Go to a chain supermarket, and chances are you'll see one type of garlic—maybe two or three if you're lucky. However, there's a mouthwatering slew of Allium sativum out there, far beyond those papery white bulbs most of us encounter at the nearest Stop 'n' Shop.

I'll give Samsung credit where it's due—the stock keyboard on the Galaxy S5 is actually pretty nice. There's a dedicated number row that resides at the top (something that the Google Keyboard needs a hack to achieve), and various settings exist to make switching between languages a breeze.

Cold brewing tea and coffee are all the rage, and for good reason: they're idiot-proof. I, personally, am a total dunce at brewing coffee. It either ends up strong enough to peel paint from a car or so weak that you can see through it. Meanwhile, I have friends who inevitably brew green tea to the point where it's painful to drink it.

Google has finally announced the newest flavor of its mobile OS, Android L (Lollipop?), and I couldn't be more excited. While we won't see its official release until the fall, there are still some features we can get our hands on right now.

It used to be easy to hack tethering—root your device and install a third-party or modded tethering app. But snuck in amongst the changes in Android 4.3, a new data-monitoring service of sorts made its debut. There used to be a time when your data connection was yours. You paid for it, so you were free to use it for whatever you wanted. Unfortunately, those days are long gone.

Apple released the new Mac OS X 10.10 Yosemite in the Mac App Store for everyone to download and install for free on October 16th, 2014, but downloading a 5+ GB file for each of your computers will take some serious time. The best thing to do is download it once and create a bootable install USB drive from the file for all of your Macs.

Bees are the key to pollination and healthy vegetation, and wasps may help by assisting in pest control, but despite their benefits in the world, they're still a real pain in the ass if they're in your face.

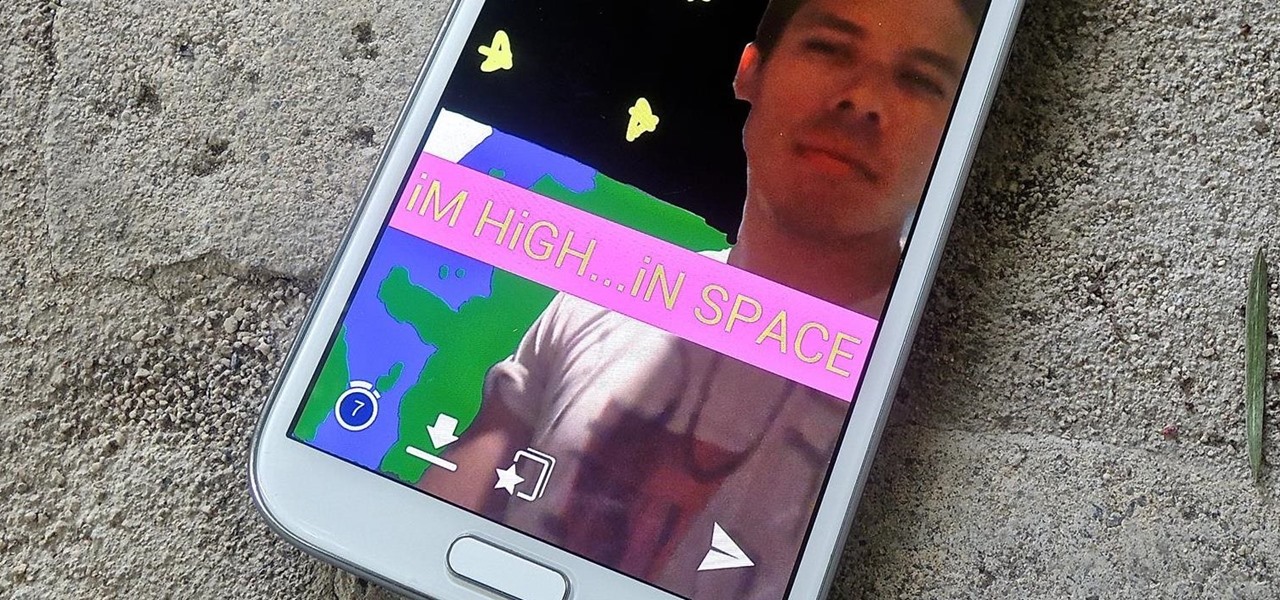
Twitter found a sweet spot with its 160-character limit, but Snapchat sports a social media low of 31 characters, forcing us to condense our ideas into a few short words when typing in picture captions because of their ephemeral nature. While this severely limited amount of words is Snapchat etiquette, I've got so much more to say than 31 characters!

