playing still. However, I do often find myself dumbfounded by all of the new features and characters in each generation.

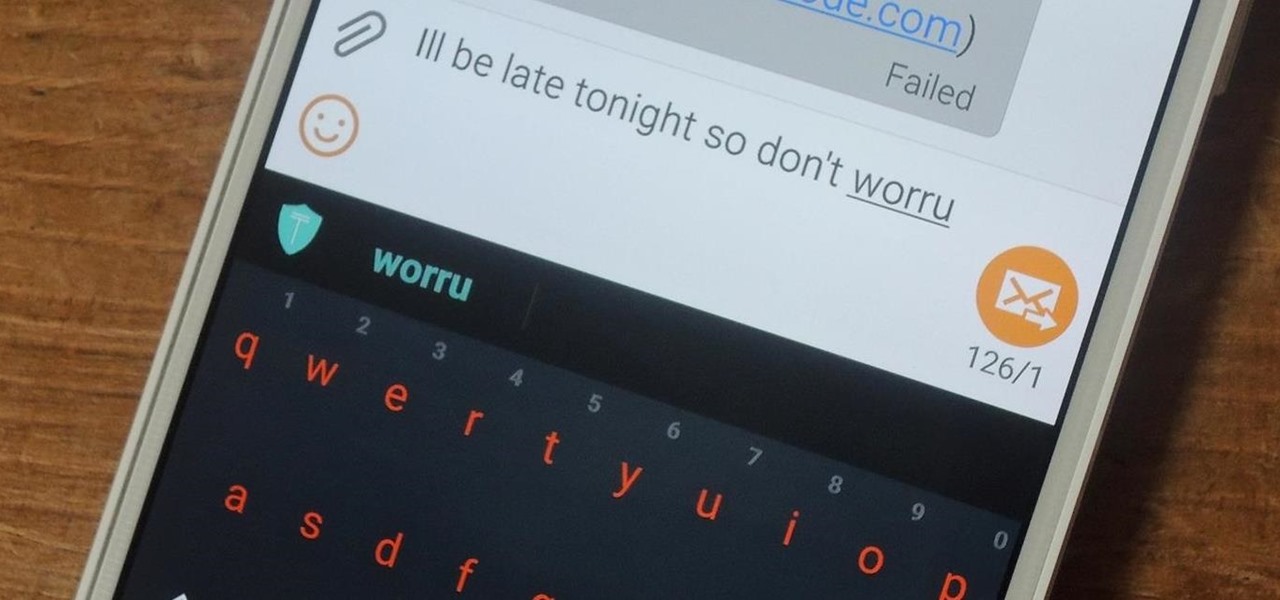
My reliance on autocorrect has made me a horrible speller. I take it for granted that it'll catch all my mistakes, but it only ends up making matters worse (especially when it inadvertently makes correct words wrong). So instead of relying on autocorrect to fix typos, why not try to completely prevent mistakes from happening in the first place?

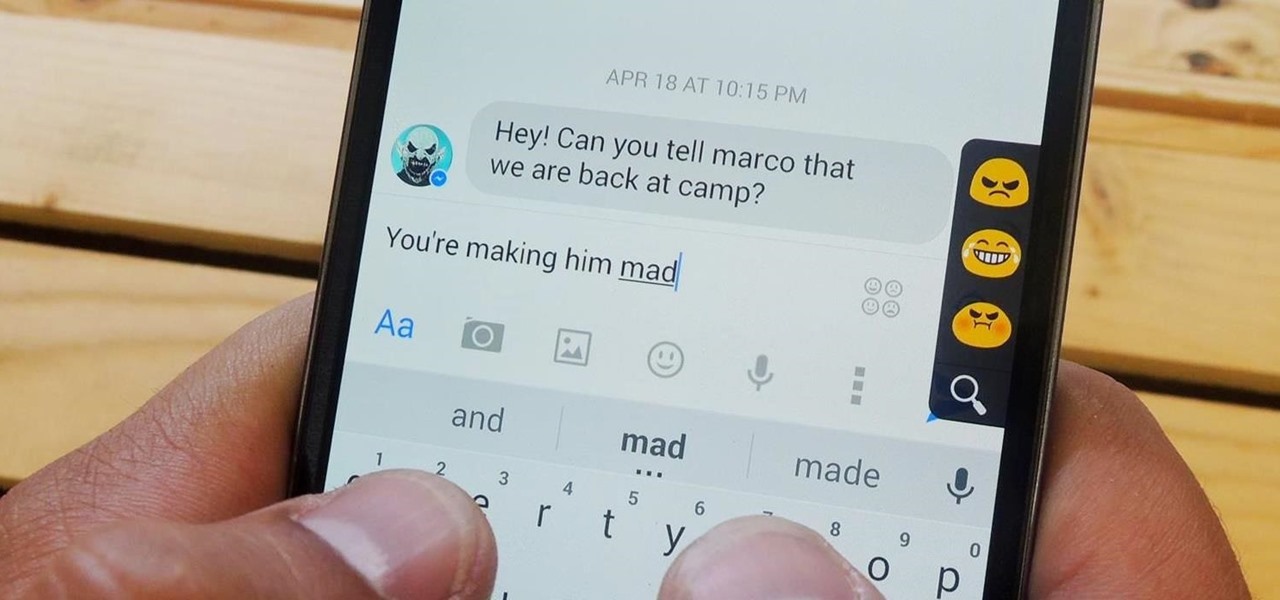
Some third-party keyboards, like SwiftKey for example, include a convenient feature that suggests emojis as your type based on the content of what you're saying. Unfortunately, many keyboards, including most stock ones, don't include this function.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