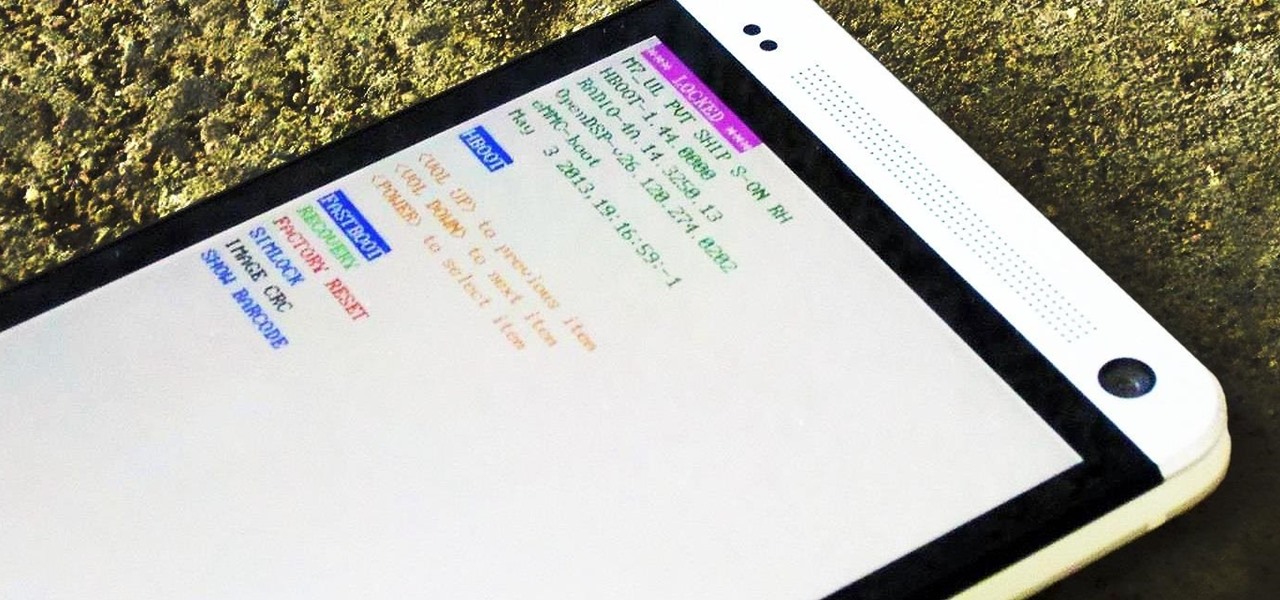
Once you unlock your bootloader and root, you're left with one more hurdle to overcome, and that's getting S-Off.

In an attempt to keep things simple, Snapchat has a limited amount of editing features, made up of "smart" photo filters, drawing pens, and special text captions. If you want more editing capabilities, you'll be pleased to know there's a way, no thanks to Snapchat, but you will need to be rooted.

Puff and Po and the Empress's Treasures, is an inspiring indie game that stays fateful to the arcade single screen plat-former style and game-play.

Ever since the much-lauded effects of the Mediterranean diet became widely known, people have been buying olive oil by the gallon. A diet that prevents heart disease, is based on fresh, seasonal foods, and includes a tasty as hell fat like olive oil? Duh—that's a no-brainer.

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

A picture is worth a thousand words, and depending on what you're taking a picture of, it could be worth a lot more. Our phone's camera can easily capture high quality photos, scan barcodes, and make us Instagram famous. You can compare prices of items and download applications just by scanning a QR code. Of course, we can always do this stuff a little bit better on our iPhones.

A banner alert for notifications is like the Robin to our iPhone's Batman—they're taken for granted and don't really get the recognition they deserve. Yes, they can be disruptive at times, but just like Robin, they can be necessary for getting things done.

There are already a ton of glitches on Grand Theft Auto Online, and one of the newest ones to be uncovered lets you make millions in less than an hour, but you will need a million to get the job done. This glitch, revealed by YouTube user Caspahz below, lets you duplicate exotic cars that you already own so you can sell them for quick cash.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

If you're reading this, chances are you're a softModder, someone who doesn't let anything stand in his or her way from ultimate customization.

Mac laptops, especially the older PowerBooks, often can become very hot when doing processor intensive tasks like movie rendering, YouTube videos streaming, database lookups, or just gaming. Often just lifting the machine from the surface is enough to cool it down without the need of expensive hardware or software tuning.

Headphone cords are one of those things we all deal with because it beats the alternative (no music). But they can be so obnoxious—they're always getting caught on things, and they seem to be perpetually tangled. If you have ear buds, you can make a simple a cord container to keep them organized, but over-ear headphones are a little more tricky.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

The fill tool will allow you to alter the appearance of objects in your web design document and can be very useful for marketing purposes. The fill tool can be used to give objects one solid color for simple designs.

Lots of us have already tried leopard nails and in this one I have added a new twist to the design to make it slightly more exciting for all of us who love this design pattern!

When we think of search it's usually in regards to the internet. But when you are using a smartphone, searching your device itself can be just as important and useful.

If you have a Mac running Mountain Lion, I'm sorry to tell you that all it takes to crash almost any app on it is eight little characters. This strange bug seems to only affect Mountain Lion and doesn't cause your computer any harm. Apparently, it even crashes the error reporter. On its own, the bug doesn't really pose a threat—just don't type it.

As enjoyable as Facebook can be at times, it can also be a great distraction and even better deterrent of getting work done. A quick "Oh, let me check my notifications" can turn into hours and hours of Facebooking, and before you know it, you're already on your 7th Wikipedia page, all thanks to that status your friend posted. The reason I mention this is because Firefox's new 17.0 update includes many features, but the one that's been making the rounds online is the integration of Facebook Me...

As a technology writer, phone screenshots can pile up on your computer in no time. Testing out different apps, showing buggy software, and doing step-by-steps can lead to a plethora of mobile screenshots piling up on your computer's desktop. The problem with my screenshots is that they save as photo.png or photo.jpeg, as do many of my other photos. If I haven't finished a project or article, I tend to move them to different folders to save them for later. After a while, the screenshots begin ...

With the Samsung Galaxy S III being a hot commodity, it's no surprise that your friends might try unlocking your fancy password-protected phone. While some friends have good intentions when using your phone, there are those certain friends who get into the phone to do this... The worst scenario might be that you leave the phone around a group of friends, come back and find that all of your social media accounts have been hacked. When you yell out to your friends asking who did it, no one make...

Playing advanced games on your phone can be pretty frustrating sometimes. Touchscreen devices are great for everyday apps and games designed solely for them, but when it comes to games that require multiple actions in conjunction with directional movement, it gets ugly.

The Dark Knight Rises. The Amazing Spider-Man. The Avengers. Halloween is a few weeks away and all we're going to see are these same ol' superhero costumes. It's like that every year, due to the immense popularity of comic book films by DC and Marvel.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

This video is about removing sticky keys. The video begins with clicking on start in Windows XP, clicking on settings, control panel, accessibility options. In accessibility options you will see three key options which are unchecked. Click on settings of the first option which is the Use StickyKeys option and you will see five options of which the first three should be checked. In the second option which is the Use FilterKeys option ,there are five options which should be checked except for t...

Learn how to install the voice changing software AV Voice Changer onto your desktop. The video will show you how to download VCS Diamond 6.0, how to install it, and gives you a free key so you can actually use it to start editing voices.

With tips from this video, play "Aloha Oe" in the key of G on the ukulele.

Check out this video to see how to make a box style weave lanyard key chain from start to finish.

Check out this video to see how to paint Buddha meditating in Sumi-e style of ink painting. The key three lines are, 1)shoulder outline, 2)inside line to abdomen, 3)slanted down line from abdomen.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).