You don't need a study to tell you how beneficial music is to helping you fall asleep. Most of you probably have your soothing playlist and SleepPhones queued up and ready to go before you get into bed and count those Zs.

The switch from Dalvik runtime to ART in Android Lollipop has rendered the Xposed Framework useless until a new version is released, but Xposed isn't the only way to mod a phone.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

How many times do you think you press the Home button on your iPhone? You probably can't place a number on it, but you know it's a lot.

Google's music offerings have been on a roll lately. First they announced a new music video streaming service called YouTube Music Key, offering ad-free playback with background listening. Then they stated that the new offering would be rolled in with their Google Play Music service, with members allowed to exclusively test the Music Key beta, which just went live. And if all that wasn't enough, they're also offering free music to boot!

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Rooting is a great way to unleash your device's full potential, but not everyone's comfortable with it. Rooting can void a warranty, cause issues with certain apps, and the process itself can be tricky for older devices. Alas, most of the great apps or mods out there require root access, like the ability to utilize a built-in KitKat feature known as Immersive Mode.

We've had the pleasure of test driving the ASUS Transformer Book T100T for the last couple of weeks, and for a $400 Windows 8 machine, it's impressive to say the least.

With rumors of the Active and Prime versions on the immensely popular Galaxy S5 circling the web for the past few weeks, today, we've got some clear proof of the upcoming Active variant.

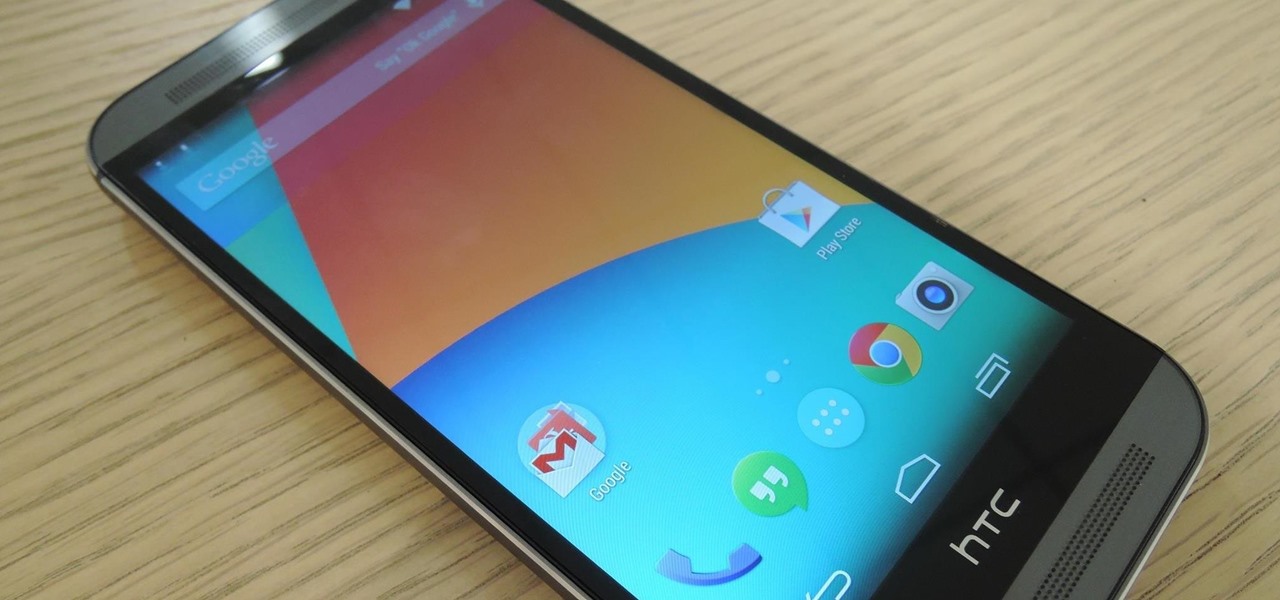
There really isn't any custom manufacturer skin, like Sense, that can match the clean look and fluidity that comes with stock Android. HTC knows this, and they, just like Samsung, include a Google Play Edition version in their flagship lineup.

Let's say you're watching a video and everything's going great, but you feel the need to raise the volume a tiny bit. You hit the volume button on your Nexus 5, and all of a sudden, a giant volume slider appears that obscures half of your video for 3 seconds.